Critical Unauthenticated RCE Vulnerability in Cisco ISE (CVE-2025-20281)

Overview
The SonicWall Capture Labs threat research team became aware of a critical remote code execution (RCE) vulnerability in Cisco Identity Services Engine (ISE). Originally disclosed on June 25, 2025, Cisco confirmed active exploitation of CVE-2025-20281 in July 2025. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) subsequently added this flaw to its Known Exploited Vulnerabilities catalog. CVE-2025-20281 is a critical severity vulnerability (CVSS 9.8) that allows an unauthenticated attacker to execute arbitrary code as root on affected systems, potentially compromising the entire network access control infrastructure.
The vulnerability enables unauthenticated attackers to execute arbitrary code as root on affected systems. This flaw impacts Cisco ISE versions 3.3 and 3.4, as well as the related ISE-Passive Identity Connector (ISE-PIC), putting a wide range of deployments at risk. The vulnerability resides in the enableStrongSwanTunnel method where insufficient input validation leads to command injection. Because this API runs with root privileges, injected commands execute as root on the ISE appliance. Exploitation requires no authentication, making immediate patching critical. Since initial disclosure of active exploitation, multiple proof-of-concept exploits have appeared in public repositories.
Technical Overview
The vulnerability stems from how ISE handles operations for VPN services. Security researchers identified the vulnerable enableStrongSwanTunnel method in the DescriptionRegistrationListener class as the primary attack vector. This function is insecure due to insufficient validation of user-supplied input, leading to command injection. Additionally, Cisco later disclosed a related deserialization vulnerability (CVE-2025-20337) affecting the same code path.
An attacker can embed operating system commands within specially crafted API requests. When Cisco ISE processes these requests, the commands execute on the underlying OS with root privileges. The exploitation leverages environment variables like ${IFS} (Internal Field Separator) to bypass whitespace restrictions in Java's Runtime.exec() calls, allowing attackers to circumvent input filtering mechanisms.
Security researcher Bobby Gould noted that while the vulnerable code runs inside a Docker container, Cisco configured this container in privileged mode. This configuration allows attackers to escape the container and gain root access on the host system using well-known Linux container escape techniques involving cgroups and release_agent mechanisms.
Triggering the Vulnerability
To trigger this vulnerability, an attacker needs only network access to the Cisco ISE API. The API, when enabled on Cisco ISE, listens for RESTful calls (typically over HTTPS) that allow remote management of ISE. No authentication or user credentials are required.
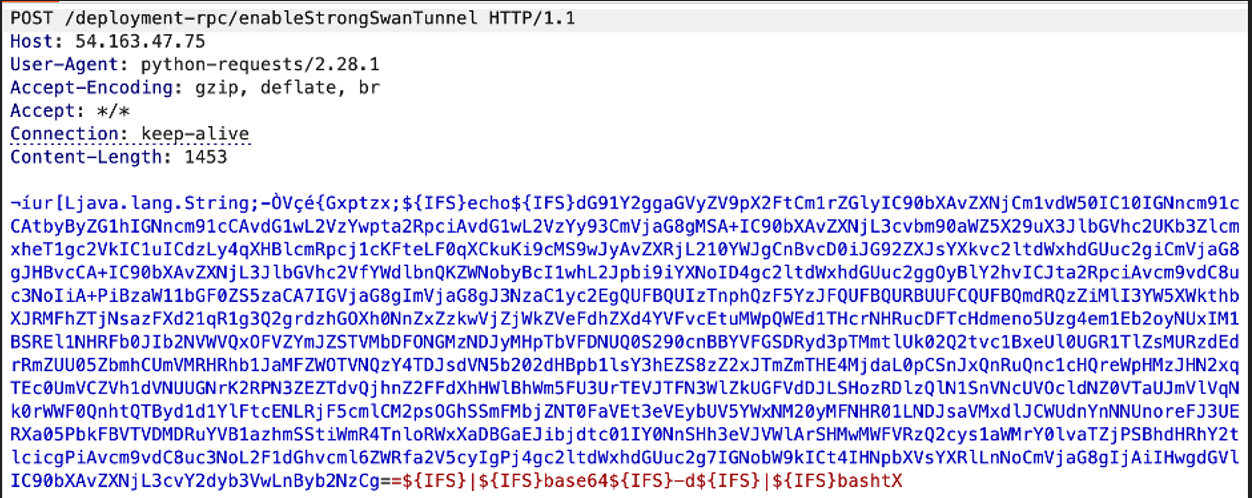
Photo Credit: ZDI
In a typical attack scenario, the adversary sends a specially crafted POST request to the vulnerable API route on the ISE server. The target endpoint is /deployment-rpc/enableStrongSwanTunnel. The attacker's request includes a malicious payload containing embedded system commands designed to create files, establish reverse shells, or execute scripts.
