-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Dropped packets because of "Invalid TCP Flag"



Description
This article describes how to workaround the drop "(Invalid TCP Flag(#2)), Module Id: 25(network)" due to network issues.
 CAUTION: This KB only shows a possible workaround for the issue however most of the drops due to Invalid TCP Flags are related to network issues and they should be analysed and corrected.
CAUTION: This KB only shows a possible workaround for the issue however most of the drops due to Invalid TCP Flags are related to network issues and they should be analysed and corrected.
If the TCP Flags behavior is wrong, following this KB article will not bring any improvement.
Cause
- Packets may be perceived as having Invalid TCP flag if packets with SYN+ACK+PSH, instead of SYN+ACK, are received.
- Packets may get to the SonicWall with incorrect sequence numbers due to 3rd party issues or source configuration (i.e. sequence number randomization).
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
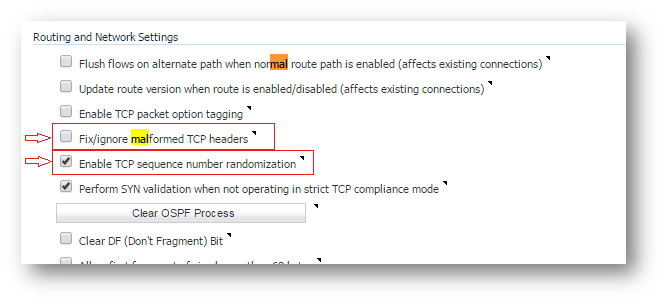
