Fake Pokemon GO apps tuck away dangerous malware (August 1, 2016)

The way Pokemon has gained popularity in the recent past is remarkable and unrivaled. If you spot people around a public place like a park carrying their mobile in a very peculiar way, most likely they are there hunting pokemons. The official Pokemon game is topping the sales charts for both Android and iOS, undoubtedly this has become a prime medium with which attackers are trying to infect mobile devices.
As of first week of July, the official Pokemon Go app was released in limited countries (highlighted in green) as shown in the map below (Courtesy - Reddit ):
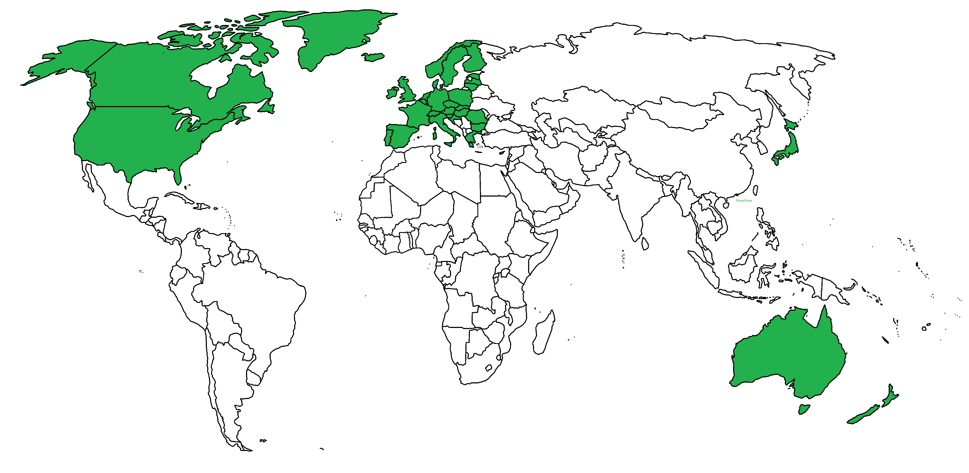
As clearly visible, this game got a limited release and is slowly rolling out to countries that could not get a day-one release. But this has left many wannabe players with no way to install the app from the official Play store, as a result they are resorting to non-store versions of the app. Their sentiment is perfectly summarized by the following comment on a forum:
