-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
CFS: Enforcing Content Filter Policies on IP Addresses based on Schedules



Description
Feature/Application:
Configuring Content Filter Policies for limiting Internet access to certain times of the day using Schedules and enforcing it on IP addresses.
- This article gives step by step configuration that allows administrators to enforce time-based Internet access along with content filtering on IP addresses.
- In order to assign custom content filter polices on IP addresses the SonicWall must have premium content filter subscription and be running SonicOS Enhanced firmware5.2 and later.
 NOTE:CFS Premium version is required to create custom CFS policies.
NOTE:CFS Premium version is required to create custom CFS policies.
For the purpose of this article we configure the followings Scenario.
- An IP Addressrange to be able to access the Internet only between 8:00AM and 5:00PM from Monday to Friday.
- Another range of IP Address to be able to access the Internet only during lunch time between 1:00PM and 2:00PM from Monday to Friday.
- Even during this period Internet access would be based on the categories allowed in the CFS policy.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Creating Schedules
SonicWall has a number of pre-configured Schedules which are for various time periods and can be used for various purposes, if suitable. For this scenario we select the pre-configured Schedule, Work Hours, which will suit our purpose as it is between 8:00 AM and 5:00 PM from Monday to Friday. For the lunchtime schedule we create a new one.
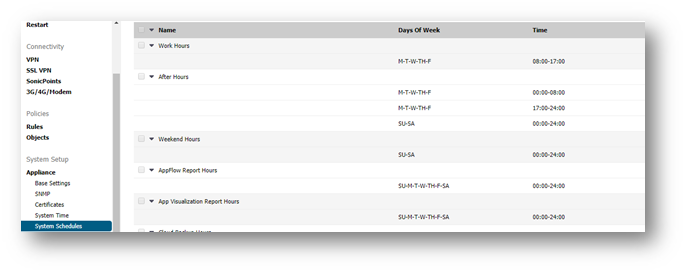
- Login to the SonicWall management Interface.
- Navigate to the Appliance | System Schedules page.
- Click Add.
- Set Schedule Name as Lunchtime
- Set Schedule type as Recurring
- Select the boxes under Mon,Tue,Wed,Thurs,Fri under Recurring.
- Set Start Time as 13:00 and Stop Time as 14:00
- Click Add to add this time under Schedule List.
- Click OK .
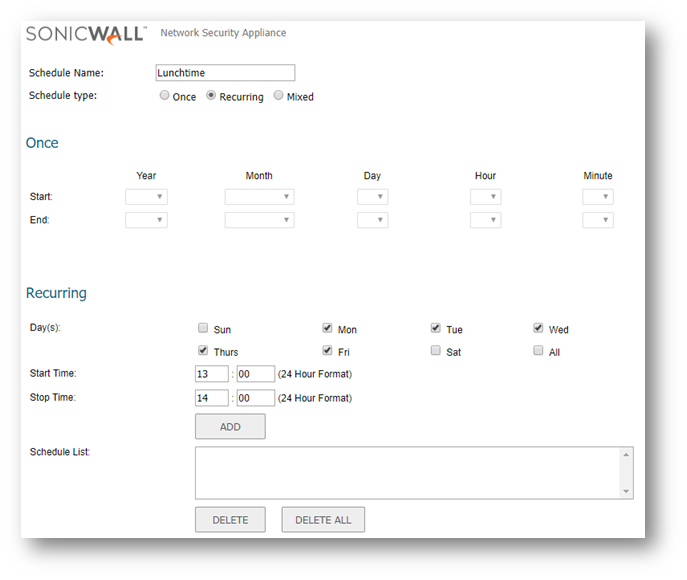
Set the Default CFS Policy as the most restrictive
- Navigate to Security Services | Content Filter
- Click on Objects|Content Filter Objects page(Link inside the Note) .
- Under CFS Profile objects.
- Click Configure on the Default Policy.
