-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Configuring Aggressive Mode Site to Site VPN when a Site has Dynamic WAN Public IP address



Description
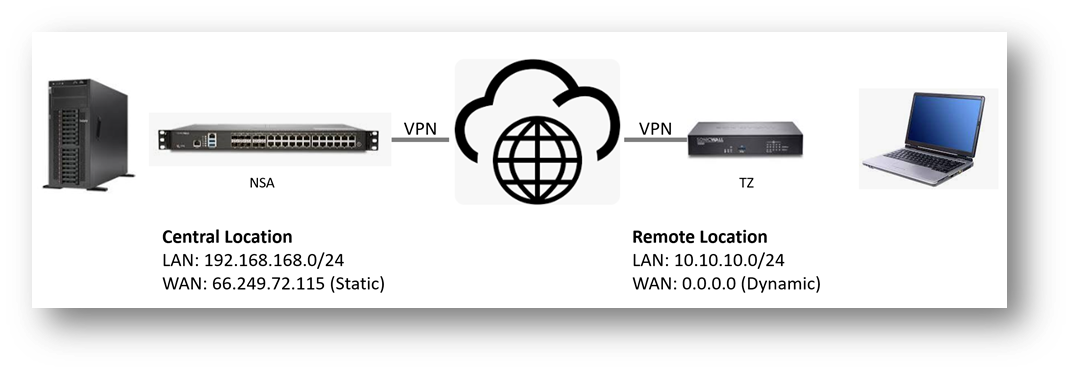
Configuring a Site to Site VPN on the central location (Static WAN IP address)
- Central location network configuration
- LAN Subnet: 192.168.168.0
- Subnet Mask: 255.255.255.0
- WAN IP: 66.249.72.115
- Local IKE ID SonicWall Identifier: Chicago (This could be any string except it has to match the remote location VPN's Peer IKE ID SonicWall Identifier)
 CAUTION: The IP Address can be dynamic but it should always be Public.
CAUTION: The IP Address can be dynamic but it should always be Public.
Private IP Addresses on WAN cause a Double NAT Effect that is unpredictable due to the uncertainty of the ISP Setup of the NAT Layers - this is why in certain scenarios VPNs may not work correctly when a private IP is specified.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
This solution explains the configuration of a Site to Site VPN on SonicWall appliances when a site has a dynamic WAN IP address.
The VPN policy is setup using Aggressive Mode.
Configuring a Site to Site VPN on the Central location
Creating Address Object for remote Site
- Login to the Central location SonicWall appliance.
- Navigate to Objects | Match Objects | Addresses, Click on Add button, enter the following settings.
- Name – Remote Vpn,
- Zone – VPN,
- Type – Network,
- Network – 192.168.168.0
- Netmask – 255.255.255.0
- Click Save.
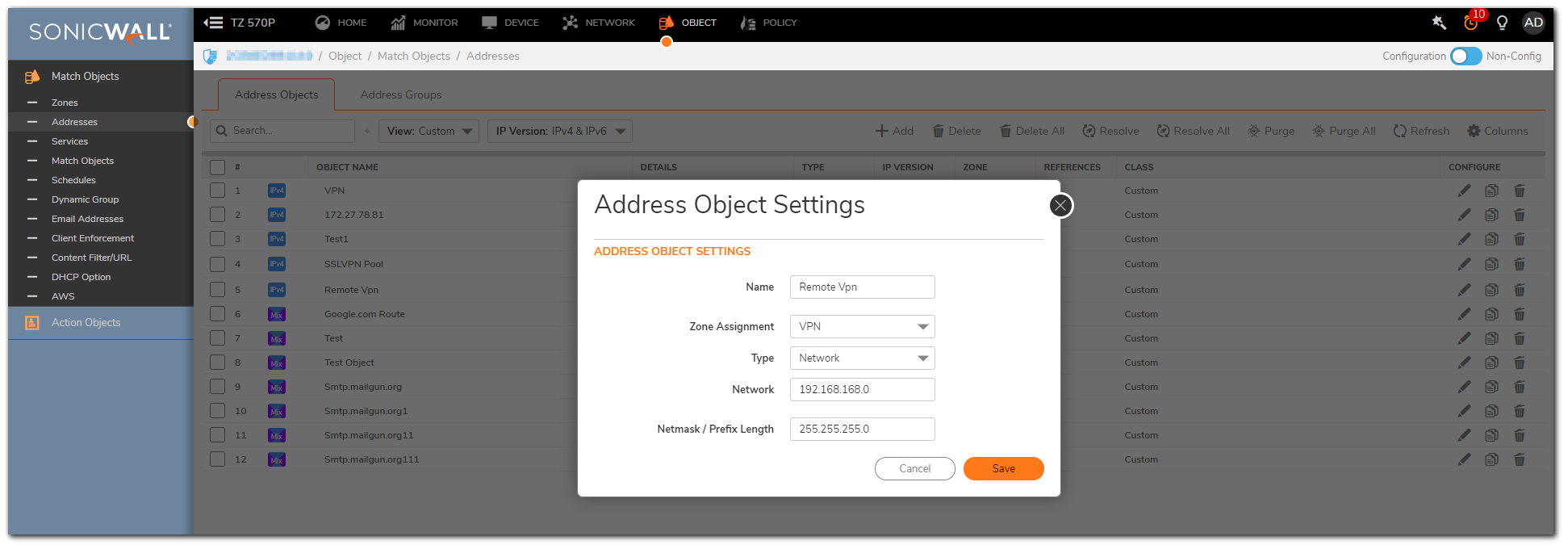
Configuring a VPN Policy
- Navigate to Network|IPSec VPN|Rules and Settings
- Click the Add button under the VPN Policies section. The VPN Policy window pops up.
General Tab
- Select the Authentication method as IKE Using Preshared Secret.
- Name Remote-Site VPN.
- IPSec Primary Gateway Name or Address: 0.0.0.0.
 NOTE: Since the WAN IP address changes frequently, it is recommended to use the 0.0.0.0 IP address as the Primary Gateway.
NOTE: Since the WAN IP address changes frequently, it is recommended to use the 0.0.0.0 IP address as the Primary Gateway. - IPSec Secondary Gateway Name or Address: 0.0.0.0.
- Shared Secret: SonicWall (The Shared Secret would be the same at both SonicWall’s. You can choose any Secret Key, but it should be entered the same on both sites).
- Local IKE ID: SonicWall Identifier -Central_Site(This could be any string except it has to match the remote location VPN's Peer IKE ID SonicWall Identifier)..
- Peer IKE ID: SonicWall Identifier - Remote_Site(This could be any string except it has to match the remote location VPN's Local IKE ID SonicWall Identifier).
