Nova RaaS: The Ransomware That ‘Spares’ Schools and Nonprofits—For Now

A new ransomware group calling themselves Nova RaaS, or ransomware-as-a-service, has been active for the past month distributing RaLord ransomware. On their blog, they claim to have no affiliations with other cybercriminal groups—and, in a surprising twist, say they’ve pledged not to target schools or nonprofit organizations.
Infection Cycle
This ransomware arrives as an executable file written in Rust.
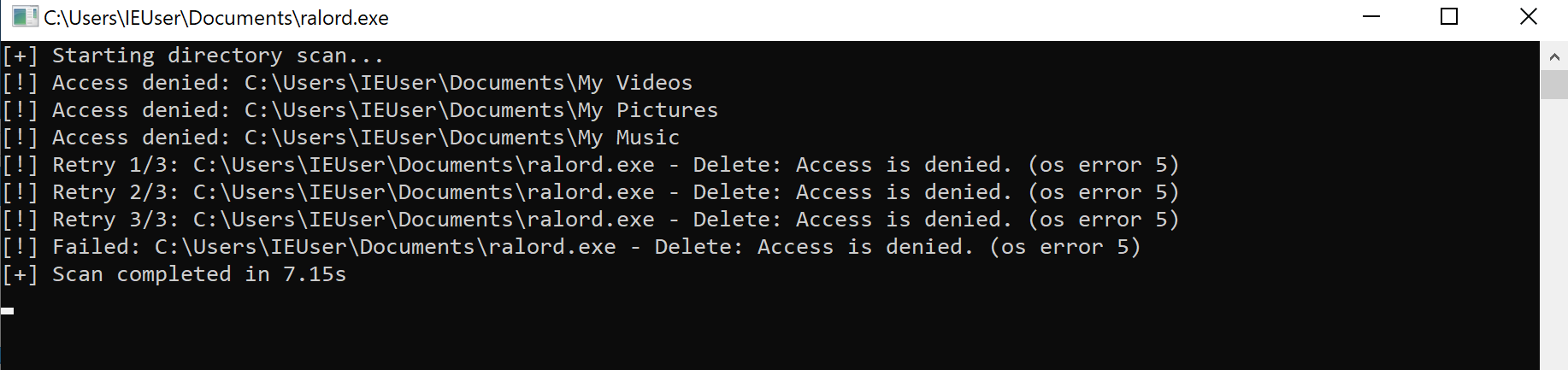
It opens a console window using conhost.exe and begins scanning the system for files to encrypt. This ransomware program is so novice that it even tries to encrypt itself.
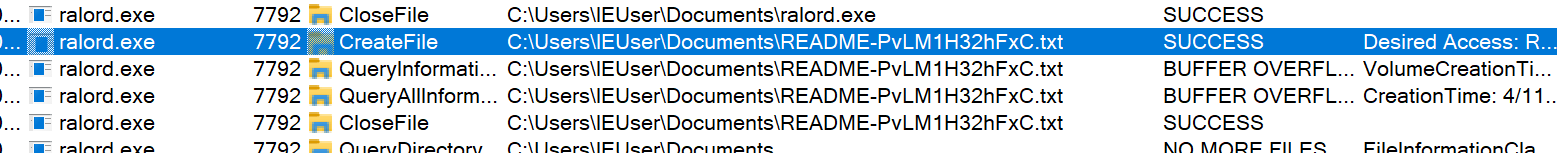
It creates a readme text file affixed with random characters.
