-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
CFS: Content Filtering Service (CFS) 3.0 Overview - SonicOS 5.8 and above.



Description
CFS: Content Filtering Service (CFS) 3.0 Overview - SonicOS 5.8 and above.
Resolution
Feature/Application:
Starting with SonicOS 5.8.0.0, SonicWall Content Filtering can also be configured using Application Firewall Infrastructure (App Rules) in addition to the legacy CFS that uses User Groups and Zones (Pre SonicOS 5.8.0.0) Enforcement.
This article describes all aspects of configuring Content Filtering Service 3.0.
- Using Application Firewall Infrastructure (CFS 3.0)
- How CFS evaluates policies
- CFS Via User and Zone Screens (CFS 2.0)
- CFS - Global Enhancements
- New CFS Categories
Using CFS with Application Firewall infrastructure allows more granular, flexible and powerful CFS policies enforcement. The following are some of the advantages of CFS with Application Firewall Infrastructure:
- Create Per Policy allow/forbidden lists.
- Include/Exclude user, user groups from CFS Policies.
- Exclude Address Objects (internal) from CFS Policies.
- Configure per Policy custom block pages.
- Configure bandwidth management on CFS Policies.
- Import Allow/Forbidden lists from file.
Note: CFS and App Rules features are license based.
 On the Security Services | Content Filter page, users are given a choice to select between Via User and Zone Screens and Via App Rules. After selecting Via App Rules and clicking on the Accept button, the SonicWall Filter Properties window, under Content Filter Type | Configure, would have only 2 tabs.
On the Security Services | Content Filter page, users are given a choice to select between Via User and Zone Screens and Via App Rules. After selecting Via App Rules and clicking on the Accept button, the SonicWall Filter Properties window, under Content Filter Type | Configure, would have only 2 tabs.
On this page we create the CFS blocked categories objects and CFS Allowed/Forbidden objects.
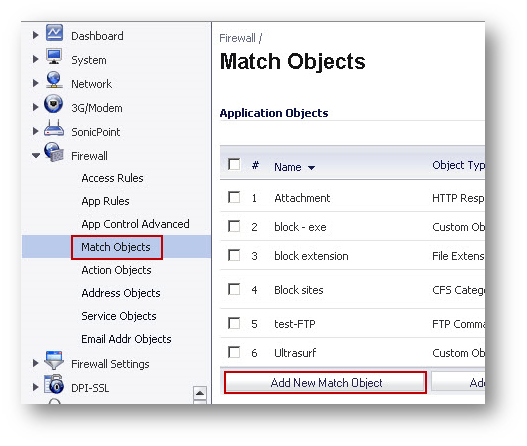
To create an object for blocking categories, select CFS Category List. This list is similar to the URL List of the User/Zone based CFS.
 CFS Allow/Forbidden List
CFS Allow/Forbidden List
To create a custom list of allowed or forbidden domains:
Select CFS Allow/Forbidden List under Match Object Type. You could also load the allow/block list from a file containing the name of the domains. Each entry in the file should be separated by a line. The maximum size of the file is 8192 bytes. If Enable HTTPS Content Filtering is enabled on the Security Services | Content Filter page, the Allowed/Forbidden Match Object entries would be allowed or blocked for either HTTP or HTTPS traffic.
Under Match Type, select any one of following Match Type options:
- Exact: Pattern exactly matches the given content to a single character.
- Partial: Pattern specified matches any portion of a given content.
- Prefix: Pattern specified matches the beginning of a given content.
- Suffix: Pattern specified matches the ending of a given content.
Example: Given the following content, "Google.com":
-
- Prefix match of "Google" will result in a match.
- Suffix match of ".com" will result in a match.
- Partial match of "googl" will result in a match.
- Exact Match of ""google.com" will result in a match.
 App Rules
App Rules On the App Rules page we configure the policies for CFS. The following options can be set when creating an App Rule:
Policy Name: Unique name for the policy Policy Type: CFS Address: Address Object/Group containing IP addresses of internal hosts in the LAN, DMZ, WLAN, VPN, SSLVPN or Custom Zone, to be included for this CFS policy. Exclusion Address: Address Object/Group containing IP addresses of internal hosts in the LAN, DMZ, WLAN, VPN, SSLVPN or Custom Zone, to be excluded from this CFS policy. Match Object: The CFS object created earlier under Match Objects page. The Match Object must be of type CFS Category List. Action Object: Actions define how the App Rules policy reacts to matching events. You can choose a customizable action or select one of the following predefined actions:
- No Action: Policies can be specified without any action. This allows “log only” policy types.
