-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
DPI-SSL Troubleshooting



Description
The following article provides in-depth troubleshooting for common DPI-SSL certificate related issues.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
When accessing a website you get an error stating your connection is not secure.
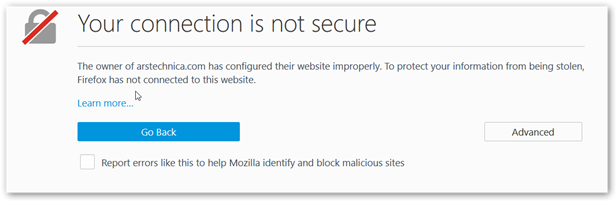
This is caused by not having the DPI-SSL resigning Certificate installed as a Trusted Root Certification Authority on this device.
You need to download the SonicWall DPI SSL certificate from the appliance interface in Policy | Deep Packet Inspection | SSL Client Deployment | Certificates 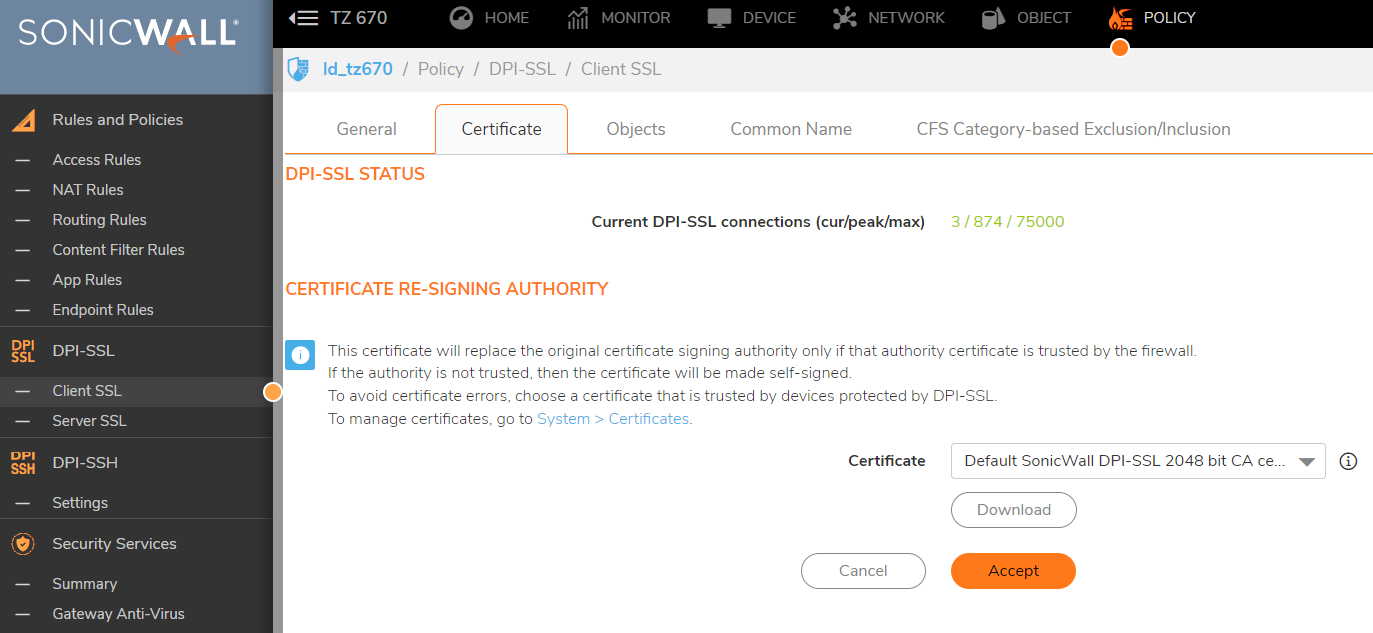
Internet Explorer/Chrome: Open Internet Explorer. Go to Tools | Internet Options, click the Content tab and click Certificates. Click the Trusted Root Certification Authorities tab and click Import. The Certificate Import Wizard will guide you through importing the certificate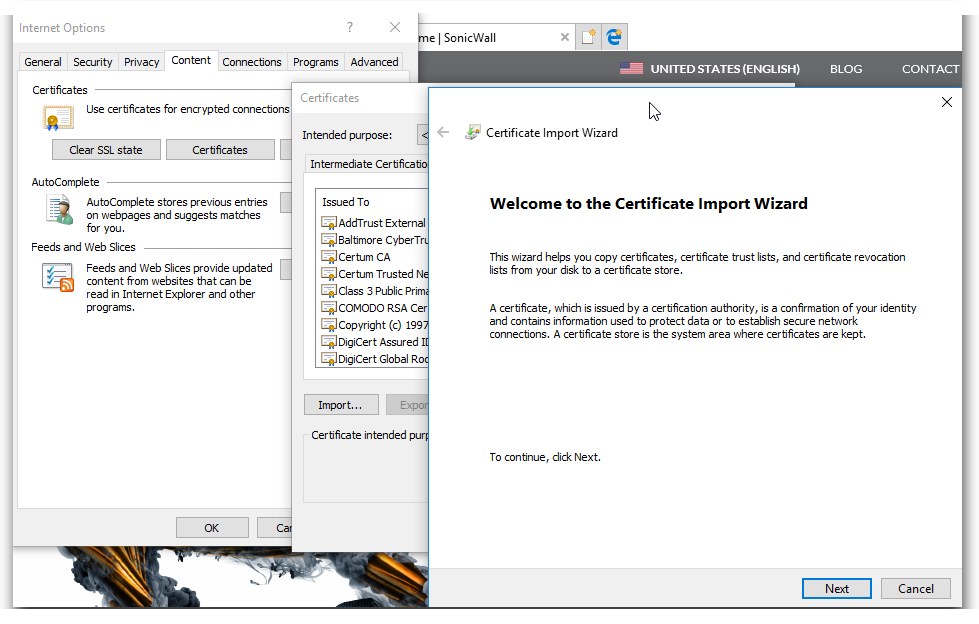
Firefox: Go to Tools | Options, click the Advanced tab and then the Certificates Tab. Select the Authorities tab, and click Import.
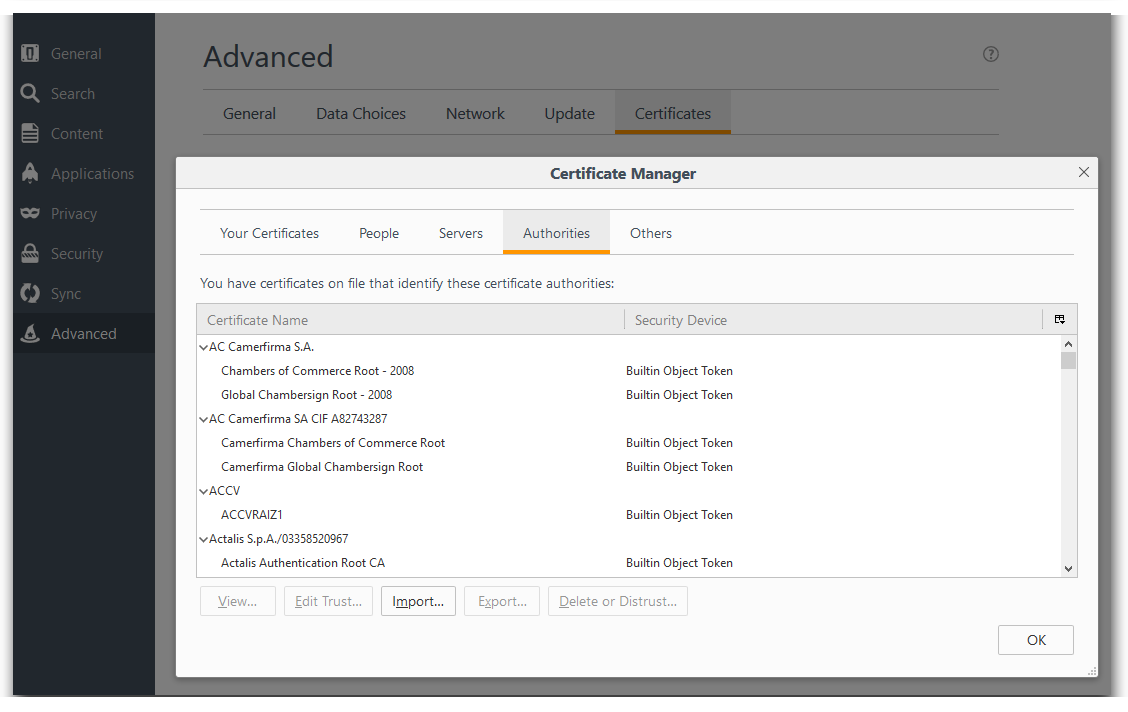
Select the certificate file, make sure the Trust this CA to identify websites check box is selected, and click OK.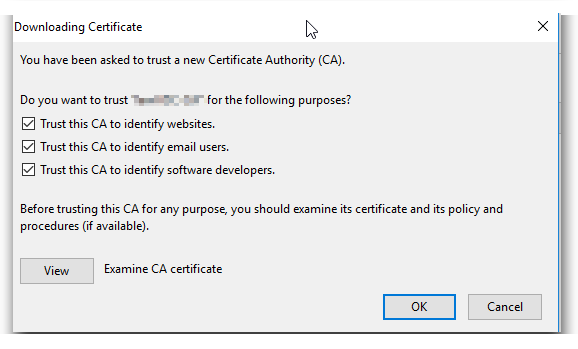
When accessing a website you get an error Secure Connection Failed(SEC_ERROR_INADEQUATE_KEY_USAGE)
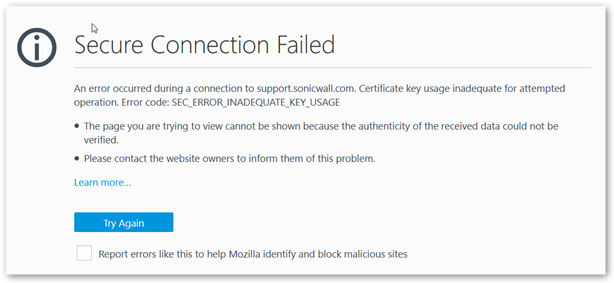
This is caused when the certificate used doesn't have resigning authority from your CA.