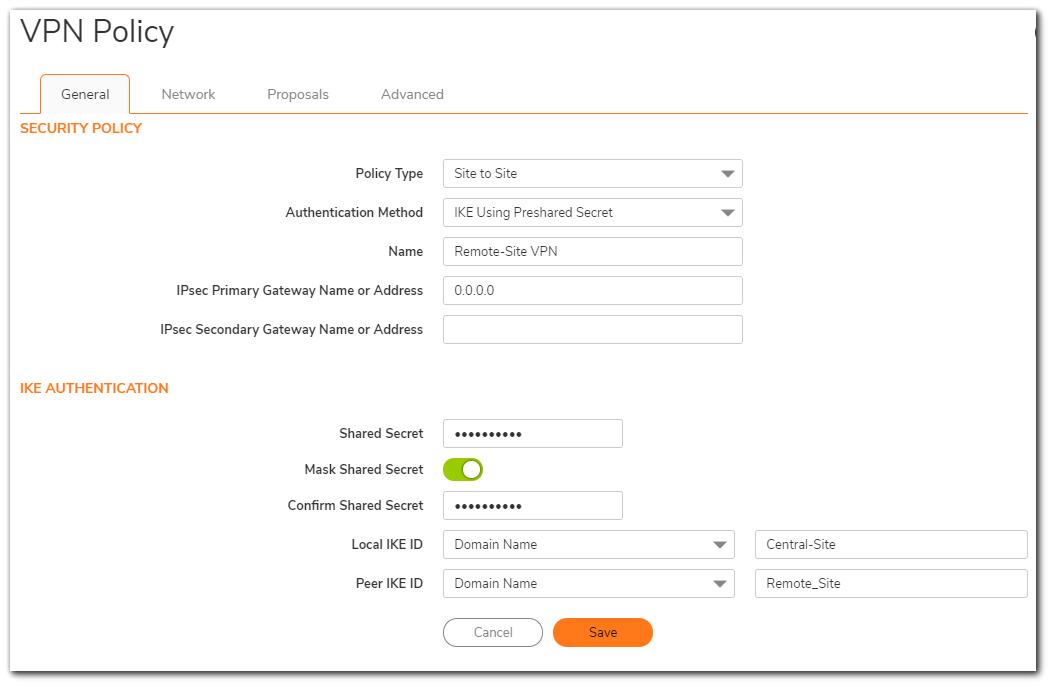
Network Tab
- Select Choose local network from list, and select the Address Object – X0 Subnet (LAN subnet).
- Select Choose destination network the list, and select the Address Object – Remote Vpn.
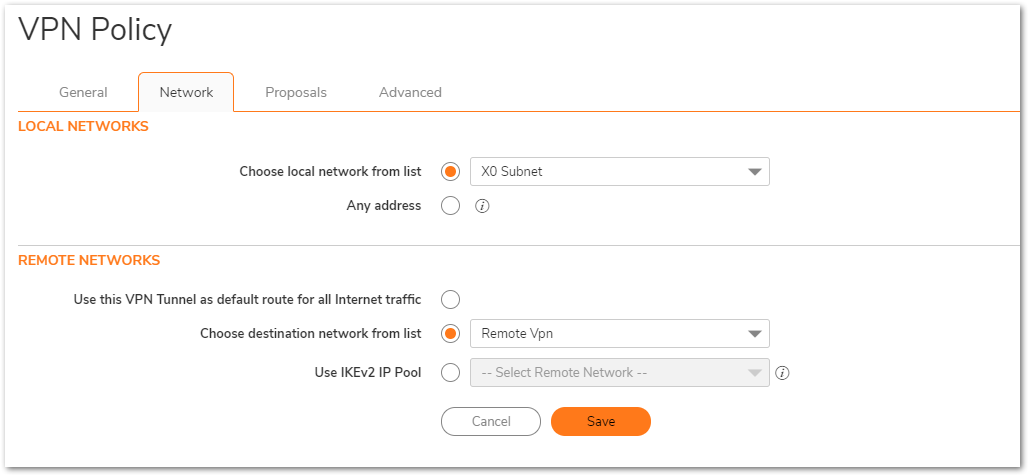
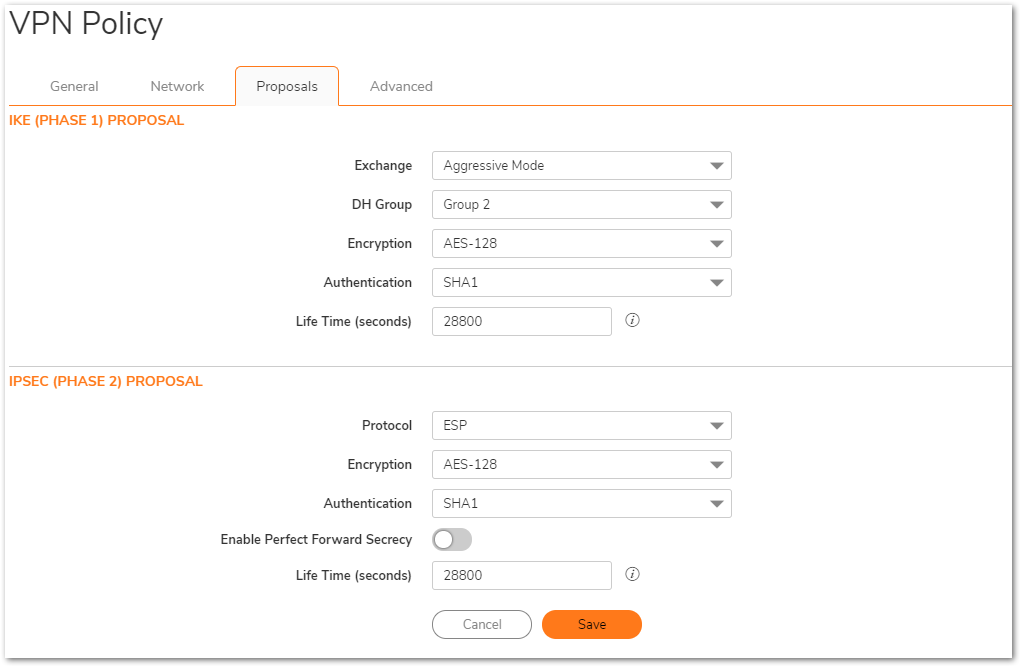
Proposals Tab
- IKE (Phase 1) Proposal.
- Exchange: Aggressive Mode.
- DH Group: Group 2.
- Encryption: AES-128.
- Authentication: SHA1.
- Life Time (seconds): 28800.
- IPSec (Phase 2) Proposal.
- Protocol: ESP
- Encryption: AES-128.
- Authentication: SHA1.
- Enable Perfect Forward Secrecy(not checked).
- Life Time (seconds): 28800.
Advanced tab
- Ensure that the VPN Policy bound to: Zone WAN.
- Click Save.
 NOTE: KeepAlive option will be disabled when Vpn policy configured with Primary Gateway Name or Address as 0.0.0.0.
