-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Common configurations to protect against Ransomware



Description
The following article outlines common configurations for defending networks against Ransomware exploits. Ransomware has evolved heavily over the past few years to include several new network exploits, including modified polymorphic front end, and zero-day worm propagation techniques.
On May 12, 2017, a variant of Ransomware known as WannaCry was successful in infecting more than 200,000 systems in over 150 countries. Preventing Ransomware and other zero-day exploits is achievable, however, requires steadfast security monitoring and network configurations.
The following is a brief guide to configuration SonicWall Network Security Appliances (Firewalls) to prevent Ransomware.
Please note that many of the steps included in this article are also relevant with many of other security recommendations that organizations should be deploying to inspect traffic and prevent breaches.
SonicWall Capture Advanced Threat Protection is available on TZ 300 and higher.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Security Services Subscription
For all SonicWall appliances, it is highly recommended to include the Essential Protection Service Suite, which includes active subscriptions for Gateway Anti-Virus, Intrusion Prevention, Anti-Spyware, Content Filtering, Botnet Filter, Geo IP Filter, Application Firewall, DPI-SSL, DPI-SSH, and Capture. If this subscription is not active then updates and configurations will not be possible.
Enable Gateway Anti-Virus
- Make sure that GAV is updated with the latest signatures.
- Enable GAV.
- Enable Cloud GAV.
- Enable Inspection on Inbound and Outbound for all HTTP, FTP, IMAP, SMTP, POP3, CIFS/NetBIOS, and TCP Stream.
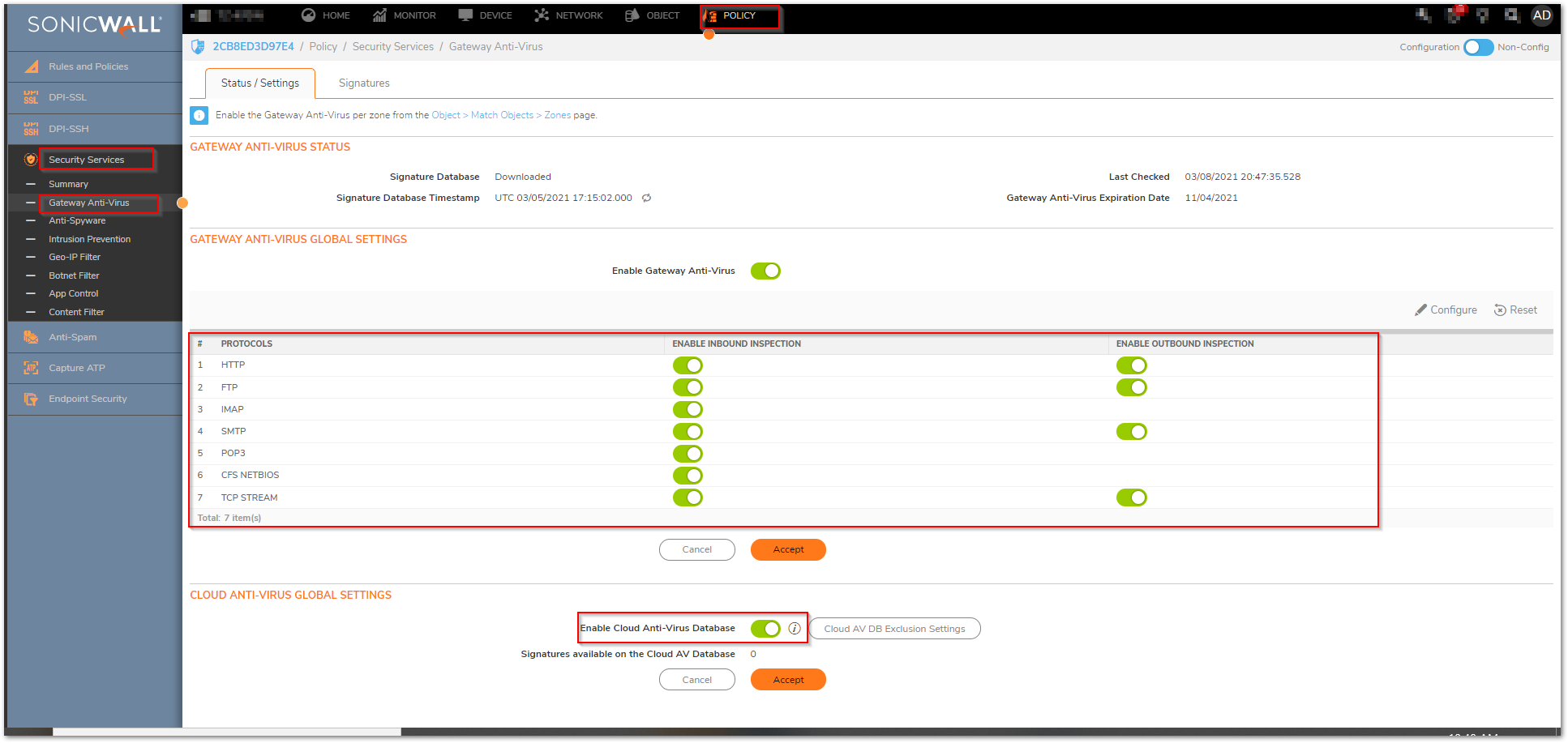
- Inside the Protocol Settings of the protocols make sure that you have enabled the option to block.
- Restrict Transfer of password-protected ZIP files.
- Restrict Transfer of MS-Office type files containing macros (VBA 5 and above).
- Restrict Transfer of packed executable files (UPX, FSG, etc).
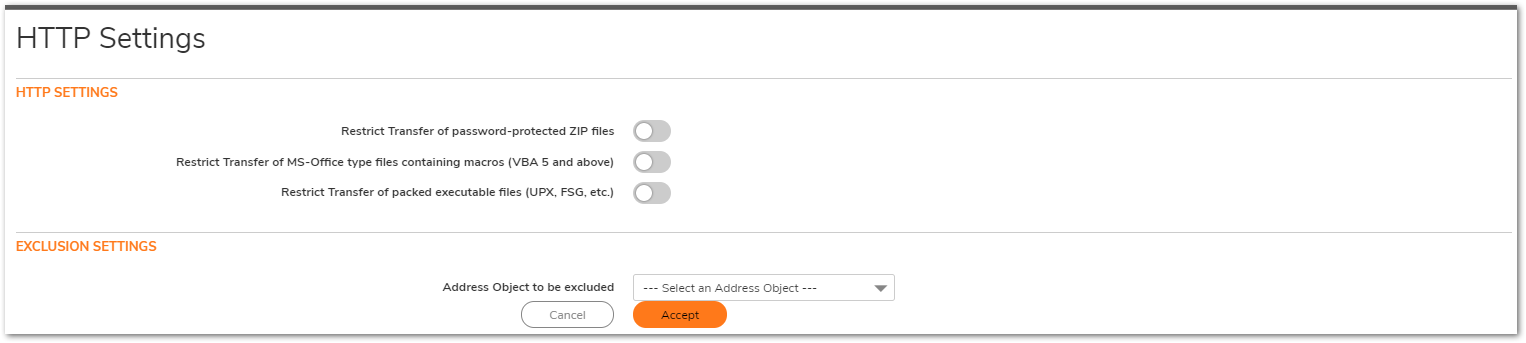
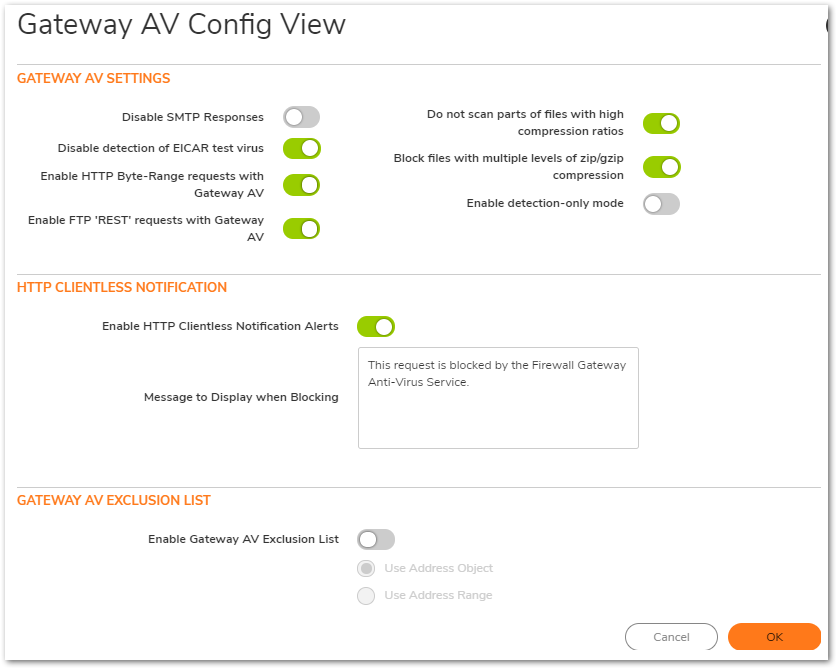
- Click Configure Gateway AV Settings.
- Enable the option to Block files with multiple levels of zip/zip compression.
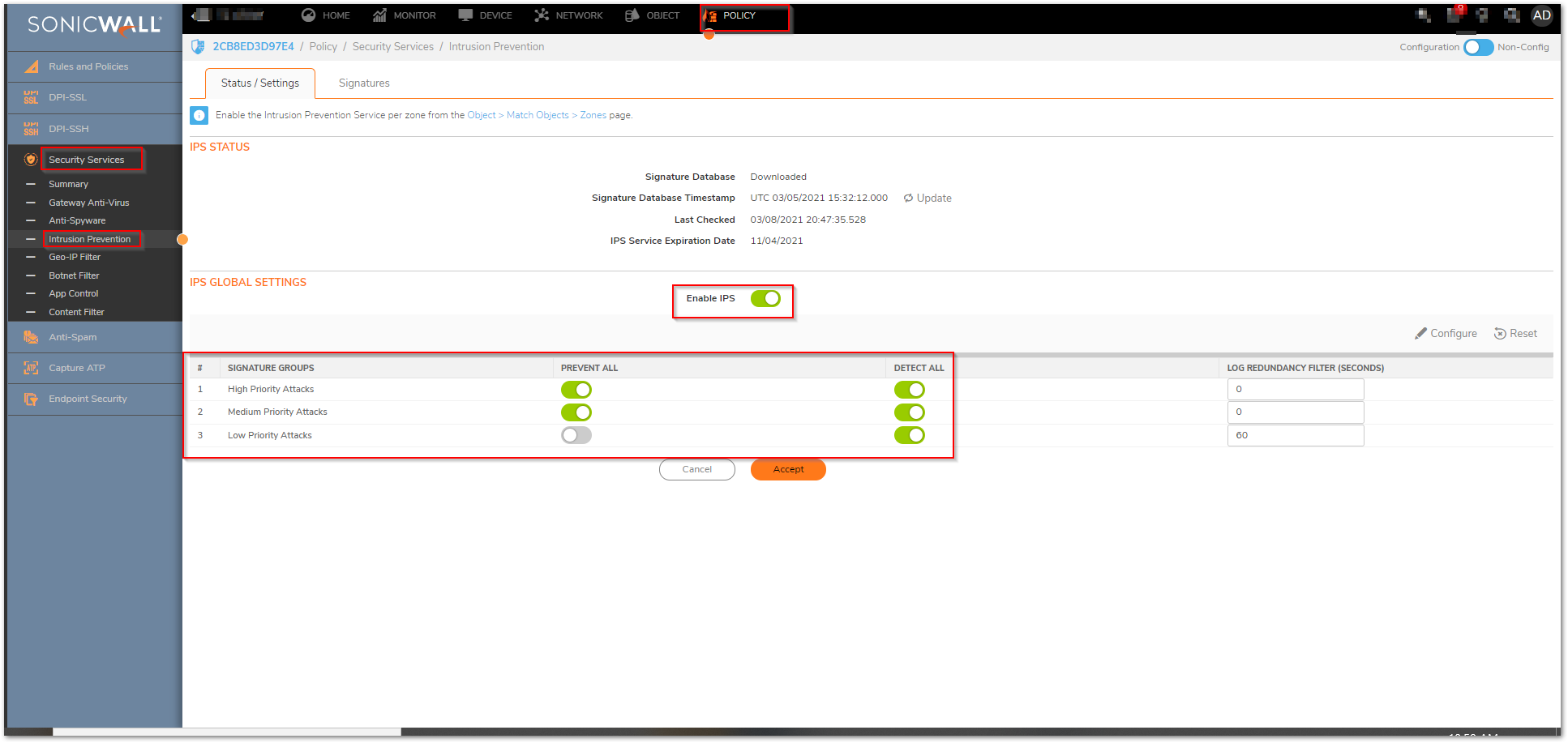
Enable Intrusion Prevention
Many of today's modified Ransomware exploits include malicious Trojans and worm elements, exploiting network communications, and impacting systems. Intrusion Prevention is an essential cornerstone of preventing these attacks in networks.