- Enable Fix/ignore malformed TCP headers and disable Enable TCP sequence number randomization in the internal settings page.
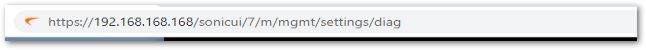
- Enter the internal settings page by entering "https://<IP ADDRESS>/sonicui/7/m/Mgmt/settings/diag" in the address bar.
- Click on Internal Settings.
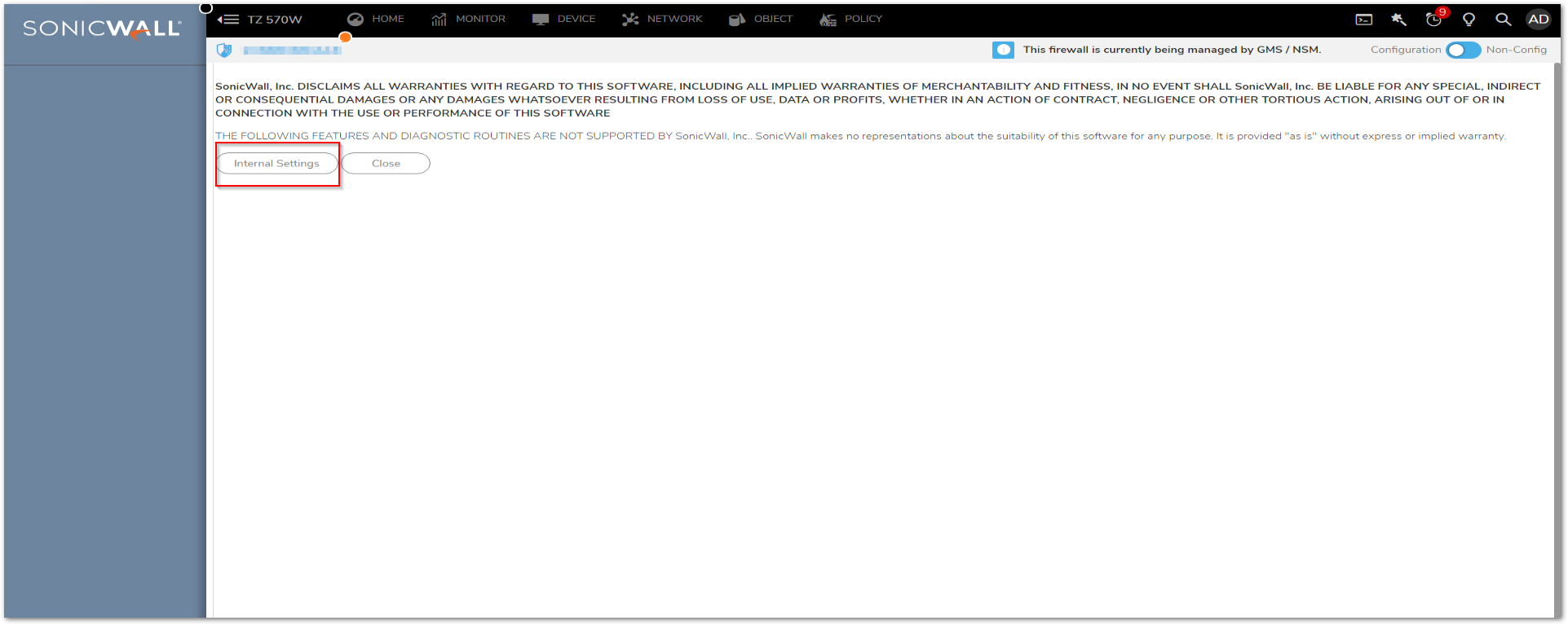
- Enable Fix/ignore malformed TCP headers and disable Enable TCP sequence number randomization.
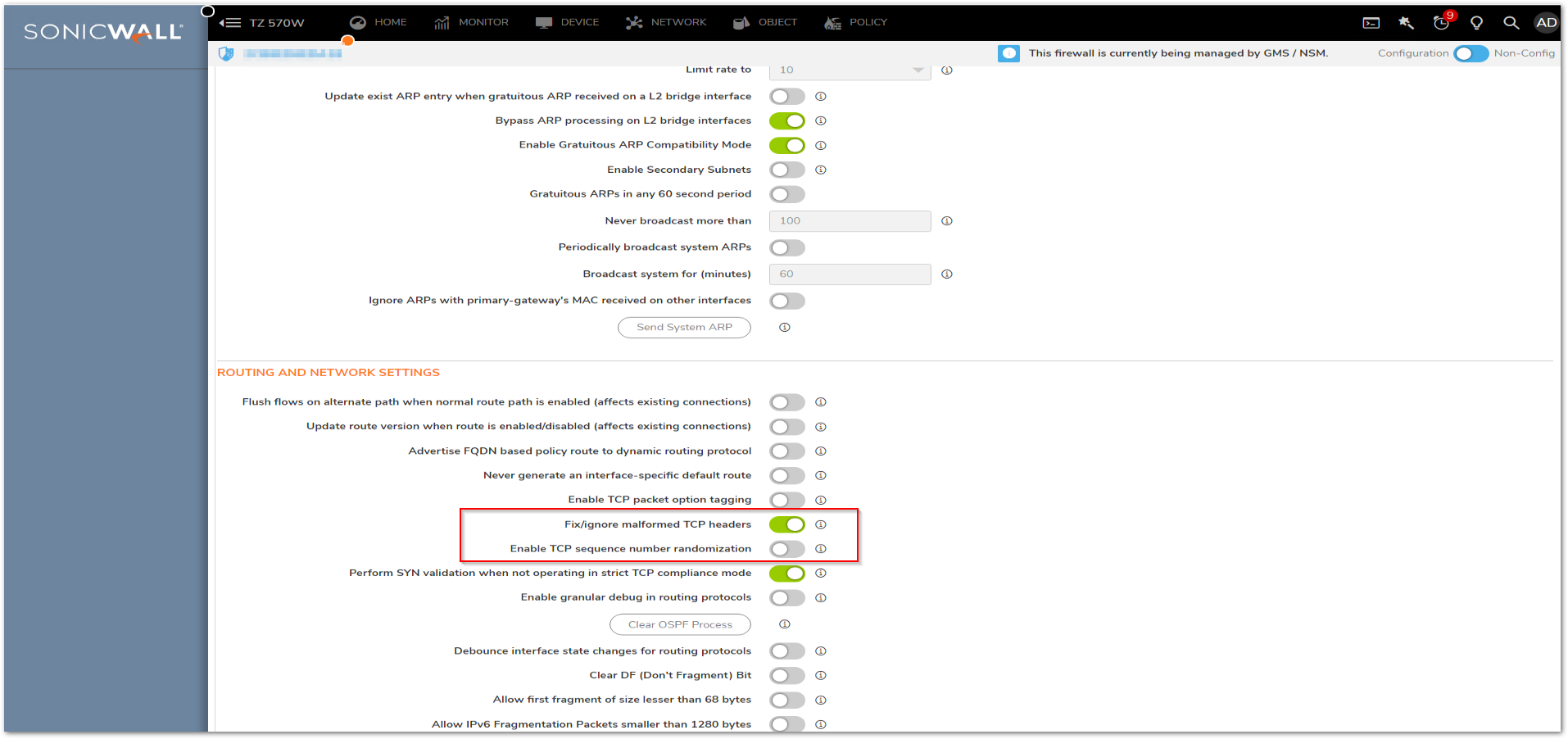
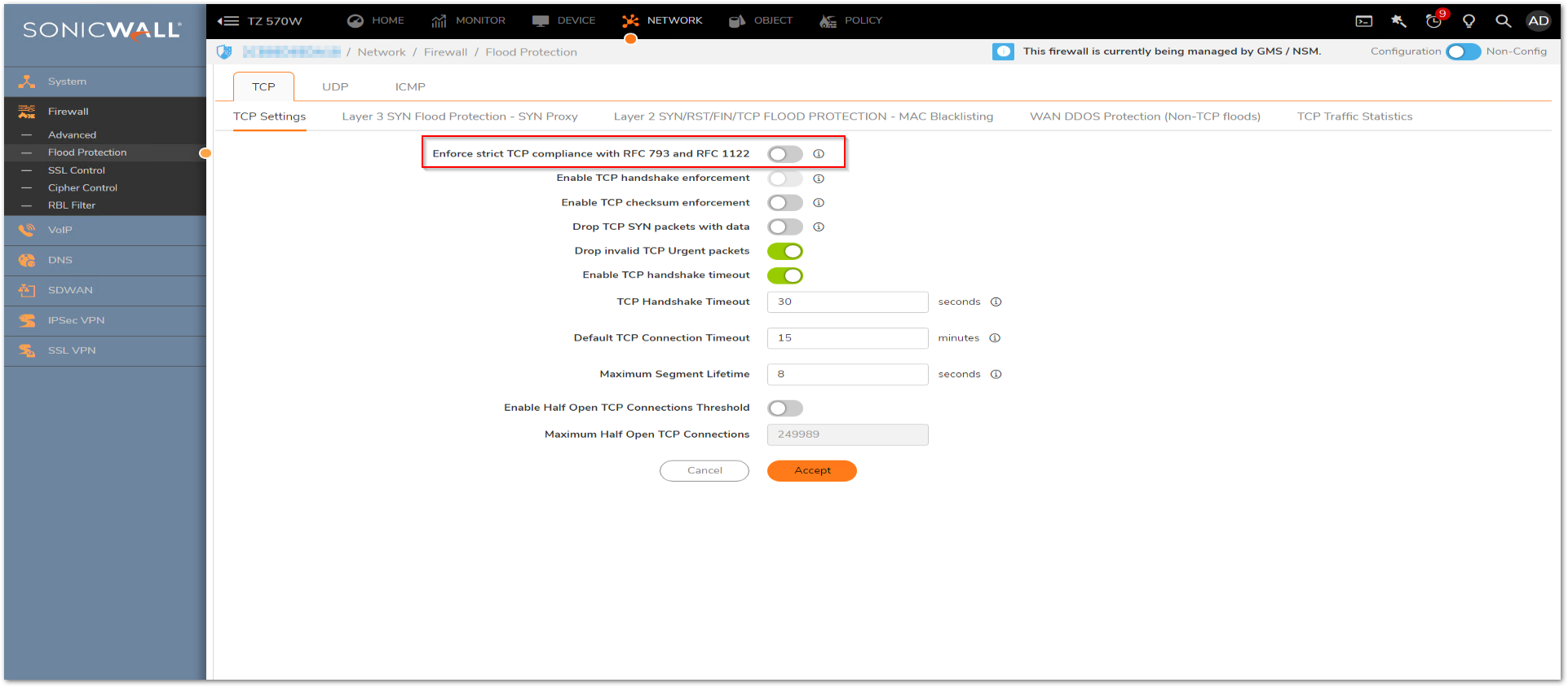
- If the drop is related to incorrect sequence number, you might disable Enforce strict TCP compliance with RFC 793 and RFC 1122 under Network tab Firewall | Flood Protection | TCP as this could be related to the sending device not fully complying with TCP standards.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
 NOTE: Invalid TCP Flag drops are usually related to a 3rd party issue as the packets are arriving to the SonicWall with a wrong sequence number or in wrong order.