NOTE: KeepAlive option will be disabled when Vpn policy configured with Primary Gateway Name or Address as 0.0.0.0.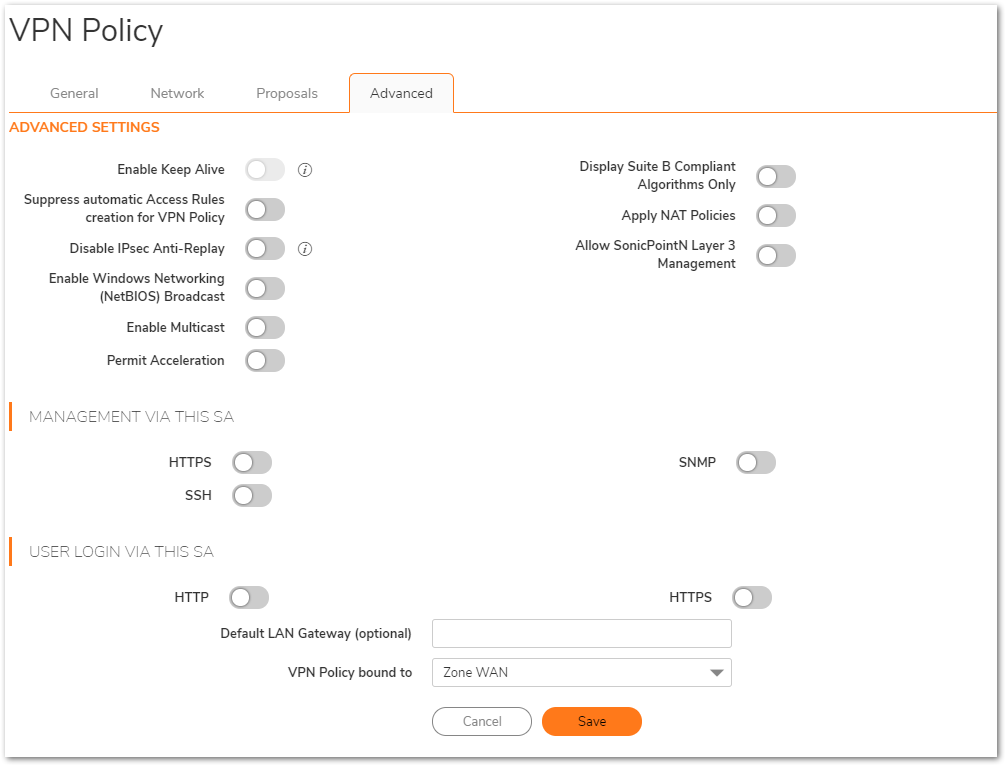
Configuring a Site to Site VPN on the remote location (Dynamic WAN IP address)
Network Configuration
- LAN Subnet: 192.168.168.0
- Subnet Mask: 255.255.255.0.
- WAN IP: DHCP (As this is a Dynamic IP Address).
- Local IKE ID SonicWall Identifier:Remote_Site(This has to match the central location VPN's Peer IKE ID SonicWall Identifier).
Creating Address Object for remote site
- Login to the Remote location SonicWall appliance.
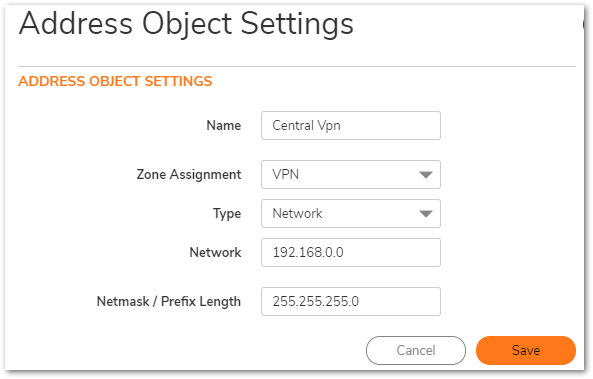
- Navigate to Objects | Match Objects | Addresses, Click on Add button, enter the following settings.
- Name – Central Vpn,
- Zone – VPN,
- Type – Network,
- Network – 192.168.0.0
- Netmask – 255.255.255.0
- Click Save.
Configuration VPN Policy
- Navigate to Network|IPSec VPN|Rules and Settings
- Click the Add button under the VPN Policies section. The VPN Policy window pops up.
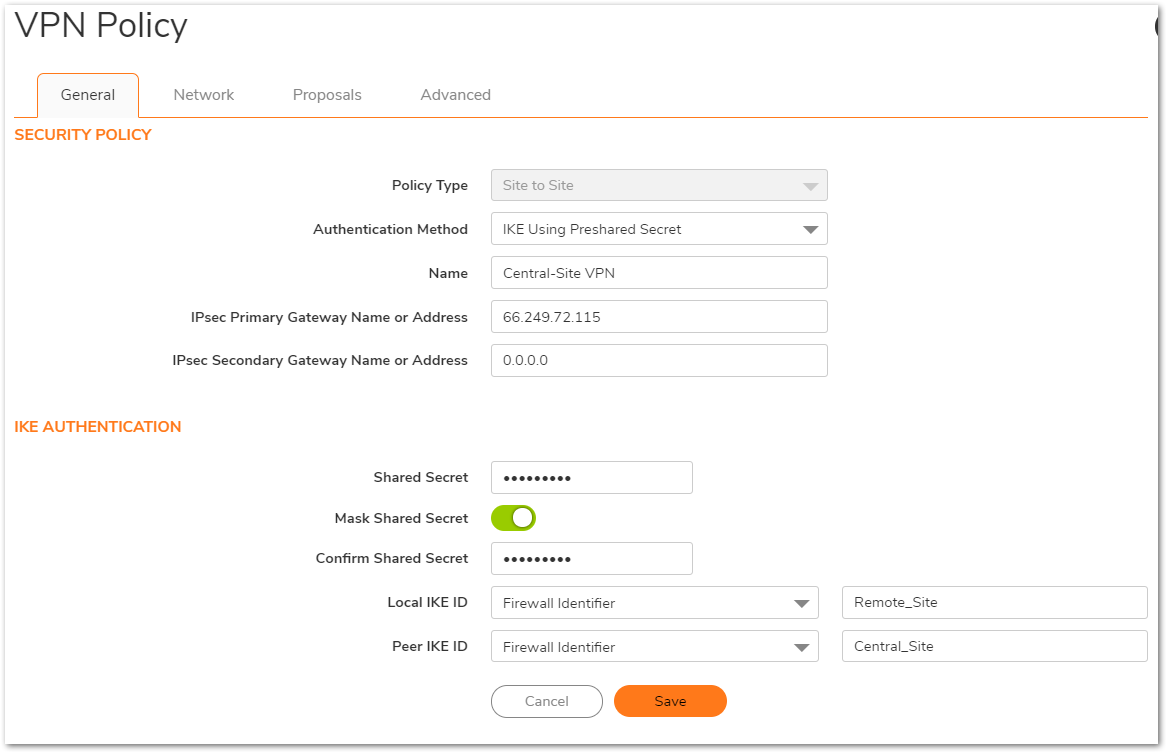
General Tab
- Select the Authentication method as IKE Using Preshared Secret.