- Make sure that the SonicWall has the latest signature updates from the SonicWall Capture Labs.
- Enable the IPS Service.
- Enable Prevention for (at a minimum) of High and Medium Threats, but may need to include Low Priority based on additional requirement and compliance regulations based on the network being deployed.
- Enable Intrusion Detection if log data of intrusion information is required. SonicWall Intrusion Detection is responsible for providing the log event of Intrusions. If not selected log data will not be created.
Enable Geo-IP Filter
Geo-IP Filter is able to control traffic to and from various countries, and is a core component of the CGSS/AGSS security subscription.
- Enable Geo-IP Filter
- This can be setup on All Connections or Firewall Rule Based.
- All Connections will include all traffic, but default rules would be to exclude Firewall Subnets.
- Firewall Rule Based requires enabling the service on individual rules within Firewall Access Rules. If this method is applied, any rules for WAN to WAN, WAN to LAN, and LAN to WAN should be enabled.
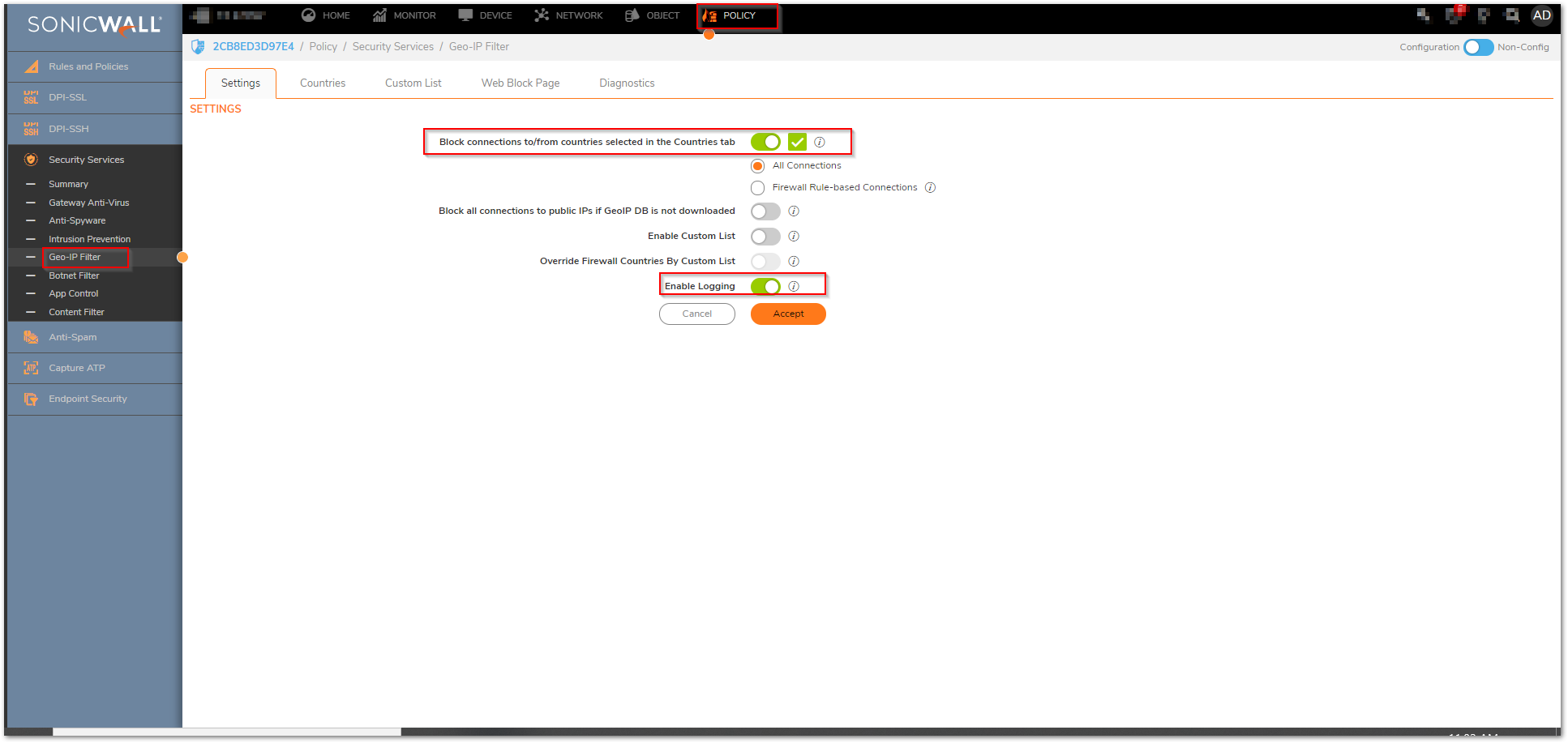
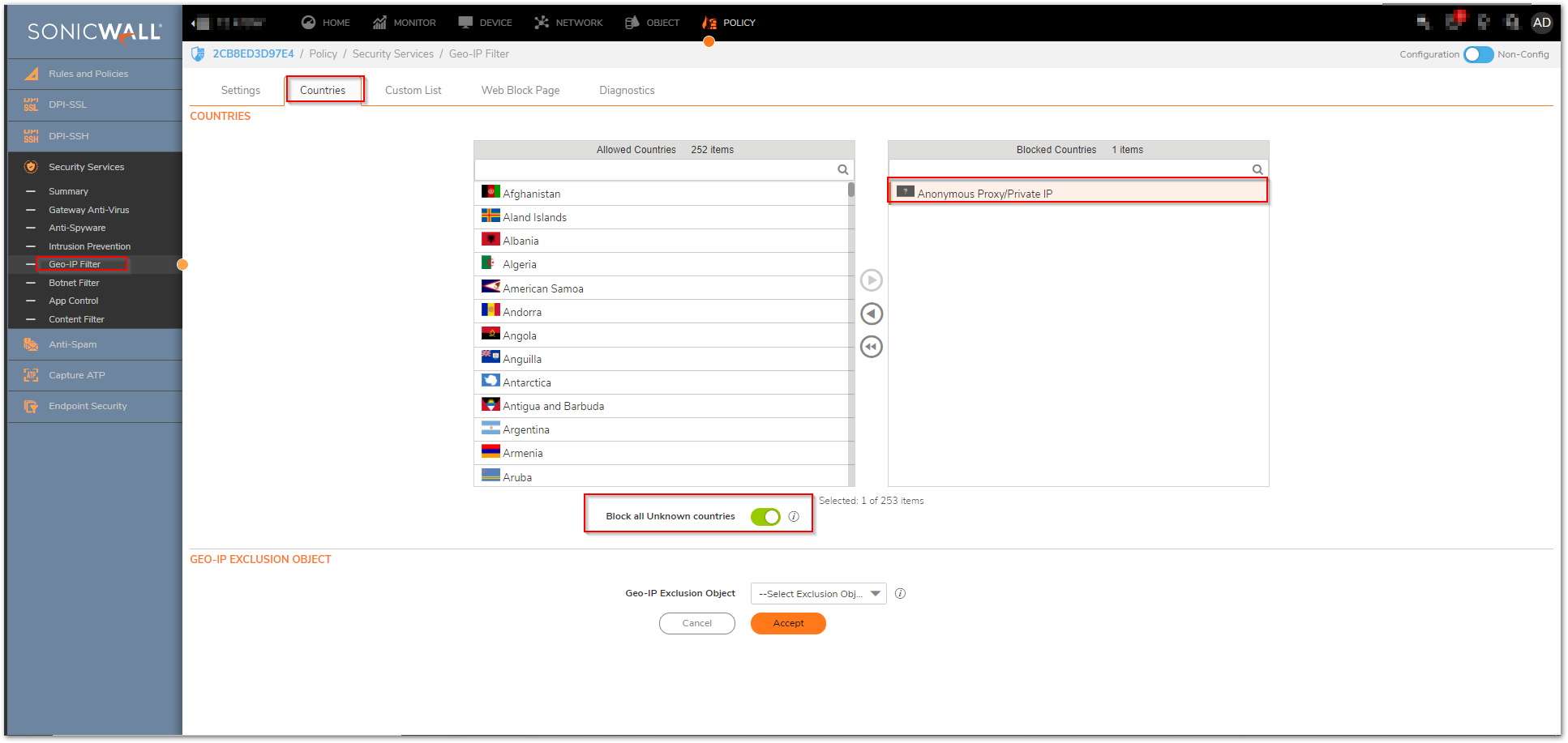
- Make sure that traffic to Anonymous Proxy / Private IP is selected at a minimum from the country list.
- Make sure that Block all UNKNOWN countries is also enabled.
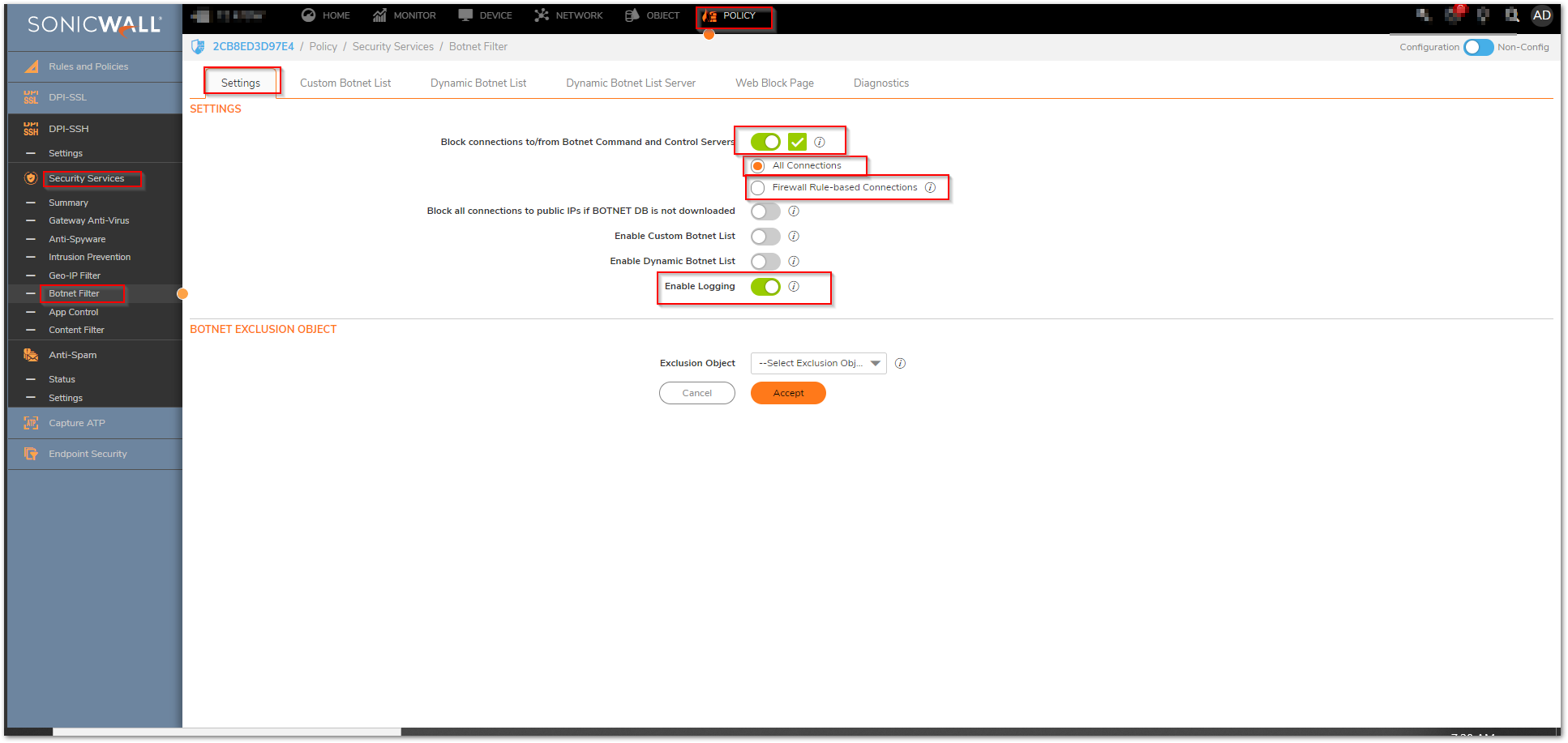
Enable Botnet Filter
Botnet Filter is able to prevent traffic to or from known malicious hosts that act as Botnet networks.
Enable Botnet Filter
- This can be setup on All Connections or Firewall Rule Based.
- All Connections will include all traffic, but default rules would be to exclude Firewall Subnets.
- Firewall Rule Based requires enabling the service on individual rules within the Firewall Access Rules. If this method is applied, any rules for WAN to WAN, WAN-> Internal or Internet->WAN should be enabled.