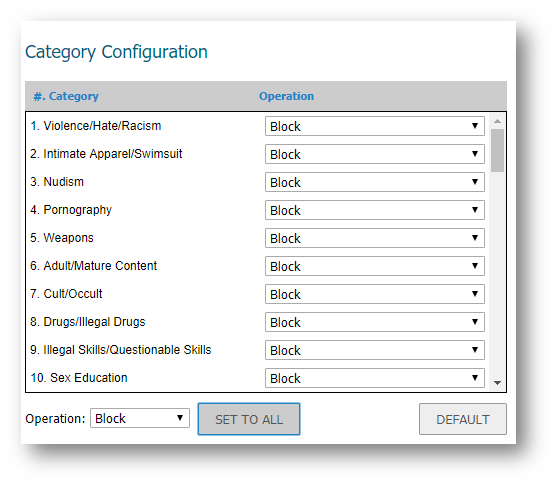
- Under settings | Category Configuration.
- Set Operation to Block and click SET TO ALL(Please note: This would block all access to the Internet therefore do not enable CFS yet on LAN or DMZ zones).
- Click OK .
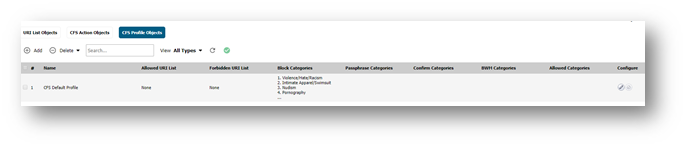
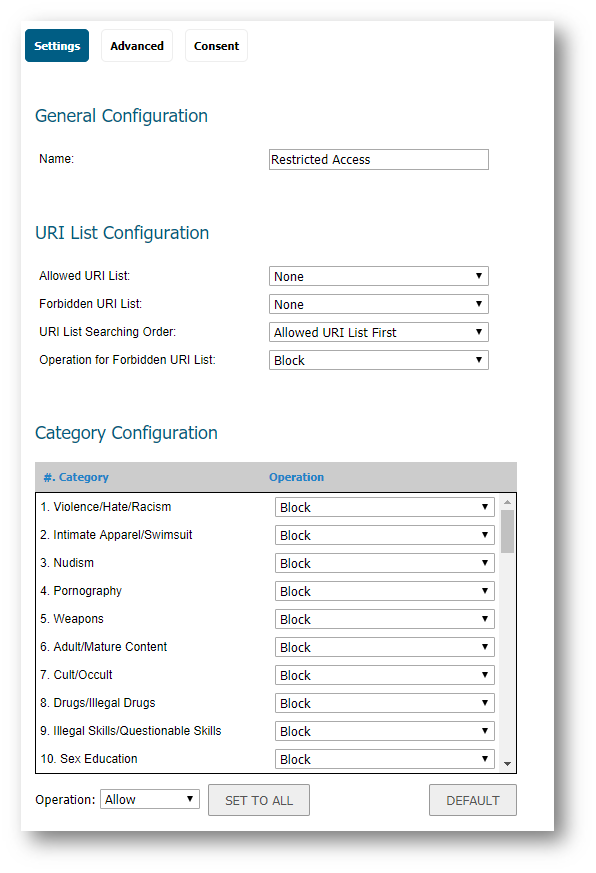
Creating new CFS Profile - Restricted Access
- Under the CFS Profile Objects tab click on the Add button.
- Enter a name for the new profile. For eg. Restricted Access
- Under the Category configuration select the categories to be blocked.
- Under Security Services | Content Filtering
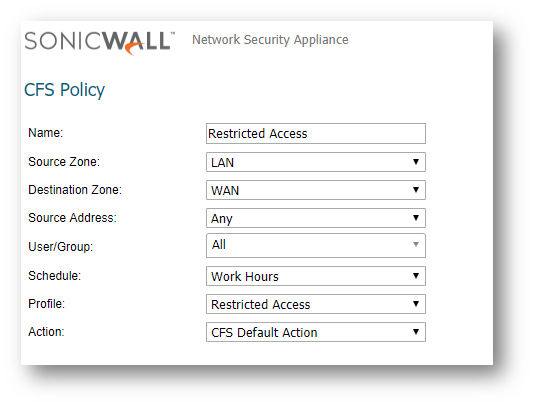
- Create a new CFS Policy.
