Secure Web Gateway (SWG)
What is a Secure Web Gateway (SWG)?
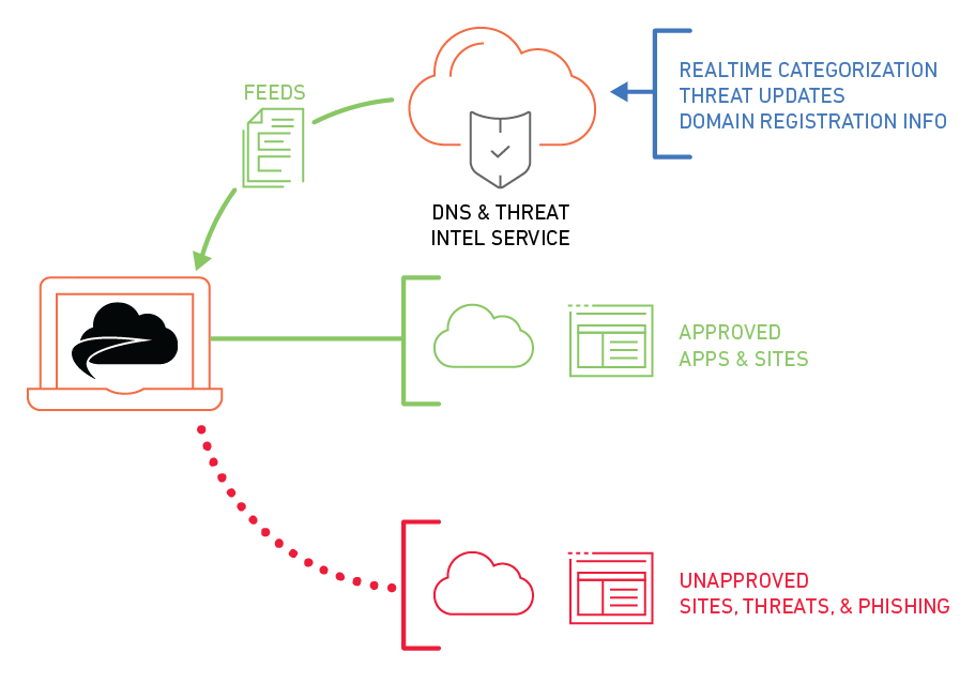
A Secure Web Gateway (SWG) acts as an efficient proxy, or intermediate server, between users and the internet, inspecting all outgoing web traffic for security threats such as malware, phishing, and malicious websites.
How Does a SWG Work?
A Secure Web Gateway (SWG) functions as a barrier between users and the internet, ensuring that web traffic is safe and compliant with organizational policies. When a user attempts to access a website or use a cloud application, the traffic is first routed through the SWG. This can happen through an on-premises device, a cloud-based service, or a hybrid deployment, depending on the organization’s setup.
As traffic passes through the SWG, it is inspected in real time. The gateway analyzes web requests and responses for malicious content, such as viruses, malware, and phishing attempts. It also decrypts and inspects encrypted HTTPS traffic to identify hidden threats. The SWG applies a set of preconfigured security and access policies—these might include blocking access to certain websites, restricting downloads, or enforcing data loss prevention rules.
If the web content or request violates any policies or contains a threat, the SWG blocks the action and may alert administrators. Otherwise, the request is allowed and the user gains access to the content. Throughout this process, the SWG continuously logs user activity, enabling security teams to monitor behavior, generate reports, and meet compliance requirements.
In essence, an SWG ensures that users can safely access the internet while protecting the organization from web-based threats and enforcing appropriate usage standards.
Use Cases
Secure Web Gateways (SWGs) serve a variety of critical functions in enterprise security strategies. Here are several common use cases that highlight their value:
One of the most prevalent use cases for an SWG is malware and threat prevention. By inspecting web traffic in real time, SWGs can block access to malicious websites, prevent the download of infected files, and stop phishing attempts before they reach users. This makes them essential for defending against ransomware, spyware, and other forms of web-based attacks.
Another key use case is enforcing acceptable use policies. Organizations often need to control employee access to non-work-related or inappropriate websites, such as social media, gambling, or adult content. SWGs allow IT teams to define and enforce these policies, helping maintain productivity and reduce legal and reputational risks.
Data loss prevention (DLP) is also a significant function of SWGs. By monitoring outbound traffic, an SWG can detect and block the unauthorized sharing or upload of sensitive data, such as customer information, intellectual property, or financial records. This is particularly important for compliance with regulations like GDPR, HIPAA, or PCI-DSS.