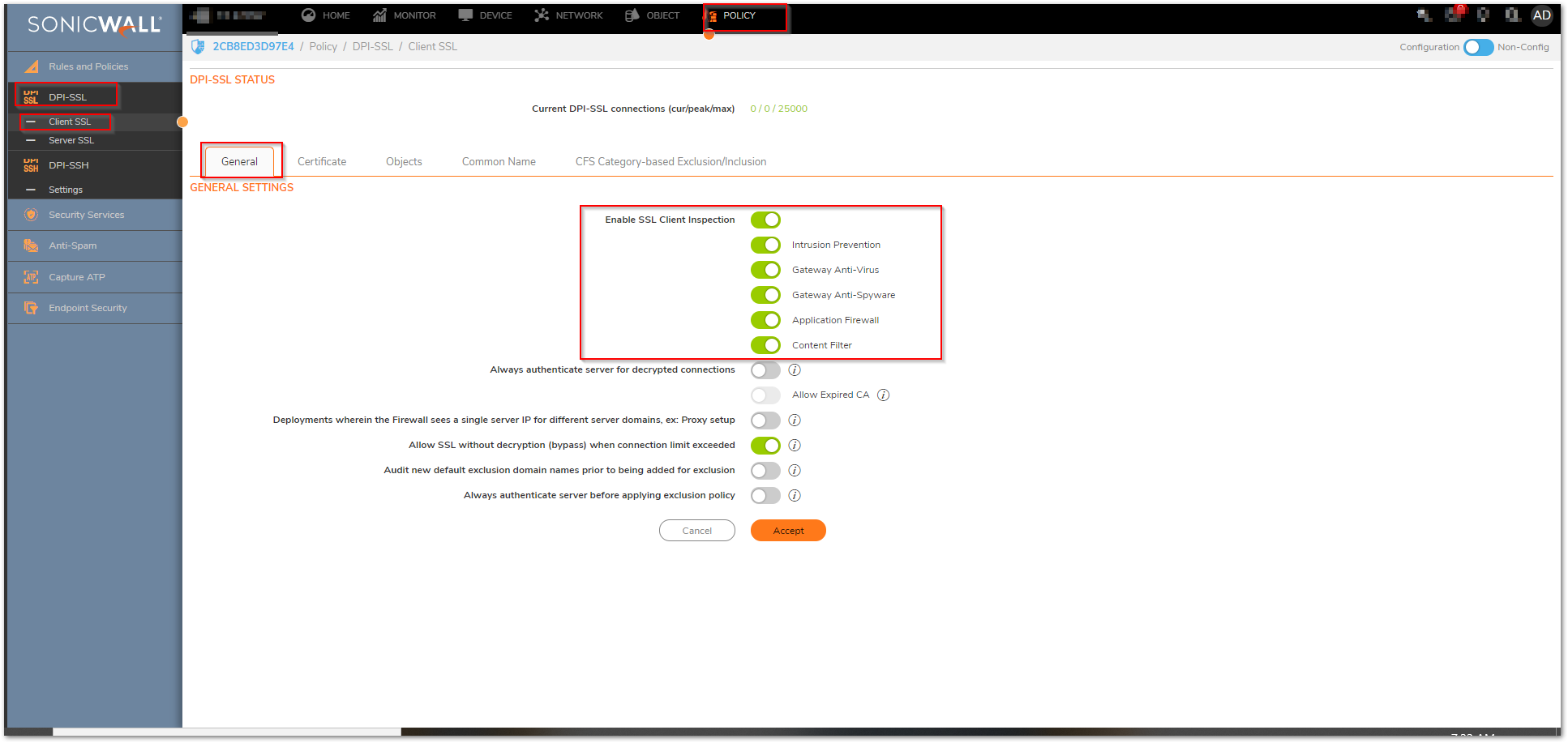
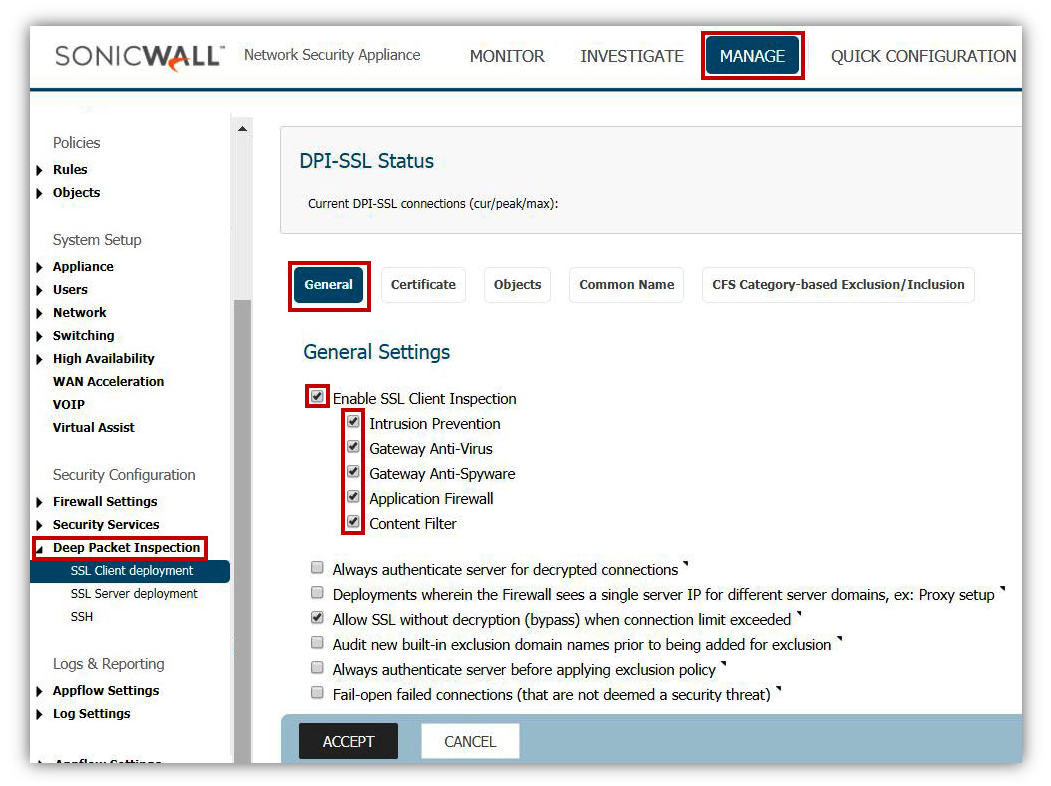
Enable DPI-SSL Client Inspection
The DPI-SSL Feature of the firewall delivers the ability to inspect within encrypted communications on multiple protocols and applications. DPI-SSL enables the firewall to act as a proxy to inspect encrypted communications such as Webmail, social media, and other web contact leveraging HTTPS connections. The settings for DPI-SSL specifically as it applies to this article is relatively simple. For questions on the setup and deployment of DPI-SSL please consult the Where Can I Learn More About DPI-SSL?.
- Enable SonicWall DPI-SSL on the firewall.
- Ensure that the services is enabled for all sub-functions including.
- Intrusion Prevention
- Gateway Anti-Virus
- Gateway Anti-Spyware
- Application Firewall
- Content Filter
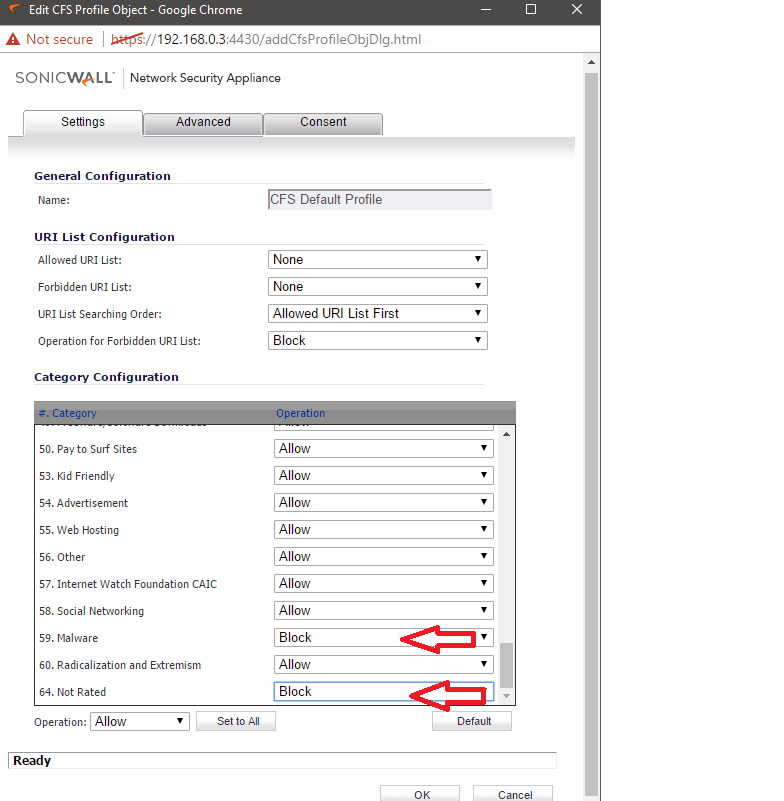
Configure Content Filtering Service
The Content Filtering rules outlined here apply to configurations for Firmware 6.2.7.1, and are based on CFS v4.0. For the purposes of preventing Ransomware, it is recommended to block access to the following categories: Malware, Hacking / Proxy Avoidance, and Not Rated.
 NOTE: Blocking the category 'Not Rated' can be management intensive as not all websites that specific networks use has been rated. Submissions for Not Rated Sites can be submitted online at Report Issues.
NOTE: Blocking the category 'Not Rated' can be management intensive as not all websites that specific networks use has been rated. Submissions for Not Rated Sites can be submitted online at Report Issues.
- Ensure that default and custom policies for user groups are all set to Block Malware, Hacking / Proxy Avoidance, and Not Rated.
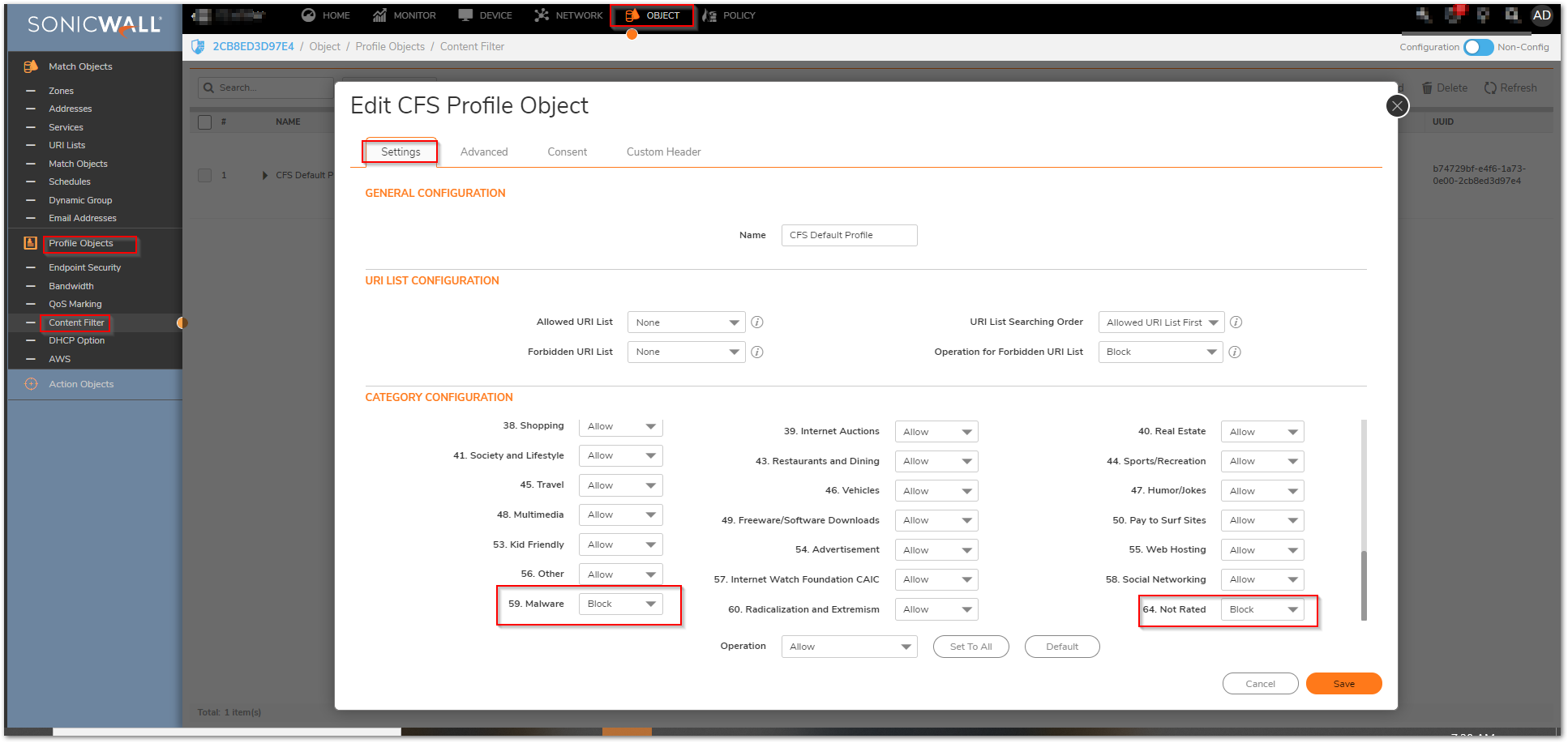
Enable Application Firewall Rules
In order to safeguard against common methods of newer generation of obfuscation leveraging traditional applications, it is recommended to enable various Application Firewall Rules. In order to prevent malware such as Ransomware from being able to circumvent enforced communications, it is advised to build rules to restrict DNS, SSH, and Proxy-Access Applications.