 EXAMPLE: Restricted Access.
EXAMPLE: Restricted Access. - Select Schedule as Work Hours.
- Select Profile as Restricted access.
- Click OK .
Creating new CFS Profile -Lunchtime Access (Under objects | Content Filter objects)
- Under the CFS Profile objects tab click on the Add button.
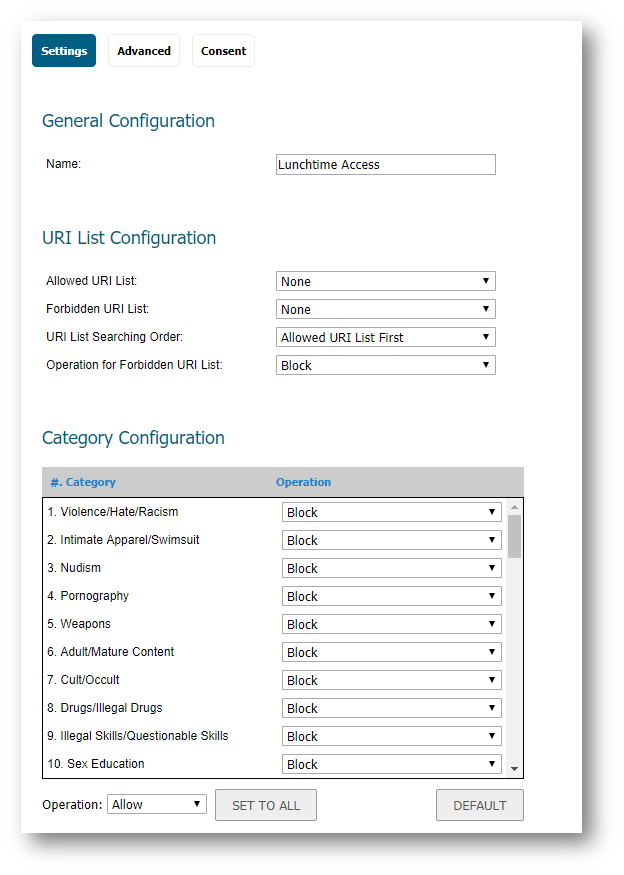
- Enter a name for the new policy. For eg. Lunchtime Access.
- Under the Category Configuration tab select the categories to be blocked.
- Under Security Services | Content Filtering.
- Create a new CFS Policy.
 EXAMPLE: Lunchtime Access.
EXAMPLE: Lunchtime Access. - Select Schedule as Lunchtime.
- Select Profile as Lunchtime Access.
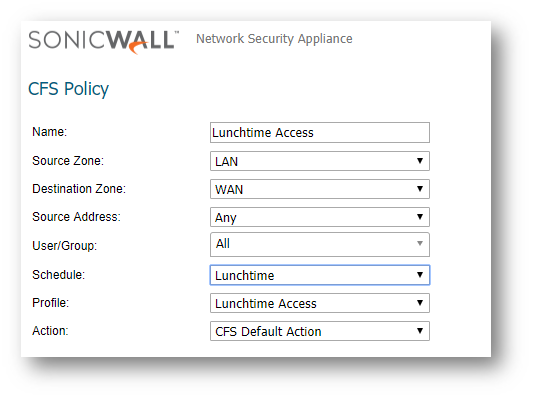
- Now that custom policies have been created, it must be enforced on IP address ranges.
Assigning CFS Policies on IP Addresses
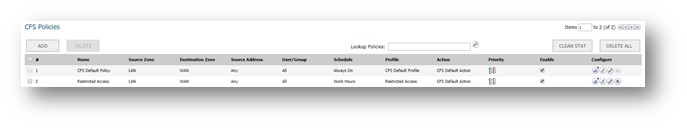
The option CFS Policy per IP Address Range is available on the SonicWall Security Services | Content Filter page. Edit policy on which IP address range has to be assigned.