Additionally, SWGs help manage and control shadow IT and cloud app usage. They provide visibility into which unsanctioned SaaS applications users are accessing, allowing security teams to assess risk and enforce access policies accordingly.
Finally, remote workforce protection has become a vital use case, especially with the rise of hybrid and fully remote work environments. Cloud-based SWGs extend the same security controls and policy enforcement to remote users, regardless of their location or device, ensuring consistent protection across the organization.
These use cases demonstrate how SWGs serve as a central component in securing web access, protecting data, and maintaining regulatory compliance in today’s complex IT environments.
Benefits of a Secure Web Gateway
A SWG acts like an internet filter, sifting dangerous content from web traffic to stop threats and data breaches. Secure Web Gateways play a crucial role in safeguarding organizations against web-based threats. Below are important benefits for using a SWG:
- Enhanced Security: SWGs provide proactive protection against web-based threats, reducing the risk of malware infections, data breaches, and other cyber-attacks originating from malicious websites or downloads.
- Regulatory Compliance: By enforcing web usage policies and data protection measures, SWGs assist organizations in meeting regulatory requirements, such as those outlined by data protection laws or industry-specific regulations.
- Productivity Improvement: SWGs offer control and visibility into web activity, enabling organizations to manage non-work-related web usage, increase productivity, and reduce bandwidth consumption.
- Cost Savings: The prevention of security incidents and data breaches through SWGs can save organizations substantial costs associated with remediation, recovery, and potential legal ramifications.
- Centralized Management: SWGs provide a centralized management interface for configuring and monitoring security policies, allowing administrators to efficiently manage web traffic across the entire network.
Challenges and Considerations
While Secure Web Gateways (SWGs) provide critical protection for organizations, they also come with certain challenges and considerations that must be addressed for successful deployment and ongoing use.
One major challenge is the complexity of deployment and configuration, especially in hybrid or multi-cloud environments. Organizations must decide whether to implement an on-premises, cloud-based, or hybrid SWG solution, each with different implications for scalability, performance, and management. Misconfigurations can lead to policy gaps, degraded user experience, or exposure to threats.
Another important consideration is SSL/TLS decryption. Modern web traffic is heavily encrypted, and while SWGs can decrypt and inspect this traffic, doing so at scale requires significant resources and can introduce latency. Organizations must balance security with performance and also address privacy concerns, especially when inspecting sensitive or personal data.
Integration with existing security infrastructure is also a key consideration. An SWG must work seamlessly with tools such as identity providers, firewalls, SIEMs, and endpoint protection platforms. Poor integration can result in fragmented visibility and inconsistent policy enforcement across the organization.
User experience impact is another common concern. If the SWG is too restrictive or introduces noticeable delays, users may seek ways to bypass it, potentially increasing risk rather than reducing it. Fine-tuning access policies to strike a balance between security and usability is essential.
Lastly, ongoing management and policy updates require dedicated effort. Threat landscapes evolve quickly, and maintaining up-to-date policies and threat intelligence is crucial. Organizations need to allocate sufficient resources to monitor logs, adjust configurations, and respond to incidents in a timely manner.
Understanding these challenges helps ensure that an SWG is effectively implemented, maintained, and aligned with broader security and business objectives.
The SonicWall Advantage: SWG Capabilities
SonicWall’s Cloud Secure Edge (CSE)'s Secure Internet Access (SIA) license delivers SWG capabilities that follows users and protects their web access wherever they may be. CSE's SWG capabilities allows organizations to block risky or unauthorized user behavior while enabling acceptable use policies (AUPs) for compliance. Below is a list of advantages of using SonicWall’s SWG:
- Always-on Protection: Our CSE app is able to provide protection even when not running due to how it is integrated into the operating system. Your users do not need to login or start the app to be protected.
- URL Filtering: Our SWG employs URL filtering techniques to block access to malicious or inappropriate websites, ensuring that users only visit trusted and safe web resources.
- Malware Detection and Prevention: We use advanced scanning mechanisms to identify and block malicious files, preventing malware infections and reducing the risk of data breaches.
- Phishing Prevention: Even when users click on bad links, access is immediately blocked to make sure that users aren’t handing over personal or financial information.
- Application Control: The CSE’s SWG allows organizations to control and manage access to various web applications, ensuring compliance with security policies and reducing the risk of unauthorized software usage.
- Real-time Categorization: Newly seen or created domains, as well as newly flagged threat domains, are categorized by our Artificial Intelligence (AI) scanning engine within seconds.
- Unlimited Block/Allow Lists: Use broad categories to quickly enhance security, and create block and allow lists to enable your employees while being as granular with your policies as possible.
Find out more about SonicWalls’s SWG Capabilities in Cloud Secure Edge.