- Name Central-Site VPN.
- IPSec Primary Gateway Name or Address: 66.249.72.115 (Gateway of the main site, which is static IP)
- IPSec Secondary Gateway Name or Address: 0.0.0.0.
- Shared Secret: SonicWall (The Shared Secret would be the same at both SonicWall’s. You can choose any Secret Key, but it should be entered the same on both sites).
- Local IKE ID: SonicWall Identifier -Remote_Site(This could be any string except it has to match the remote location VPN's Peer IKE ID SonicWall Identifier)
- Peer IKE ID: SonicWall Identifier - Central_Site(This could be any string except it has to match the remote location VPN's Local IKE ID SonicWall Identifier)
Network Tab
- Select Choose local network from list, and select the Address Object – X0 Subnet .
- Select Choose destination network from list, and select the Address Object – Central Vpn.
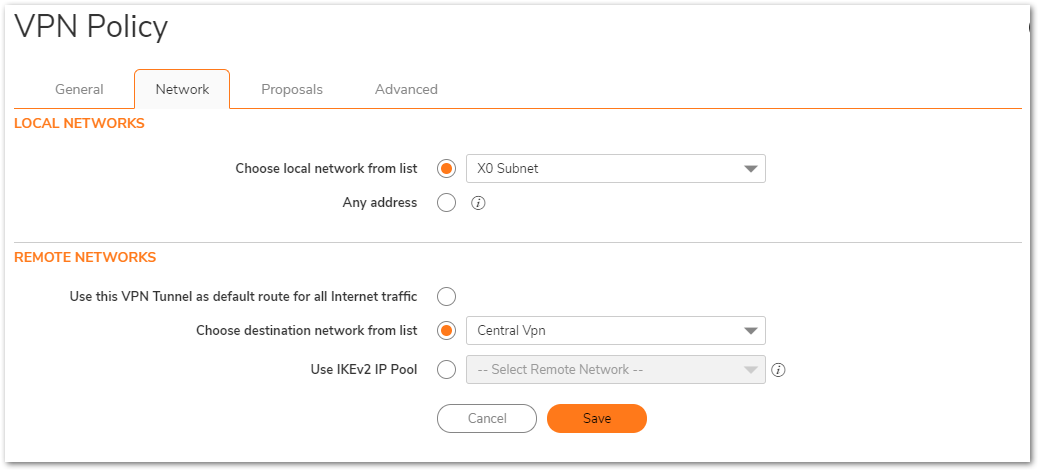
Proposals Tab
- IKE (Phase 1) Proposal.
- Exchange: Aggressive Mode.
- DH Group: Group 2.
- Encryption: AES-128 .
- Authentication: SHA1.
- Life Time (seconds): 28800 .
- IPSec (Phase 2) Proposal.
- Protocol: ESP.
- Encryption: AES-128.
- Authentication: SHA1.
- Enable Perfect Forward Secrecy (not checked) .
- DH Group: Group 2.
- Life Time (seconds): 28800.

Advanced Tab
- Enable Keep Alive box should be checked.
- VPN Policy bound to: Zone WAN.
- Click Save.
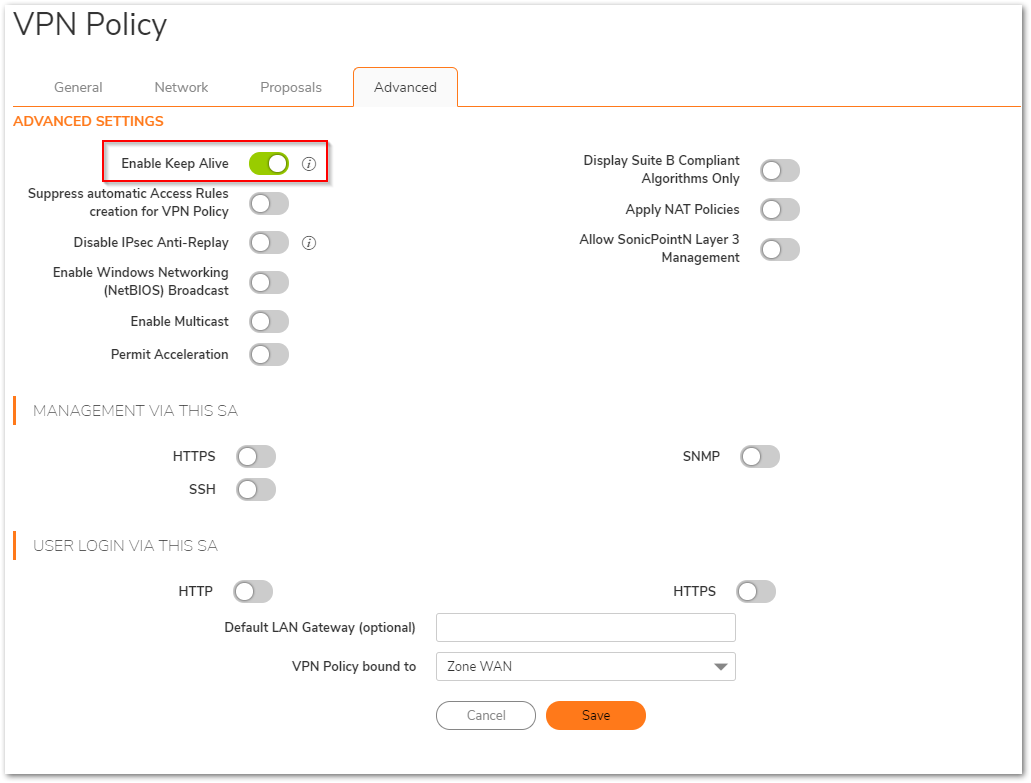
How to Test
- From the remote location try to ping an IP address on the central location.
 NOTE: Before receiving successful replies, you might see couple of “Request Timed Out“ messages while the VPN tunnel is still establishing.
NOTE: Before receiving successful replies, you might see couple of “Request Timed Out“ messages while the VPN tunnel is still establishing.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
This solution explains the configuration of a Site to Site VPN on SonicWall appliances when a site has dynamic WAN IP address.
The VPN policy is setup using Aggressive Mode.
Configuring a Site to Site VPN on the Central location
- Creating Address Object for remote Site
- Login to the central location SonicWall appliance.
- Navigate to Manage | Policies | Objects | AddressObjects page.
- Click Add button, enter the following settings.
- Name – newyork vpn,
- Zone – VPN,
- Type – Network,
- Network – 10.10.10.0,
- Netmask – 255.255.255.0
- Click OK.