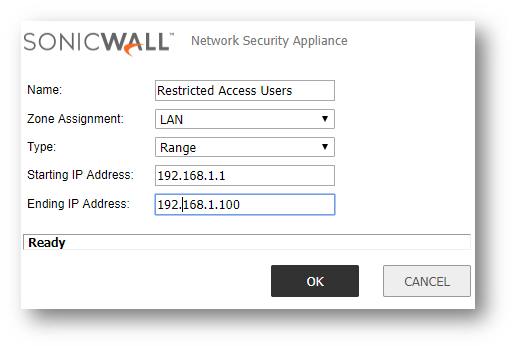
- Click Edit button(Restricted access policy).
- Under Source ,Create a new address object.
- Starting IP Address From enter 192.168.1.1.
- Ending Address To enter 192.168.1.100.
- Click OK.
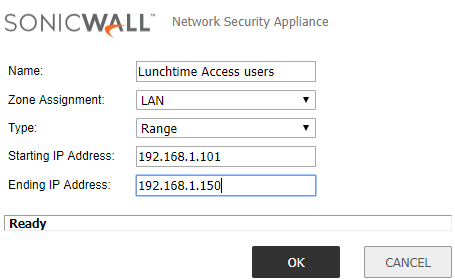
- Click Edit button(Lunch Access policy).
- Under Source ,Create a new address object.
- Starting IP Address From enter 192.168.1.101
- Ending Address To enter 192.168.1.150
- Click OK .
Enabling CFS
- Security Services | Content Filter, Under Global settings, tick of checkbox Enable Content Filtering Service.
How to Test
In order to test the above scenario, have hosts with IP address in the range 192.168.1.101 to 192.168.150 go online during Lunchtime (1PM to 2PM) hours and outside Lunchtime hours. If the hosts are unable to go online outside Lunchtime hours and able to go online during Lunchtime hours then the Schedule configured in the CFS Policy assigned to the IP address range is being successfully enforced. However, hosts within the IP range will not be able to access any sites belonging to the blocked CFS categories at any time of the day.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Creating Schedules
SonicWall has a number of pre-configured Schedules which are for various time periods and can be used for various purposes, if suitable. For this scenario we select the pre-configured Schedule, Work Hours, which will suit our purpose as it is between 8:00 AM and 5:00 PM from Monday to Friday. For the lunchtime schedule we create a new one.
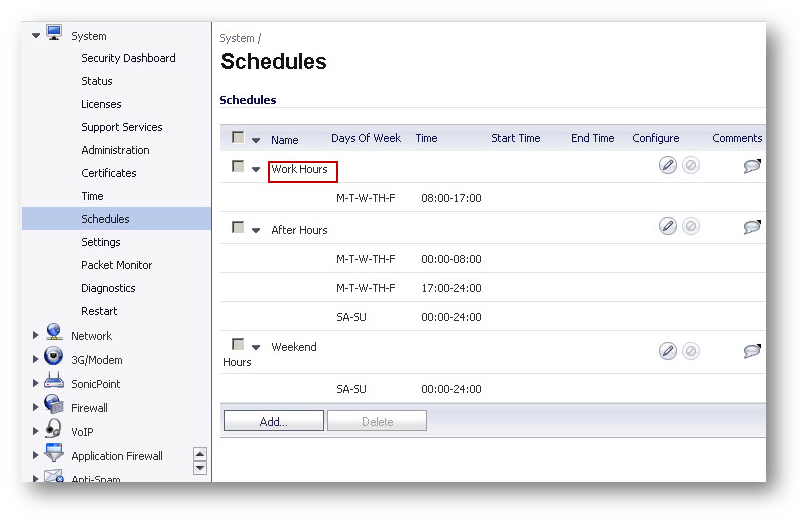
- Login to the SonicWall management Interface.