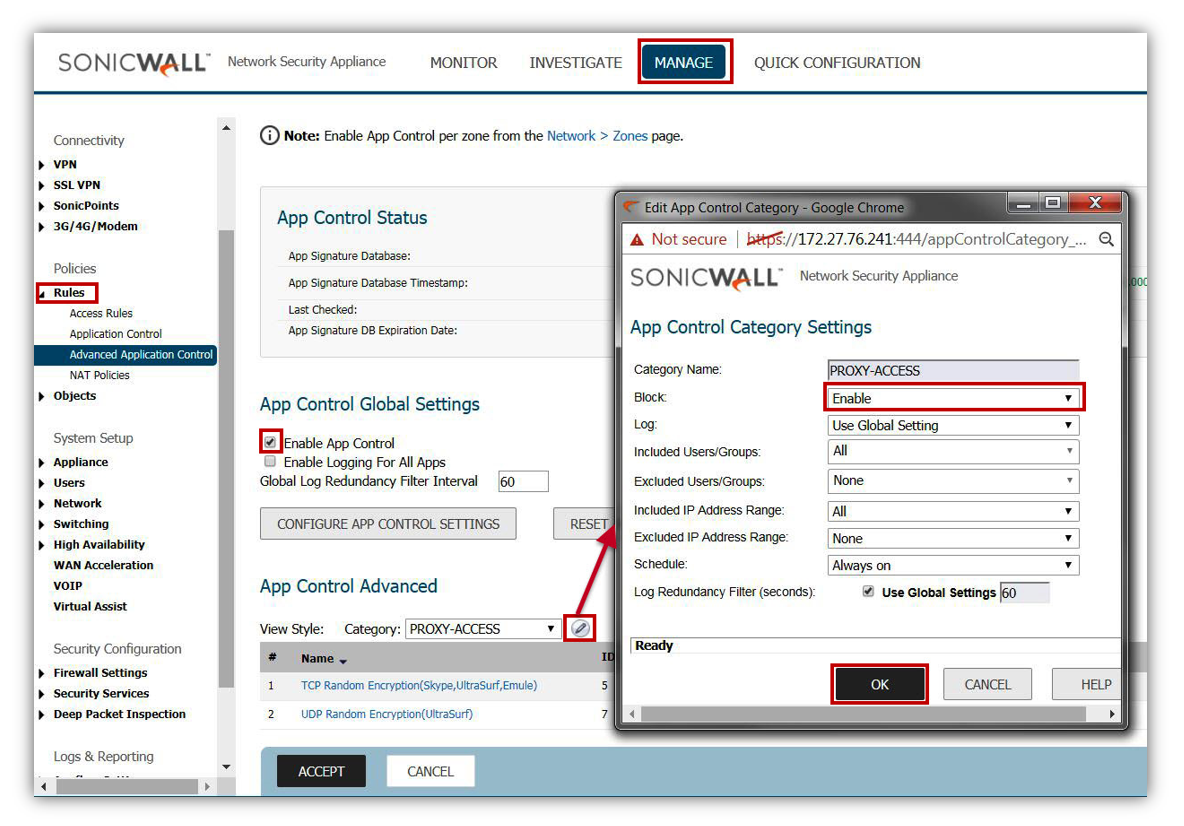
- While DNS is typically TCP/UDP 53, the DNS protocol can be used on non-standard ports. Malicious applications will leverage DNS Cache Poisoning, or redirect traffic to illegitimate sites. It is advised to lock down not only access rules to specify Trusted DNS Hosts, but to also create an Address Object and Application Rule to restrict the DNS protocol to only the Trusted DNS Host. In the below example, Google DNS 8.8.8.8 is an address object. You can create a custom address group and add it to the exclusion list.
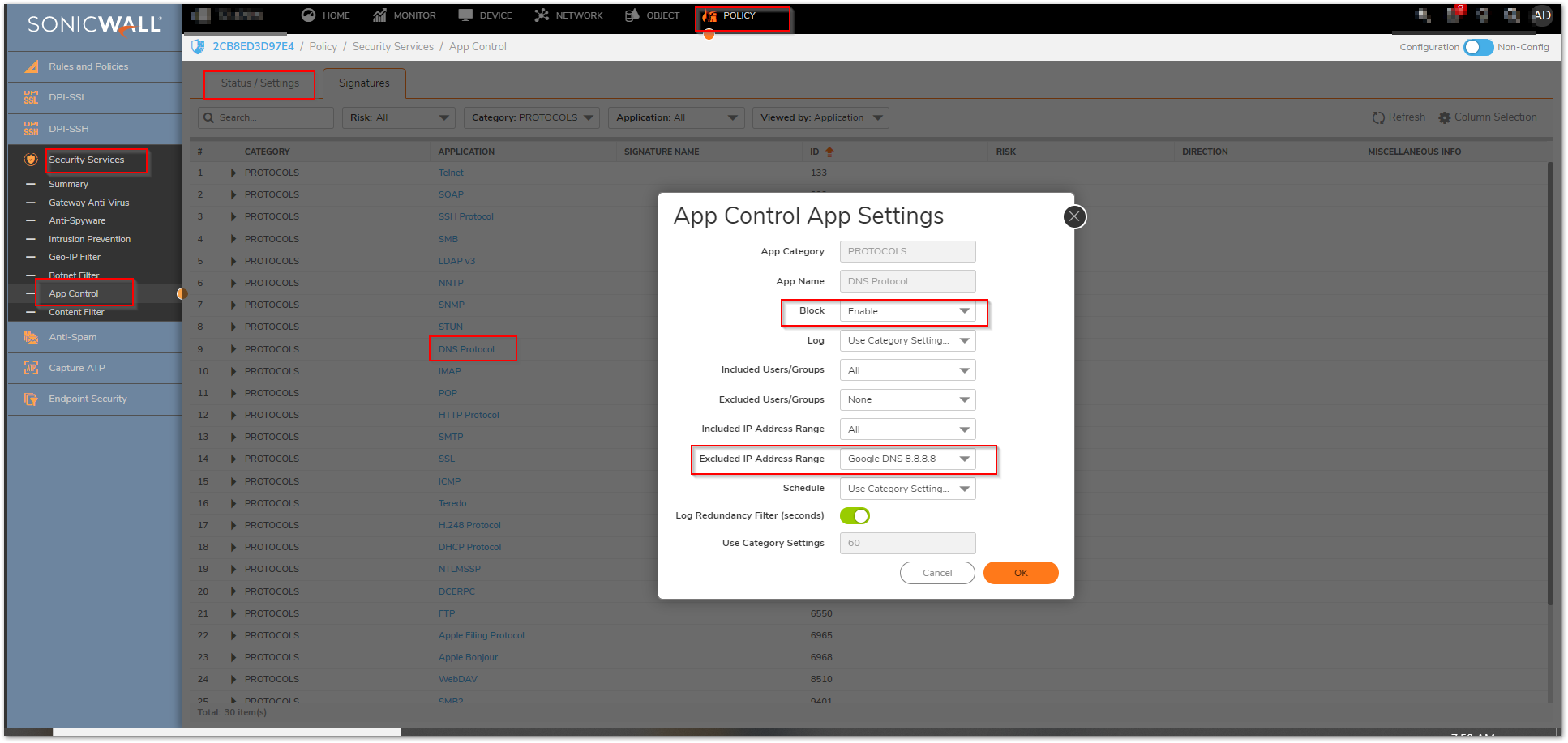
- This security mechanism can also be applied with SonicWall's DNS Proxy configuration as an alternative, however, this will still require application and access rules to restrict DNS to untrusted sources.
- The last Application Firewall policy that should be created is the prevention of all Proxy-Access Applications.
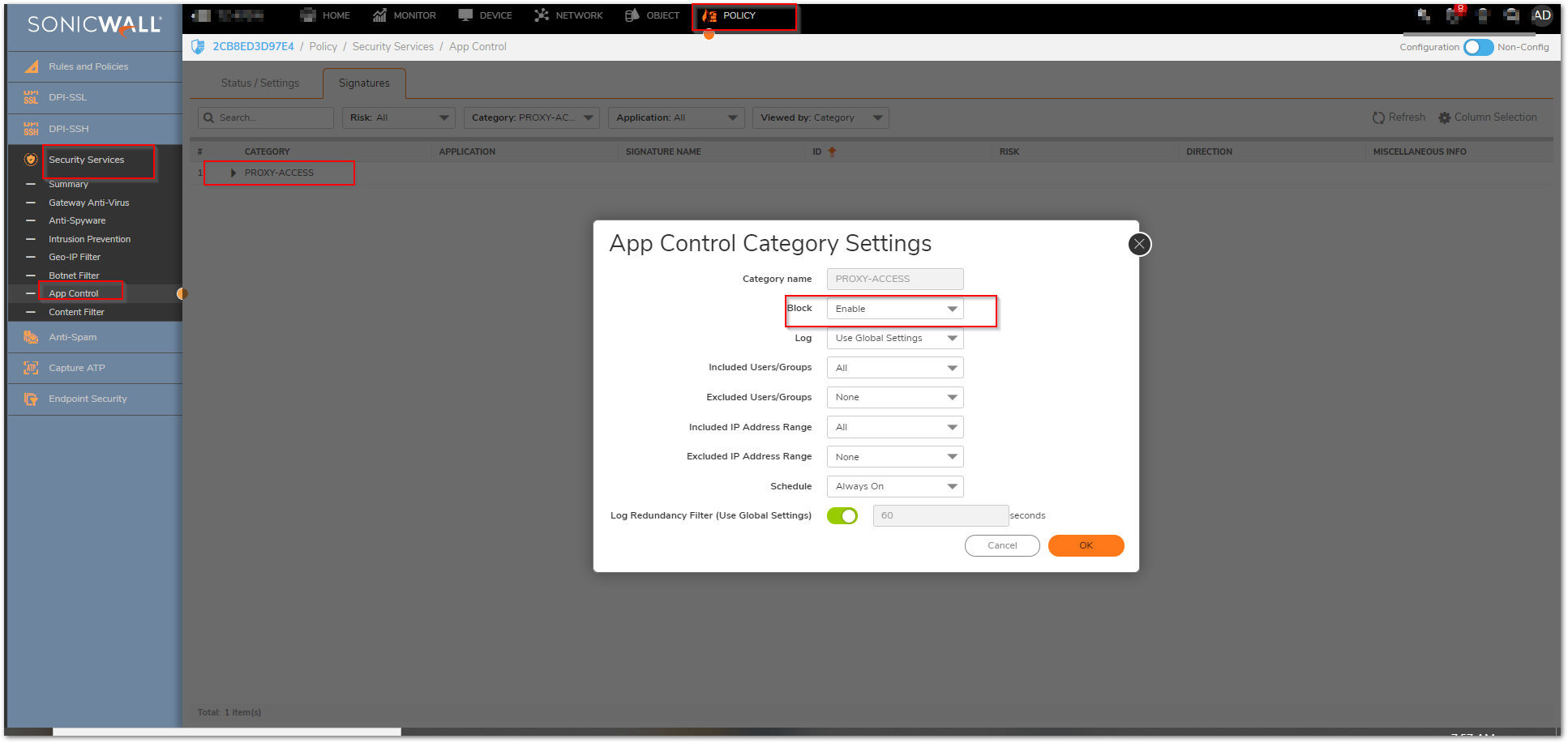
- By blocking this entire category there is the potential for legitimate applications to also break or cease to function properly. It is advised that these applications be reviewed and exceptions be created where applicable for the source and destination specific information for those specific applications.