This process can be automated in a Windows Domain Environment using Group Policy. You can see the following article: Distributing the Default SonicWall DPI-SSL CA certificate to client computers using Group Policy
Certificate Errors in Browsers - Self-signed certificate
When Client DPI-SSL is enabled, accessing a few websites may cause the browser to display a certificate error. The specific error message could vary with different browsers. In Firefox it would show invalid security certificate and in Chrome the error message is Invalid Certificate Authority. In the certificate details, we would see the certificate is self-signed.
This error occurs rarely with some websites. This error occurs when the server sends a certificate signed by a CA not in the SonicWall's certificate store forcing the SonicWall to re-sign the certificate as self-signed certificate.
To resolve this issue, export the Root CA certificate of the website (either from a PC not intercepted by DPI-SSL or by disabling DPI-SSL temporarily) and import it into the SonicWall certificate store.
This is done from Device | Settings | Certificates
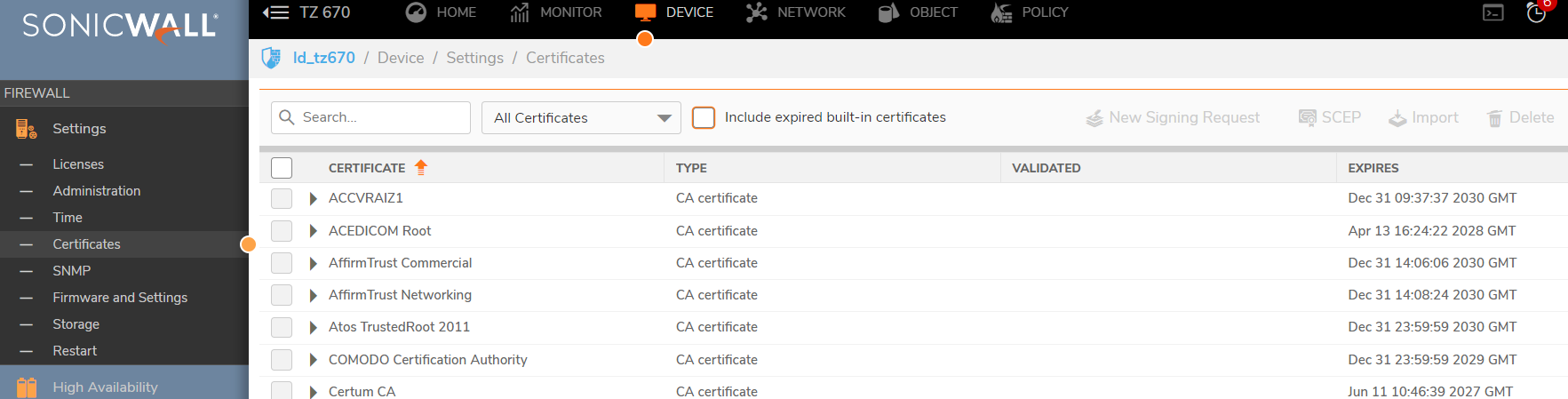
By default, when a server presents a certificate which cannot be verified by Client DPI-SSL because the Root CA is not present in its certificate store, it re-writes the certificate as a self-signed certificate. This default behavior of the SonicWall can be changed.
Go to the diag page of the SonicWall. The Diag page can be reached by typing in the LAN IP of the SonicWall in the browser, with a IP/sonicui/7/m/mgmt/settings/diag at the end. . Under the DPI-SSL section, enable the option Block connections to sites with untrusted certificates. Click on Accept to save the change.
 CAUTION: This is not recommended.
CAUTION: This is not recommended.
Client DPI-SSL and non-browser applications
There are certain applications which do not work when Client DPI-SSL is enabled though the SonicWall Client DPI-SSL CA certificate is imported into the certificate store. This is because such applications and/or websites do certificate pinning or SSL pinning. Certificate pinning is an extra check to make sure that the server the client is connecting to is really who they say they are, and not an impostor.
These applications include:
- Windows Update
- DropBox Client App
- Apple App Store
- Logmein Client
- Google Drive Client App
To allow these applications to work what we need to do is white list these certificates from DPI-SSL. When you add a certificate to this white list is will exclude any address that uses that certificate from being scanned by any of the DPI-SSL engines. We maintain a built in certificate white list to prevent connection issues with common websites.
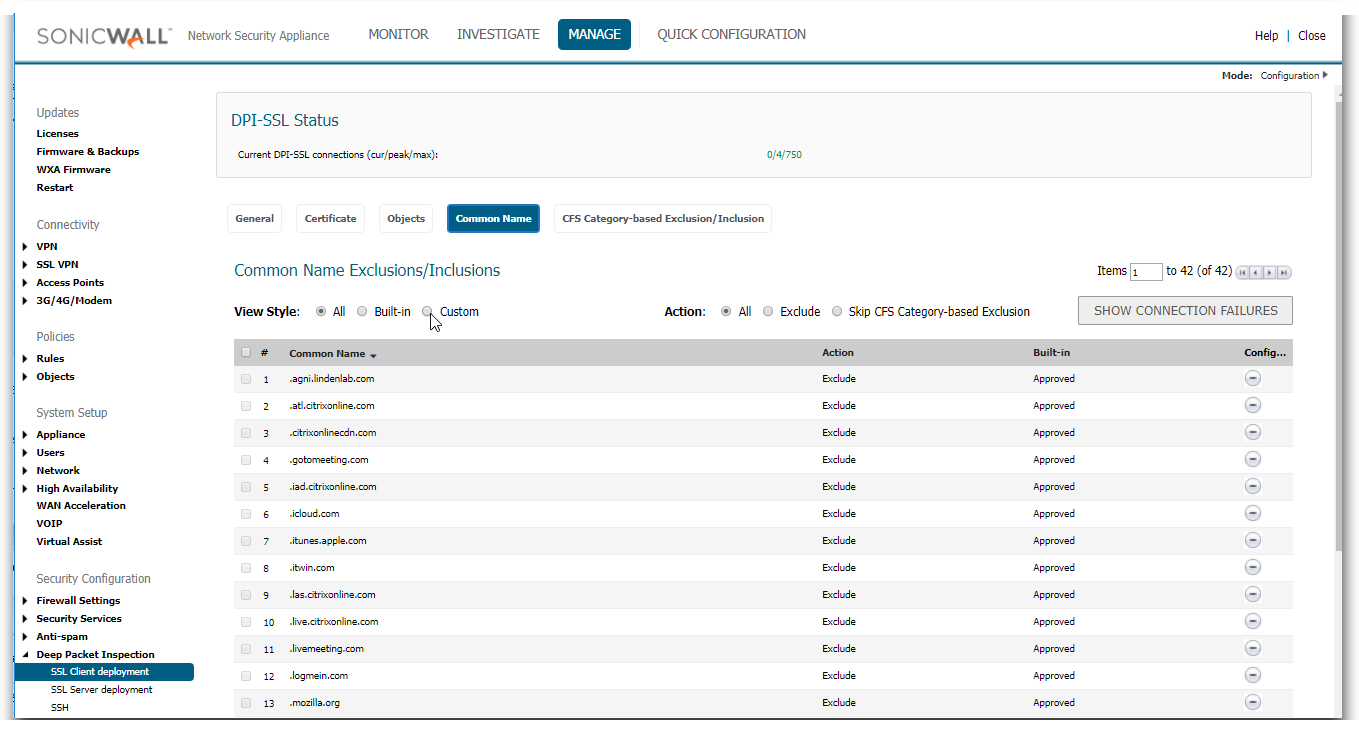
To view this list you will need to access Policy | Deep Packet Inspection | SSL Client Deployment | Common Name
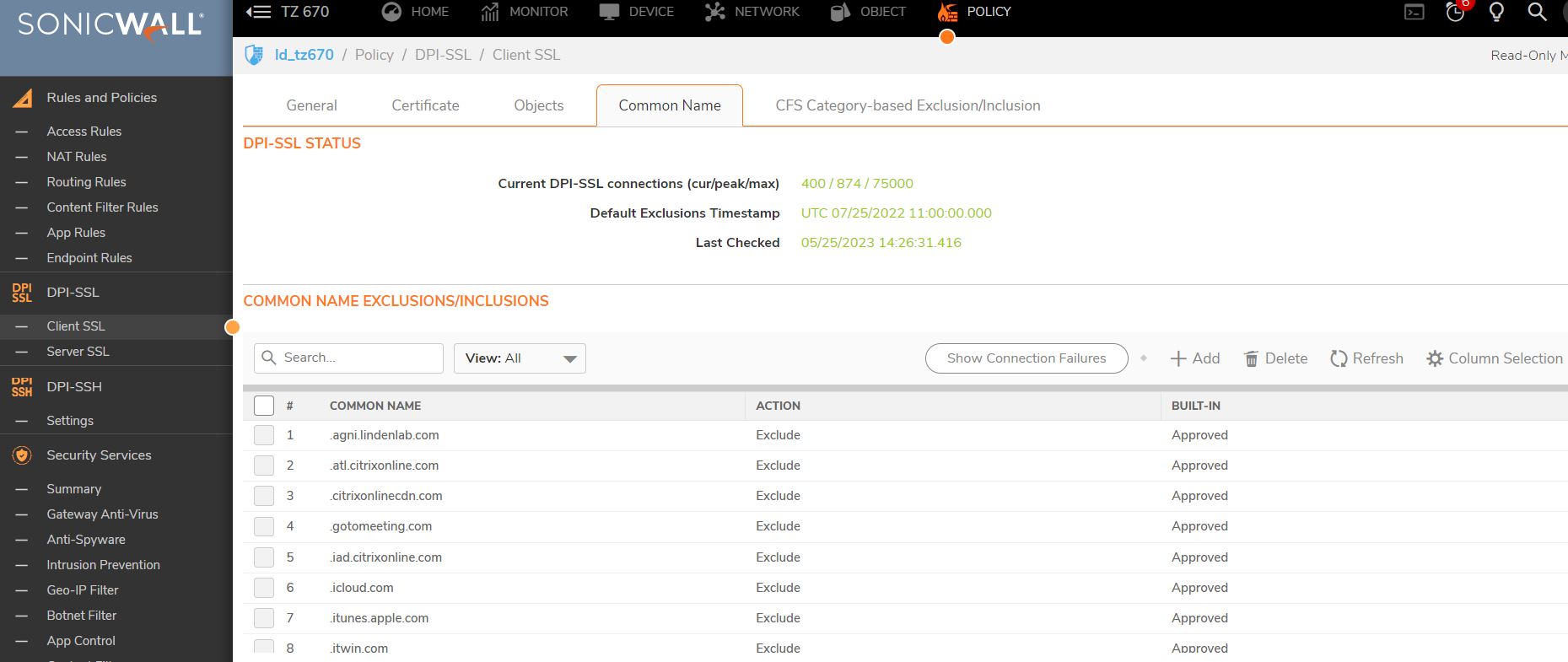
You can add exceptions in two ways.