- Navigate to System | Schedules page.
- Click Add.
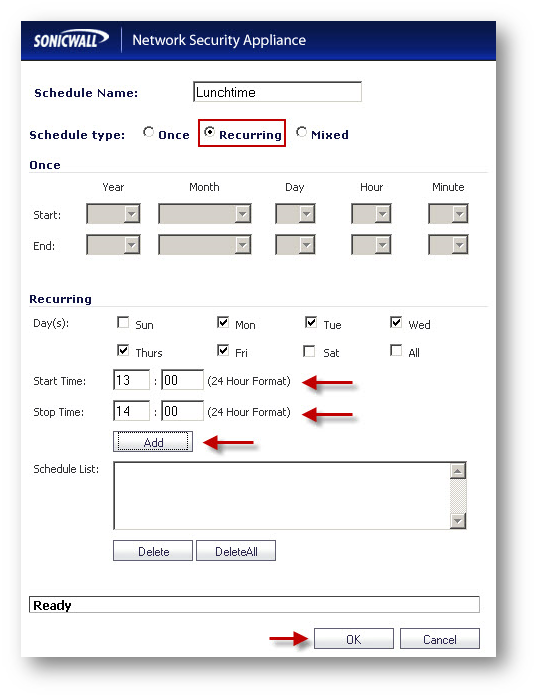
- Set Schedule Name as Lunchtime.
- Set Schedule type as Recurring.
- Select the boxes under Mon,Tue,Wed,Thurs,Fri under Recurring.
- Set Start Time as 13:00 and Stop Time as 14:00.
- Click Add to add this time under Schedule List.
- Click OK .
Set the Default CFS Policy as the most restrictive
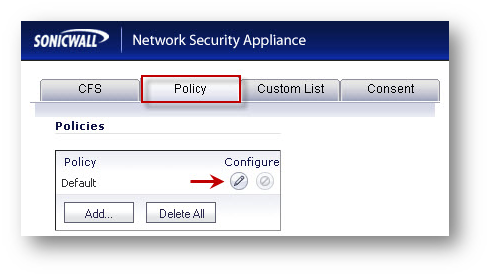
- Navigate to Security Services | Content Filter.
- Click Configure against SonicWall CFS.
- In the SonicWall Filter Properties windows, click Policy tab.
- Click Configure on the Default Policy.
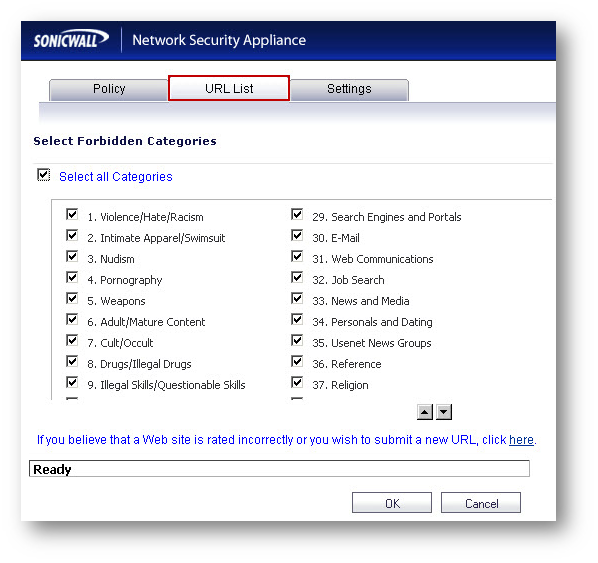
- Click URL List tab.
- Check the box under Select all Categories (Please note: This would block all access to the Internet therefore do not enable CFS yet on LAN or DMZ zones).
- Click OK .