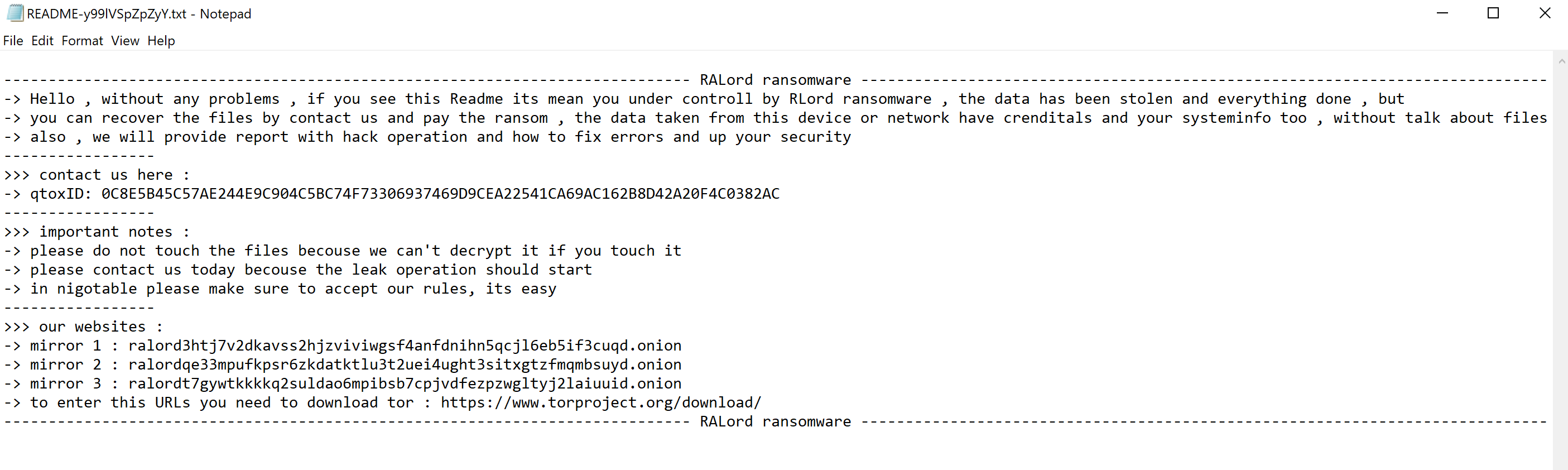
This readme contains the ransom note with instructions on how to recover the files. However, the ransom note does not mention a fixed ransom amount like most ransomware notes. Instead, it lists a qTox ID where the victim can contact the cybercriminals to negotiate.
It appends “.ralord” to all encrypted files.
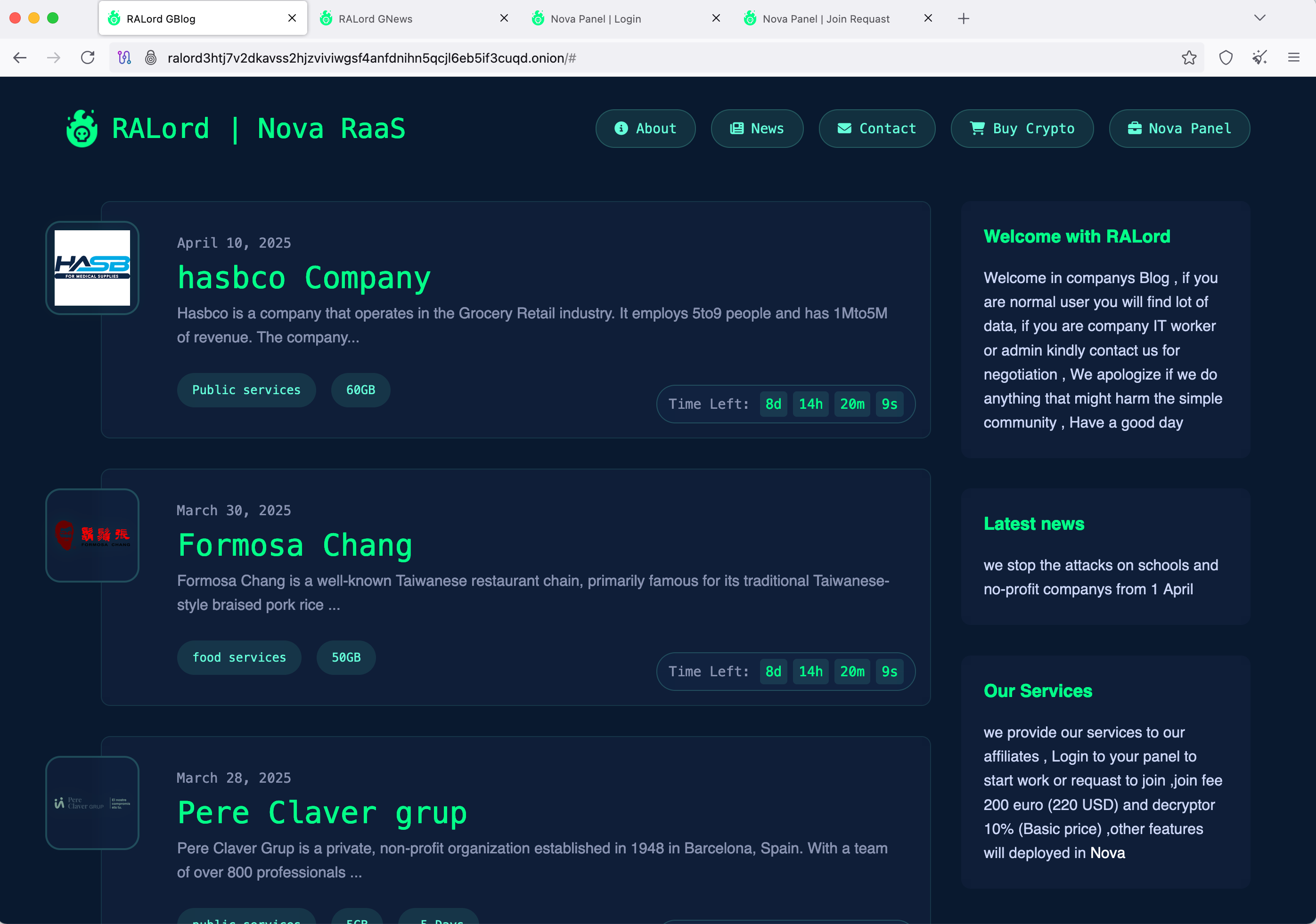
RaLord’s onion website reveals their latest victim, including details on how much data was exfiltrated and how many days remain until the victim’s data will be published—presumably if no payment is received.