The first way is if you know the common name of the certificate you want to exclude. You click on add, and you can add the common names of the certificates you want to exclude.
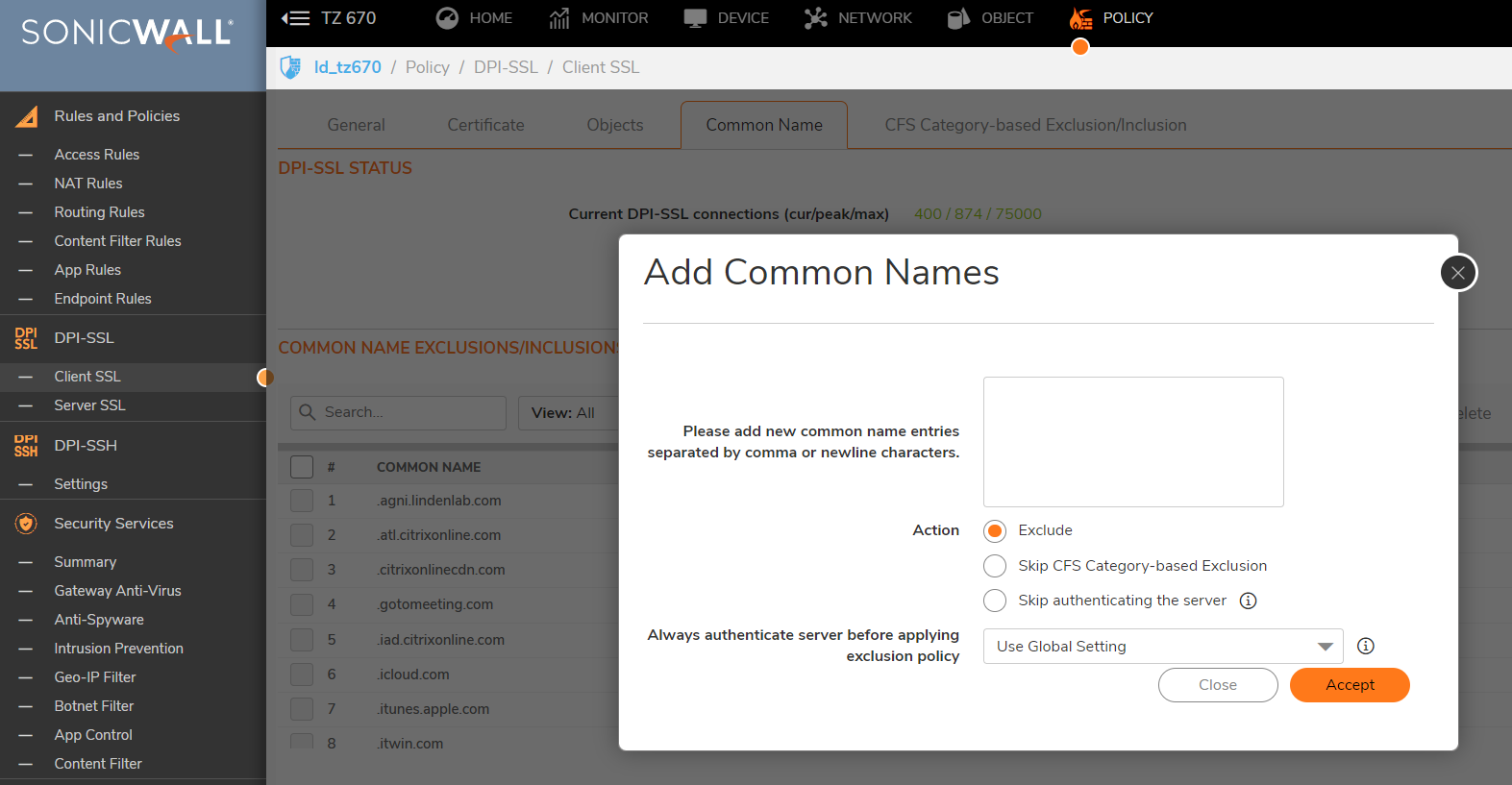
The second way is when you click on Show Connection Failures. On this screen it will present you a list of websites that have had SSL connection failures while DPI-SSL is enabled. You can check the box next to any of these and click exclude to add them to the common name exclusion list.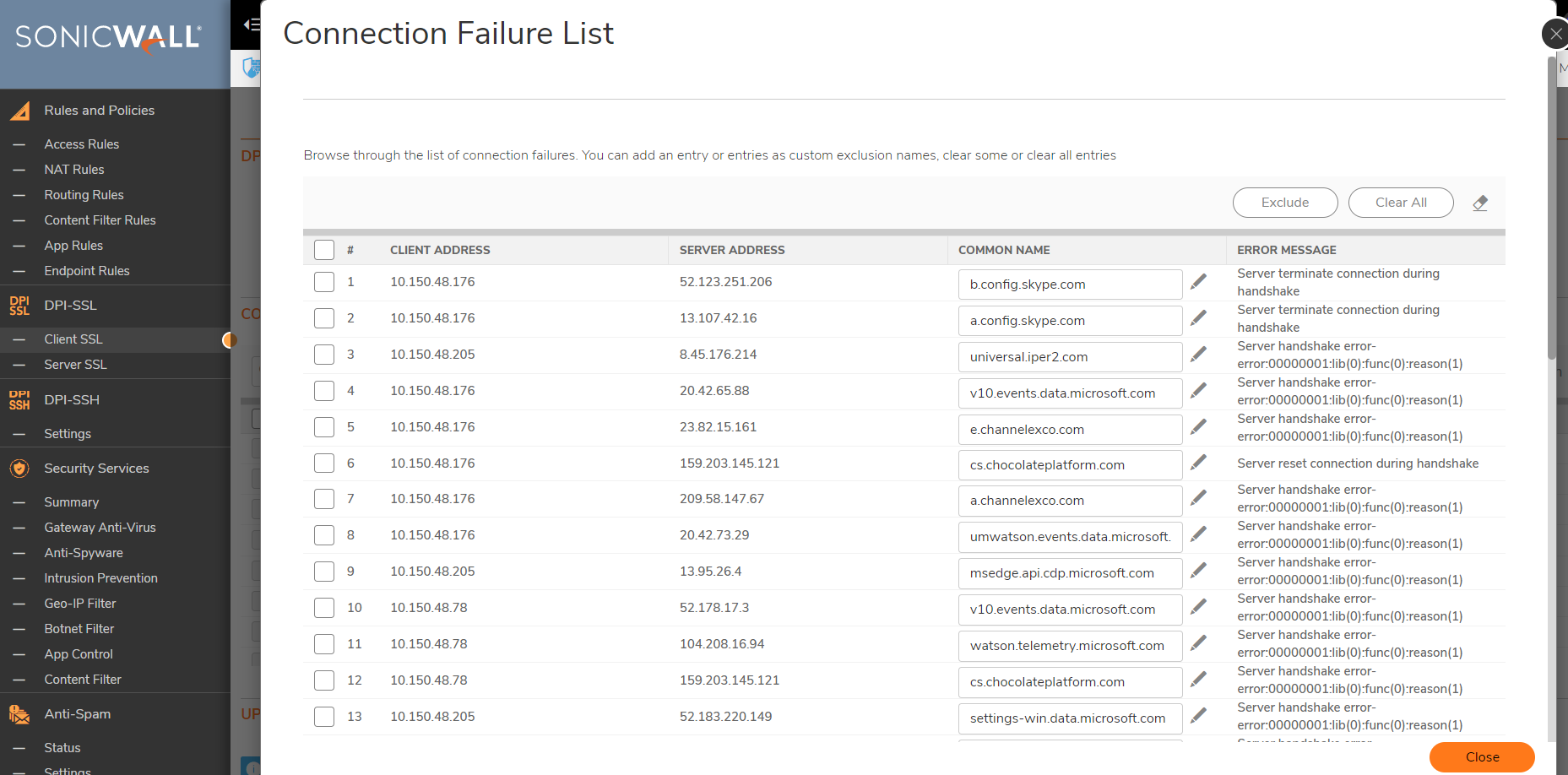
Connection Limits
Websites like Google, Yahoo and others begin to put more importance towards customer privacy. Most companies are moving towards HTTPS services while others offer a choice of both HTTP and HTTPS. On an average more than 50% of network traffic is SSL/TLS and is increasing. With these Changes the connections per user are on the rise. All web browsers use multiple connections per user per page request. Many websites use encryption by default.