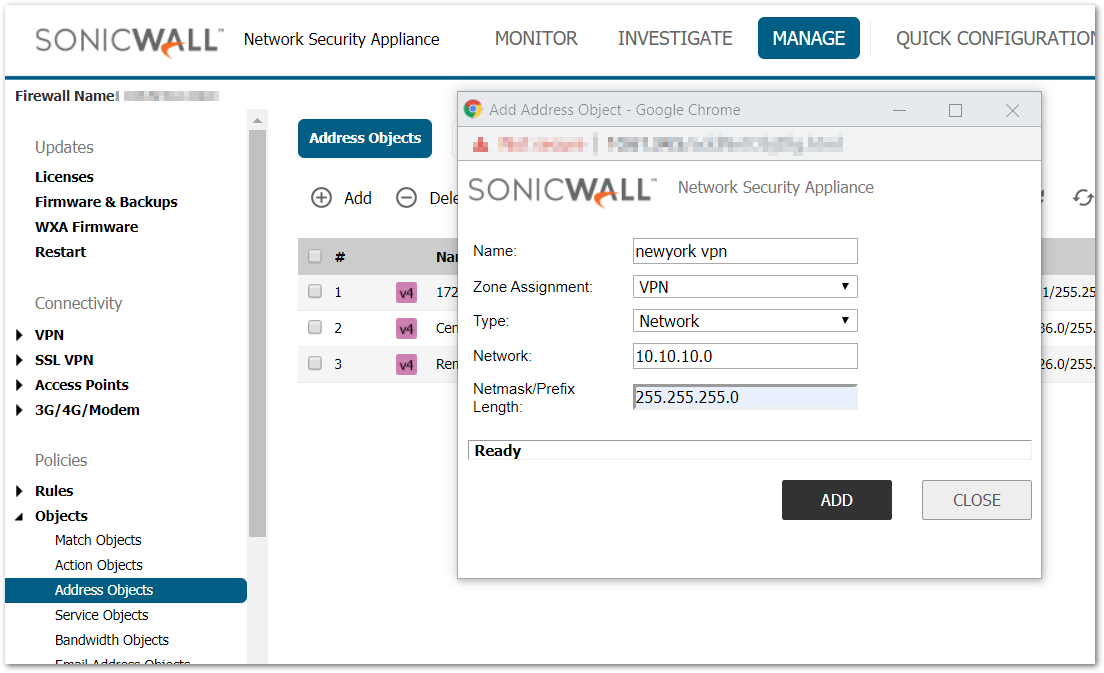
- Configuring a VPN Policy
- Navigate to Manage | Connectivity | VPN | Base Settings.
- Check the box “Enable VPN” under Global VPN Settings.
- Click Add button under VPN Policies section. The VPN Policy window pops up.
General Tab
- Select the Authentication method as IKE Using Preshared Secret.
- Name: New York Aggressive Mode VPN.
- IPSec Primary Gateway Name or Address: 0.0.0.0.
 NOTE: Since the WAN IP address changes frequently, it is recommended to use the 0.0.0.0 IP address as the Primary Gateway.
NOTE: Since the WAN IP address changes frequently, it is recommended to use the 0.0.0.0 IP address as the Primary Gateway. - IPSec Secondary Gateway Name or Address: 0.0.0.0.
- Shared Secret: SonicWall (The Shared Secret would be the same at both SonicWall’s. You can choose any Secret Key, but it should be entered sam on both sites).
- Local IKE ID: SonicWall Identifier - Chicago (This could be any string except it has to match the remote location VPN's Peer IKE ID SonicWall Identifier)..
- Peer IKE ID: SonicWall Identifier - newyork (This could be any string except it has to match the remote location VPN's Local IKE ID SonicWall Identifier).

Network Tab
- Select Choose local network from list, and select the Address Object – X0 Subnet (LAN subnet).
- Select Choose destination network from list, and select the Address Object – newyork vpn.
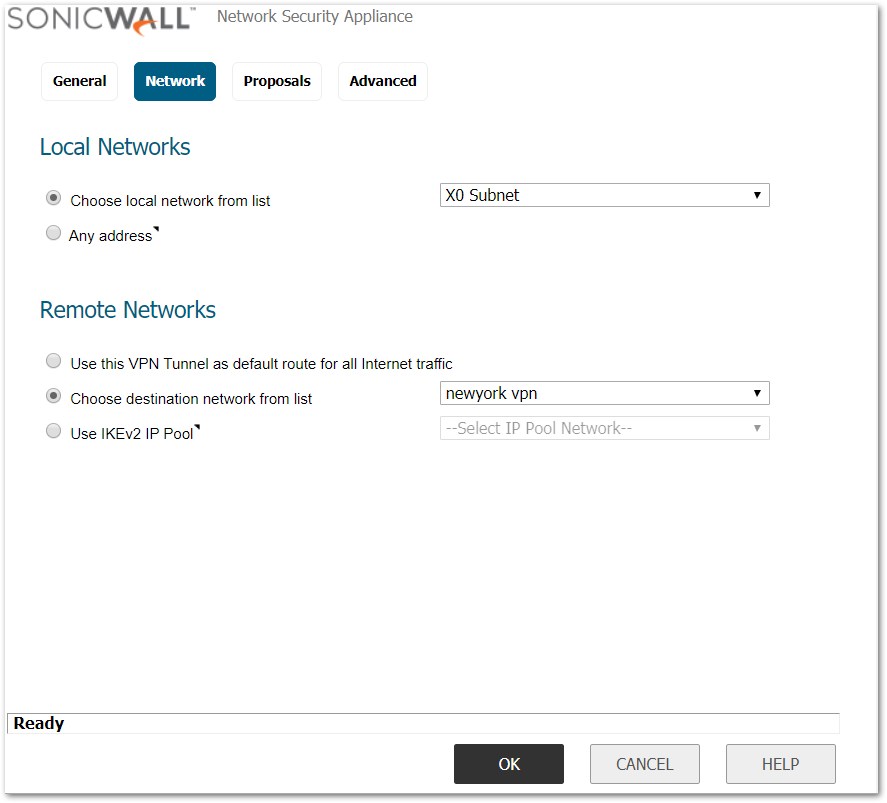
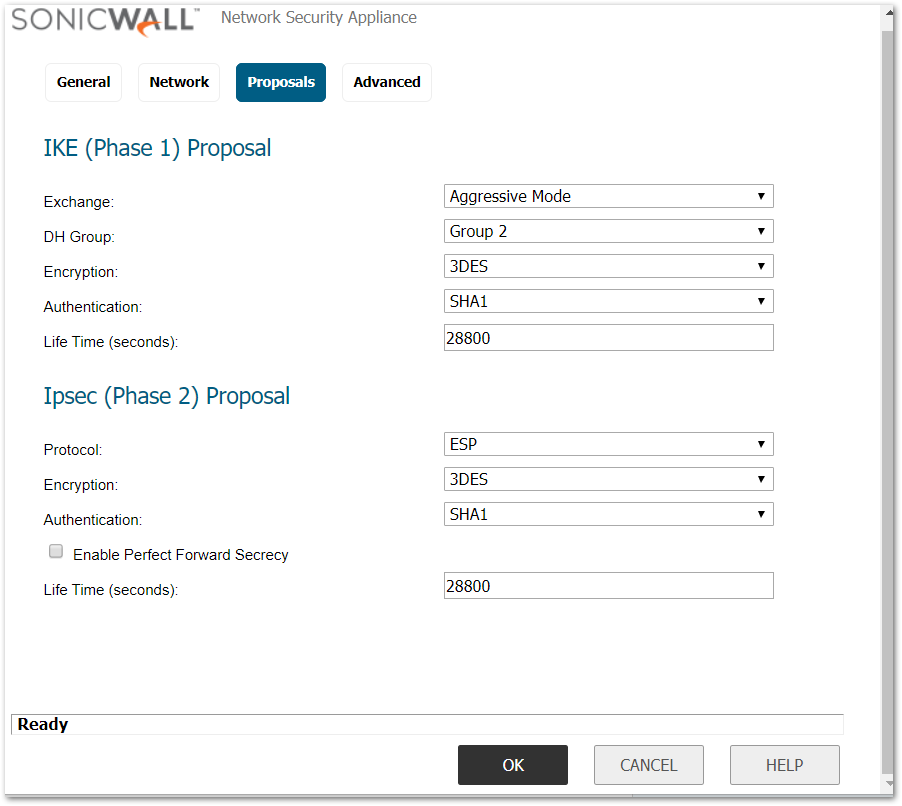
Proposals Tab
- IKE (Phase 1) Proposal.