Due to flawed input validation, Cisco ISE fails to reject malicious input. The attacker exploits the server's trust in the malicious data, treating it as legitimate configuration. Cisco's advisory confirms that attackers can upload arbitrary files to affected devices and execute those files by exploiting this vulnerability. The crafted request instructs ISE to write malicious code onto the system and immediately execute it with root permission.
Exploitation
Following successful exploitation, attackers typically gain shell access or execute arbitrary commands on the ISE host. The ZDI researcher's exploit demonstrates a multi-step attack chain: initial code execution inside a Docker container (running as root), followed by container escape techniques to break out to the host operating system with full root access. This progression allows attackers to advance from zero access to complete system control in a single attack flow.
An additional attack vector leveraging the same vulnerability has been published in proof-of-concept code (Figure 2) on GitHub; however, there are no confirmed reports validating this as a legitimate attack path. The code demonstrates that the vulnerability can allegedly be reached via Cisco's External RESTful Services API for user management. According to the proof-of-concept, attackers would abuse the internal user creation endpoint (POST /ers/config/internaluser), which purportedly lacks authentication requirements. The claimed method involves injecting shell metacharacters into the JSON body (specifically the "name" field of an InternalUser object) to achieve root command execution. This alternate path would supposedly succeed because the ERS API fails to validate request authentication and content type, allowing malicious input to reach the vulnerable StrongSwan handling code. However, this approach differs significantly from the established ZDI research methodology, and access to vulnerable devices would be required for independent verification, which was not available at the time of this writing.
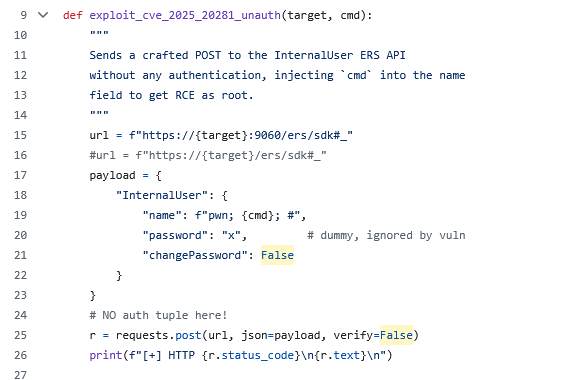
Photo Credit: GitHub
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following security signature has been released:
IPS: 21305 Cisco Identity Services Engine invokeStrongSwanShellScript RCE
IPS:21340 Cisco ISE-PIC Remote Command Execution
Remediation Recommendations
Organizations should implement the following steps:
Apply Cisco's Patches: Upgrade Cisco ISE to a fixed software release. Cisco has issued patched versions for affected branches—specifically, update ISE 3.3 to Patch 7 or later and ISE 3.4 to Patch 2 or later, which contain permanent fixes for this vulnerability. Earlier 3.x releases (3.1, 3.2, etc.) are not affected by this vulnerability but should be updated to supported versions for ongoing security.
Disable ERS API if Unused: If the External RESTful Services API is not required in your environment, disable it. The ERS API in Cisco ISE is an optional service (disabled by default) that administrators can enable for integrations.
Restrict Network Access: Limit exposure of Cisco ISE management and API interfaces. Ensure that ISE's administrative web interface (including ERS endpoints) is not directly accessible from the internet or untrusted networks.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