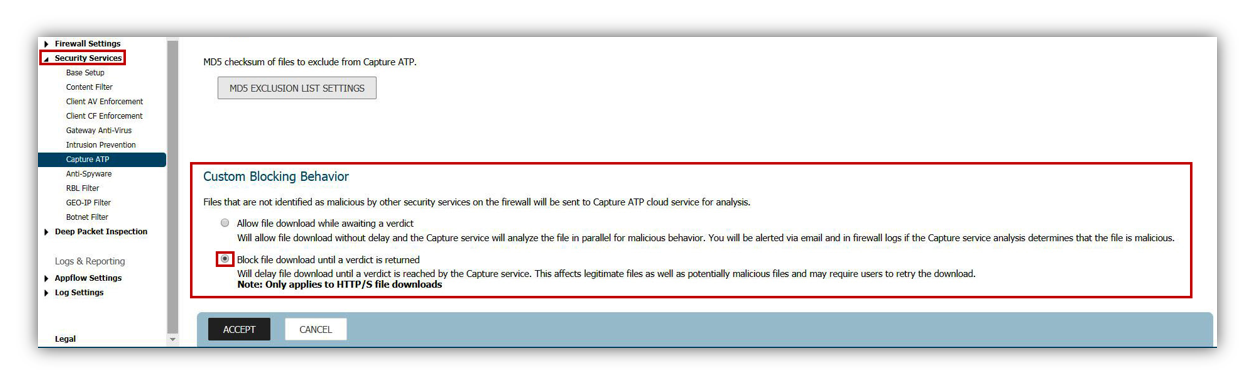
Enable Capture
Given the dynamic and constant creation of new malware, it is highly advised that the SonicWall Capture solution. Be advised this requires the Essential Protection service Suite License.
- Enable Capture, and ensure that Gateway Anti-Virus is enabled on all services.
- Ensure that all file types are selected for inspection.
- It is recommended to enable Capture to 'Block until verdict'. This will prevent malware from passing through the system until properly tested.
Additional suggestions to prevent Ransomware exploits may include, but not limited to.
- Installing end-point Anti-Virus software and keeping it updated with the latest signatures.
- Updating host Operating Systems, browsers, and browser Plugin with the latest security patches.
- Performing regular offline (cold) system back-ups.
- Educating users on the dangers of opening unknown files from unknown sources, etc.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Security Services Subscription
For all SonicWall appliances it is highly recommend to include the Advanced Gateway Security Suite (AGSS), which includes active subscriptions for Gateway Anti-Virus, Intrusion Prevention, Anti-Spyware, Content Filtering, Botnet Filter, Geo IP Filter, Application Firewall, DPI-SSL, DPI-SSH, and Capture. If this subscription is not active then updates and configurations will not be possible.
Enable Gateway Anti-Virus
- Make sure that GAV is updated with latest signatures.
- Enable GAV.
- Enable Cloud GAV.
- Enable Inspection on Inbound and Outbound for all HTTP, FTP, IMAP, SMTP, POP3, CIFS/NetBIOS, and TCP Stream.
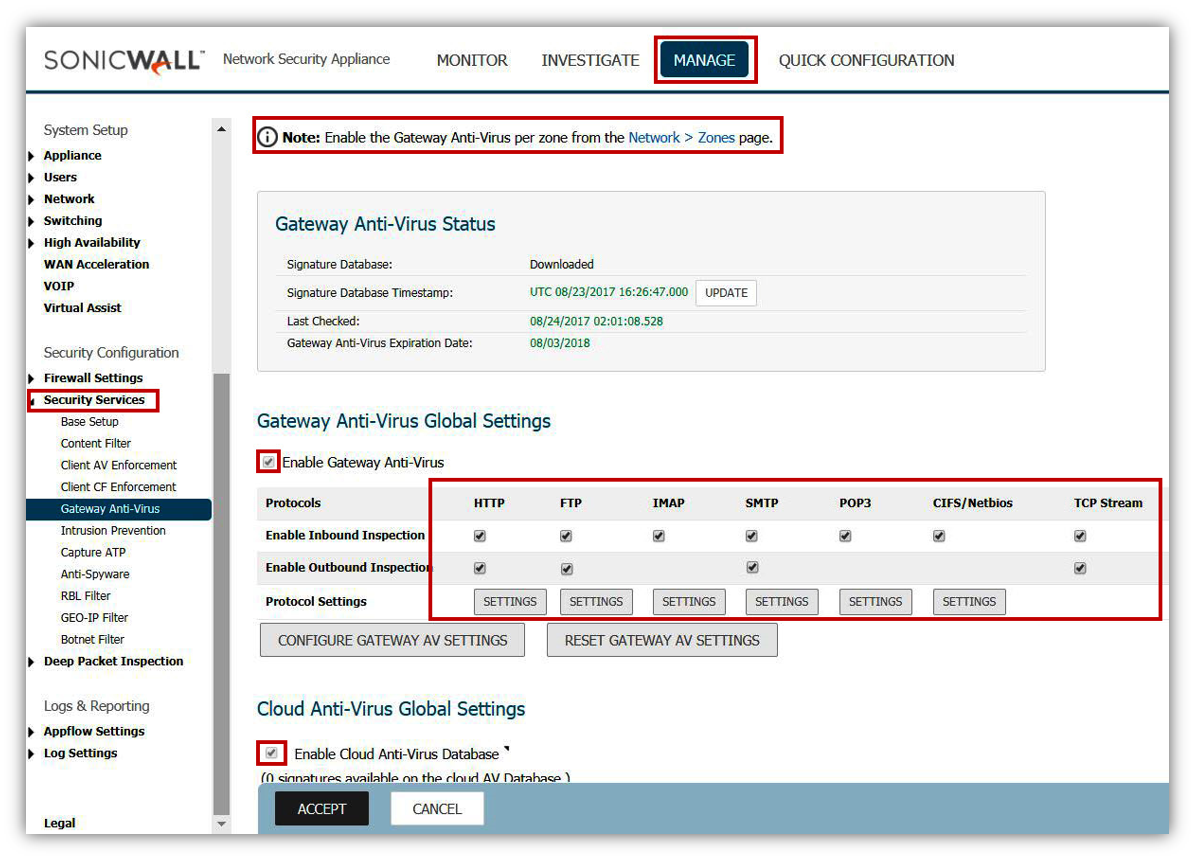
- Inside the Settings of the protocols make sure that you have enabled the option to block.
- Restrict Transfer of password-protected ZIP files.
- Restrict Transfer of MS-Office type files containing macros (VBA 5 and above).
- Restrict Transfer of packed executable files (UPX, FSG, etc).
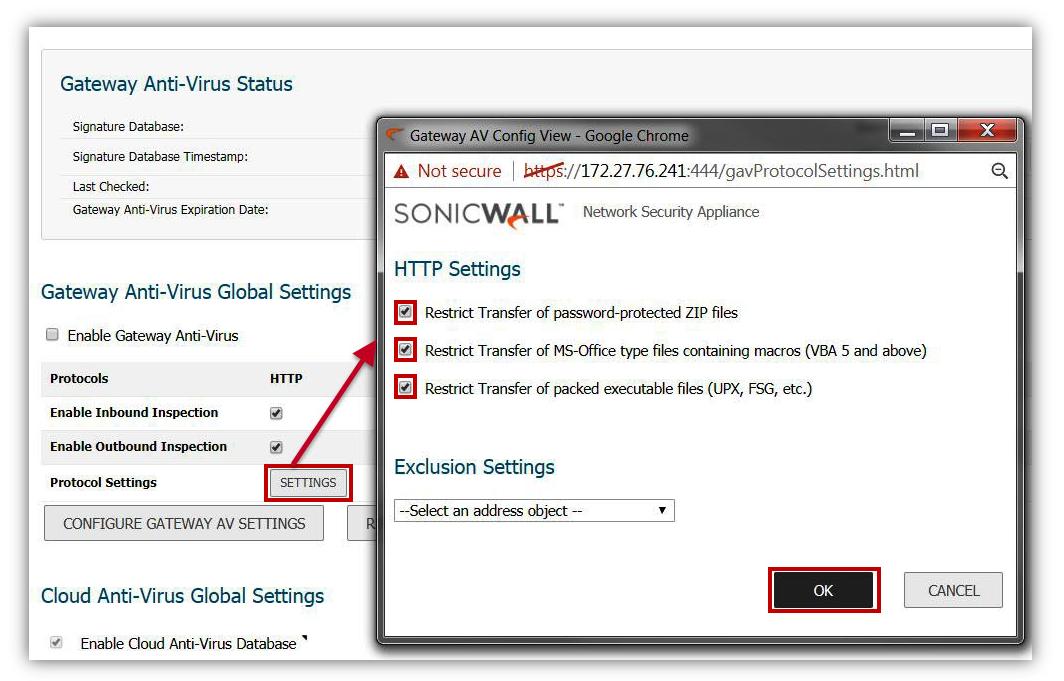
- Click Configure Gateway AV Settings.
- Enable the option to Block files with multiple levels of zip/zip compression.
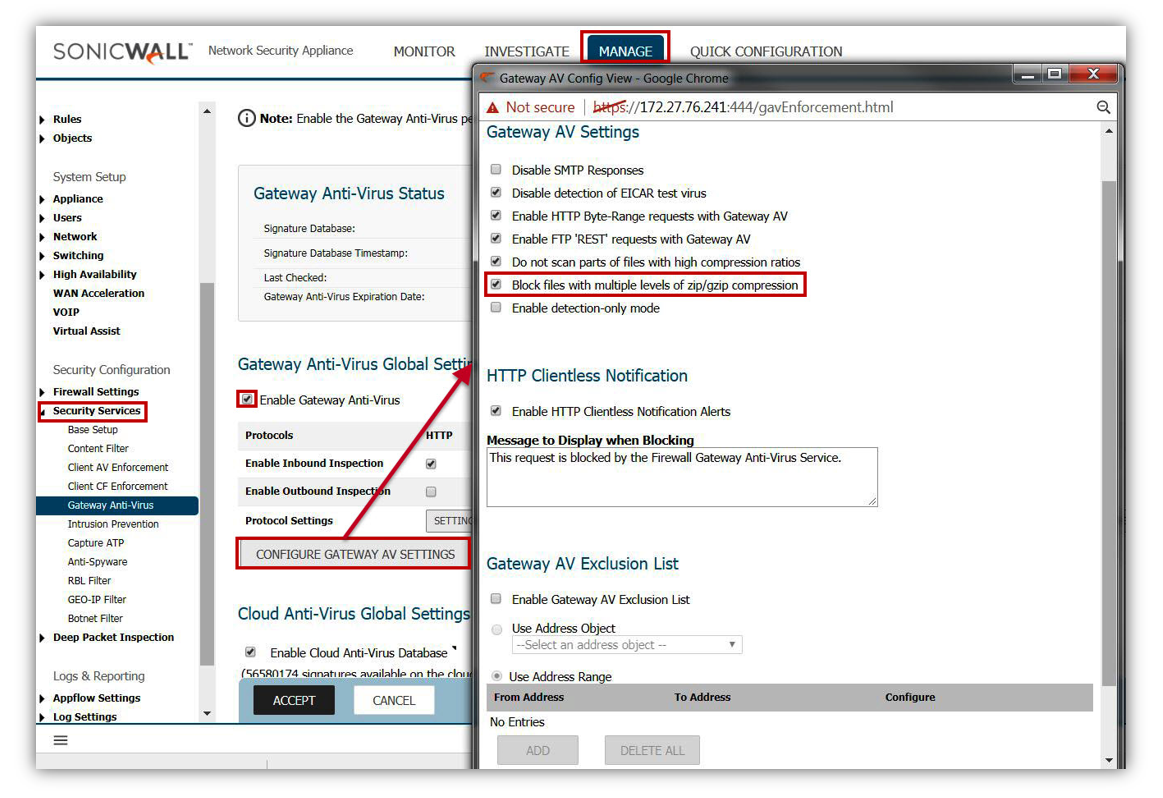
Enable Intrusion Prevention
Many of today's modified Ransomware exploits include malicious Trojans and worm elements, exploiting network communications, and impacting systems. Intrusion Prevention is an essential cornerstone of preventing these attacks in networks.
- Make sure that the SonicWall has the latest signature updates from the SonicWall Capture Labs.
- Enable the IPS Service.
- Enable Prevention for (at a minimum) of High and Medium Threats, but may need to include Low Priority based on additional requirement and compliance regulations based on the network being deployed.