Creating new CFS Policy - Restricted Access
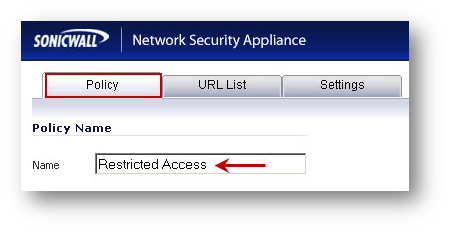
- Under Policy tab click Add.
- Enter a name for the new policy.
 EXAMPLE: Restricted Access.
EXAMPLE: Restricted Access. - Under the URL List tab select the categories to be blocked.
- Click Settings tab
- Under Filter Forbidden URLs by time of day select Work Hours. This is one of the pre-configured schedules.
- Click OK.
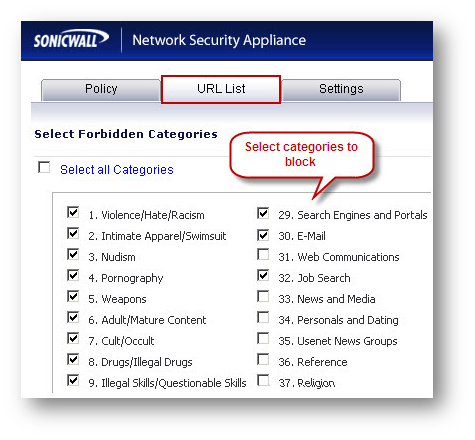
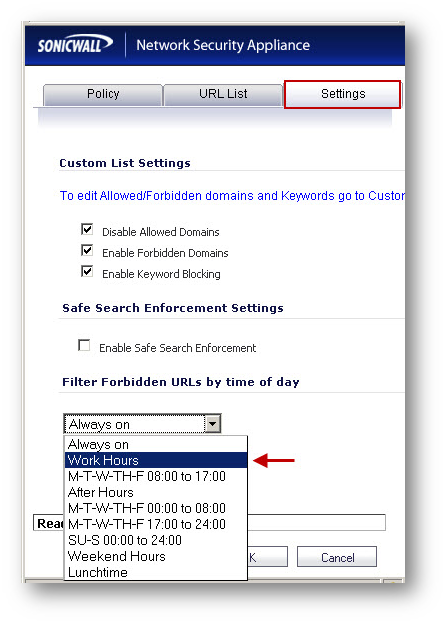
Creating new CFS Policy -Lunchtime Access
- Under the Policy tab click Add.
- Enter a name for the new policy.
 EXAMPLE: Lunchtime Access.
EXAMPLE: Lunchtime Access. - Under the URL List tab select the categories to be blocked.
- Click Settings.
- Under Filter Forbidden URLs by time of day select Lunchtime. This is the newly added custom schedule.
- Click OK .
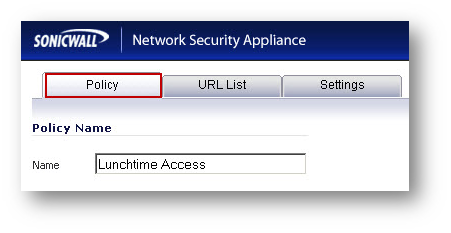
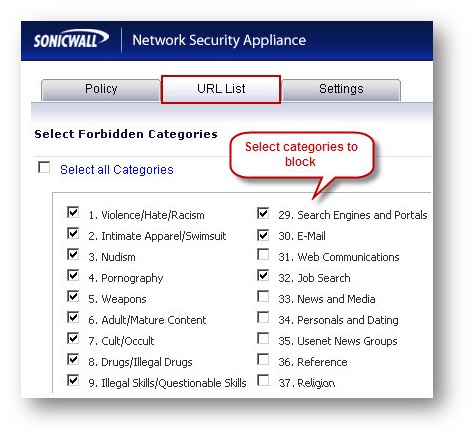
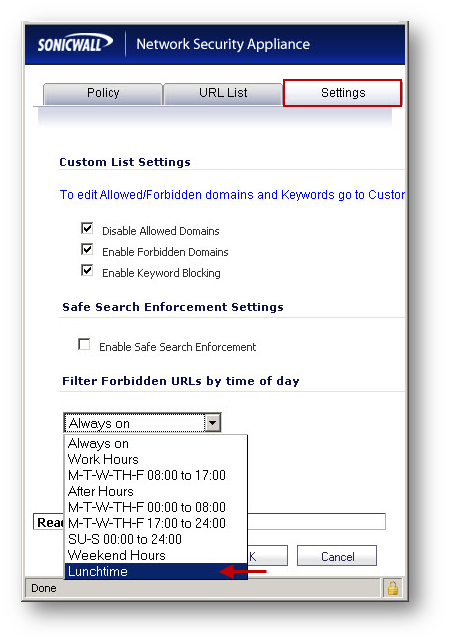
- Now that custom policies have been created, it must be enforced on IP Address ranges.
