-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Configuring IPFIX w/ Extensions Flow Reporting (SonicOS 5.8.1 and above)



Description
Configuring IPFIX w/ Extensions Flow Reporting (SonicOS 5.8.1 and above)
Resolution
Configuring SNMP on the UTM appliance
1. To configure SNMP, log into the UTM appliance. Browse to System | Administration.
2. Enable SNMP. Click Configure.

4. Ensure that SNMP is enabled on the interface that SonicWall Scrutinizer will communicate with. In this example, SNMP will be enabled on the X0 LAN interface. For deployments where the Netflow collector is reached over a VPN tunnel, SNMP must be allowed from the Netflow collector to the UTM appliance using Access Rules.
 Configuring External Flow Reporting
Configuring External Flow Reporting
1. Browse to Log | Flow Reporting. Enable “Report to EXTERNAL flow collector”. Optionally, you can turn on Flow Reporting and Visualization (Internal Reporting) for access to the App Flow Monitor in the UTM appliance.
2. SonicWall Scrutinizer supports collection of IPFIX (Netflow version-10) with Extensions. Advanced SonicWall-specific reporting is available only with IPFIX with Extensions. Set the “External flow reporting type” to “IPFIX with Extensions”.
3. Enter the IP of the SonicWall Scrutinizer server. The default port number for Netflow reporting is UDP/2055. Customize this based on the port selected when SonicWall Scrutinizer was installed.
4. The “Source IP to use for collector on a VPN tunnel” should be configured if the SonicWall Scrutinizer collector is accessed over a VPN tunnel. The IP entered will the source IP of the Netflow traffic sent to SonicWall Scrutinizer. For example, the X0 IP of the UTM appliance can be used. SNMP must be allowed from SonicWall Scrutinizer to the IP entered into this text field.
5. Ensure that both the “Send templates at regular intervals” and “Send static flows at regular intervals” are checked. This ensures that SonicWall Scrutinizer always receives up-to-date templates and static flows from the UTM appliance.
6. Ensure that all of the tables are selected for the following three drop-down menus:
“Send static flows for the following tables”
“Send dynamic flows for the following tables”
“Include following additional reports via IPFIX”
7. The recommended “Flow reporting mode” is “Realtime with bulk”. Realtime with bulk allows the firewall to send multiple Netflow records per Netflow packet.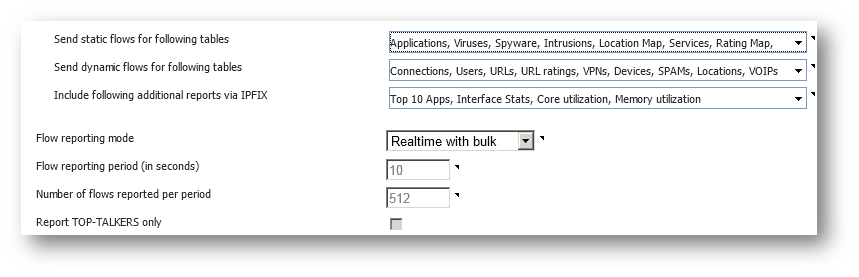
- “Report flows on connection OPEN” will report a flow when the connection is opened. This is enabled by default. Not reporting on connection open will result in potential inaccurate reporting to an external collector. This would be especially noticeable when a flow doesn’t close for a long period of time, for example during a large download.
- “Report flows on threat detection” will report a flow when a threat is detected in the flow. This is enabled by default.
- “Report flows on application detected” will report a flow when an application is detected by the DPI engine.
- “Report flows on user detection” will report a flow when the flow is identified for a logged-in user.
- “Report flows on VPN tunnel detection” will report a flow when the flow is identified as being used over a VPN tunnel.
- “Reporting flows on Kilobytes exchanged” will report a flow when the set number of Kilobytes has been transferred on a connection. This means a flow will be reported multiple times throughout the life of the flow (each time the set number of Kilobytes has been transferred). It is recommended to turn on this option. Not using this setting, or setting it too high or too low will potentially result in inaccurate (understated or overstated) reports, or spikes in reporting where usage appears too high for a short period of time. A good baseline is 100 Kilobytes (the default). The “Report ONCE” option will cause the flow to only be reported one time on Kilobytes exchanged. Instead of reporting every 100 Kilobytes, it’ll report once 100 Kilobytes has been transferred. In most situations, this option should be disabled, as reporting will be affected.
- “Report flows on connection CLOSE” will report a flow when the connection has closed. This is enabled by default.
- “Report DROPPED flows” will report a flow when the connection is dropped. This is enabled by default.
- “Skip reporting of STACK flows (connections)” is enabled by default, and does not report connections generated by the system stack. Disabling this will result in additional reported flows to the external collector.
- “Include following URL types” will report URLs accessed with the selected file types. By default, all of the file types listed in the drop-down menu are enabled.
After making all desired changes, the unit requires a reboot. Browse to System | Restart. Click the Restart button to reboot the appliance.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO