-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
EPC configuration for iOS Mobile Connect Connections



Description
Mobile Connect VPN connections can be checked and provisioned in a separate EPC zones. This article will explain the different EPC definition checks that can be performed with the iOS devices when connecting with the Mobile Connect client. We recommend a separate EPC zone and Profile for Mobile Connect connections as the definition settings would be different from other client machines connections and checks.
Cause
Admin would like to provide access to resources based on some properties of the iOS phones like Equipment ID, Certificate, iOS version, etc.,
Resolution
1. EPC Check for UDID/Equipment ID:
Step 1: Obtaining the Equipment ID: ActiveSync based EPC check uses the serial number of the iOS device whereas for Mobile Connect client, we will be using the UDID of the device. Users can find the UDID using iTunes or from the SMA appliance System message log / Unregistered device log.
Once we launch iTunes, we need to click on the serial number of the Phone and then we can see the UDID details as shown below: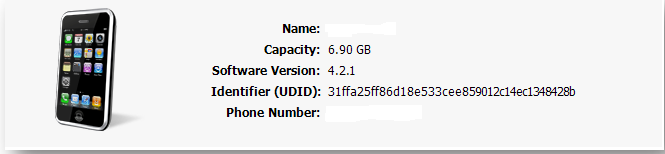
To get the Equipment ID from the appliance, define a EPC Profile using Variable.
a) Create a variable from Resources - Variables. Click New. Configure a Name for the variable, Type as User attribute, Select the Realm and then select the appropriate attribute in which you will configure the Equipment ID of the user. Save.
b) Navigate to End Point Control Profiles - Add a new iOS profile - Set Type as Equipment ID. In the Device Identifier field, select the variable. Select the checkbox "Match profile if user has no registered devices"
c) Add to Current Attributes, Save and add the profile in the zone. Add the zone to appropriate community.
Now the user does not have any Equipment ID entered in the attribute, so the first connection will be allowed and following log will be seen in the appliance System message logs.
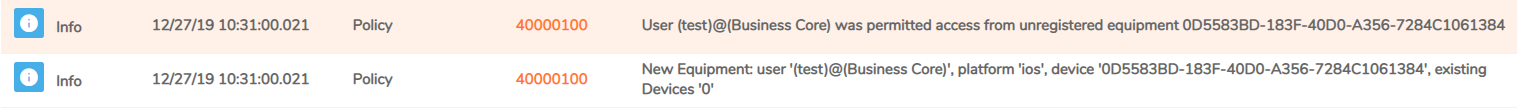
The same Equipment ID can be found in Unregistered device log:
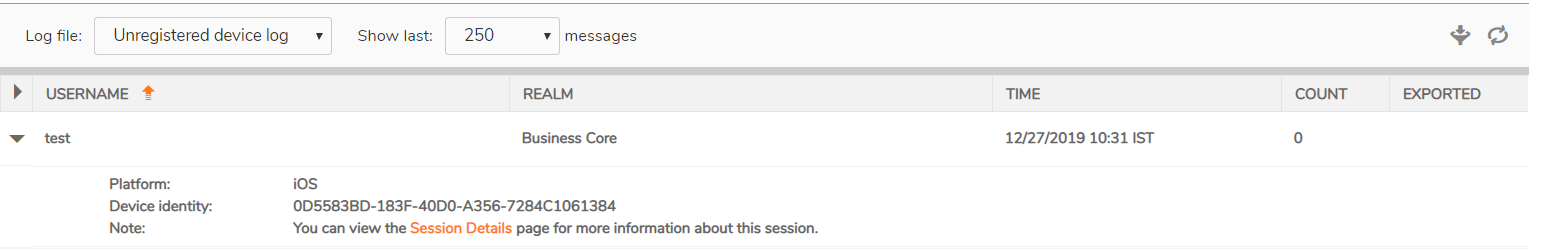
Step 2: As we now have the Equipment ID of the devices, configure the same in the respective user's attribute. From then on, only the configured IDs will be allowed.
2. EPC Check for Client certificates
For configuring a client certificate profile, Click Here
3. EPC check for iOS version
a. Configure the EPC profile to allow certain iOS based devices only. In the following example, we are allowing connections only from iOS 4.2.1 & later.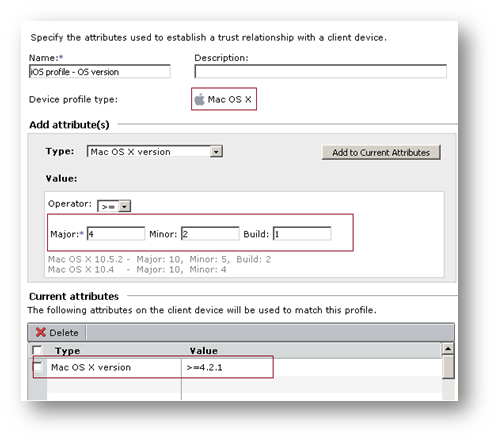
4. EPC check for Application or Directory to deny Jailbroken phone access
Finally customers can deny Jailbroken phones from connecting to the network using the mobile connect client by defining EPC checks for Jailbroken applications and File names. Phones matching these profiles can be provisioned to a deny zone.
a. Check for Jailbroken application Directory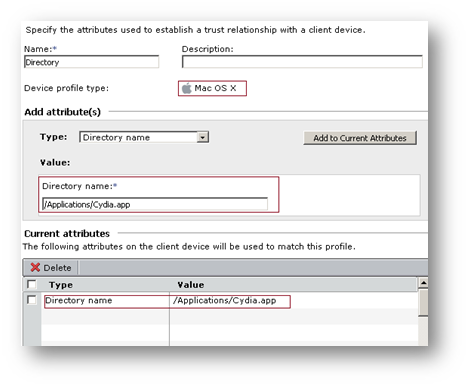
b. Check for File names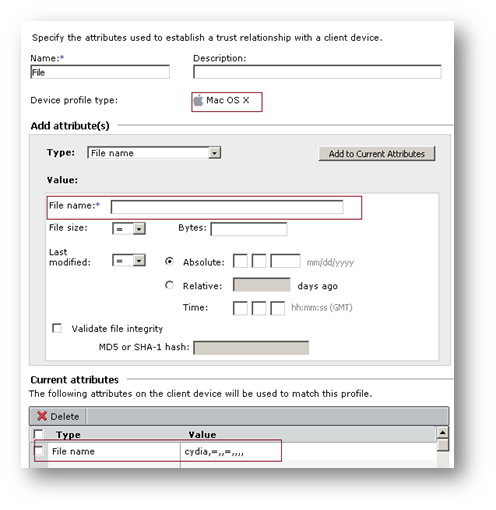
Based on the above results, we can provision Jailbroken phones in a separate EPC zone. The following is the Realm configuration example used to test the above definitions. As you can see we are using the same realm to connect regular clients and Mobile Connect clients.
Related Articles
- How to download Client Installation package and the access agents from the appliance using WinSCP
- SMA 1000: How to update Advanced EPC Signatures to the Latest Version
- If OTP is enabled, NX disconnects after SMA100 Connect Agent installation






 YES
YES NO
NO