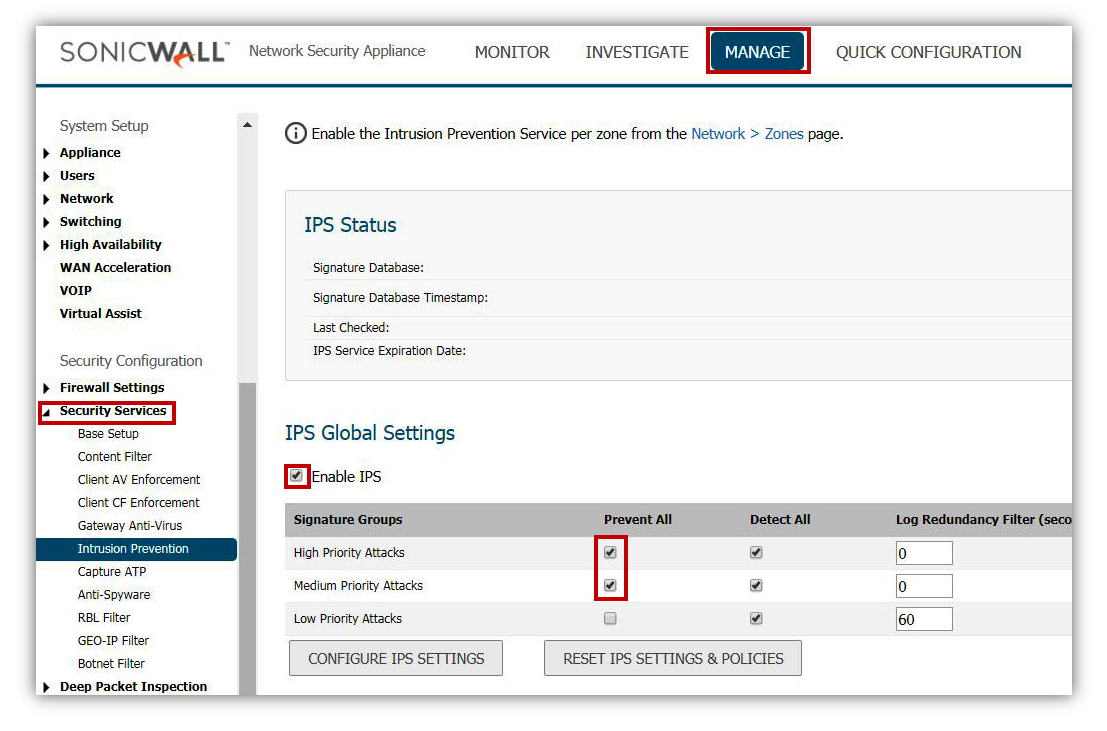
- Enable Intrusion Detection if log data of intrusion information is required. SonicWall Intrusion Detection is responsible for providing the log event of Intrusions. If not selected log data will not be created.
Enable Geo-IP Filter
Geo-IP Filter is able to control traffic to and from various countries, and is a core component of the CGSS/AGSS security subscription.
- Enable Geo-IP Filter
- This can be setup on All Connections or Firewall Rule Based.
- All Connections will include all traffic, but default rules would be to exclude Firewall Subnets.
- Firewall Rule Based requires enabling the service on individual rules within Firewall Access Rules. If this method is applied, any rules for WAN to WAN, WAN to LAN, and LAN to WAN should be enabled.
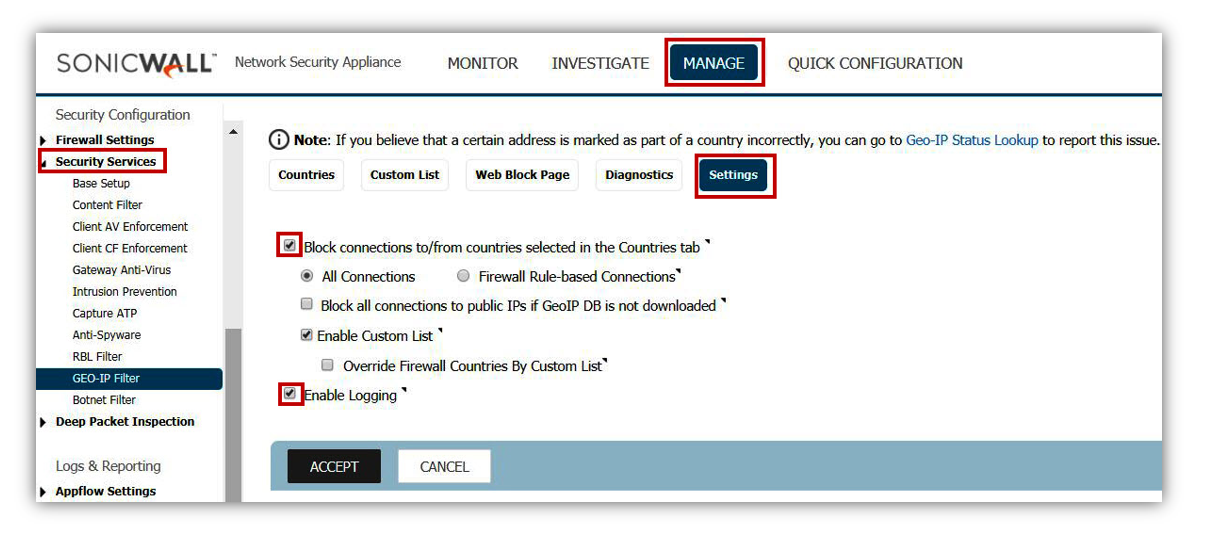
- Make sure that traffic to Anonymous Proxy / Private IP is selected at a minimum from the country list.
- Make sure that Block all UNKNOWN countries is also enabled.
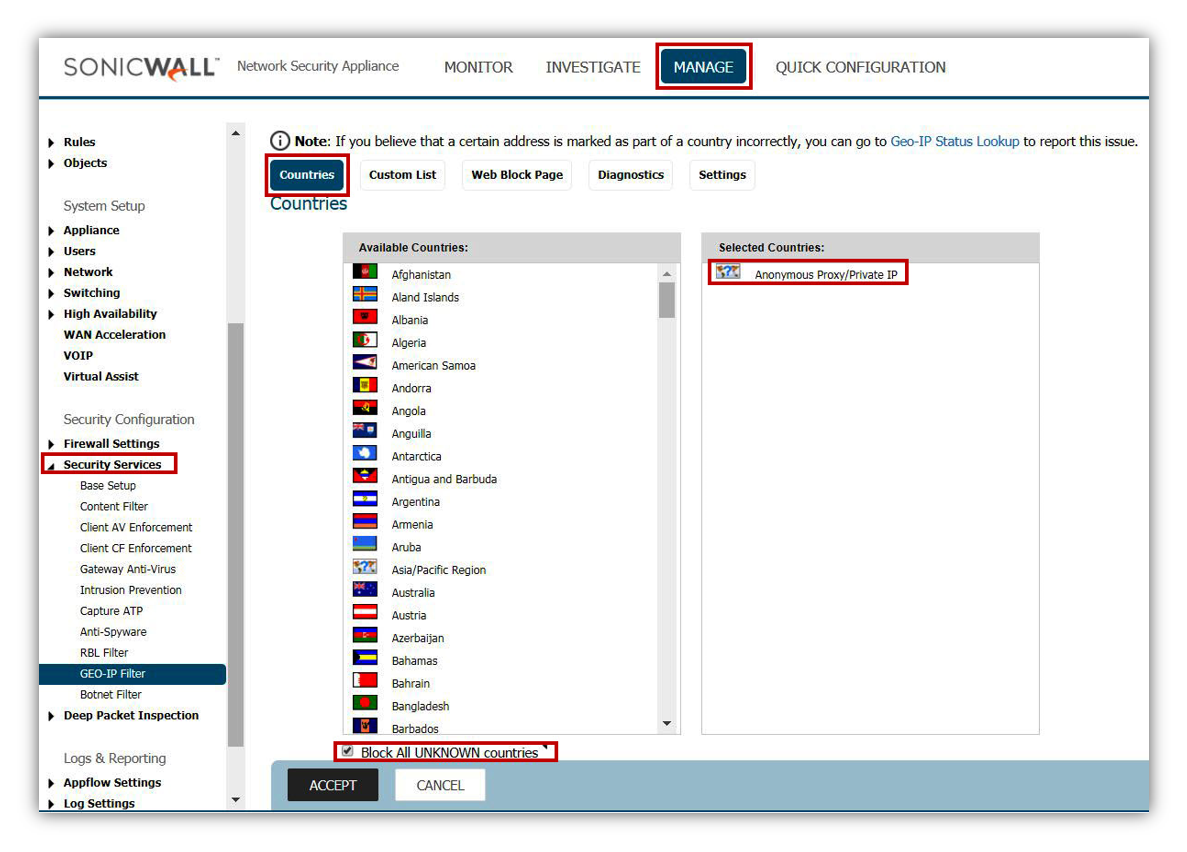
Enable Botnet Filter
Botnet Filter is able to prevent traffic to or from known malicious hosts that act as Botnet networks.
- Enable Botnet Filter.
- This can be setup on All Connections or Firewall Rule Based.
- All Connections will include all traffic, but default rules would be to exclude Firewall Subnets.
- Firewall Rule Based requires enabling the service on individual rules within the Firewall Access Rules. If this method is applied, any rules for WAN to WAN, WAN-> Internal or Internet->WAN should be enabled.
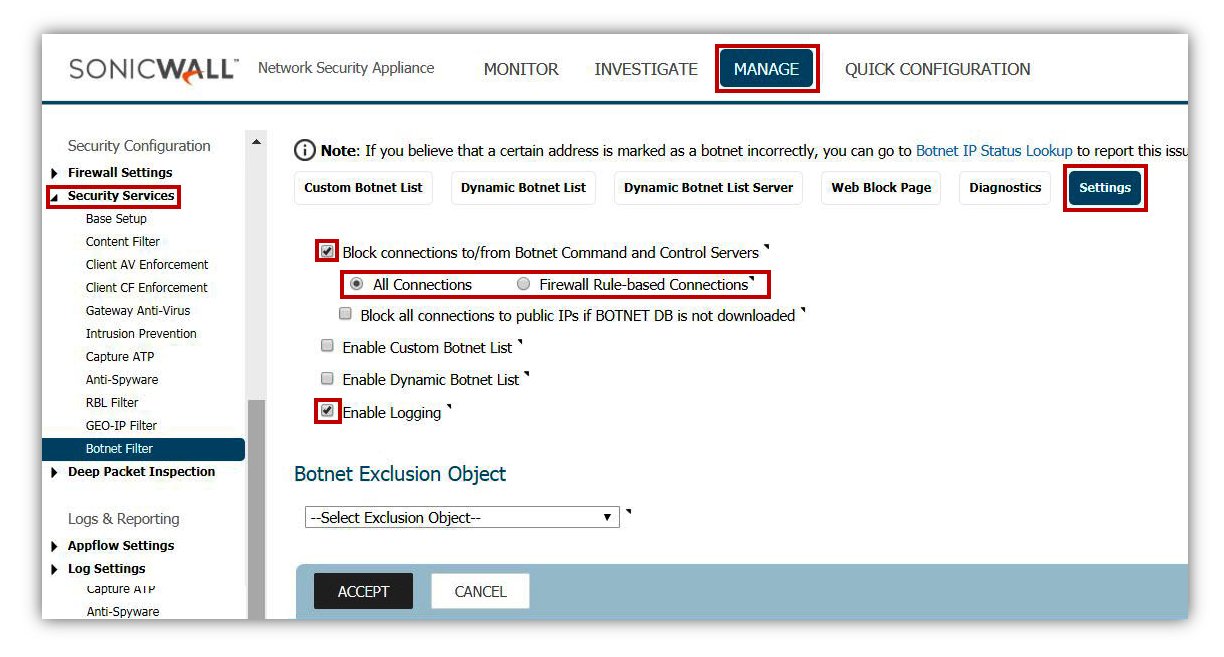
Enable DPI-SSL Client Inspection
The DPI-SSL Feature of the firewall delivers the ability to inspect within encrypted communications on multiple protocols and applications. DPI-SSL enables the firewall to act as a proxy to inspect encrypted communications such as Webmail, social media, and other web contact leveraging HTTPS connections. The settings for DPI-SSL specifically as it applies to this article is relatively simple. For questions on the setup and deployment of DPI-SSL please consult the Where Can I Learn More About DPI-SSL?.
- Enable SonicWall DPI-SSL on the firewall.
- Ensure that the services is enabled for all sub-functions including.
- Intrusion Prevention
- Gateway Anti-Virus
- Gateway Anti-Spyware
- Application Firewall
- Content Filter
Configure Content Filtering Service
The Content Filtering rules outlined here apply to configurations for Firmware 6.2.7.1, and are based on CFS v4.0. For the purposes of preventing Ransomware, it is recommended to block access to the following categories: Malware, Hacking / Proxy Avoidance, and Not Rated.
 NOTE: Blocking the category 'Not Rated' can be management intensive as not all websites that specific networks use has been rated. Submissions for Not Rated Sites can be submitted online at Report Issues.
NOTE: Blocking the category 'Not Rated' can be management intensive as not all websites that specific networks use has been rated. Submissions for Not Rated Sites can be submitted online at Report Issues.
- Ensure that default and custom policies for user groups are all set to Block Malware, Hacking / Proxy Avoidance, and Not Rated.