The following table shows some average TCP connections per user accessing various sites:
- google.com 8 Yes
- facebook,com 43 Yes
- youtube.com 23 Yes
- yahoo.com 31 Yes
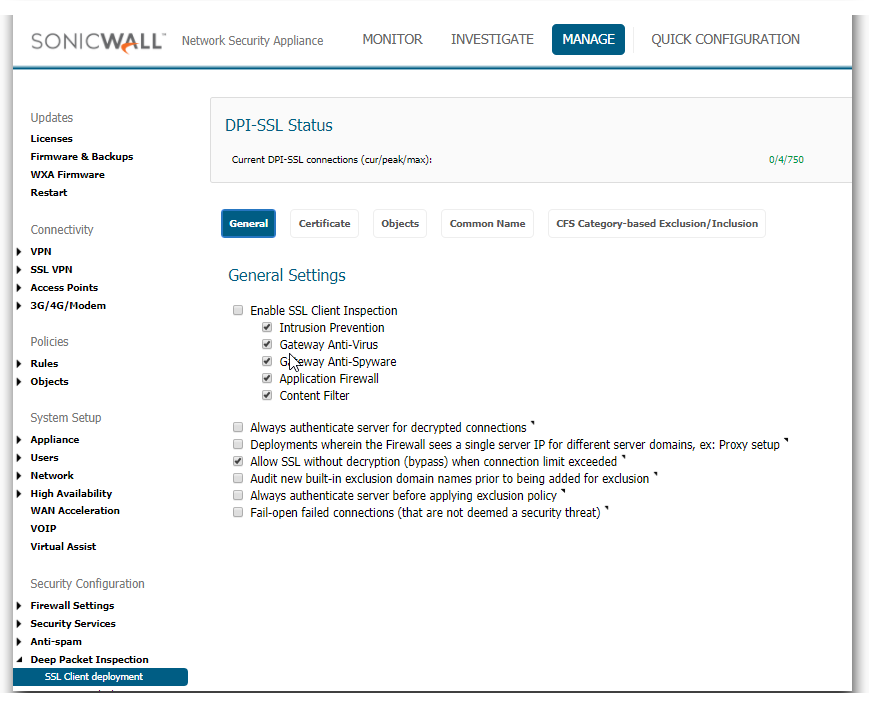
SonicWall's Deep Packet Inspection technology Extends across all applicable HTTPS traffic and SSL based traffic. DPI-SSL is resource intensive, so system resource needs balancing with other functionalities. The max concurrent DPI-SSL connection limit sets an upper limit on the resources allocation to DPI-SSL. Each firewall has a different maximum connection limit. This can be viewed from the Policy | Deep Packet Inspection | SSL Client Deployment. At the top under connection status you can see the maximum connection limit for your device.
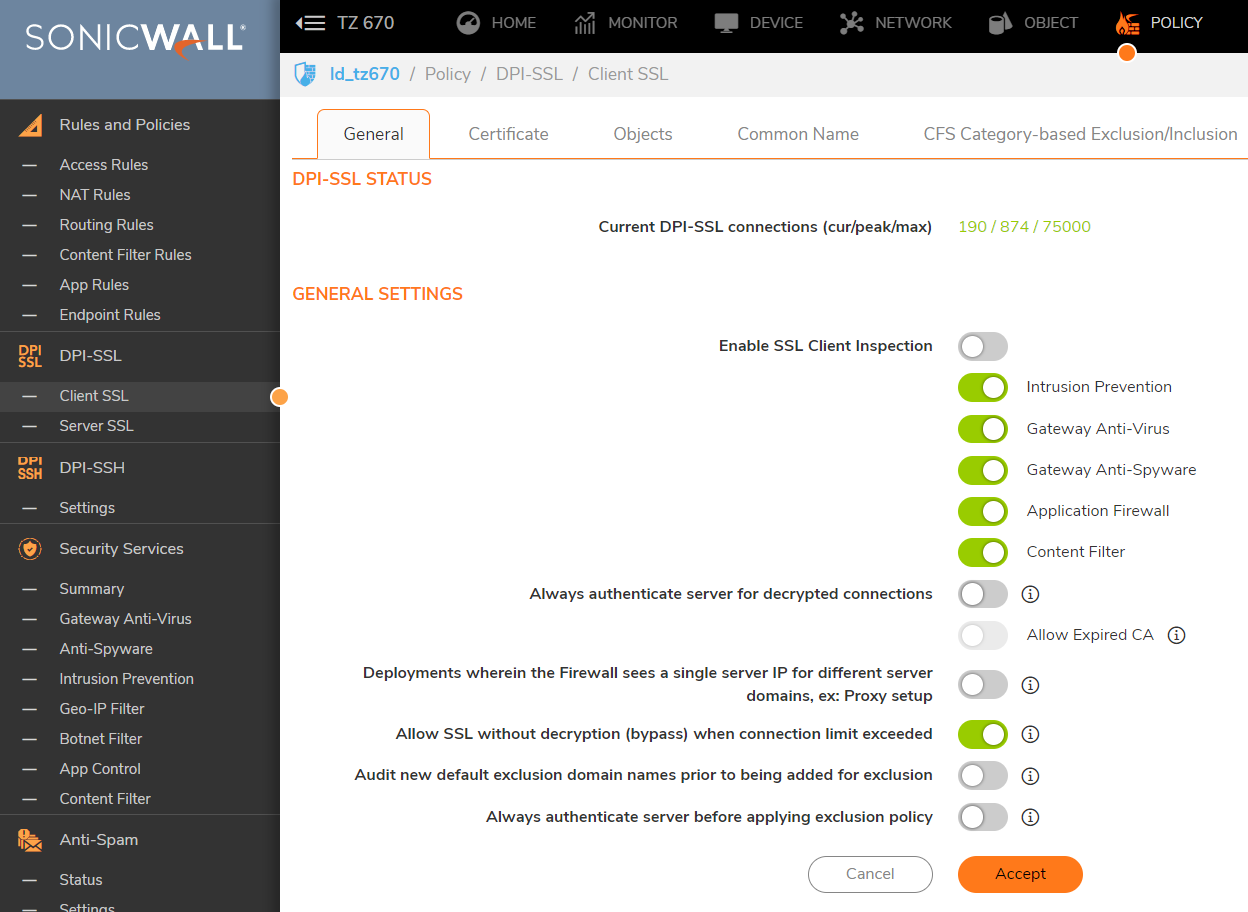
To manage around this it is recommended to exclude trusted traffic from DPI-SSL this can be done in two ways.
The first way is to exclude based on Object in Policy | Deep Packet Inspection | SSL Client Deployment | Objects
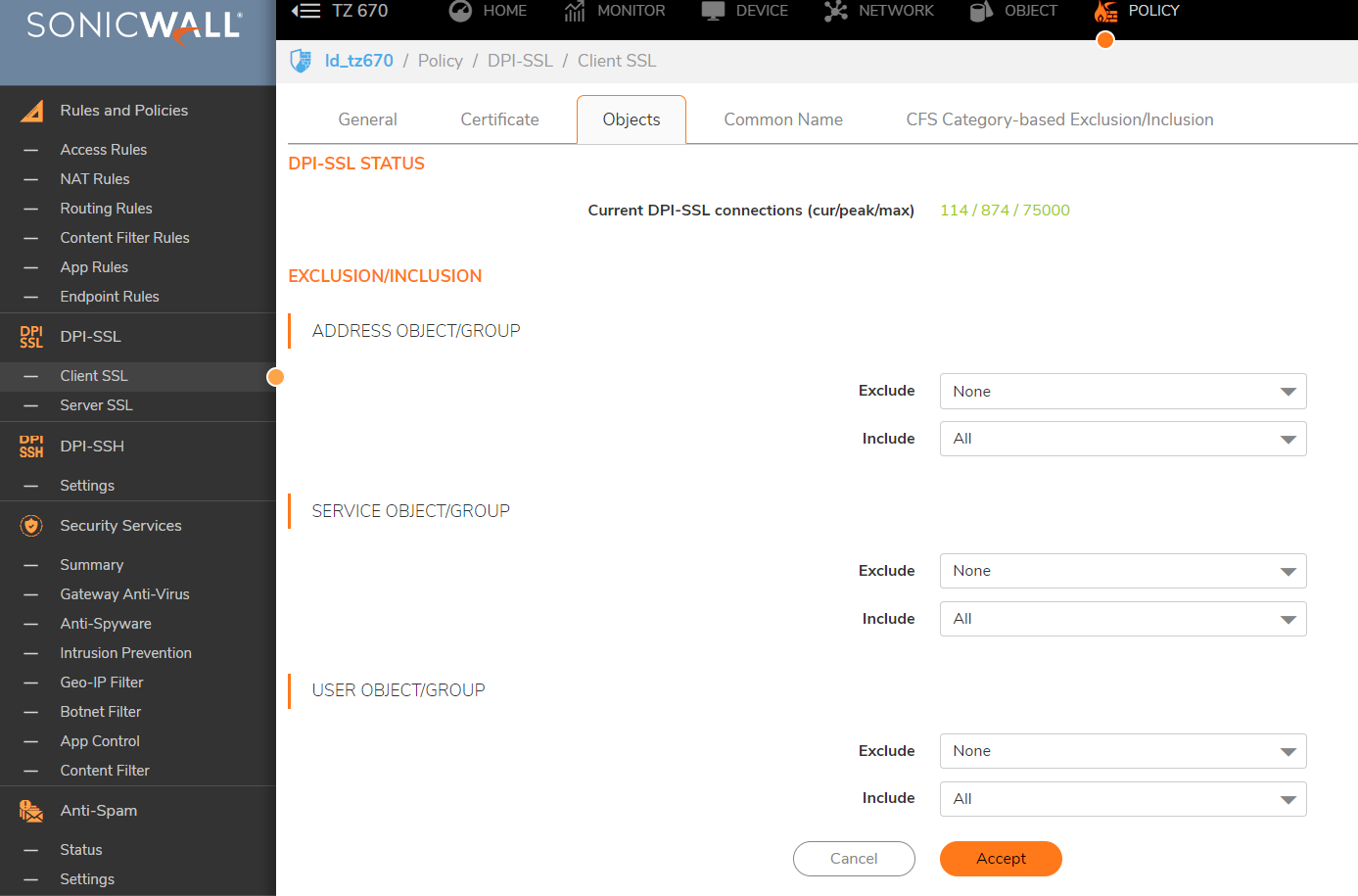
You can include and exclude based on Address/Service/User objects.
See Also:
The second way is to exclude based on CFS Category.
