-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Application List Objects



Description
Application List Objects are a selection of the application category, threat level, type of technology, and attributes. These can be used to create policies using App rules for a group of applications/application categories.
Resolution
Application List Objects:
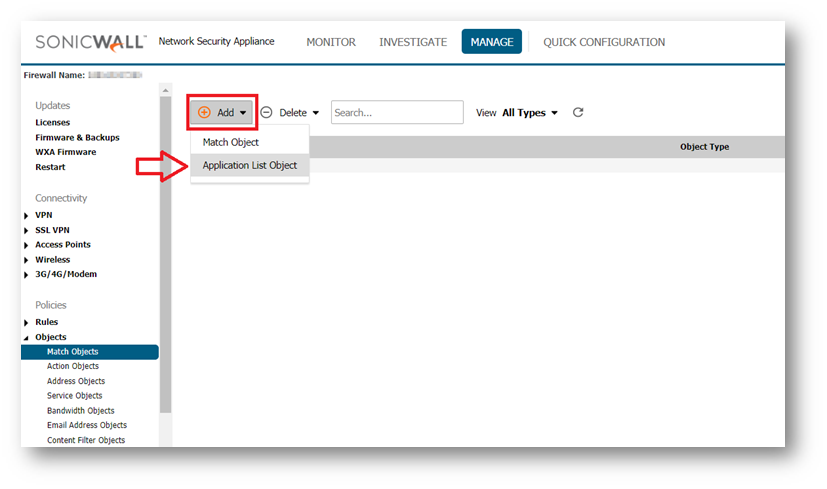
To view this option, Navigate to Manage | Objects | Match Objects. When creating an application list object, you choose from the same application categories, signatures, or specific applications that are shown on the Rules > App Control page. The dialog provides two choices:
Application – You can create an application filter object on this screen. This screen allows selection of the application category, threat level, type of technology, and attributes. After selections are made, the list of applications matching those criteria is displayed. The Application screen provides one way to create a match object of the Application List type.
Category – You can create a category filter object on this screen. A list of application categories is displayed, with descriptions that appear when you move your mouse over a category. The Category screen allows you to create a match object of the Application Category List type.
Application Filters:
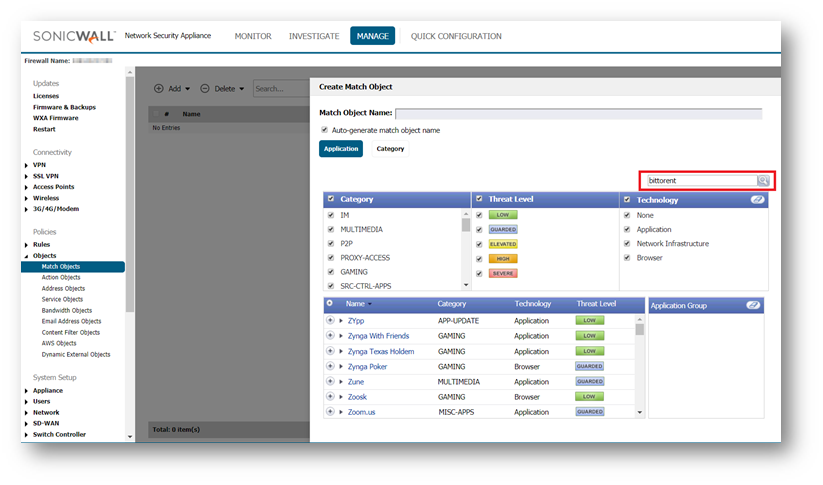
The Application screen provides a list of applications for selection. You can control which applications are displayed by selecting one or more application categories, threat levels, and technologies. You can also search for a keyword in all application names by typing it into the Search field near the top right of the display. For example, type in “bittorrent” into the Search field and click the Search icon to find multiple applications with “bittorrent” (not case-sensitive) in the name.
- When the application list is reduced to a list that is focused on your preferences, you can select the individual applications for your filter by clicking the Plus icon next to them, and then save your selections as an application filter object with a custom name or an automatically generated name. The image below shows the dialog with all categories, threat levels, and technologies selected, but before any individual applications have been chosen.
- As you select the applications for your filter, they appear in the Application Group field on the right. You can edit the list in this field by deleting individual items or by clicking the eraser to delete all items. The image below shows several applications in the Application Group field. The selected applications are also marked with a green checkmark icon in the application list on the left side.
