Understanding SalatStealer: A Threat Actor’s Golang Stealer Toolset

Overview
This week, SonicWall Capture Labs Threat Research Team analyzed a sample of SalatStealer. This is a Golang malware capable of infiltrating a system and enumerating through browsers, files, cryptowallets and systems while embedding a complete array of monitoring tools to push and pull any data on disk.
Infection Cycle
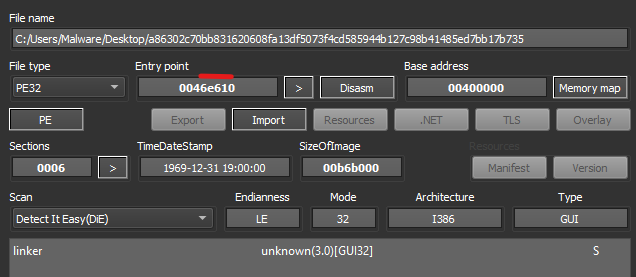
Initial detection of the sample shows that it is UPX packed. Unpacking via UPX’s built-in utility is able to be done without issue. The unpacked file is shown as ‘unknown’ when run through DIE again, but the linux ‘file’ utility gives a 32-bit Windows PE. An initial search of the strings shows a Golang build ID and libraries.
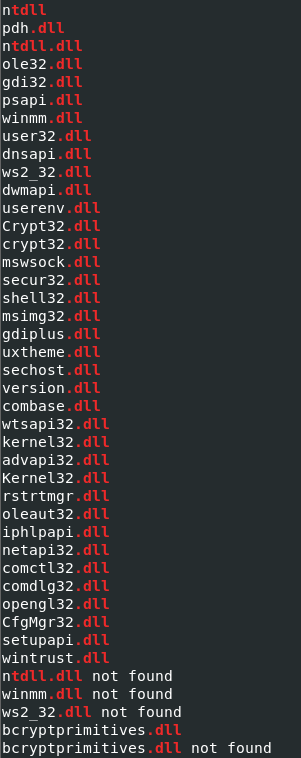
There is only one statically linked library is kernel32.dll, while FLOSS indicates that there are multiple libraries that could be loaded at runtime. Since the process is capable of reading the process execution block (PEB) and side-loading libraries into itself and other processes, the dynamic loading allows for flexibility in communication, compression, and system enumeration.
Once the program starts, the first check is for a cpuid to validate that the system is legitimate. If this fails, the program exits. A success loads Go libraries and additional routines to begin enumerating user accounts, running processes, and OS information. If the current account is unable to run or load the application with appropriate permissions, privilege escalation is performed.
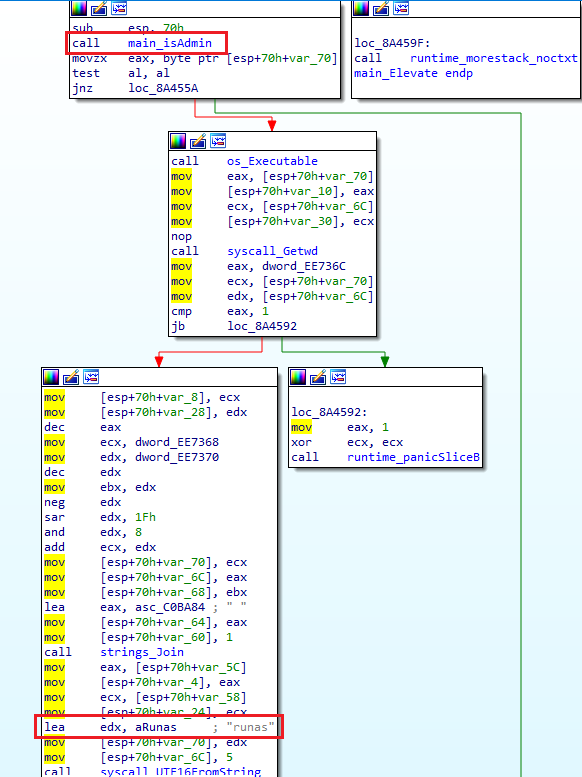
Along with escalation, a keylogger is initialized that tracks both GetKeyState and GetKeyAsyncState. The program also monitors mouse location and click activity, and takes regular screenshots. All of this is put on a schedule to be compressed and sent to a randomized IP address.