- Exchange: Aggressive Mode.
- DH Group: Group 2.
- Encryption: 3DES.
- Authentication: SHA1.
- Life Time (seconds): 28800 .
- IPSec (Phase 2) Proposal.
- Protocol: ESP.
- Encryption: 3DES.
- Authentication: SHA1.
- Enable Perfect Forward Secrecy(not checked).
- Life Time (seconds): 28800.
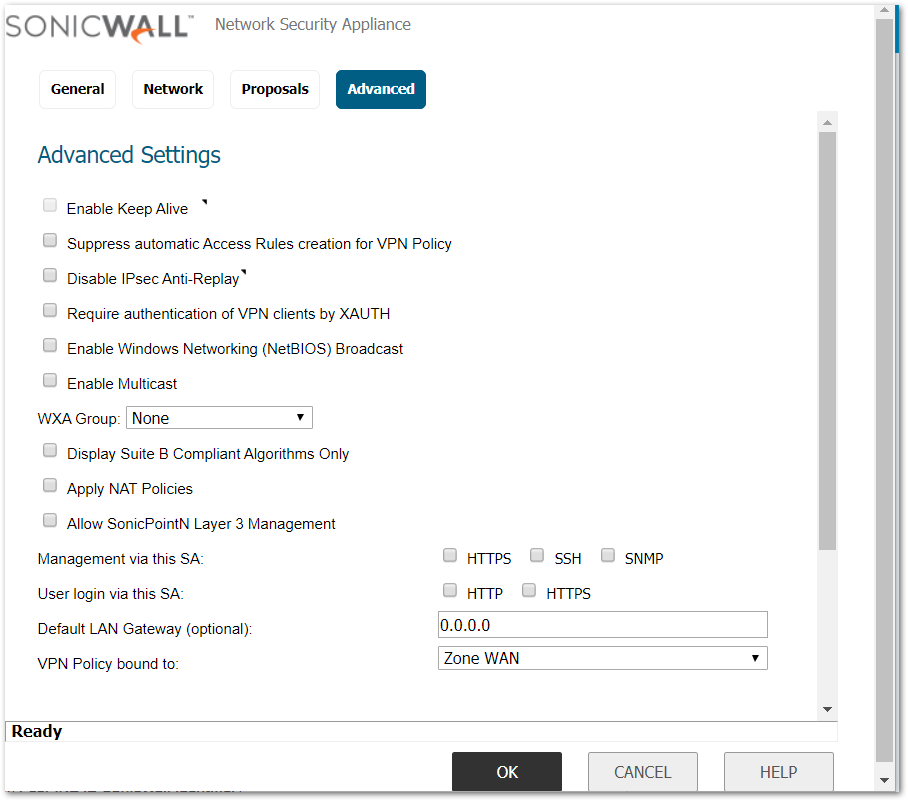
Advanced tab
- Ensure that the VPN Policy bound to: Zone WAN.
- Click OK
Configuring a Site to Site VPN on the remote location (Dynamic WAN IP address)
 NOTE: The Dynamic WAN IP Address must be Public.
NOTE: The Dynamic WAN IP Address must be Public.
Network Configuration
- LAN Subnet: 10.10.10.0.
- Subnet Mask: 255.255.255.0.
- WAN IP: DHCP (As this is a Dynamic IP Address).
- Local IKE ID SonicWall Identifier: newyork (This has to match the central location VPN's Peer IKE ID SonicWall Identifier).
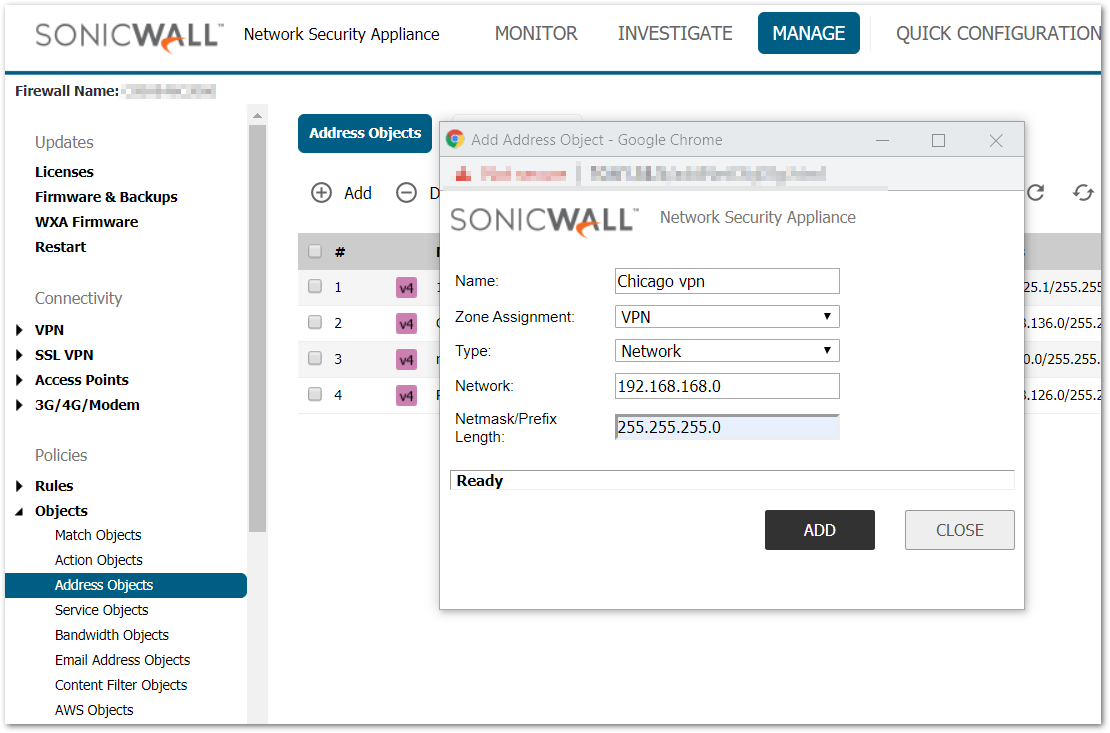
- Creating Address Object for remote site
- Login to the Remote location SonicWall appliance.