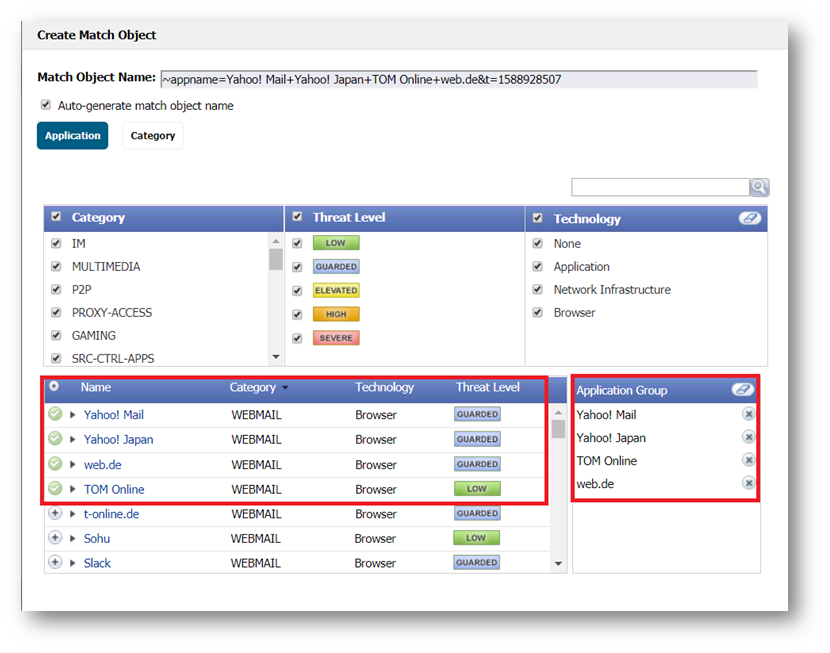
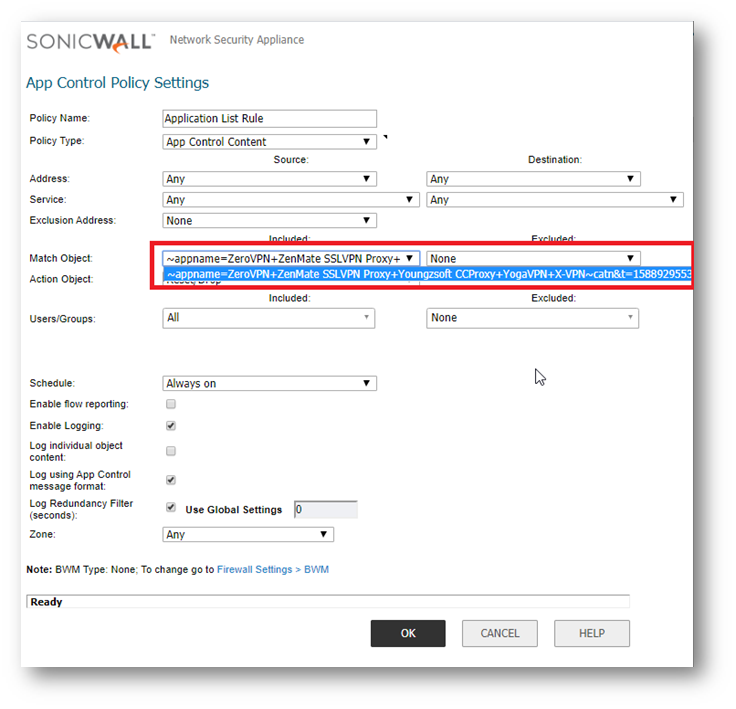
- When finished selecting the applications to include, you can type in a name for the object in the Match Object Name field (first, clear the Auto-generate match object name checkbox) and click the ACCEPT button. You will see the object name listed on the Objects > Match Objects page with an object type of Application List. This object can then be selected when creating an App Rules policy or an App Based Route policy.
Application list objects created using the Auto-generate match object name option display a tilde (~) as the first character of the object name.
Category Filters:
The Category tab provides a list of application categories for selection. You can select any combination of categories and then save your selections as a category filter object with a custom name. The image below shows the dialog with the description of the P2P category displayed.
Configuring Application List Objects:
To configure an application list object:
- Navigate to Firewall | Match Objects.
- Click the Add Application List Object button. The Create Match Object dialog displays.