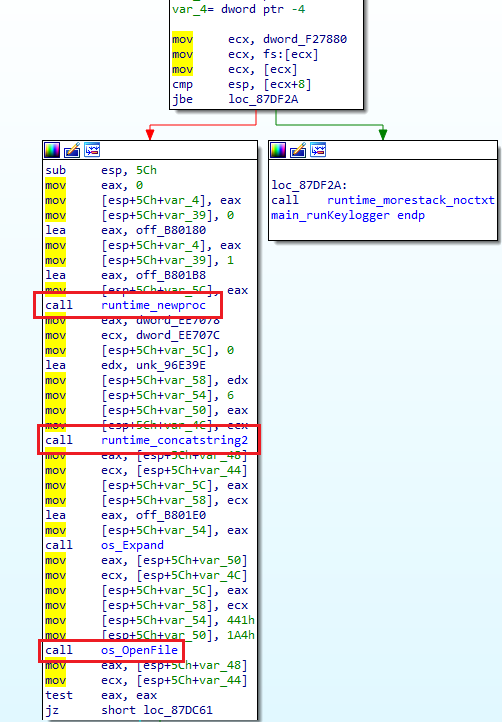
There are regular checks for debugging by the use of software breakpoints that, when triggered, will crash the malware. Further analysis in IDA pro revealed a variety of structs and attributes were found for targeted applications.
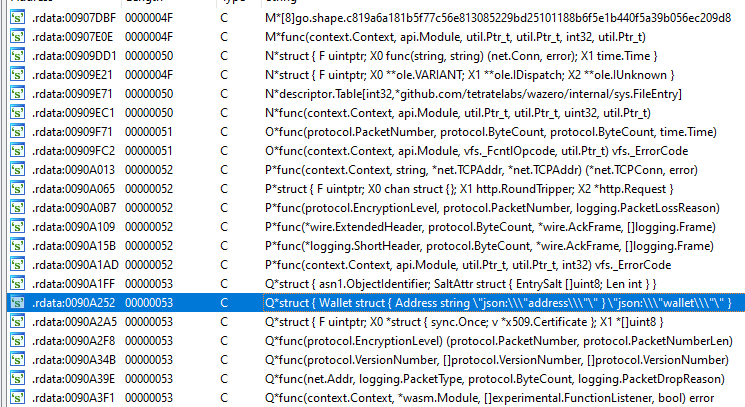
Starting from memory offset .rdata:0096E1B0, there are stackstrings showing many of the malwares’ targets on a victim system, listed below:
Targeted Wallets
| Armory | Coin98 | Finnie | Pontem |
| Atomic Wallet | Coowon | Guarda | Saturn |
| Bitapp | Exodus | Iconex | Sollet |
| Chedot | Dragon | Kaikas | Wombat |
| Coinomi Wallet | Fenrir | Kometa | XMR.PT |
| CocCoc | Fewcha | Oxygen | XinPay |
Targeted Browsers
| 7Star | Citrio | Iridium | Orbitum | Vivaldi |
| Amigo | CyberFox | K-Melon | QIP Surf | Yandex Browser |
| Brave | DC Browser | Kometa | Slimjet |
|
| CentBrowser | Edge | Liebao | Thorium |
|
| Chedot | Epic Privacy | Maxthon3 | Torch |
|
| Chrome | Firefox | Opera | UR Browser |
|
Additional targeted apps:
- Telegram
- Steam
- Discord
If the victim system has SQL installed, the following commands will run against any database found:
- SELECT item1, item2 FROM metaData WHERE id = 'password'
- SELECT origin_url, action_url, username_value, password_value, date_created FROM logins
- SELECT origin_url, username_element, username_value, password_element, password_value, signon_realm FROM logins
- SELECT name,encrypted_value,host_key,path,expires_utc FROM cookies WHERE length(encrypted_value) > 0
- SELECT LogonId, StartTime, LogonType FROM Win32_LogonSession WHERE LogonType=2
When strings have been parsed, there are multiple tools integrated from github that are easily identified:
- github.com/tetratelabs/wazero/
- github.com/quic-go/
- github.com/ncruces/go-sqlite3/
- github.com/lxn/win
- github.com/nfnt/
- github.com/go-ole
- github.com/yusufpapurcu/wmi
- github.com/StackExchange/wmi
- github.com/rickb777/date
- github.com/capnspacehook/taskmaster
- github.com/rodolfoag/gow32
- github.com/andygrunwald/vdf
- github.com/gorilla/websocket
- github.com/buger/jsonparser
Sonicwall Protection
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: GremlinMod.STL (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI™ and the Capture Client endpoint solution.
IOCs
MD5: d32af766300df849fecaf3f9d9808db4
SHA-1: 4fa9319f0f6b55506e43dee8c764afdeb7e5ba2e
SHA-256: a86302c70bb831620608fa13df5073f4cd585944b127c98b41485ed7bb17b735
Share This Article

An Article By
An Article By
Security News
Security News