- Packet Monitor: Select this action to allow the Packet Monitor feature under System to filter packets based on the App Rules defined with this action. This action works in conjunction with Enable filter based on the firewall rule in the Monitor Filter tab in the Packet Monitor Configuration window.
- BWM High: Enabling this option would enforce Bandwidth Management on this policy with following parameters for Inbound/Outbound traffic:
- Maximum 100%
- Guaranteed: 0.00%
- BWM Medium: Enabling this option would enforce Bandwidth Management on this policy with following parameters for Inbound/Outbound traffic:
- Maximum 90%
- Guaranteed: 0.00%
- BWM Low: Enabling this option would enforce Bandwidth Management on this policy with following parameters for Inbound/Outbound traffic:
- Maximum: 70%
- Guaranteed: 0.00%
The following custom action can be used when using App Rule with CFS:
- Per Policy bandwidth management (BWM): Bandwidth aggregation for each policy defined.
- Per Action bandwidth management (BWM): Multiple policies will be subject to a single aggregate bandwidth management setting when they share the same action.
- HTTP Block Page: This Action Object can be created under Firewall | Action Objects
User Groups Select the User Groups to be Excluded or Included in this policy. Schedule Select a Schedule created under System | Schedules Enable Logging When this policy is triggered, the action selected above would be logged in App Firewall format. See here. Log using CFS message format Checking this box would log the message in CFS format instead of App Firewall format. See here. Log Redundancy Specifies the minimum number of seconds between log entries for multiple matches to the same policy. For example, a log redundancy setting of 10 will log no more than one message every 10 seconds for each policy match. Zone Select LAN, WLAN, DMZ, SSLVPN, VPN CFS Allow List Select a previously created CFS Allow/Forbidden List object. This object must be of Match Object Type CFS Allow/Forbidden List CFS Forbidden List Select a previously created CFS Allow/Forbidden List object. This object must be of Match Object Type CFS Allow/Forbidden List Enable Safe Search Allows you to force Web search sites like Google and Yahoo that have content restriction options always to use their strictest settings. 
Different Users/User Groups:
Most Specific / Least Restrictive is the default evaluation process of CFS policies assigned to different groups/users. Most Specific always has the highest priority (i.e. CFS policy for “All” group is least specific, CFS policy for local/authenticated group is more specific, CFS policy for a user is most specific. When policies are at the same level of specificity, the least restrictive option has the highest precedence.Example 1:
- Alex is part of Engineering and Alex is part of San Jose employees.
- Group San Jose is not allowed to access Sports.
- Group Engineering is allowed to access Sports.
- Result is Alex is allowed to access Sports – consistent with today’s CFS policy evaluation logic where least restrictive option among groups has higher precedence)
Example 2:
- Group “All” is allowed to access Sports.
- Group “Engineering” is not allowed to access Sports.
- Alex (who is part of Engineering) will not be allowed to access Sports, because CFS policy for Engineering group is more specific than CFS policy for “All” group (even though “All” group policy is less restrictive. In legacy CFS implementation the policy assigned to a specific Group has higher precedence than “Default” policy enabled on a zone).
- Group “All” (default) can be used to create ip subnet (address object/group) or zone based CFS policies.
Multiple Policies assigned to same group:
When multiple CFS policies are assigned to the same group, the evaluation logic is additive:
Example:
CFS policy 1: Engineering is not allowed to access porn, gambling, adult content.
CFS policy 2: Apply BWM for Engineering when accessing Sports, Multimedia, Social Networking at 1 Mbps.
The result of the above policies is that Sports access will be bandwidth managed at 1 Mbps when accessed by a member of Engineering group even through “CFS policy 1” implies that Sports should be allowed for Engineering.
CFS Via User and Zone Screens
CFS via user and Zone Screens is the legacy CFS configuration where multiple policies are configured and assigned to User Groups and IP Addresses with CFS enabled on the zones. The Enhancement made to this mode of configuring CFS is the capability to configure custom Allowed/Forbidden list to each CFS policy.On the Security Services | Content Filter age, select Via User and Zone Screens and click on the Accept button at the top.
Selecting this option would disable any App Rules based CFS policy under the Firewall | App Rules page.
 Click on the Configure button to bring up the SonicWall Filter Properties window.
Click on the Configure button to bring up the SonicWall Filter Properties window. - Click on the Policy tab.
- Click on the Add button to bring up the Add CFS Policy window.
- Enter a name for the policy.
- Click on the URL List and select the CFS categories to be blocked.
- Click on the Custom List tab.