- Navigate to Manage | Policies | Objects | AddressObjects page.
- Click Add button, enter the following settings.
- Name – Chicago vpn.
- Zone – VPN.
- Type – Network.
- Network – 192.168.168.0.
- Netmask – 255.255.255.0.
- Click OK .
- Configuration VPN Policy
- Navigate to Manage | Connectivity | VPN | Base Settings.
- Check the box Enable VPN under Global VPN Settings.
- Click Add button under the VPN Policies section. The VPN Policy window pops up.
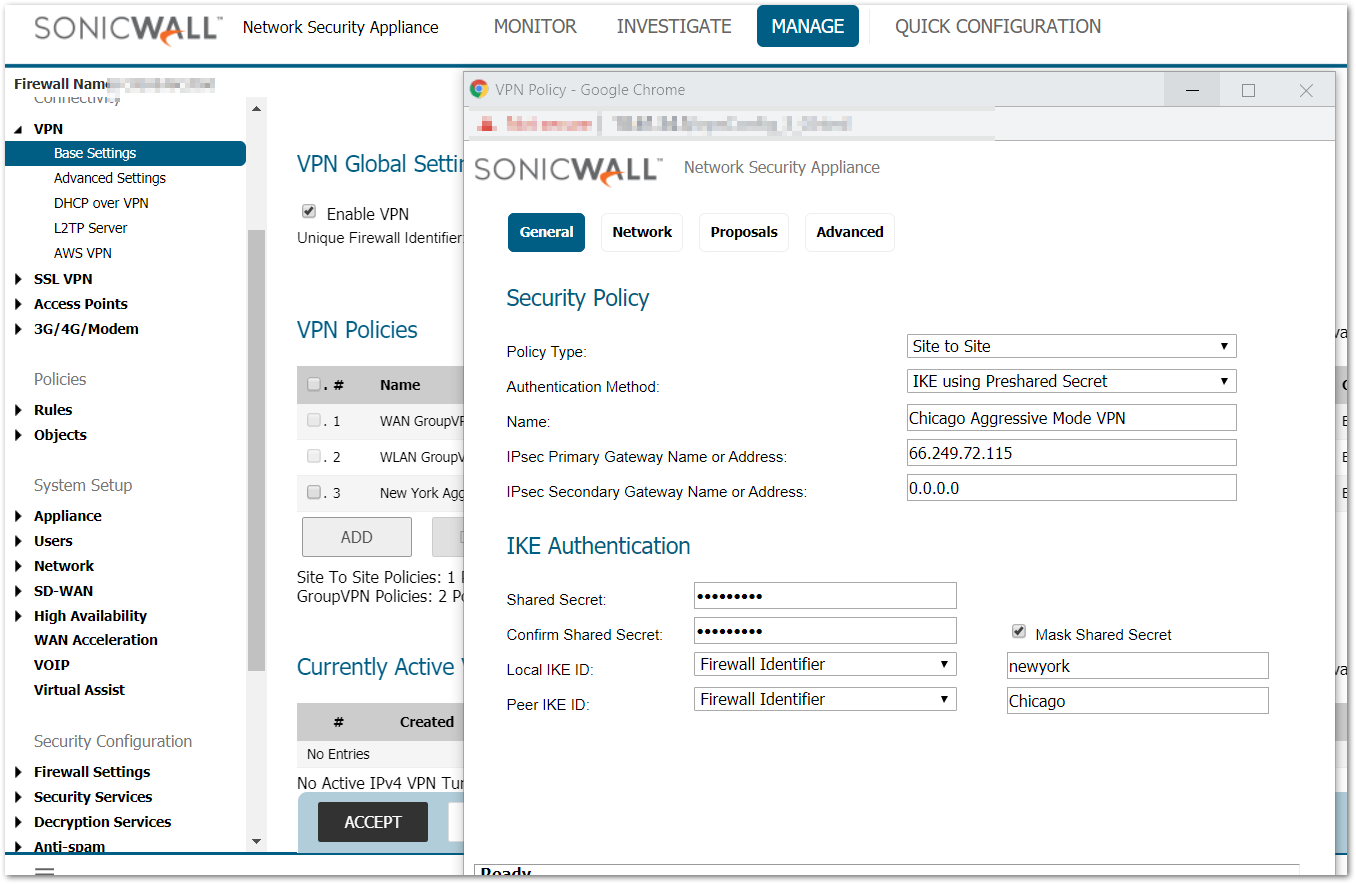
General Tab
- Select the Authentication method as IKE Using Preshared Secret.
- Name: Chicago Aggressive Mode VPN.
- IPSec Primary Gateway Name or Address: 66.249.72.115 ( Gateway of the main site, which is static IP).
- IPSec Secondary Gateway Name or Address: 0.0.0.0.
- Shared Secret: SonicWall.
- Local IKE ID: SonicWall Identifier - newyork (This has to match the central location VPN's Peer IKE ID SonicWall Identifier).
- Peer IKE ID: SonicWall Identifier – Chicago (This has to match the central location VPN's Local IKE ID SonicWall Identifier).
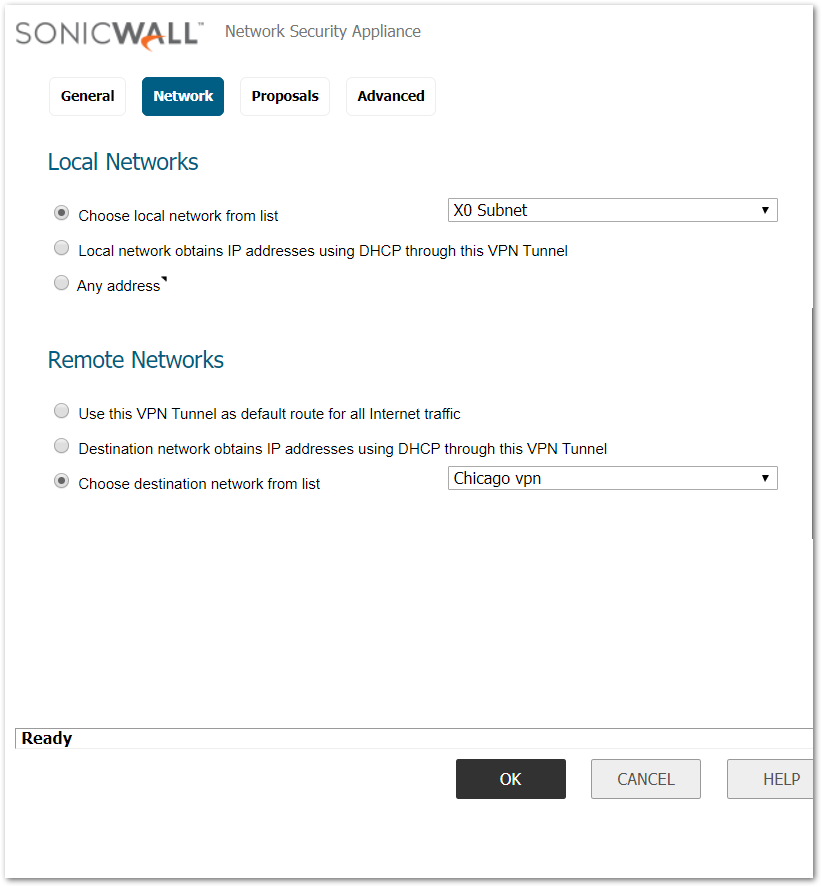
Network Tab
- Select Choose local network from list, and select the Address Object – LAN Primary Subnet .