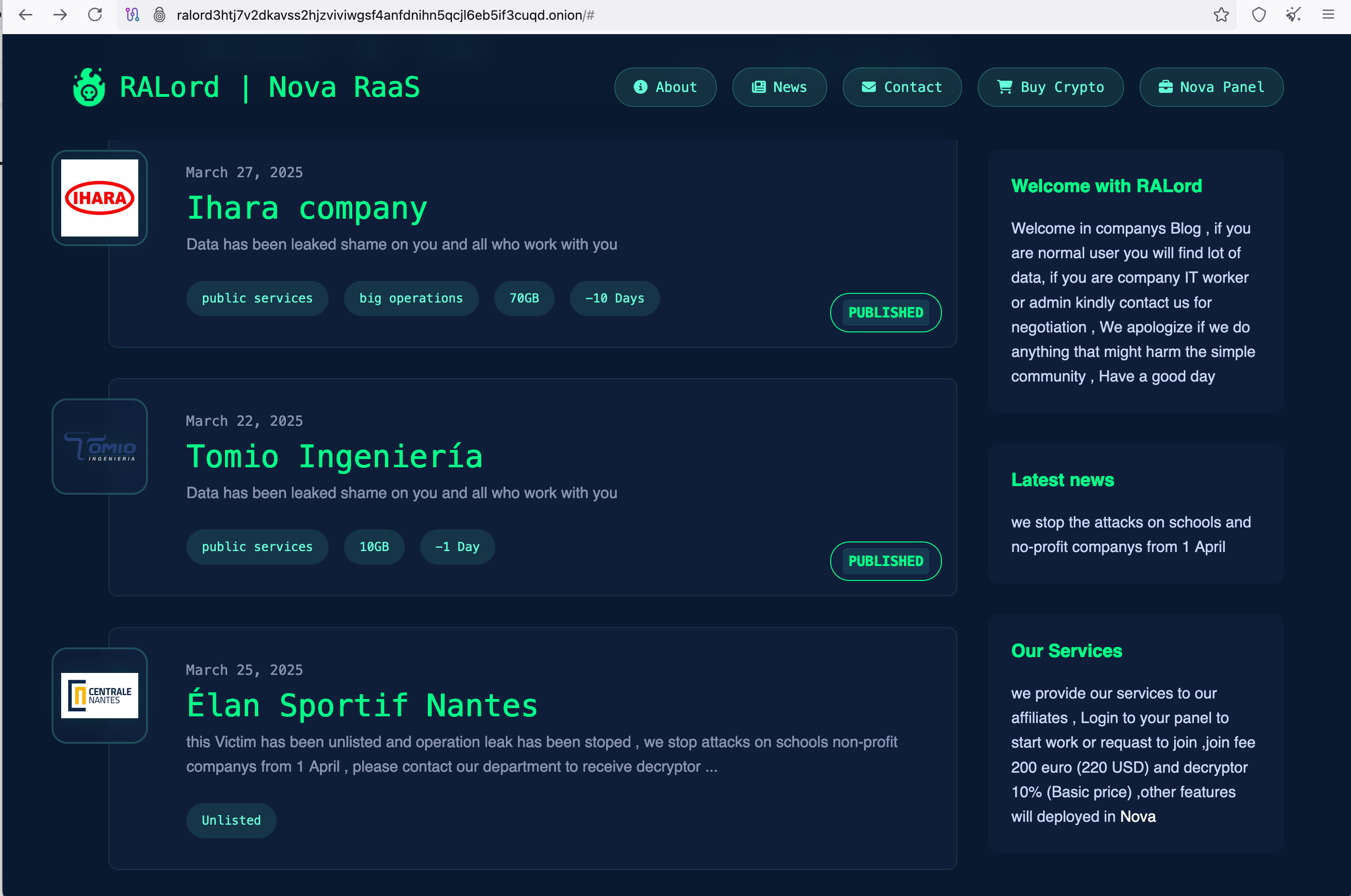
In the “News” section of their blog, they announced they will no longer target schools and nonprofit organizations beginning in April. In fact, one of their earlier victims was a school, which is now marked as “unlisted.”
