-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Analyze threats detected by Capture Client using the Attack Storyline



Description
The SentinelOne autonomous Agent automatically groups behavioural events detected related to a single threat into one Attack Storyline. All alerts related to the Storyline of that threat are joined into a single alert. When you run mitigation on a threat, all events in the Attack Storyline are mitigated. This lets security analysts understand the full story of what happened on an endpoint. Use the storyline to understand the full story behind threats and save time for your security teams.
If a threat is detected by the behavioral engine, an Attack Storyline is generated (e.g. Fileless malware, Scripts, Lateral Movement etc). For threats detected by reputation or the Static AI engine, no behavior is detected so there will be no storyline. To see all events of a dynamic threat (detected by a Behavioral AI engine) in a graphical process tree and a table view, open the Attack Storyline section for a Threat on its details page.
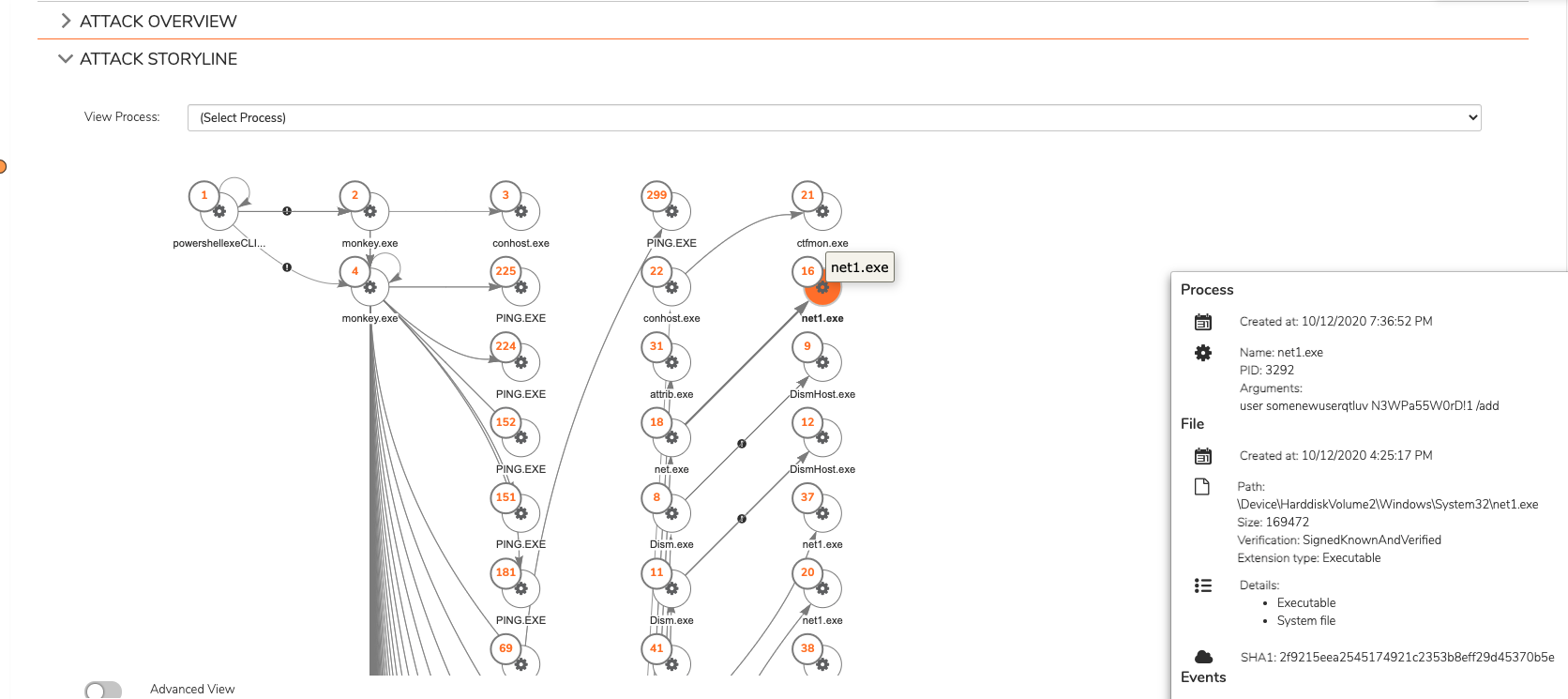
To use the Process tree:
- If available, click the plus sign (+) in a node to see its children, or Load more to see more nodes.
- Drag and drop the tree.
- Zoom in and out. Click Full Screen Mode to see only the tree in your browser window.