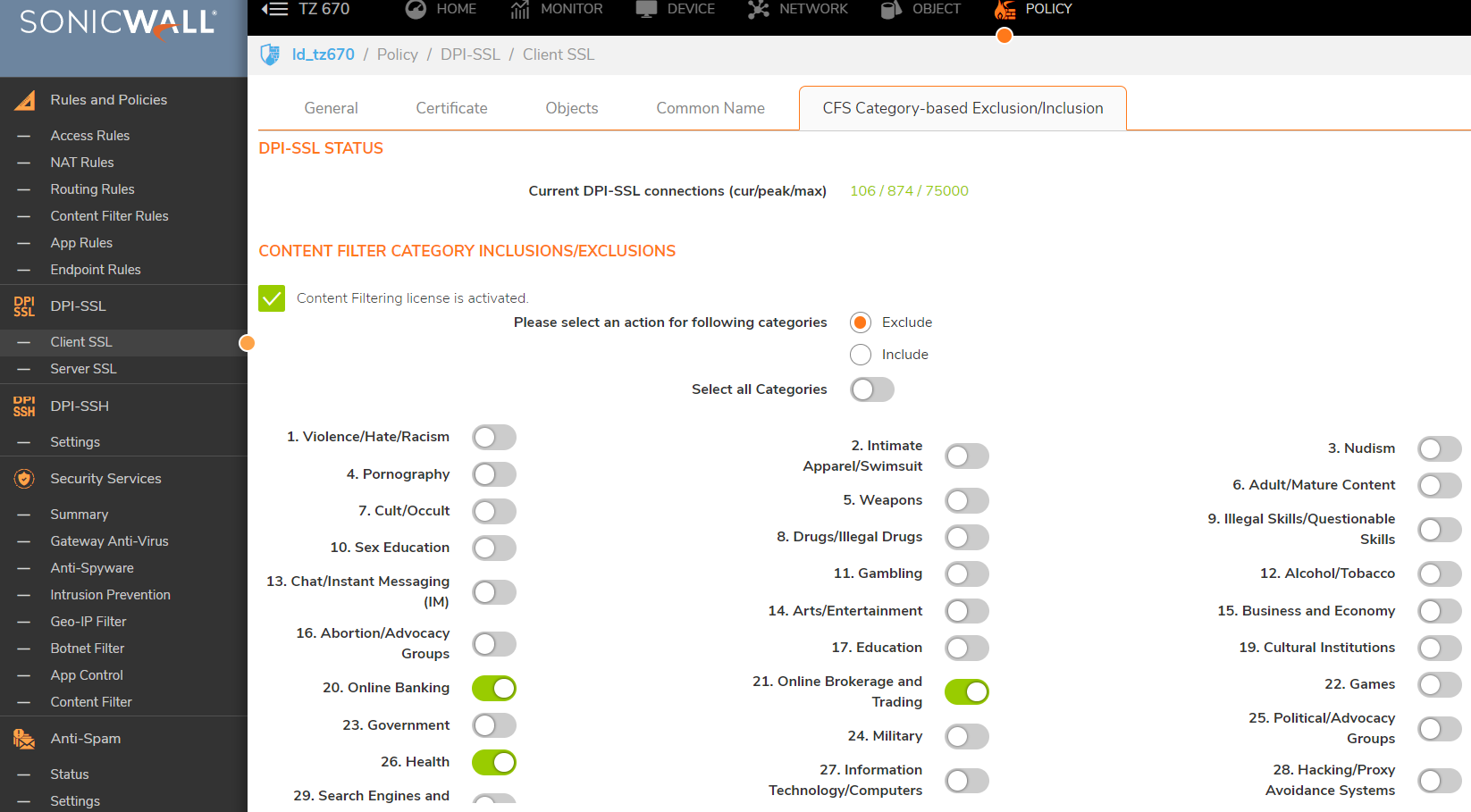
This is done from Policy | Deep Packet Inspection | SSL Client Deployment | CFS Category-based Exclusion/Inclusion
On this screen you can set whether you want to include or exclude based on Content Filter categories. And then select those categories. It is recommended to exclude the Online Banking and Health categories due to privacy concerns.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
When accessing a website you get an error stating your connection is not secure.

This is caused by not having the DPI-SSL resigning Certificate installed as a Trusted Root Certification Authority on this device.
You need to download the SonicWall DPI SSL certificate from the appliance interface in Manage | Deep Packet Inspection | SSL Client Deployment | Certificates 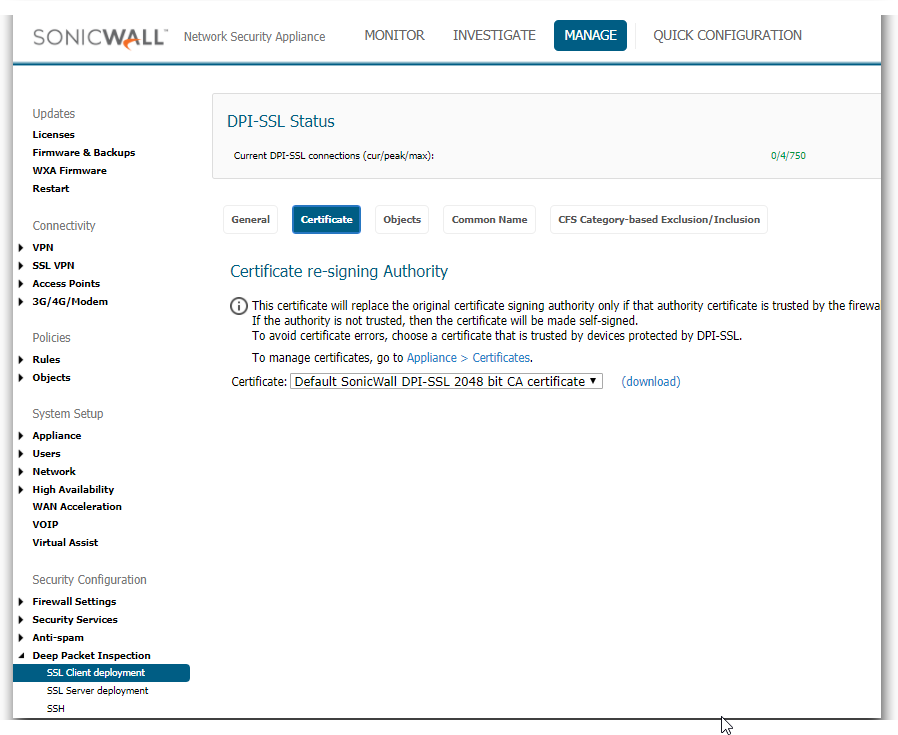
Internet Explorer/Chrome: Open Internet Explorer. Go to Tools | Internet Options, click the Content tab and click Certificates. Click the Trusted Root Certification Authorities tab and click Import. The Certificate Import Wizard will guide you through importing the certificate
Firefox: Go to Tools | Options, click the Advanced tab and then the Certificates Tab. Select the Authorities tab, and click Import.

Select the certificate file, make sure the Trust this CA to identify websites check box is selected, and click OK.
When accessing a website you get an error Secure Connection Failed(SEC_ERROR_INADEQUATE_KEY_USAGE)

This is caused when the certificate used doesn't have resigning authority from your CA.
This process can be automated in a Windows Domain Environment using Group Policy. You can see the following article: Distributing the Default SonicWall DPI-SSL CA certificate to client computers using Group Policy
Certificate Errors in Browsers - Self-signed certificate
When Client DPI-SSL is enabled, accessing a few websites may cause the browser to display a certificate error. The specific error message could vary with different browsers. In Firefox it would show invalid security certificate and in Chrome the error message is Invalid Certificate Authority. In the certificate details, we would see the certificate is self-signed.
This error occurs rarely with some websites. This error occurs when the server sends a certificate signed by a CA not in the SonicWall's certificate store forcing the SonicWall to re-sign the certificate as self-signed certificate.
To resolve this issue, export the Root CA certificate of the website (either from a PC not intercepted by DPI-SSL or by disabling DPI-SSL temporarily) and import it into the SonicWall certificate store.
This is done from Manage | Appliance | Certificates
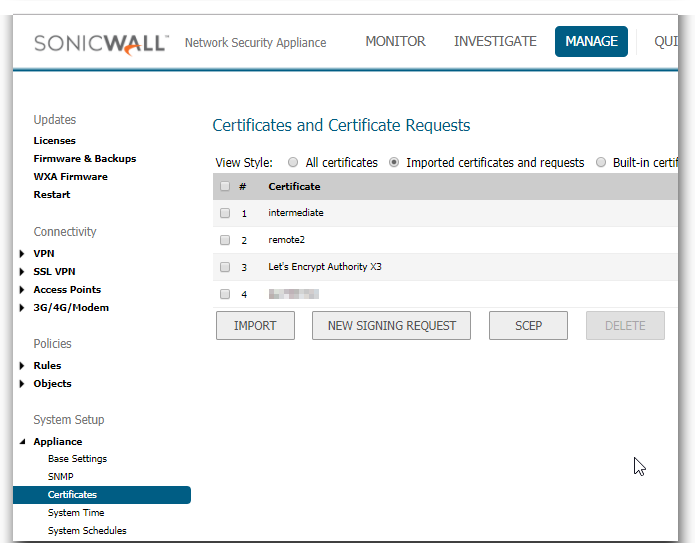
By default, when a server presents a certificate which cannot be verified by Client DPI-SSL because the Root CA is not present in its certificate store, it re-writes the certificate as a self-signed certificate. This default behavior of the SonicWall can be changed.
Go to the diag page of the SonicWall by entering http://<deviceip>/diag.html. Under the DPI-SSL section, enable the option Block connections to sites with untrusted certificates. Click on Accept to save the change.
 CAUTION: This is not recommended.
CAUTION: This is not recommended.
Client DPI-SSL and non-browser applications
There are certain applications which do not work when Client DPI-SSL is enabled though the SonicWall Client DPI-SSL CA certificate is imported into the certificate store. This is because such applications and/or websites do certificate pinning or SSL pinning. Certificate pinning is an extra check to make sure that the server the client is connecting to is really who they say they are, and not an impostor.
These applications include:
- Windows Update
- DropBox Client App
- Apple App Store
- Logmein Client
- Google Drive Client App
To allow these applications to work what we need to do is white list these certificates from DPI-SSL. When you add a certificate to this white list is will exclude any address that uses that certificate from being scanned by any of the DPI-SSL engines. We maintain a built in certificate white list to prevent connection issues with common websites.