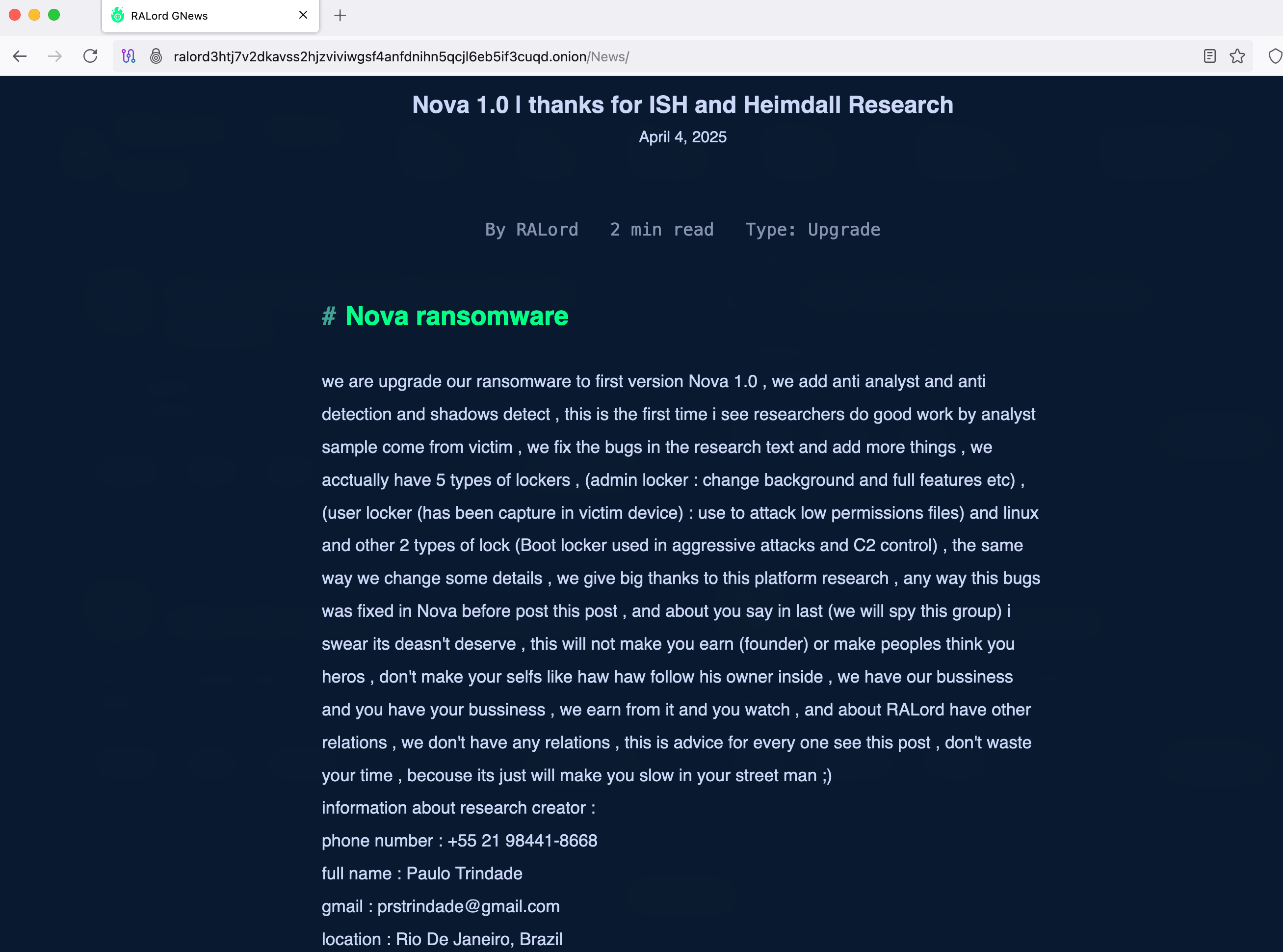
The ransomware blog also documents recent updates and improvements to the program, demonstrating how the group continues to refine their techniques and add new features.