Enable Application Firewall Rules
In order to safeguard against common methods of newer generation of obfuscation leveraging traditional applications, it is recommended to enable various Application Firewall Rules. In order to prevent malware such as Ransomware from being able to circumvent enforced communications, it is advised to build rules to restrict DNS, SSH, and Proxy-Access Applications.
- While DNS is typically TCP/UDP 53, the DNS protocol can be used on non-standard ports. Malicious applications will leverage DNS Cache Poisoning, or redirect traffic to illegitimate sites. It is advised to lock down not only access rules to specify Trusted DNS Hosts, but to also create an Address Object and Application Rule to restrict the DNS protocol to only the Trusted DNS Host.
- This security mechanism can also be applied with SonicWall's DNS Proxy configuration as an alternative, however this will still require application and access rules to restrict DNS to untrusted sources.
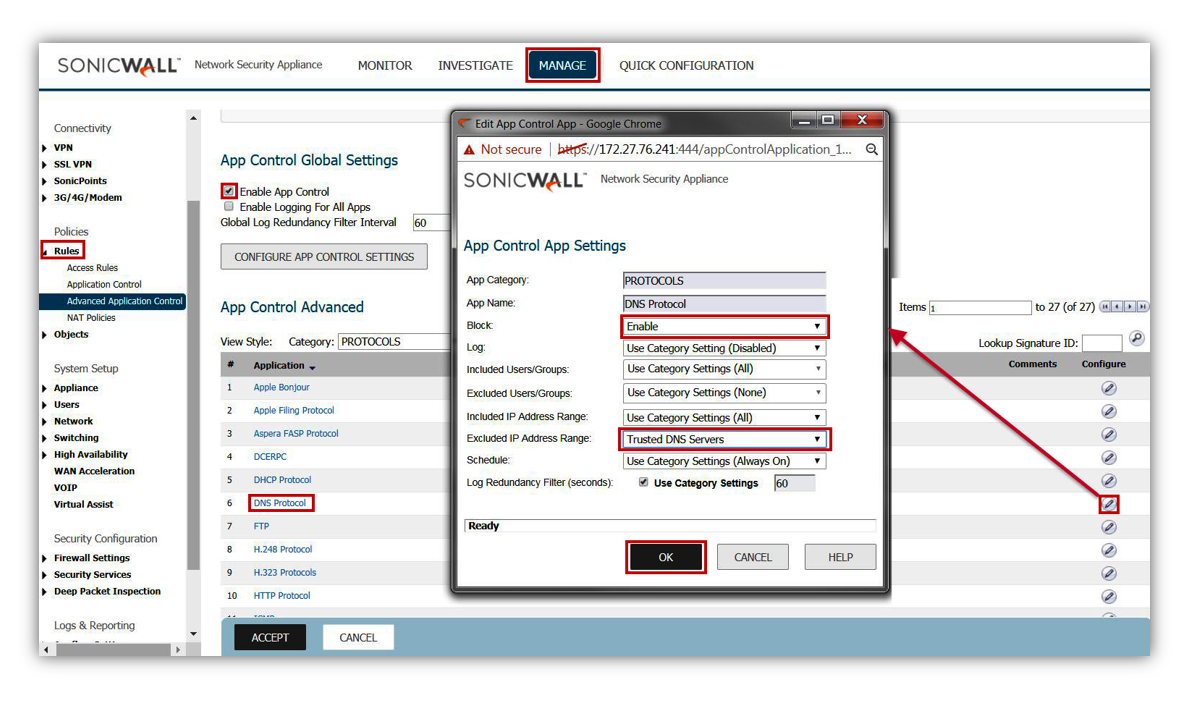
- The next application rule would be to restrict SSH Connections to only trusted and trained users, from only trusted sources, or to only trusted destinations.
- It is advised to create this control as an Application Firewall rule, as it is possible to deviate from the standard SSH TCP 22 configuration.
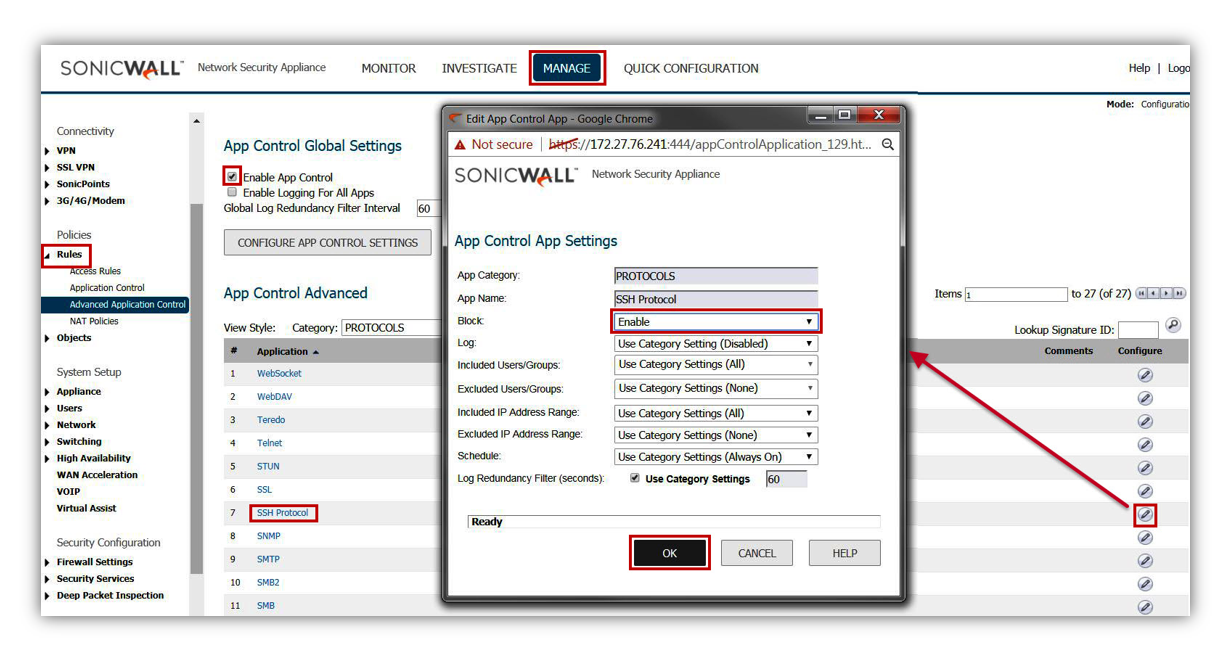
- The last Application Firewall policy that should be created is the prevention of all Proxy-Access Applications.
- By blocking this entire category there is the potential for legitimate applications to also break or cease to function properly. It is advised that these applications be reviewed and exceptions be created where applicable for the source and destination specific information for those specific applications.
Enable Capture
Given the dynamic and constant creation of new malware, it is highly advised that the SonicWall Capture solution. Be advised this requires the AGSS (Advanced Gateway Security Suite) License.
- Enable Capture, and ensure that Gateway Anti-Virus is enabled on all services.
- Ensure that all file types are selected for inspection.
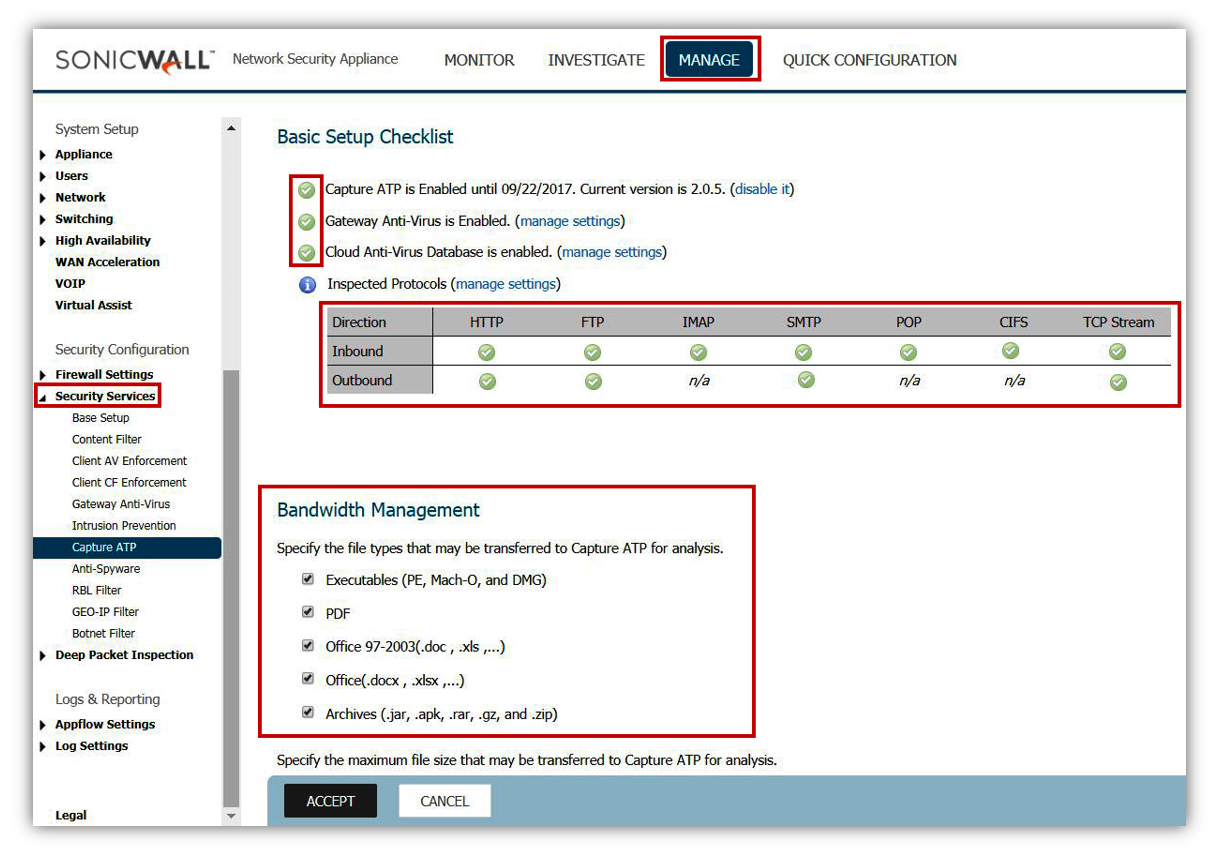
- It is recommended to enable Capture to 'Block until verdict'. This will prevent malware from passing through the system until properly tested.
Additional suggestions to prevent Ransomware exploits may include, but not limited to.
- Installing end-point Anti-Virus software and keeping it updated with the latest signatures.
- Updating host Operating Systems, browsers, and browser Plugin with the latest security patches.
- Performing regular offline (cold) system back-ups.
- Educating users on the dangers of opening unknown files from unknown sources, etc.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Security Services Subscription
For all SonicWall appliances it is highly recommend to include the Advanced Gateway Security Suite (AGSS), which includes active subscriptions for Gateway Anti-Virus, Intrusion Prevention, Anti-Spyware, Content Filtering, Botnet Filter, Geo IP Filter, Application Firewall, DPI-SSL, DPI-SSH, and Capture. If this subscription is not active then updates and configurations will not be possible.
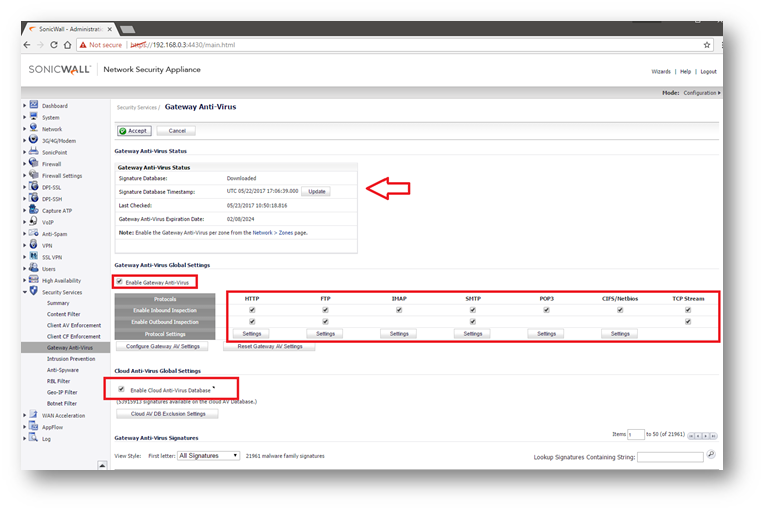
Enable Gateway Anti-Virus
- Make sure that GAV is updated with latest signatures
- Enable GAV
- Enable Cloud GAV
- Enable Inspection on Inbound and Outbound for all HTTP, FTP, IMAP, SMTP, POP3, CIFS/NetBIOS, and TCP Stream.