To view this list you will need to access Manage | Deep Packet Inspection | SSL Client Deployment | Common Name
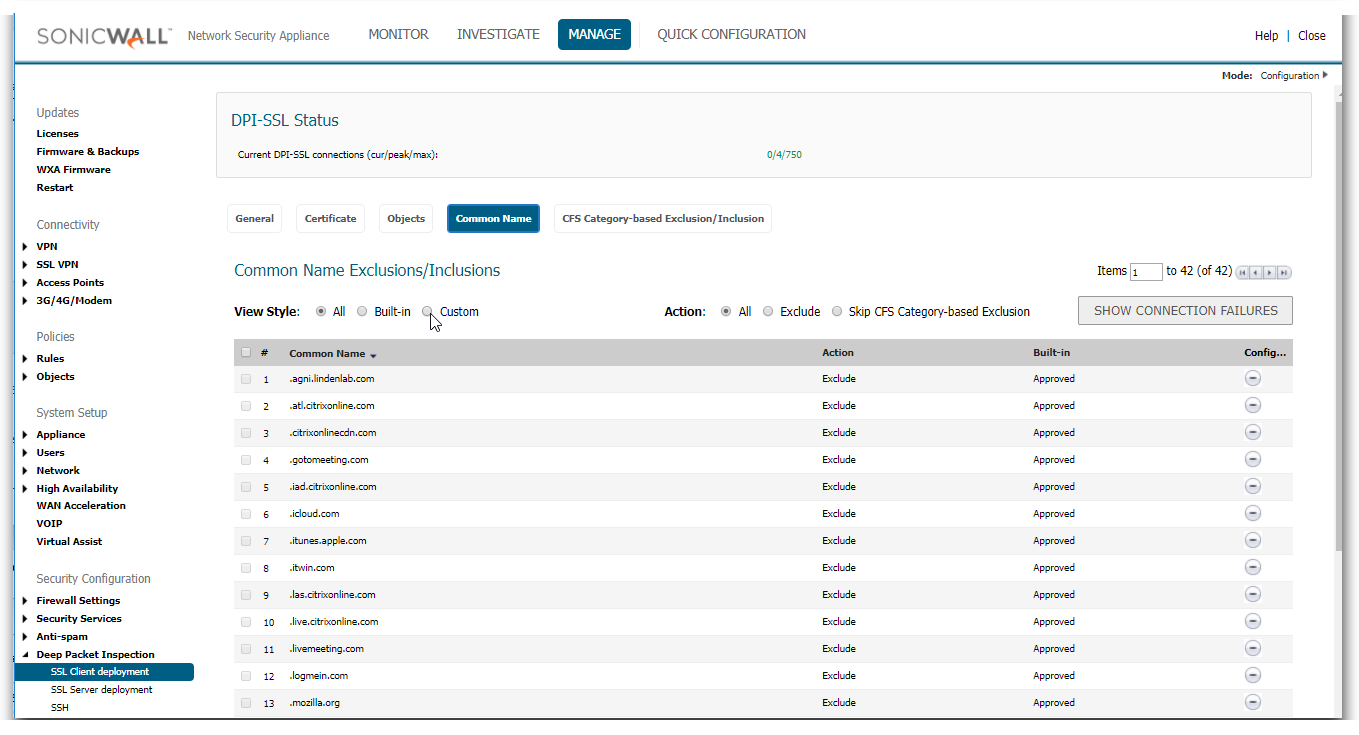
You can add exceptions in two ways.
The first way is if you know the common name of the certificate you want to exclude. You click on add, and you can add the common names of the certificates you want to exclude.
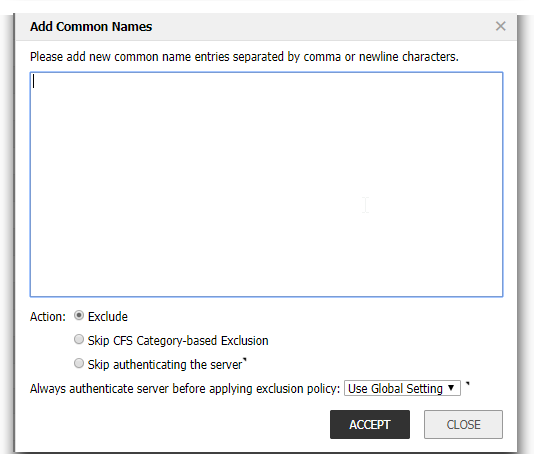
The second way is when you click on Show Connection Failures
On this screen it will present you a list of websites that have had SSL connection failures while DPI-SSL is enabled. You can check the box next to any of these and click exclude to add them to the common name exclusion list.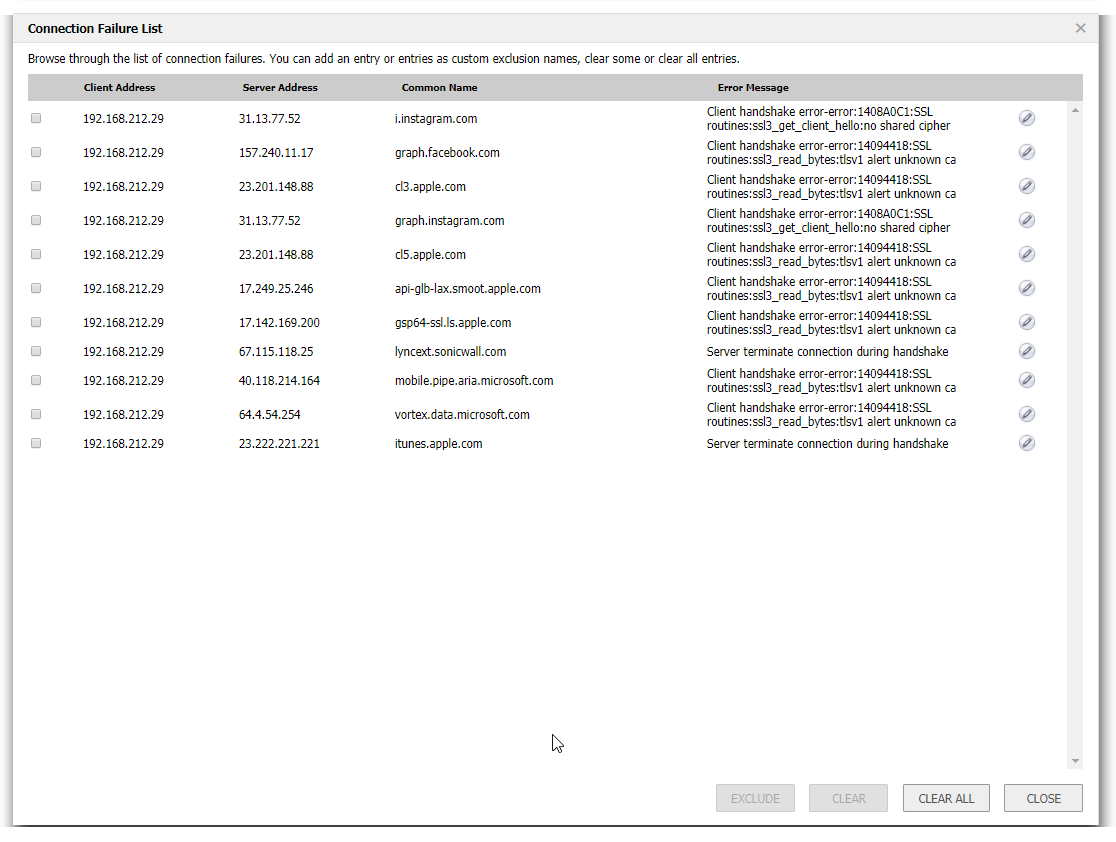
Connection Limits
Websites like Google, Yahoo and others begin to put more importance towards customer privacy. Most companies are moving towards HTTPS services while others offer a choice of both HTTP and HTTPS. On an average more than 50% of network traffic is SSL/TLS and is increasing. With these Changes the connections per user are on the rise. All web browsers use multiple connections per user per page request. Many websites use encryption by default.
The following table shows some average TCP connections per user accessing various sites:
- google.com 8 Yes
- facebook,com 43 Yes
- youtube.com 23 Yes
- yahoo.com 31 Yes
SonicWall's Deep Packet Inspection technology Extends across all applicable HTTPS traffic and SSL based traffic. DPI-SSL is resource intensive, so system resource needs balancing with other functionalities. The max concurrent DPI-SSL connection limit sets an upper limit on the resources allocation to DPI-SSL. Each firewall has a different maximum connection limit. This can be viewed from the Manage | Deep Packet Inspection | SSL Client Deployment. At the top under connection status you can see the maximum connection limit for your device.
To manage around this it is recommended to exclude trusted traffic from DPI-SSL this can be done in two ways.
The first way is to exclude based on Object in Manage | Deep Packet Inspection | SSL Client Deployment | Objects
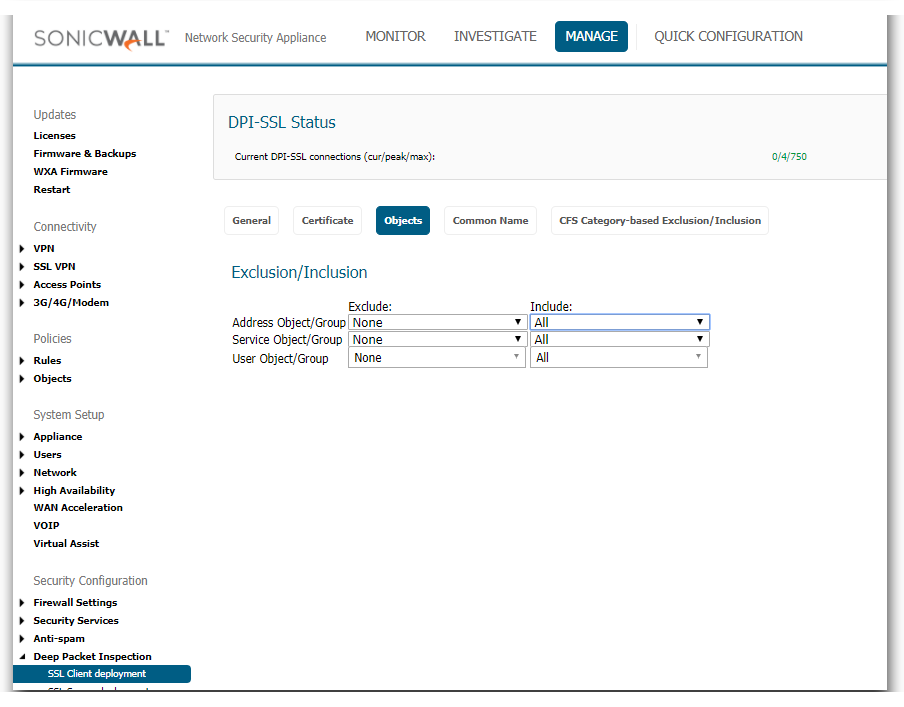
You can include and exclude based on Address/Service/User objects.
See Also:
How to Configure service objects
Understanding Address Objects in SonicOS
The second way is to exclude based on CFS Category.
This is done from Manage | Deep Packet Inspection | SSL Client Deployment | CFS Category-based Exclusion/Inclusion
On this screen you can set whether you want to include or exclude based on Content Filter categories. And then select those categories. It is recommended to exclude the Online Banking and Health categories due to privacy concerns.