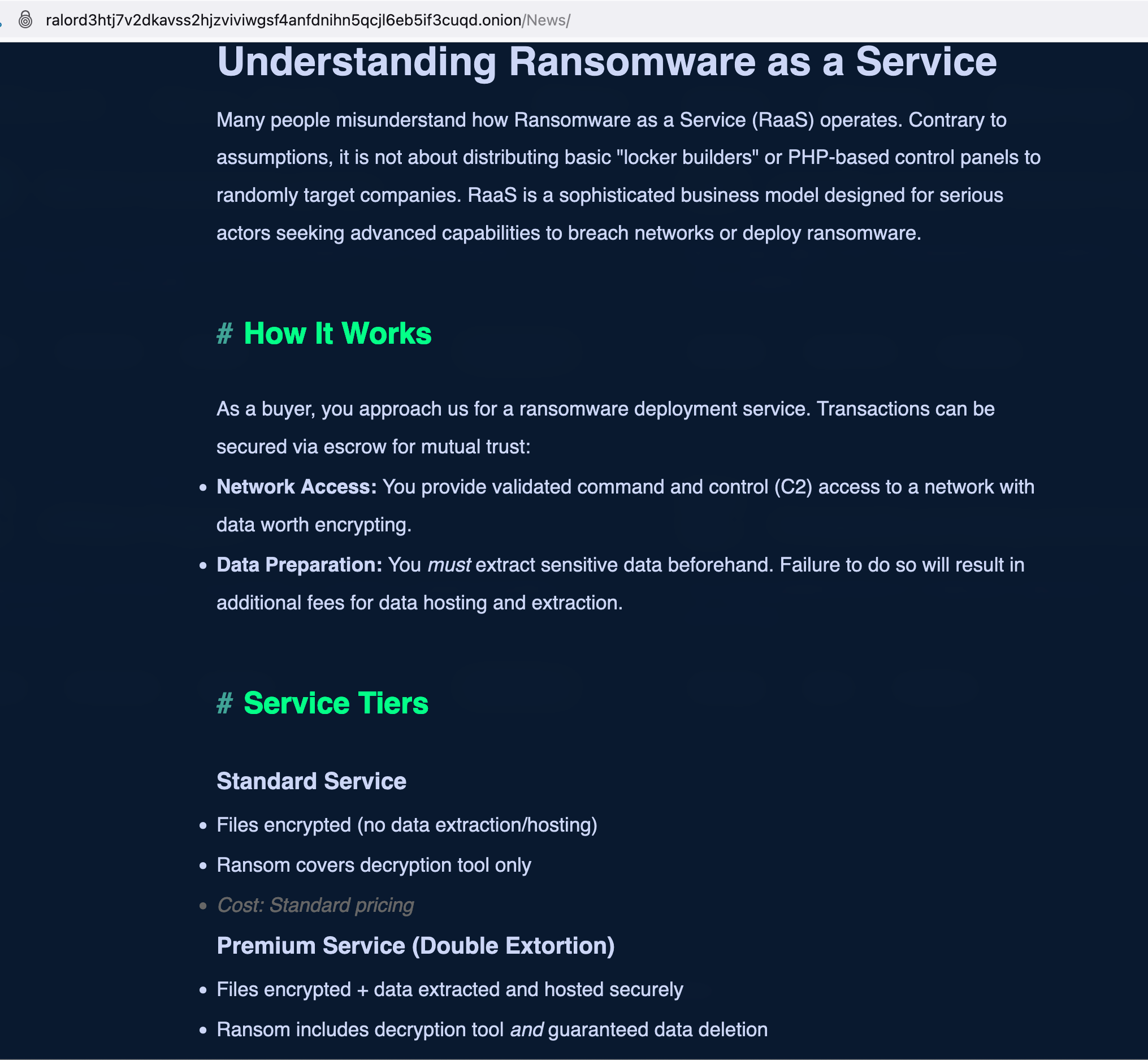
A detailed explanation of how their ransomware-as-a-service offering works—and how to partner with them—is also provided on their onion site.
SonicWall Capture Labs provides protection against this threat via the following signature:
• GAV:RALord.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI™ and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