There are a number of guides available online that highlight how to acquire non-store apps and "sideload" them on an Android device. Malicious entities saw this as a good opportunity to use Pokemon as a malicious vector, soon enough there were a number of third party app stores littered with apps that claim to be official but in reality they stash malicious components.
In this blog we highlight a few types of malicious apps that are trying to pass themselves off as the official Pokemon app but they hide malicious contents.
- Pokemon Apps with DroidJack:
There are few fake Pokemon apps that harbor a Remote Access Tool (RAT) named DroidJack that can give the attacker complete control over the victim's device. Two of them are listed below:
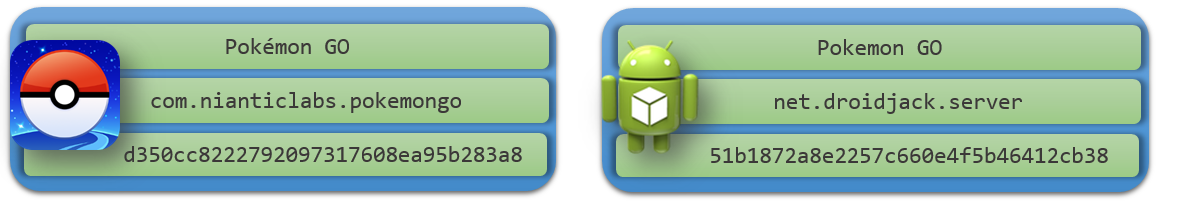
The following are few capabilities among a plethora of options available in DroidJack:
- Read, delete and write SMS messages
- Read and delete call logs
- Make calls
- Read, write, delete and add contacts
- Take pictures from front/back camera
- Record videos from front/back camera
Below is a comparison of the code present in the legitimate Pokemon Go app alongside fake Pokemon Go apps with DroidJack component:
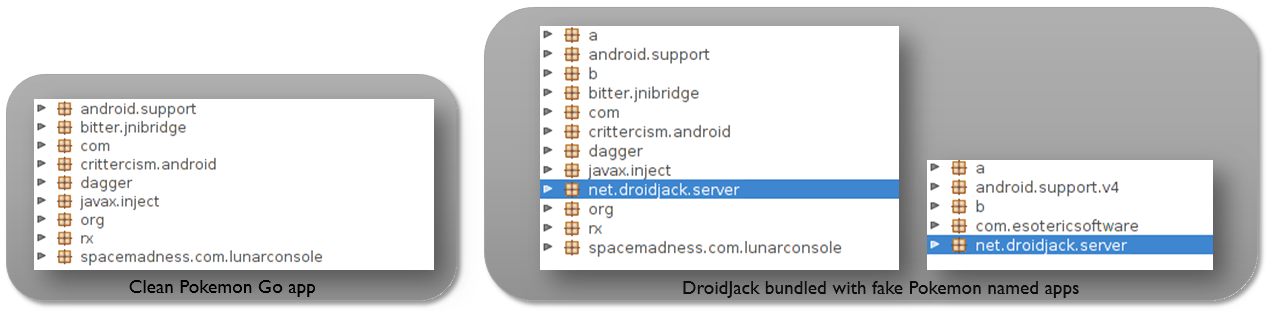
As we can see one of the fake app (d350cc8222792097317608ea95b283a8) has almost the same code structure as the original one apart from the addition of DroidJack components. The second fake app (51b1872a8e2257c660e4f5b46412cb38) just contains the DroidJack component and shares only the app name with the legitimate app.
- Adware:
Most of the Pokemon adware apps have the same icon as the original, even the name is almost the same, as a result they may pass off as legitimate. In many cases the size of these apps give away their guise, the two instances listed below are around 2.6 MB each whereas the original one is around 58 MB.
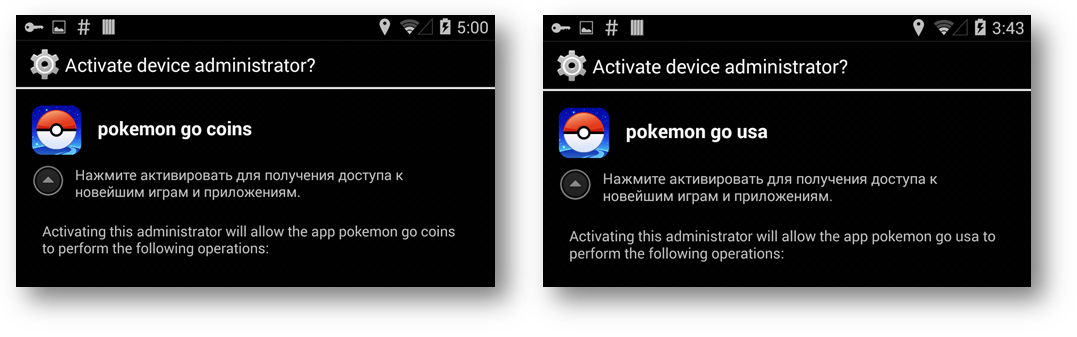
Once installed these adware apps ask for device administrator privileges, the original app does not ask for the same:
Upon opening the app they showed survey questions following which we started seeing pop-ups on the device via the browser:
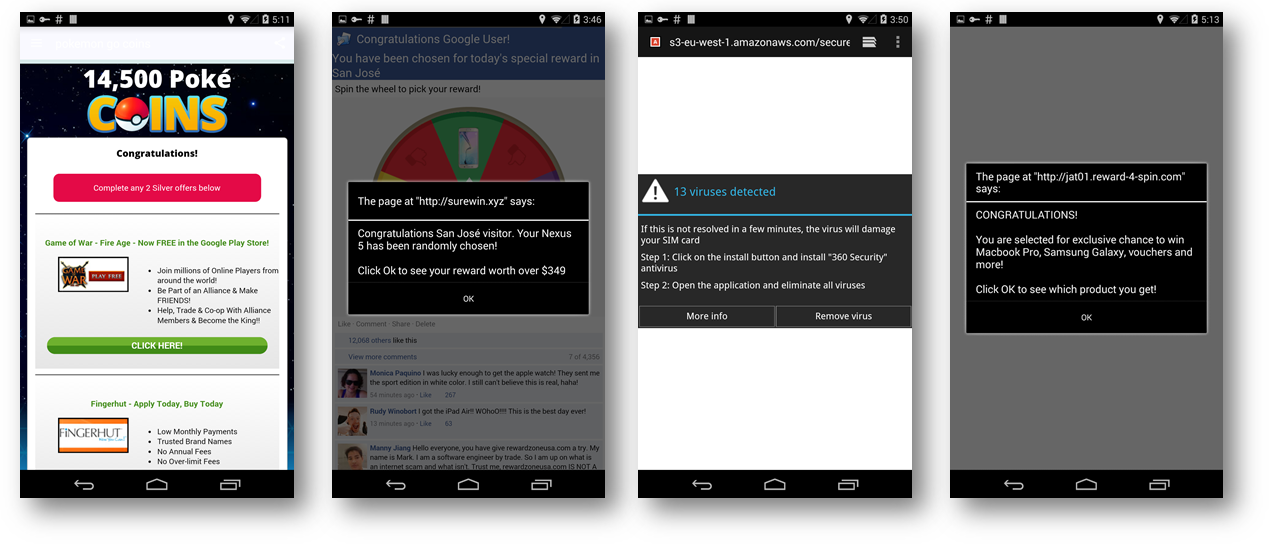