- Select Choose destination network from list, and select the Address Object – Chicago vpn.
Proposals Tab
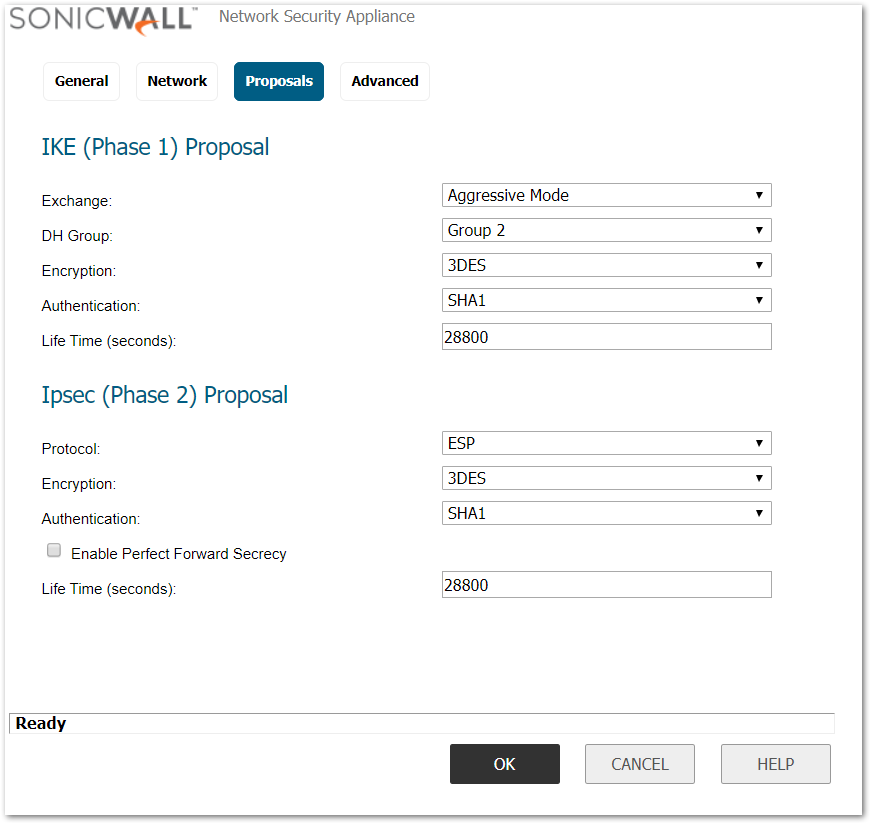
- IKE (Phase 1) Proposal.
- Exchange: Aggressive Mode.
- DH Group: Group 2.
- Encryption: 3DES .
- Authentication: SHA1.
- Life Time (seconds): 28800 .
- IPSec (Phase 2) Proposal.
- Protocol: ESP.
- Encryption: 3DES .
- Authentication: SHA1.
- Enable Perfect Forward Secrecy (not checked) .
- DH Group: Group 2.
- Life Time (seconds): 28800.
Advanced Tab
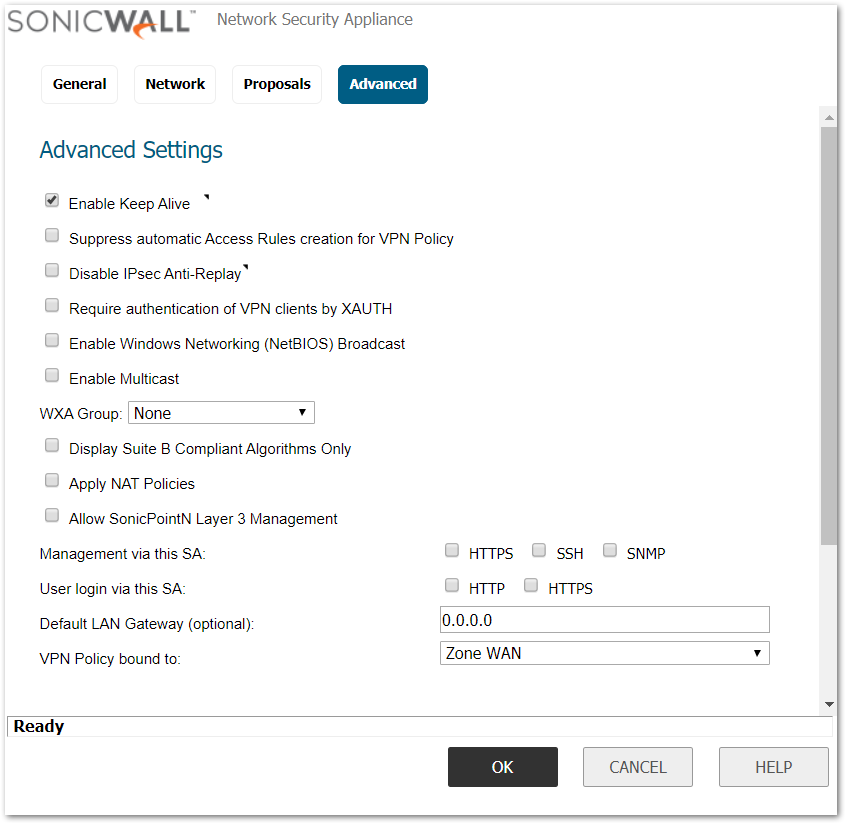
- Enable Keep Alive box should be checked.
- VPN Policy bound to: Zone WAN.
- Click OK .
How to Test
- From the remote location try to ping an IP address on the central location.
 NOTE:Before receiving successful replies, you might see couple of “Request Timed Out“ messages while the VPN tunnel is still establishing.
NOTE:Before receiving successful replies, you might see couple of “Request Timed Out“ messages while the VPN tunnel is still establishing.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > VPN
- Firewalls > NSv Series > VPN
- Firewalls > TZ Series > VPN






 YES
YES NO
NO