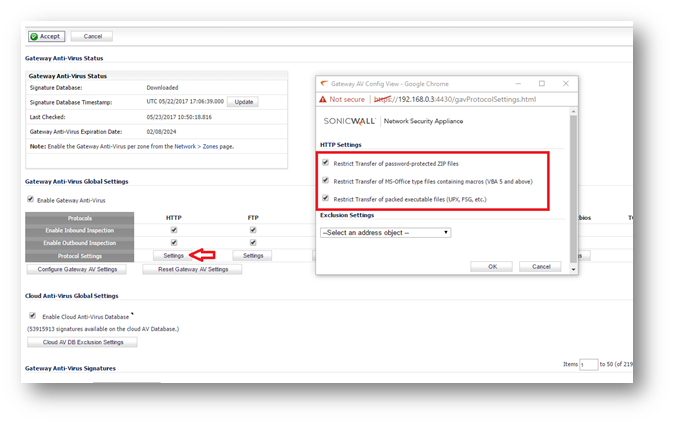
- Inside the Settings of the protocols make sure that you have enabled the option to block.
- Restrict Transfer of password-protected ZIP files.
- Restrict Transfer of MS-Office type files containing macros (VBA 5 and above).
- Restrict Transfer of packed executable files (UPX, FSG, etc).
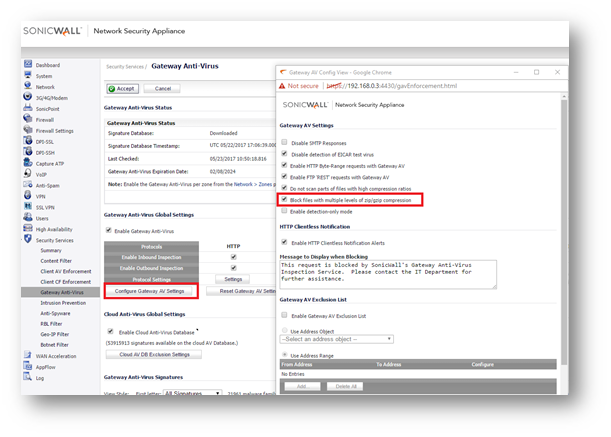
- Click Configure Gateway AV Settings.
- Enable the option to Block files with multiple levels of zip/zip compression.
Enable Intrusion Prevention
Many of today's modified Ransomware exploits include malicious Trojans and worm elements, exploiting network communications, and impacting systems. Intrusion Prevention is an essential cornerstone of preventing these attacks in networks.
- Make sure that the SonicWall has the latest signature updates from the SonicWall Capture Labs.
- Enable the IPS Service.
- Enable Prevention for (at a minimum) of High and Medium Threats, but may need to include Low Priority based on additional requirement and compliance regulations based on the network being deployed.
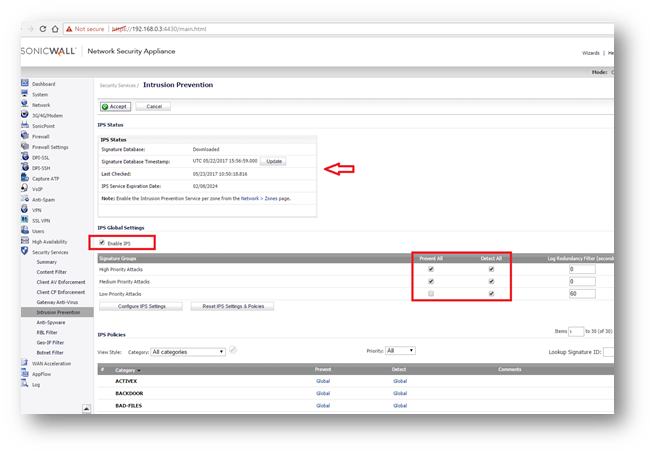
- Enable Intrusion Detection if log data of intrusion information is required. SonicWall Intrusion Detection is responsible for providing the log event of Intrusions. If not selected log data will not be created.
Enable Geo-IP Filter
Geo-IP Filter is able to control traffic to and from various countries, and is a core component of the CGSS/AGSS security subscription.
- Enable Geo-IP Filter
- This can be setup on All Connections or Firewall Rule Based.
- All Connections will include all traffic, but default rules would be to exclude Firewall Subnets.
- Firewall Rule Based requires enabling the service on individual rules within Firewall Access Rules. If this method is applied, any rules for WAN to WAN, WAN to LAN, and LAN to WAN should be enabled.
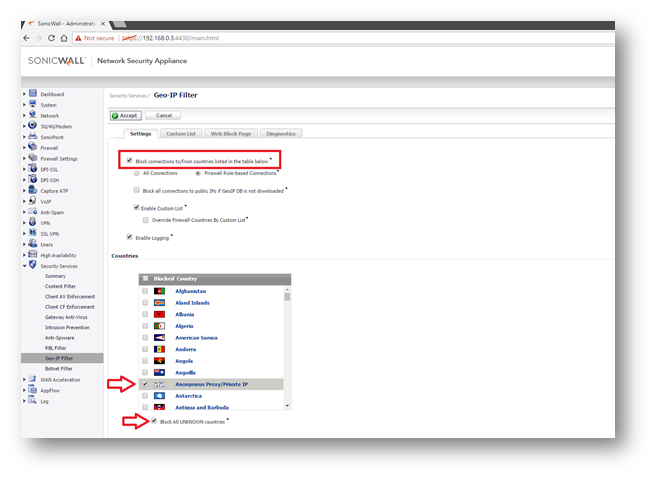
- Make sure that traffic to 'Anonymous Proxy / Private IP' is selected at a minimum from the country list.
- Make sure that Block all UNKNOWN countries is also enabled.
Enable Botnet Filter
Botnet Filter is able to prevent traffic to or from known malicious hosts that act as Botnet networks.
- Enable Botnet Filter.
- This can be setup on All Connections or Firewall Rule Based.
- All Connections will include all traffic, but default rules would be to exclude Firewall Subnets.
- Firewall Rule Based requires enabling the service on individual rules within the Firewall Access Rules. If this method is applied, any rules for WAN to WAN WAN-> Internal or Internet->WAN should be enabled.

Enable DPI-SSL Client Inspection
The DPI-SSL Feature of the firewall delivers the ability to inspect within encrypted communications on multiple protocols and applications. DPI-SSL enables the firewall to act as a proxy to inspect encrypted communications such as Webmail, social media, and other web contact leveraging HTTPS connections. The settings for DPI-SSL specifically as it applies to this article is relatively simple. For questions on the setup and deployment of DPI-SSL please consult the Where Can I Learn More About DPI-SSL?.
- Enable SonicWall DPI-SSL on the firewall.
- Ensure that the services is enabled for all sub-functions including.
- Intrusion Prevention
- Gateway Anti-Virus
- Gateway Anti-Spyware
- Application Firewall
- Content Filter

Configure Content Filtering Service
The Content Filtering rules outlined here apply to configurations for firmware 6.2.7.1, and are based on CFS v4.0. For the purposes of preventing Ransomware, it is recommended to block access to the following categories: Malware, Hacking / Proxy Avoidance, and Not Rated.
 NOTE: blocking the category 'Not Rated' can be management intensive as not all websites that specific networks use has been rated. Submissions for Not Rated Sites can be submitted online at Report Issues.
NOTE: blocking the category 'Not Rated' can be management intensive as not all websites that specific networks use has been rated. Submissions for Not Rated Sites can be submitted online at Report Issues.
- Ensure that default and custom policies for user groups are all set to Block Malware, Hacking / Proxy Avoidance, and Not Rated

Enable Application Firewall Rules
In order to safeguard against common methods of newer generation of obfuscation leveraging traditional applications, it is recommended to enable various Application Firewall Rules. In order to prevent malware such as Ransomware from being able to circumvent enforced communications, it is advised to build rules to restrict DNS, SSH, and Proxy-Access Applications.
- While DNS is typically TCP/UDP 53, the DNS protocol can be used on non-standard ports. Malicious applications will leverage DNS Cache Poisoning, or redirect traffic to illegitimate sites. It is advised to lock down not only access rules to specify Trusted DNS Hosts, but to also create an Address Object and Application Rule to restrict the DNS protocol to only the Trusted DNS Host.
- This security mechanism can also be applied with SonicWall's DNS Proxy configuration as an alternative, however this will still require application and access rules to restrict DNS to untrusted sources.
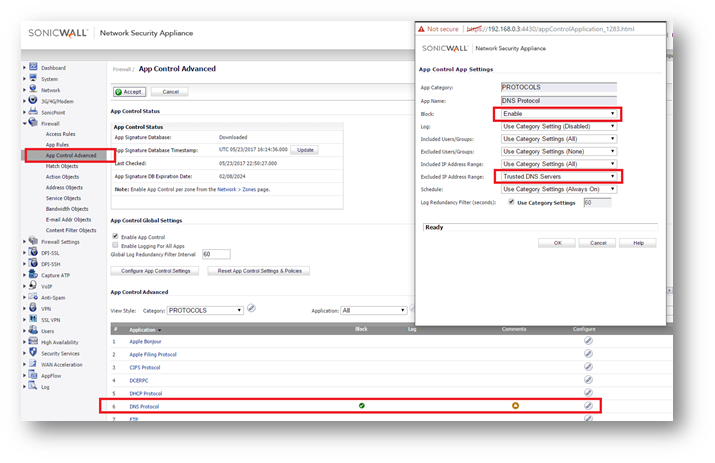
- The next application rule would be to restrict SSH Connections to only trusted and trained users, from only trusted sources, or to only trusted destinations.
- It is advised to create this control as an Application Firewall rule, as it is possible to deviate from the standard SSH TCP 22 configuration.

- The last Application Firewall policy that should be created is the prevention of all Proxy-Access Applications.

- By blocking this entire category there is the potential for legitimate applications to also break or cease to function properly. It is advised that these applications be reviewed and exceptions be created where applicable for the source and destination specific information for those specific applications.
Enable Capture
 NOTE: Given the dynamic and constant creation of new malware, it is highly advised that the SonicWall Capture solution. Be advised this requires the AGSS (Advanced Gateway Security Suite) License.
NOTE: Given the dynamic and constant creation of new malware, it is highly advised that the SonicWall Capture solution. Be advised this requires the AGSS (Advanced Gateway Security Suite) License.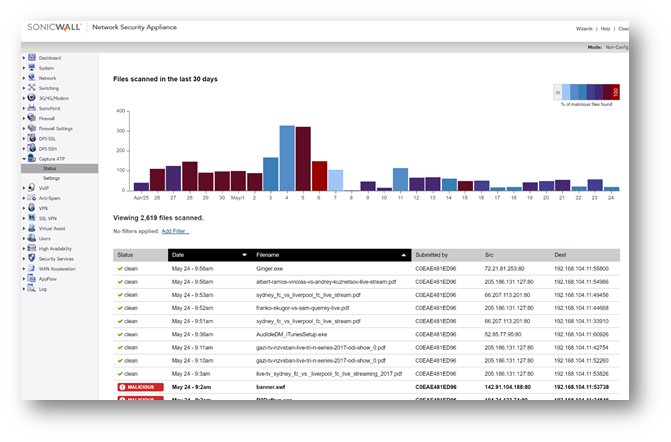
- Enable Capture, and ensure that Gateway Anti-Virus is enabled on all services.
- Ensure that all file types are selected for inspection.
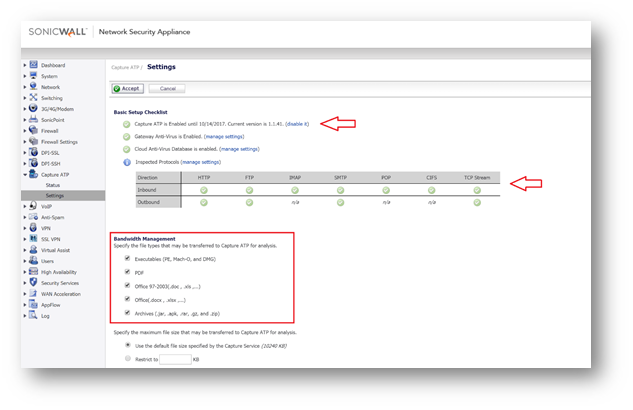
- It is recommended to enable Capture to Block until verdict. This will prevent malware from passing through the system until properly tested.
Additional suggestions to prevent Ransomware exploits may include, but not limited to.
- Installing end-point Anti-Virus software and keeping it updated with the latest signatures.
- Updating host Operating Systems, browsers, and browser Plugin with the latest security patches.
- Performing regular offline (cold) system back-ups.
- Educating users on the dangers of opening unknown files from unknown sources, etc.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > NSa Series > IPS/GAV/Spyware
- Firewalls > NSv Series > IPS/GAV/Spyware
- Firewalls > TZ Series > IPS/GAV/Spyware






 YES
YES NO
NO