New Year greeting card spam (Dec 30, 2009)

SonicWALL UTM Research team observed a new spam campaign starting on December 29, 2009 which involves a fake greeting card e-mail pretending to contain a link to New Year card. The e-mail looks like following:
Subject: Your have received a greetings card
Email Body:
------------------------
Have a happy and colorful New Year!
http://cpz.gumen(REMOVED)/2010.html -> leads to the malicious website that is still live
------------------------
The e-mail message looks like below:
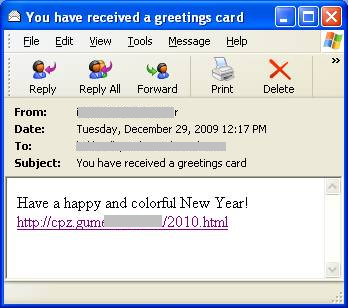
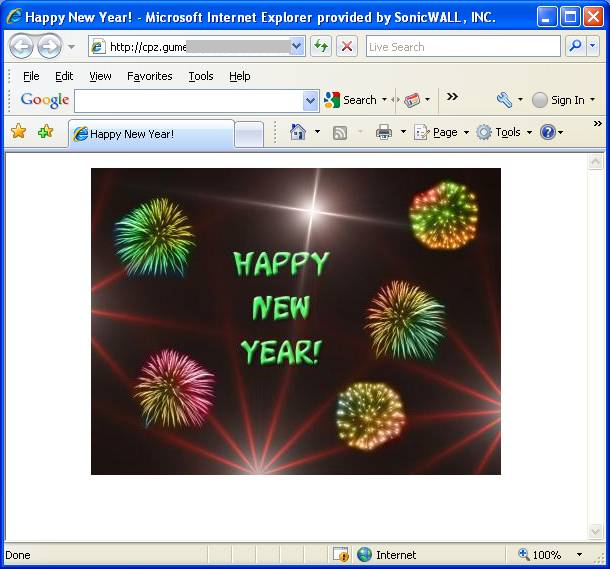
If the user clicks on the link in the e-mail, it leads to a malicious website that displays a happy new year image as seen below:
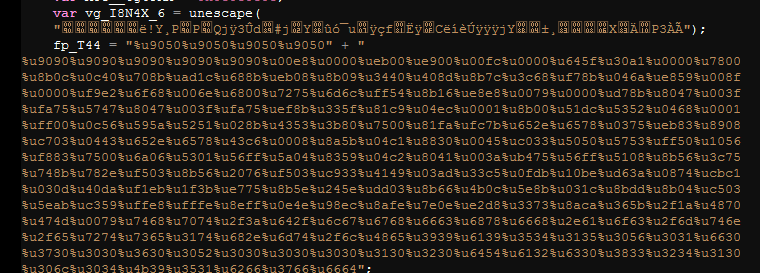
The site has an obfuscated javascript code that executes when it loads. It tries to exploit multiple vulnerabilities including 0-day in Microsoft DirectShow (msvidctl.dll) and Adobe Acrobat Reader. If the exploit attempt is successful then it injects the shellcode shown below:
The shellcode leads to download and execution of a new variant of Bredolab and Mebroot Trojan.
SonicWALL Gateway AntiVirus provides protection against this attack via GAV: Pdfka.ASD (Exploit), GAV: Tedroo.gen (Trojan),and GAV: Bredolab.SME_2 (Trojan) signatures
Share This Article

An Article By
An Article By
Security News
Security News