Assigning CFS Policies on IP Addresses
The option CFS Policy per IP Address Range is available on the SonicWall Security Services | Content Filter page. Scroll down the Content Filter page and check the box under Enable Policy per IP Address Range.
- Click Add .
- Under IP Address From enter 192.168.1.1.
- Under IP Address To enter 192.168.1.100.
- From the drop-down menu under CFS Policy, select Restricted Access.
- Click OK .
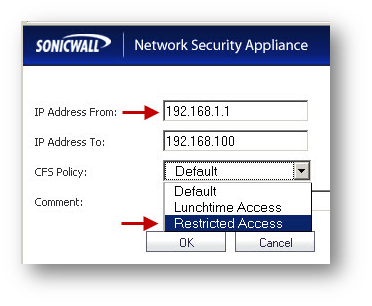
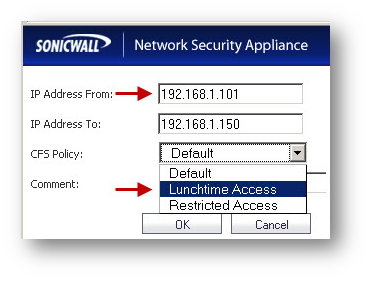
- Click Add .
- Under IP Address From enter 192.168.1.101.
- Under IP Address To enter 192.168.1.150.
- From the drop-down menu under CFS Policy, select Lunchtime Access.
- Click OK .
- Click Accept .
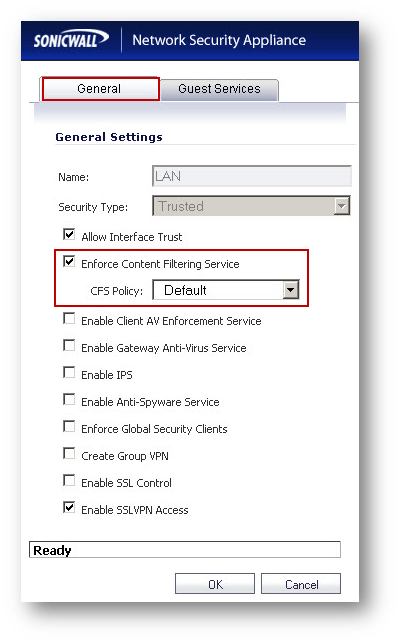
Enabling CFS on zones
- Navigate to Network |Zones.
- Click configure on LAN or DMZ zone.
- Check the box under : Enforce Content Filtering Service..
- Select the CFS Policy as Default.
- Click OK .
How to Test
In order to test the above scenario, have hosts with IP address in the range 192.168.1.101 to 192.168.150 go online during Lunchtime (1PM to 2PM) hours and outside Lunchtime hours. If the hosts are unable to go online outside Lunchtime hours and able to go online during Lunchtime hours then the Schedule configured in the CFS Policy assigned to the IP address range is being successfully enforced. However, hosts within the IP range will not be able to access any sites belonging to the blocked CFS categories at any time of the day.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Content Filtering Service
- Firewalls > NSv Series > Content Filtering Service
- Firewalls > TZ Series > Content Filtering Service






 YES
YES NO
NO