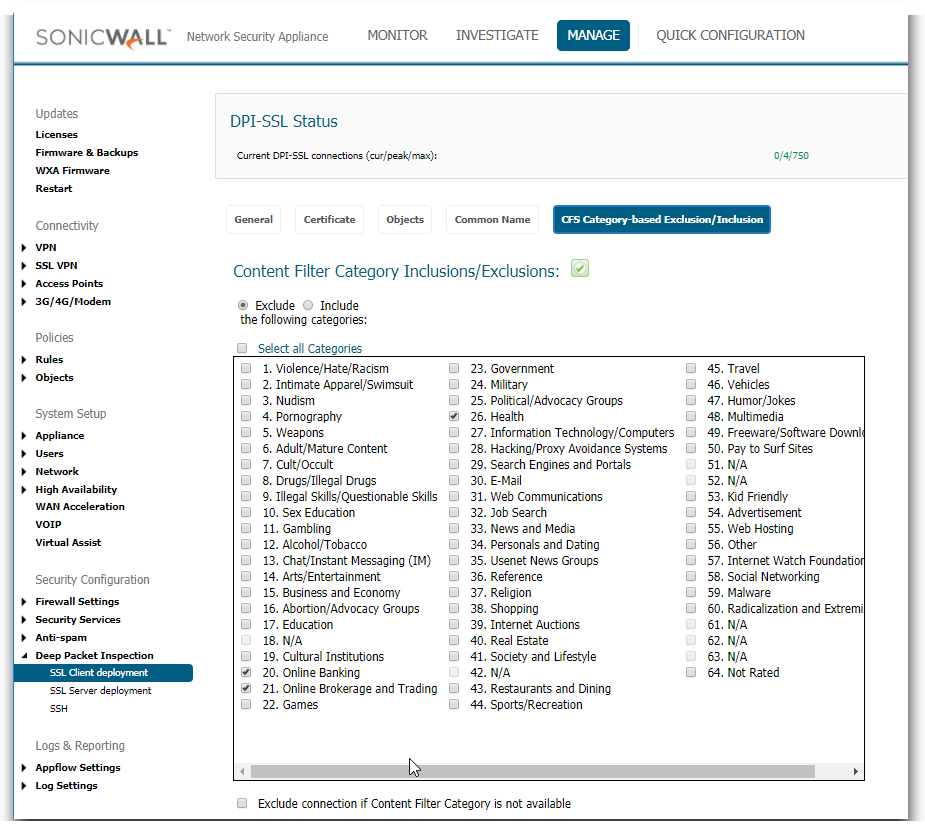
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
When accessing a website you get an error stating your connection is not secure.

This is caused by not having the DPI-SSL resigning Certificate installed as a Trusted Root Certification Authority on this device.
You need to download the SonicWall DPI SSL certificate from the appliance interface in DPI-SSL | Client SSL | Certificates 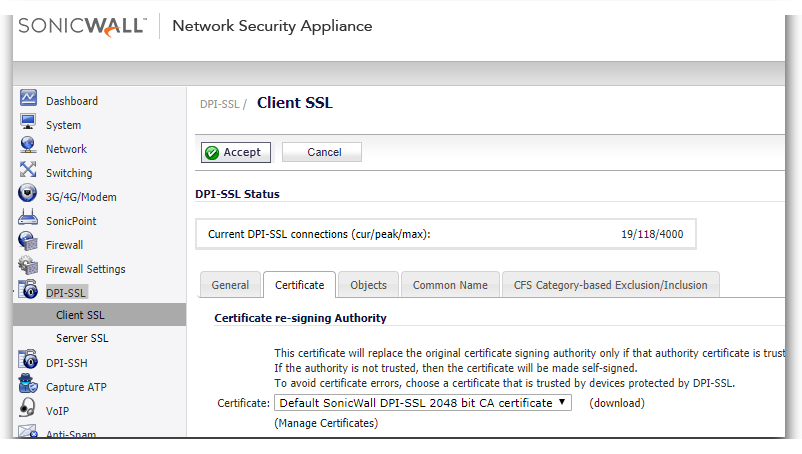
Internet Explorer/Chrome: Open Internet Explorer. Go to Tools | Internet Options, click the Content tab and click Certificates. Click the Trusted Root Certification Authorities tab and click Import. The Certificate Import Wizard will guide you through importing the certificate
Firefox: Go to Tools | Options, click the Advanced tab and then the Certificates Tab. Select the Authorities tab, and click Import.

Select the certificate file make sure the Trust this CA to identify websites check box is selected, and click OK.
When accessing a website you get an error Secure Connection Failed(SEC_ERROR_INADEQUATE_KEY_USAGE)

This is caused when the certificate used doesn't have resigning authority from your CA.
This process can be automated in a Windows Domain Environment using Group Policy. You can see the following article: Distributing the Default SonicWall DPI-SSL CA certificate to client computers using Group Policy
Certificate Errors in Browsers - Self-signed certificate
When Client DPI-SSL is enabled, accessing a few websites may cause the browser to display a certificate error. The specific error message could vary with different browsers. In Firefox it would show invalid security certificate and in Chrome the error message is Invalid Certificate Authority. In the certificate details, we would see the certificate is self-signed.
This error occurs rarely with some websites. This error occurs when the server sends a certificate signed by a CA not in the SonicWall's certificate store forcing the SonicWall to re-sign the certificate as self-signed certificate.
To resolve this issue, export the Root CA certificate of the website (either from a PC not intercepted by DPI-SSL or by disabling DPI-SSL temporarily) and import it into the SonicWall certificate store.
This is done from System | Certificates | Import
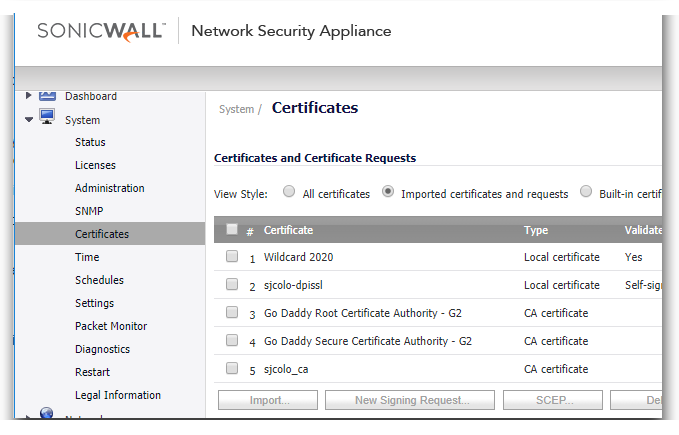
By default, when a server presents a certificate which cannot be verified by Client DPI-SSL because the Root CA is not present in its certificate store, it re-writes the certificate as a self-signed certificate. This default behavior of the SonicWall can be changed.
Go to the diag page of the SonicWall by entering http://<deviceip>/diag.html. Under the DPI-SSL section, enable the option Block connections to sites with untrusted certificates
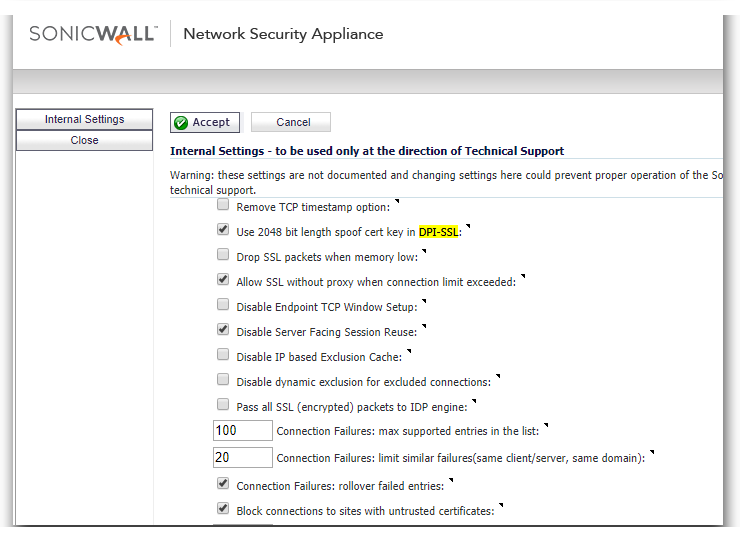
Click on Accept to save the change.
 CAUTION: This is not recommended.
CAUTION: This is not recommended.
Client DPI-SSL and non-browser applications
There are certain applications which do not work when Client DPI-SSL is enabled though the SonicWall Client DPI-SSL CA certificate is imported into the certificate store. This is because such applications and/or websites do certificate pinning or SSL pinning. Certificate pinning is an extra check to make sure that the server the client is connecting to is really who they say they are, and not an impostor.
Here are some of such applications:
- Windows Update
- DropBox Client App
- Apple App Store
- Logmein Client
- Google Drive Client App
To allow these applications to work what we need to do is white list these certificates from DPI-SSL. When you add a certificate to this white list is will exclude any address that uses that certificate from being scanned by any of the DPI-SSL engines. We maintain a built in certificate white list to prevent connection issues with common websites.
To view this list you will need to access DPI-SSL | Client SSL | Common Name
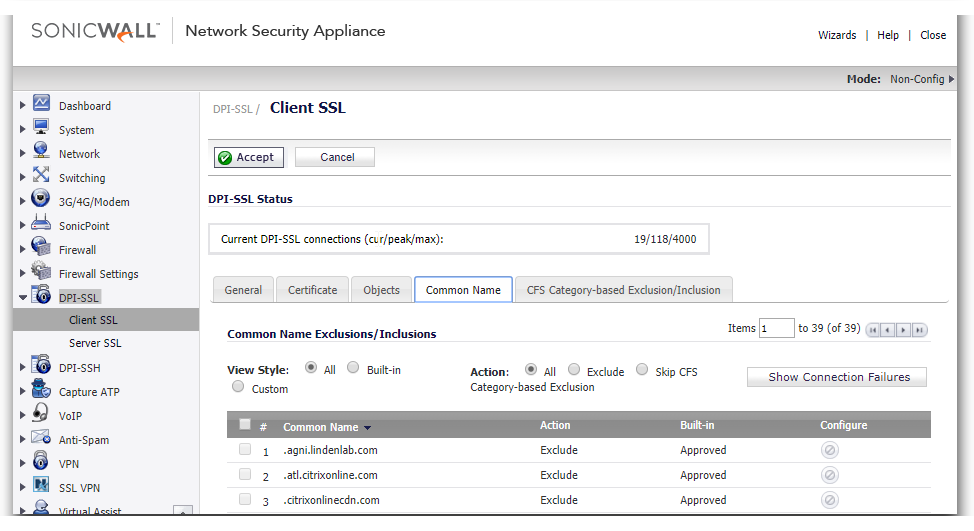
You can add exceptions in two ways.