- Enter Allowed/Forbidden domains and Keyword list here.
- Click on the Settings tab.
- Under Custom List settings, select the Source of Allowed, Source of Forbidden Domains and Source of Keyword. The options are:
- None: The Allowed, Forbidden and Keyword list for this policy will not be enforced.
- Global: Setting this option would make the global Allowed, Forbidden and Keyword list set under the main Custom List tab applicable for this CFS Policy.
- Local: Setting this option would make the Allowed, Forbidden and Keyword list set under the Custom List tab of this policy applicable for this CFS Policy.
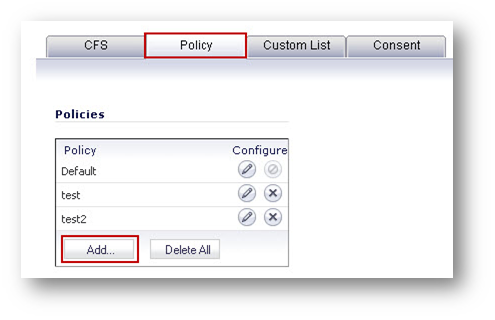
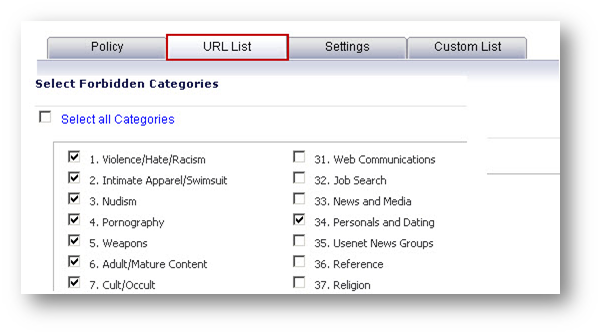

In addition to the above, the following enhancements have been made globally - applicable to both CFS Via App Rules and User and Zone-based CFS:
CFS Custom Category
This option enables you to customize CFS categories thus overriding global CFS database ratings. For eg. in the screenshot below, cnn.com, which is rated "News and Media" by the global CFS database, is re-rated as Information Technology/Computers - Category 27.
- On the Content Filter main page, select the Enable check box under CFS Custom Category.
- Click on the Accept button at the top of the page.
- Click on Add to open Edit CFS Local Rating window.
- Enter a name for this local rating entry.
- Select the category to which the site is to be re-rated.
- Enter the domain name of the site.
 In the the example above, cnn.com (global CFS category - News and Media) is given a custom category of Information Technology/Computers, which replaces the global category . If the category News and Media is blocked but cnn.com needs to be allowed, re-categorizing it as an allowed category (in this eg. Information Technology/Computers) would allow cnn.com. The entries here are interpreted as "suffix strings" meaning any prefix added to cnn.com, eg. us.cnn.com, will be treated as belonging to the custom category.
In the the example above, cnn.com (global CFS category - News and Media) is given a custom category of Information Technology/Computers, which replaces the global category . If the category News and Media is blocked but cnn.com needs to be allowed, re-categorizing it as an allowed category (in this eg. Information Technology/Computers) would allow cnn.com. The entries here are interpreted as "suffix strings" meaning any prefix added to cnn.com, eg. us.cnn.com, will be treated as belonging to the custom category.  The earlier IP based HTTPS filtering filter HTTPS traffic based on server IP addresses. The enhancement described here is to applicable to both IP addresses and hostnames for rating HTTPS websites. HTTPS Content Filtering is applicable for the domains entered in the Custom List and the Match Objects entries in Allowed/Forbidden List under Firewall | Match Objects page.
The earlier IP based HTTPS filtering filter HTTPS traffic based on server IP addresses. The enhancement described here is to applicable to both IP addresses and hostnames for rating HTTPS websites. HTTPS Content Filtering is applicable for the domains entered in the Custom List and the Match Objects entries in Allowed/Forbidden List under Firewall | Match Objects page.
Hostnames are obtained through two ways:
1. Examine SSL Client Hello messages and if it supports SSL server name extension, it will have hostname included in the SSL Client Hello. This hostname is used to get rating information.
2. Another method is to examine Server Hello messages to get certificate Common Names (CN) from the certificate and use the same to get rating information.The following CFS categories have been added in the new firmware:
- Multimedia (48)
- Social Networking (58)
- Malware (59)
- Internet Watch Foundation CAIC (Child Abuse & Illegal Content)
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series
Not Finding Your Answers?
ASK THE COMMUNITY






 YES
YES NO
NO