NOTE: Invalid TCP Flag drops are usually related to a 3rd party issue as the packets are arriving to the SonicWall with a wrong sequence number or in wrong order.
- Enable Fix/ignore malformed TCP headers and disable Enable TCP sequence number randomization in the internal settings page.
- Enter the internal settings page by entering diag.html in the address bar in place of main.html.
- Click on Internal Settings.

- Enable Fix/ignore malformed TCP headers and disable Enable TCP sequence number randomization.
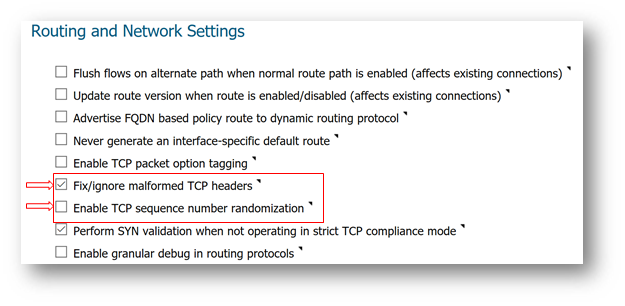
- If the drop is related to incorrect sequence number, you might disable Enforce strict TCP compliance with RFC 793 and RFC 1122 from Firewall Settings | Flood Protection as this could be related to the sending device not fully complying with TCP standards.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Here's some workarounds for this issue.
 NOTE: Invalid TCP Flag drops are usually related to a 3rd party issue as the packets are arriving to the SonicWall with a wrong sequence number or in wrong order.
NOTE: Invalid TCP Flag drops are usually related to a 3rd party issue as the packets are arriving to the SonicWall with a wrong sequence number or in wrong order.
- Enable “Fix/ignore malformed TCP headers“ and disable “Enable TCP sequence number randomization” in the internal settings page.
- Enter the internal settings page by entering diag.html in the address bar in place of main.html.
- Click Internal Settings.
- Enable Fix/ignore malformed TCP headers and disable Enable TCP sequence number randomization.
- If the drop is related to incorrect sequence number, you might disable Enforce strict TCP compliance with RFC 793 and RFC 1122 from Firewall Settings | Flood Protection as this could be related to the sending device not fully complying with TCP standards.
Related Articles
- How to block like/comment/post/share features of Facebook using App Rules
- How to block various YouTube features using App Rules
- How can I enable or disable SonicWall firewall management access?
Categories
- Firewalls > TZ Series > Networking
- Firewalls > NSa Series > Networking
- Firewalls > NSv Series > Networking






 YES
YES NO
NO