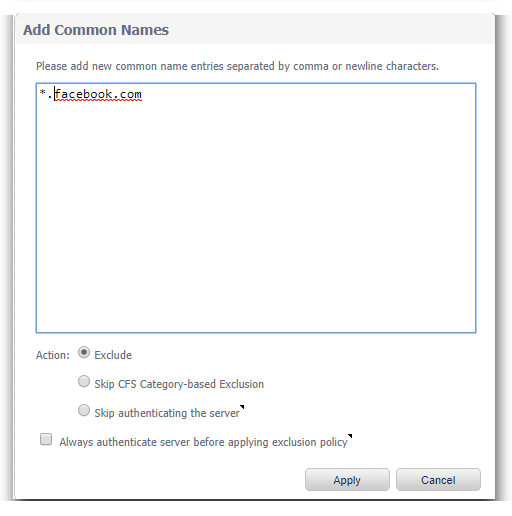
The first way is if you know the common name of the certificate you want to exclude. You click on add, and you can add the common names of the certificates you want to exclude.
The second way is when you click on Show Connection Failures
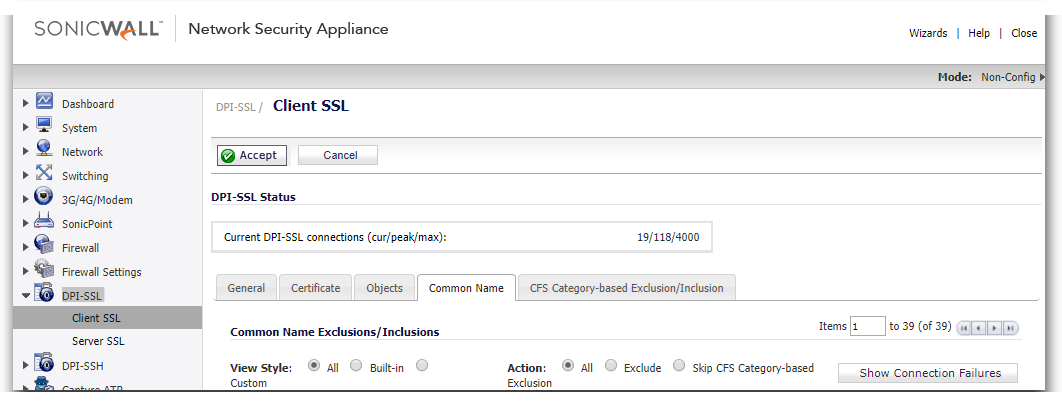
On this screen it will present you a list of websites that have had SSL connection failures while DPI-SSL is enabled. You can check the box next to any of these and click exclude to add them to the common name exclusion list.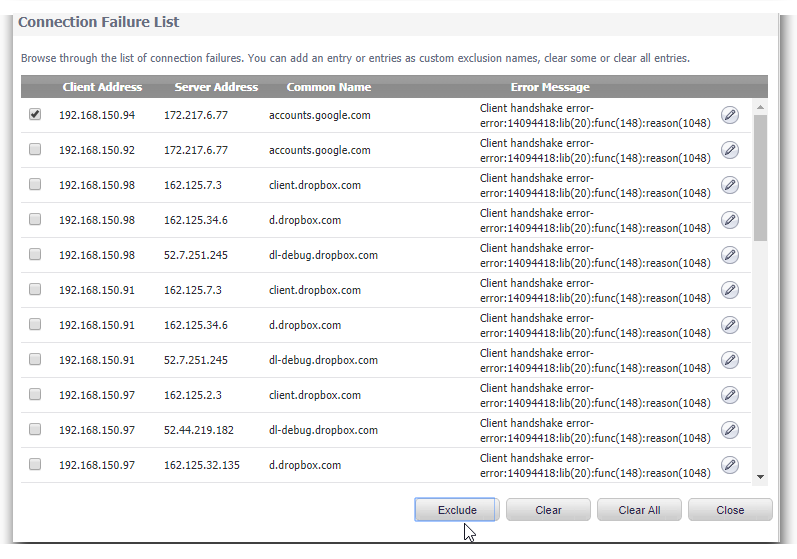
Connection Limits
Websites like Google, Yahoo and others begin to put more importance towards customer privacy. Most companies are moving towards HTTPS services while others offer a choice of both HTTP and HTTPS. On an average more than 50% of network traffic is SSL/TLS and is increasing. With these Changes the connections per user are on the rise. All web browsers use multiple connections per user per page request. Many websites use encryption by default.
The following table shows some average TCP connections per user accessing various sites:
- google.com 8 Yes
- facebook,com 43 Yes
- youtube.com 23 Yes
- yahoo.com 31 Yes
SonicWall's Deep Packet Inspection technology Extends across all applicable HTTPS traffic and SSL based traffic. DPI-SSL is resource intensive, so system resource needs balancing with other functionalities. The max concurrent DPI-SSL connection limit sets an upper limit on the resources allocation to DPI-SSL. Each firewall has a different maximum connection limit. This can be viewed from the DPI-SSL | Client SSL. At the top under connection status you can see the maximum connection limit for your device.
To manage around this it is recommended to exclude trusted traffic from DPI-SSL this can be done in two ways.
The first way is to exclude based on Object in DPI-SSL | Client SSL | Objects
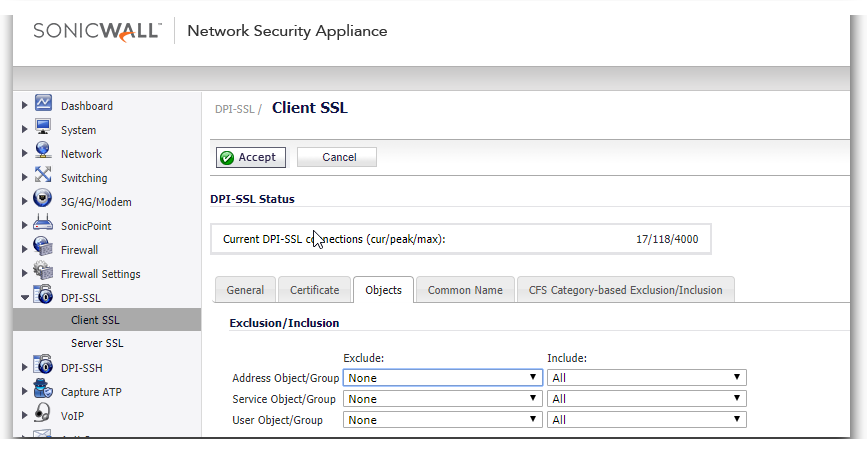
You can include and exclude based on Address/Service/User objects.
See Also:
How to Configure service objects
Understanding Address Objects in SonicOS
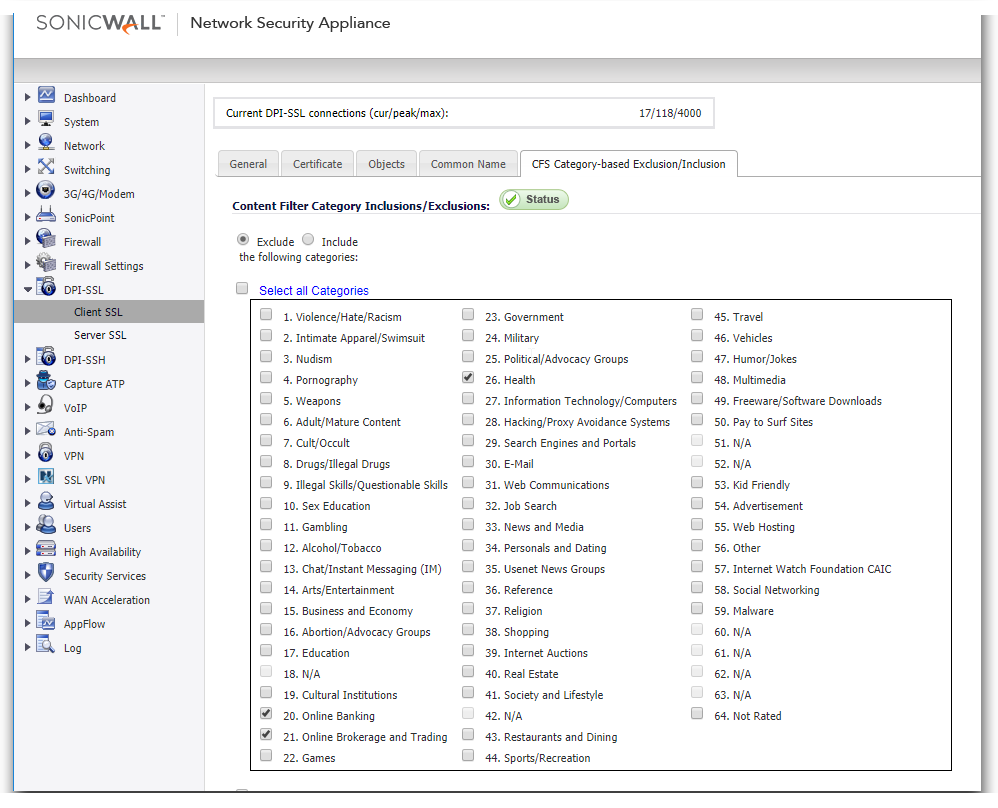
The second way is to exclude based on CFS Category.
This is done from DPI-SSL | Client SSL | CFS Category-based Exclusion/Inclusion
On this screen you can set whether you want to include or exclude based on Content Filter categories. And then select those categories. It is recommended to exclude the Online Banking and Health categories due to privacy concerns.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > SonicWall NSA Series > DPI-SSL
- Firewalls > SonicWall SuperMassive 9000 Series > DPI-SSL
- Firewalls > TZ Series > DPI-SSL






 YES
YES NO
NO