Some pop-ups would lead to installation of more adware on the device. Furthermore, we saw some overlays with advertisements that covered a big part of the screen: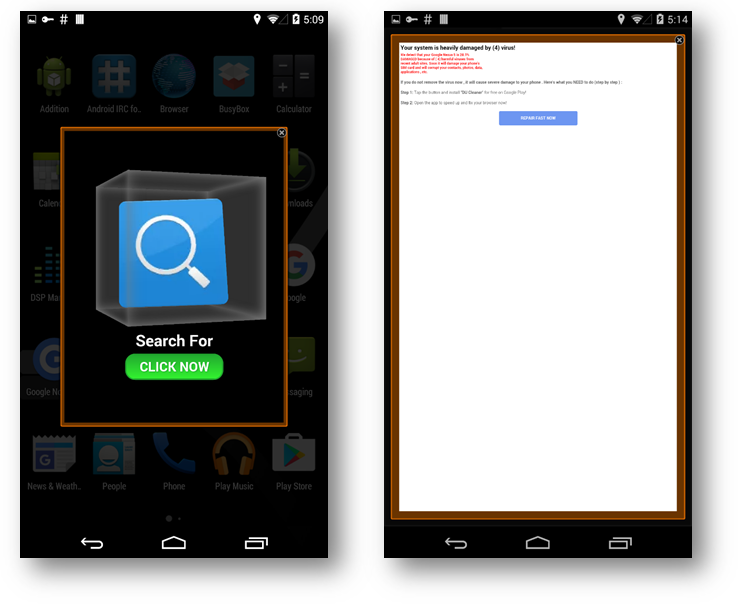
- Installers
Some Pokemon apps would install other secondary apps on the device, during our analysis the secondary apps downloaded were mostly adware. A few such installer apps are listed below:
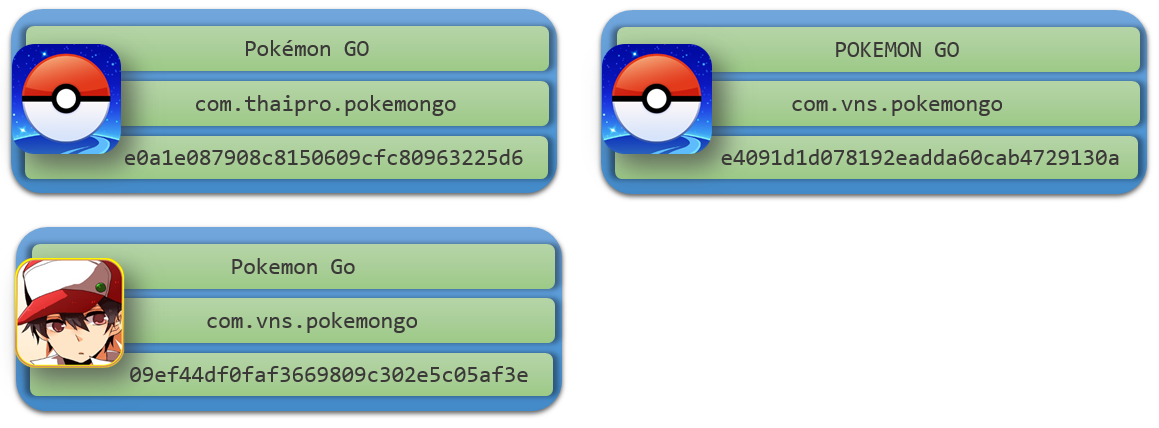
Below is an instance where secondary apps are getting downloaded:
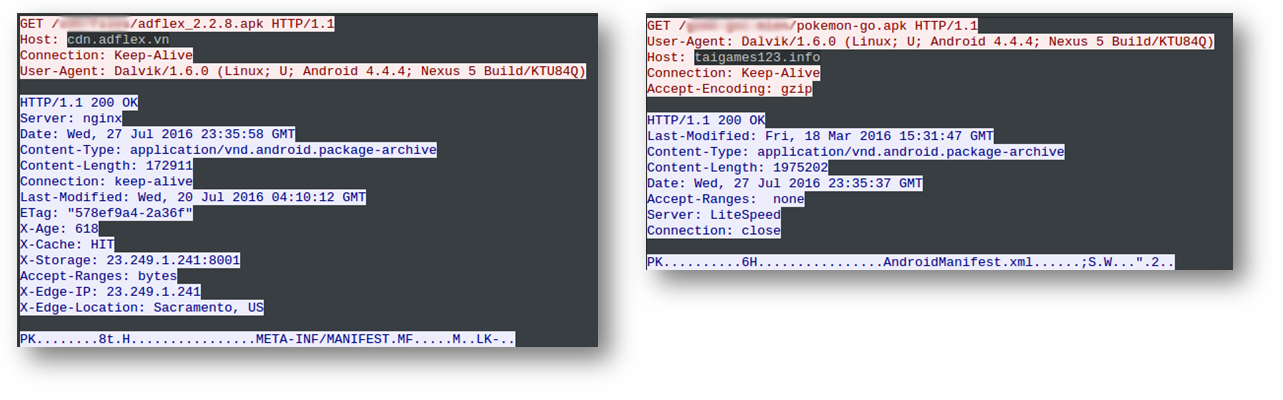
These downloaded apps are stored locally on the device as shown below:
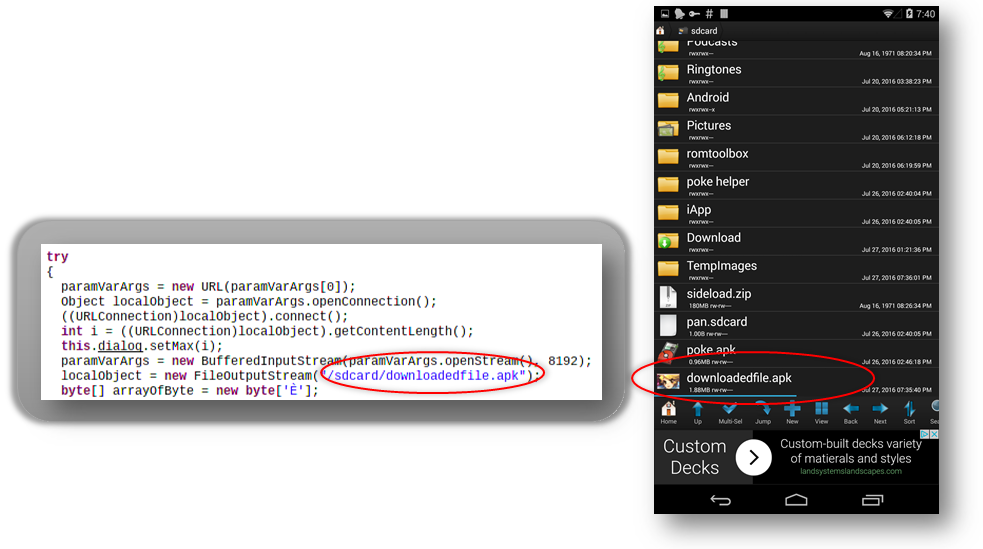
These apps send sensitive information about the device to the attackers:
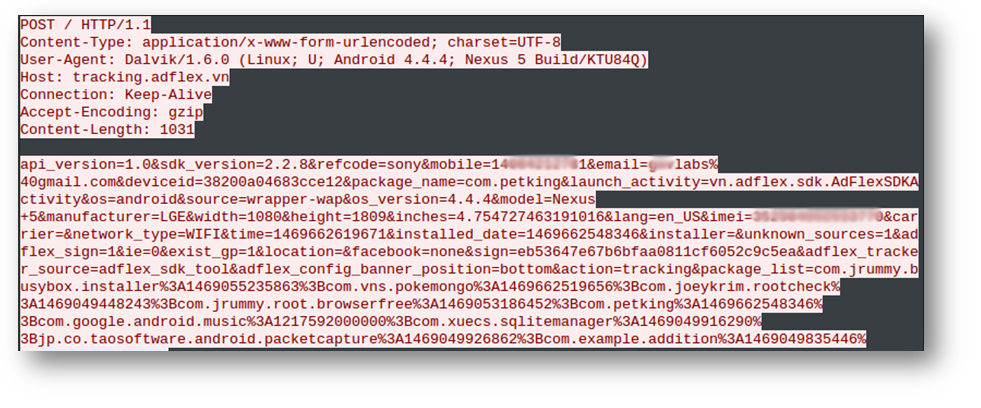
Some of the data that was sent includes:- Phone number
- IMEI
- Email ID
- List of installed apps
Below are a few details about the Official Pokemon Go app that should be noted in order to determine authenticity of the app:
- Name of the official app is Pokemon GO. The name is copied by a number of fake apps, sometimes with slight variations
- The package size for Version 0.29.3 is 58.06 MB. Many fake apps tend to be of different size so this is a good measure to understand the authenticity of the app
- The package name of the official app is com.nianticlabs.pokemongo. Many fake apps have a different package name but there are few fake ones with the same package name
- Developer for the original app is Niantic, Inc. Most of the fake apps have a different developer name
- One more very useful way to understand the legitimacy of the official app is via the following details:
- MD5: 2580d2687af1ffaaec16ff3b48380f76
- SHA256:8bf2b0865bef06906cd854492dece202482c04ce9c5e881e02d2b6235661ab67
- One extremely important thing to note is that the official Pokemon app does not require administrator privileges. So if a Pokemon app is requesting for one then its a clear sign that something is wrong
In-case you decide to download and install the app from a 3rd party app store then it is advisable to make sure all of the above mentioned points match for the downloaded app. Even if a single point mis-matches then there is a possibility that the app downloaded is fake.