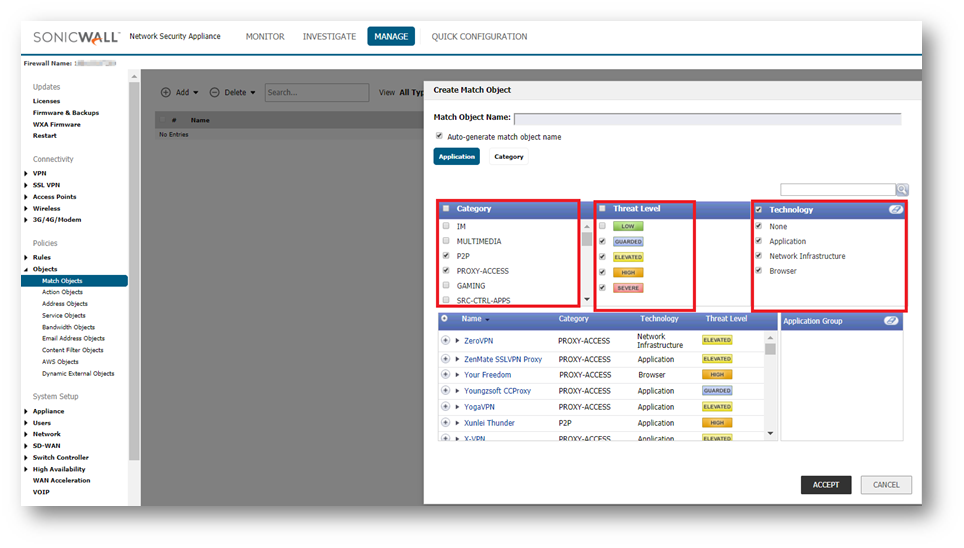
You can control which applications are displayed by selecting one or more application categories, threat levels, and technologies. When the application list is reduced to a list that is focused on your preferences, you can select the individual applications for your filter.
- In the Search field near the top right of the page, optionally enter in part of an application name and click the Search icon to search for applications with that key word in their names.
- In the Category pane, select the check boxes for one or more application categories.
- In the Threat Level pane, select the check boxes for one or more threat levels.
- In the Technology pane, select the check boxes for one or more technologies
- Click the plus sign next to each application you want to add to your filter object. To display a description of the application, click its name in the Name column. A Detailed Information pop-up dialog displays with the following information:
a) Description
b) Sig ID; you can click this ID to display a SonicWall SonicAlert
c) Category
d) Technology; such as Application or Browser
e) Risk, with color-coded threat level
As you select the applications for your filter, the plus sign icon becomes a green checkmark icon and the selected applications appear in the Application Group pane on the right. You can edit the list in this field by deleting individual items or by clicking the eraser to delete all items.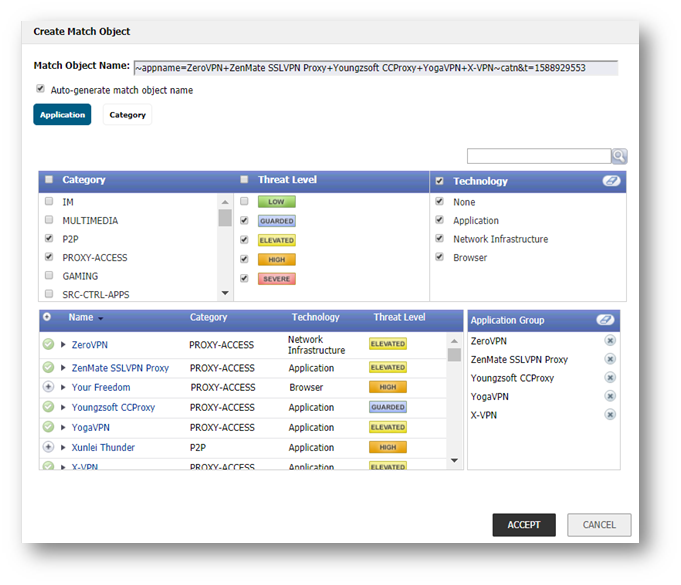
- When finished selecting the applications to include, type in a name for the object in the Match Object Name field or you can let it auto generate the name for you.
- Click Accept button. You will see the object name listed on the Firewall > Match Objects page with an object type of Application List. This object can then be selected when creating an App Rules policy.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO