-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Cannot connect to LDAP Server on port 389, 3268 and 636.



Description
Email Security LDAP authentication fails even though credentials are correct on port 389, 3268 and 636
WebUI log shows the following:
EXCEPTION THROWN LdapAuth.login(): UNABLE to connect to the primary LDAP server : javax.naming.AuthenticationNotSupportedException: [LDAP: error code 8 - 00002028: LdapErr: DSID-0C0901FC, comment: The server requires binds to turn on integrity checking if SSLTLS are not already active on the connection, data 0, v1772
Cause
This issue is the result of a non-default domain policy set in active directory that enforces all LDAP authentication to be secured with SSL.
This policy on the domain controller is: "Domain controller: LDAP server signing requirements" and if set to "Require signing" the LDAP data-signing option must be negotiated unless Transport Layer Security/Secure Socket Layer (TLS/SSL) is being used. This also sets the following registry key on all domain controllers:
This issue is seen many times after a Microsoft update.
Resolution
There are 2 methods to resolve this issue:
Method 1
- Change the policy Domain controller: LDAP server signing requirements on the Domain Controllers to None which will set the LDAP Data signing to not require in order to bind with the server. However, if the client requests data signing, the server supports it.

- Setting this policy to "none" will also change the following registry setting on all DCs:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesNTDSParametersLDAPServerIntegrity=1 NOTE:This is the default setting.
NOTE:This is the default setting. - Once this setting is changed on the DC, the ESP server should allow unsecured LDAP Authentication and the process in KB2441205 will allow authentication against active directory from the ESP Administrator.
Method 2
- Configure the ESP Adminserver process to bind securely with the LDAP server hosted by the Windows Domain Controller.In order to accomplish this the following steps must be completed:
- Obtain the Domain Controllers Self-Signed SSL Server Certificate.
 NOTE: One can refer to the Windows security group to obtain the required certificate.
NOTE: One can refer to the Windows security group to obtain the required certificate. - Once the appropriate certificate is obtained, one must install the certificate in the Trusted Root Certification Authorities Container on the FAST ESP Server.
- Test the secure LDAP connection from the ESP Server using LDP.EXE.
See the following to obtain more information on obtaining and utilizing LDP.EXE:
Ldp Overview
http://technet.microsoft.com/en-us/library/cc772839(WS.10).aspx - Launch LDP.EXE from the FAST ESP Admin Server.
- Choose Connection from the file menu.
- Choose Connect from the drop down menu.
- Type the name of the DC with which to establish a connection.
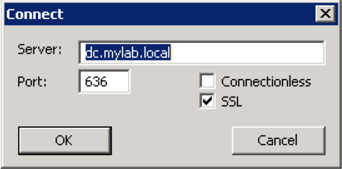
- Change the port number to 636.
 NOTE: 636 is the secure LDAP port (LDAPS).
NOTE: 636 is the secure LDAP port (LDAPS). - Choose the checkbox SSL to enable an SSL connection.
- Click OK to test the connection.
- If successful, a secure LDAPS connection is established to the DC and validates the certificate that was installed in step 2.
- At this point the Root CA SSL Certificate that was obtained in step 1, must be installed into the JAVA Key Store to ensure that the JAVA based ESP Adminserver component will be able to successfully establish a secure LDAP connection to the DC.
- This step can be accomplished by using keytool that is shipped with JAVA:
 EXAMPLE: $JAVA_HOME/bin/keytool -import -alias root -keystore $JAVA_HOME/lib/security/cacerts -trustcacerts -file /ldap-server.cer
EXAMPLE: $JAVA_HOME/bin/keytool -import -alias root -keystore $JAVA_HOME/lib/security/cacerts -trustcacerts -file /ldap-server.cer NOTE: The certificate is added to the default JVM truststore $JAVA_HOME/lib/security/cacerts, and added with the alias 'root'.
NOTE: The certificate is added to the default JVM truststore $JAVA_HOME/lib/security/cacerts, and added with the alias 'root'.
/ldap-server.cer refers to the SSL certificate which the JVM client uses to trust the LDAP server.
See the following Information for assistance with this process:Importing a Certificate for the CA:http://download.oracle.com/javase/1.3/docs/tooldocs/win32/keytool.html. - Once the DC Root Cert is successfully imported into he Java Keystore, open and edit the login.conf file in path: %FASTSEARCH%adminserverwebappsadminserverWEB-INFlogin.conf
- Modify the existing entry:
LDAP {
no.fast.vespa.security.auth.JaasLdapProvider required
providerURL="ldaps://gc1.contoso.com:636 "
principalFormat="{0}@contoso.coml (@contoso.coml) ";
Where ldaps://gc1.contoso.com:636is the full LDAP URL to company’s LDAP server, and where @contoso.com is a common part of all user names. NOTE: The difference in this setting compared with KB2441205 is the LDAP URL is being changed to ldaps and port 636 which is required to establish a secure ldap connection.
NOTE: The difference in this setting compared with KB2441205 is the LDAP URL is being changed to ldaps and port 636 which is required to establish a secure ldap connection. - Edit the file %FASTSEARCH%adminserverwebappsadminserverWEB-INFclassesesp4j-security-context.xml.
- Change the loginContextname property to LDAP on the bean with id id="jaasAuthenticatorTarget".
 NOTE: The property specifies which login context to use. Changing this setting to LDAP will activate the login context specified in WEB-INFlogin.conf.
NOTE: The property specifies which login context to use. Changing this setting to LDAP will activate the login context specified in WEB-INFlogin.conf. EXAMPLE: /WEB-INF/login.conf LDAP
EXAMPLE: /WEB-INF/login.conf LDAP - Restart Adminserver:
nctrl stop adminserver
nctrl start adminserver - Login to the admin node and navigate to FAST Home |User Administration | Create Users & Groups.
- Create a user with the same name as the Windows user that requires access rights to ESP.
- Select This user will be authenticated by an external management system.
- Give this user rights in ESP,
 EXAMPLE: choose “may create and delete users and groups (admin)":
EXAMPLE: choose “may create and delete users and groups (admin)": NOTE: If one chooses to authenticate a user by an external user management system, the User Name field must match the user login of the external user management system (AD User account in this case). It is not required to fill in the e-mail and password fields for users authenticated through an external user management system.
NOTE: If one chooses to authenticate a user by an external user management system, the User Name field must match the user login of the external user management system (AD User account in this case). It is not required to fill in the e-mail and password fields for users authenticated through an external user management system. - Once these changes are made, one can log into the ESP admin console with mapped external accounts that are maintained in the Windows Domain.
Related Articles
- Email Security: How to download the Outlook Junk Tool?
- Configuring SonicWall Email Security to Ensure Maximum effectiveness, High Throughput
- How to exclude the domain from DHA scanning?
Categories
- Email Security > Email Security Appliance
- Email Security > Email Security Software
- Email Security > Hosted Email Security
- Email Security > Hosted Email Security > LDAP Configuration
- Email Security > Email Security Appliance > LDAP Configuration






 YES
YES NO
NO