Apart from the points mentioned above we urge you to double check the app on VirusTotal as the original app is shown as clean:
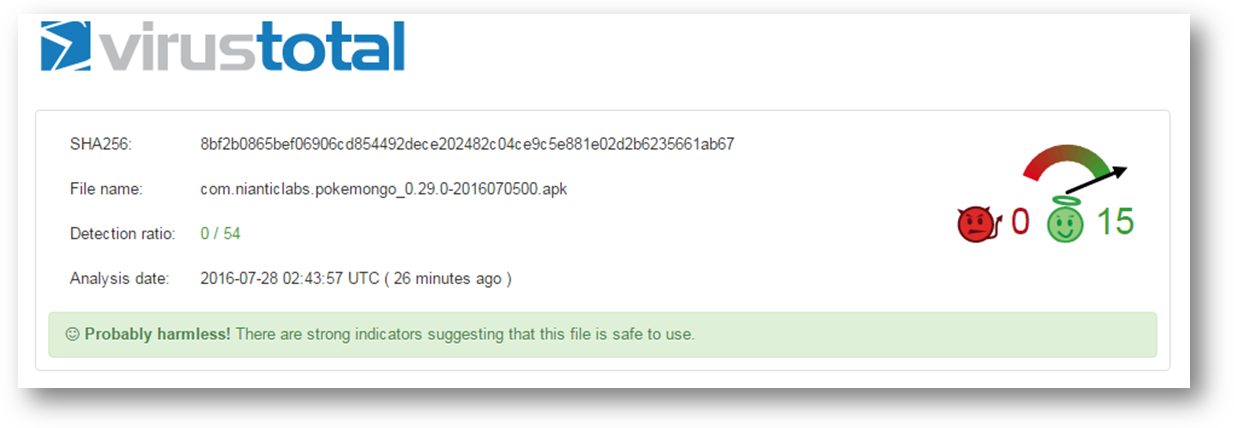
As always, we highly recommend downloading the app only from the official Google Play store when the app is available for your country.
The Pokemon fever is expected to stay, infact it's likely to increase as more countries engage in this phenomenon. Partake in this with utmost caution if you decide to catch 'em all.
Dell SonicWALL provides protection against multiple versions of this threat via the following signatures:
- GAV: AndroidOS.Pokemon.DW (Trojan)
- GAV: AndroidOS.Pokemon.DJK (Trojan)
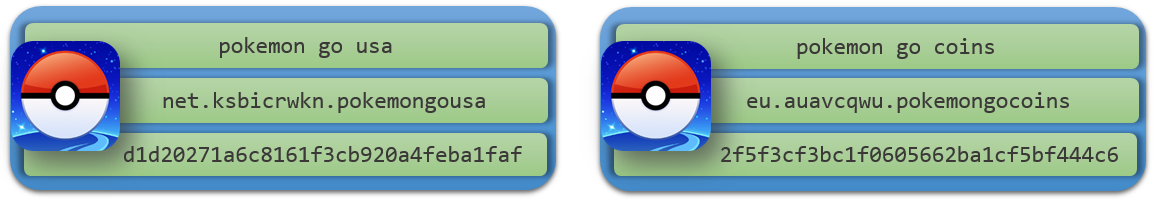
APK Package Details:
- Threat Type: Adware
- Package Name: net.ksbicrwkn.pokemongousa
- MD5: d1d20271a6c8161f3cb920a4feba1faf
- Package Name: eu.auavcqwu.pokemongocoins
- MD5: 2f5f3cf3bc1f0605662ba1cf5bf444c6
- Threat Type: DroidJack component
- Package Name: com.nian
ticlabs.pokemongo - MD5: d350cc8222792097317608ea95b283a8
- Package Name: net.droidjack.server
- MD5: 51b1872a8e2257c660e4f5b46412cb38
- Threat Type: Installer
- Package Name: com.thaipro.pokemongo
- MD5: e0a1e087908c8150609cfc80963225d6
- Package Name: com.vns.pokemongo
- MD5: e4091d1d078192eadda60cab4729130a
- Package Name: com.vns.pokemongo
- MD5: 09ef44df0faf3669809c302e5c05af3e
Share This Article

An Article By
An Article By
Security News
Security News