- In the Processes menu on the left, select a process to view in the tree. By default the root process is shown. Click Search Processes to search for a specific process in the storyline.
- Click a node to see its details in the Process Summary on the right.
- When you select a node, see where it falls in the timeline below.
- The events table is also filtered to show events related to that node.
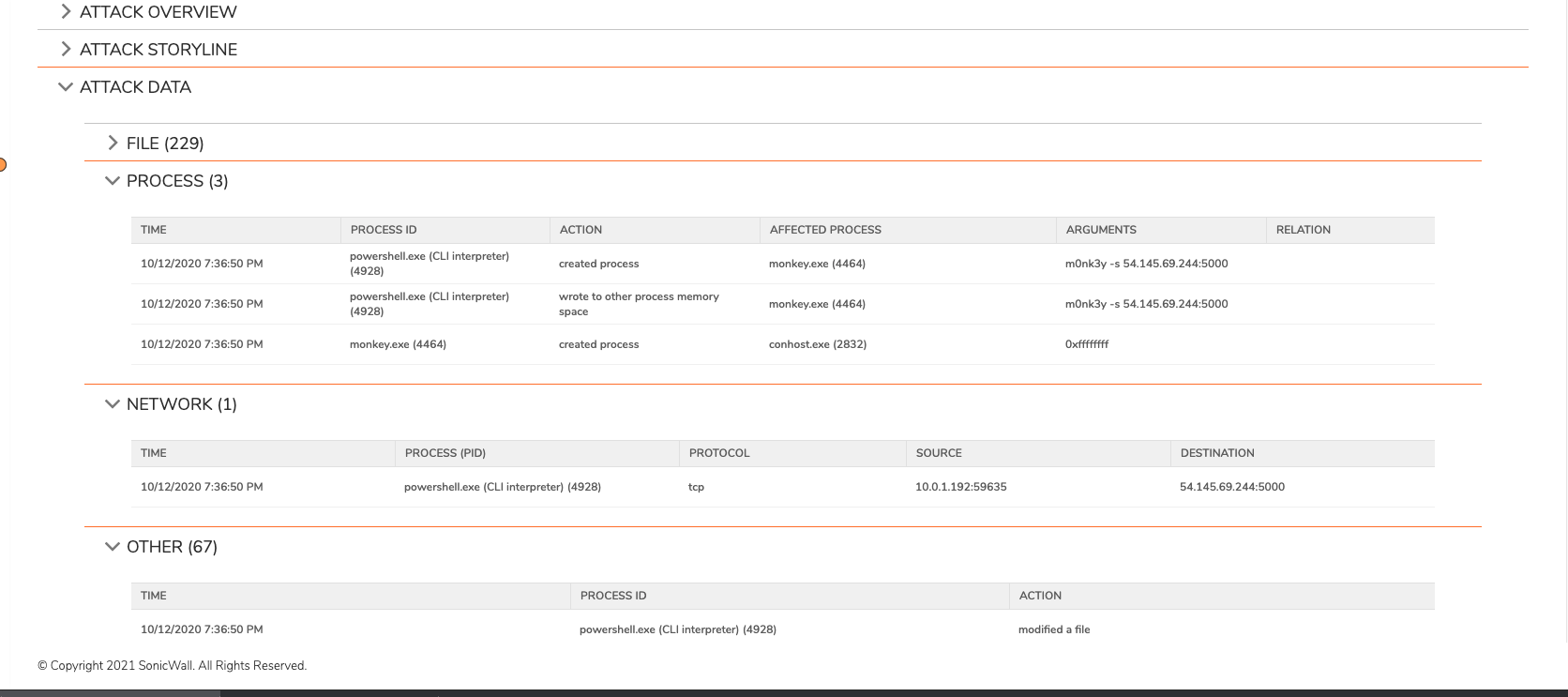
In addition, details of the events related to the threat are shown in the Threat Data section. This includes File, Processes, Network and Others event types. All of the event data can also be downloaded as a JSON or CSV file for further analysis and investigation in 3rd party tools.
File data includes all file actios taken by the convicted processes – creation, deletion or modification with details of the hash value and the path of the files. Process data shows what child processes were created by the parent process that was convicted. Network data shows all network connections to/from the endpoint that were made by the convicted process. Other data will show other type of information including Registry actions and Behavioural Indicators identified (such as actions take for persistence by malware).
Related Articles
- SentinelOne agent command line tool
- Capture Client Agent Return Codes - Phase 1
- Configure Email and Notification(Alerts) in Capture Client for Tenants






 YES
YES NO
NO