TOR chat with Black Basta ransomware operator runs dry

The SonicWall Capture Labs threat research team has recently been tracking a ransomware family called Black Basta. Black Basta first appeared in April 2022 and is believed to be operated by a well organized cybercrime group called Fin7. It has been reported that this group has already breached over 90 organizations and caused over $1B USD in damage.
Infection Cycle:
Upon execution, a console appears with the following text:
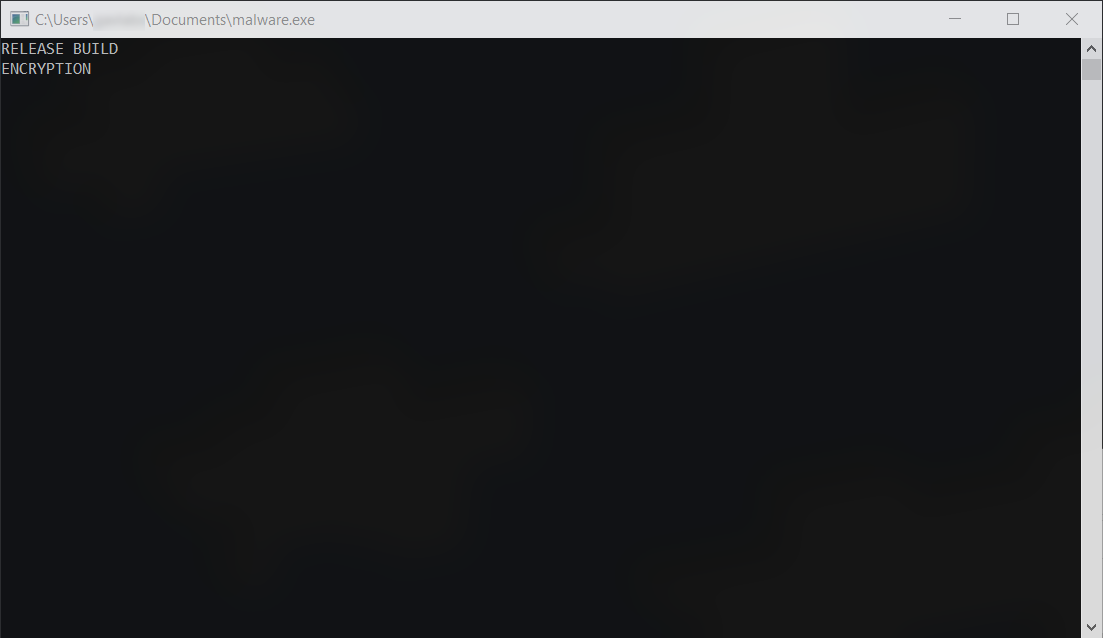
It then quickly disables console output using the FreeConsole Windows API:
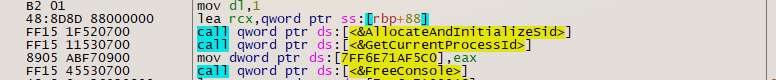
It obtains information about storage volumes attached to the system and begins its encryption process:
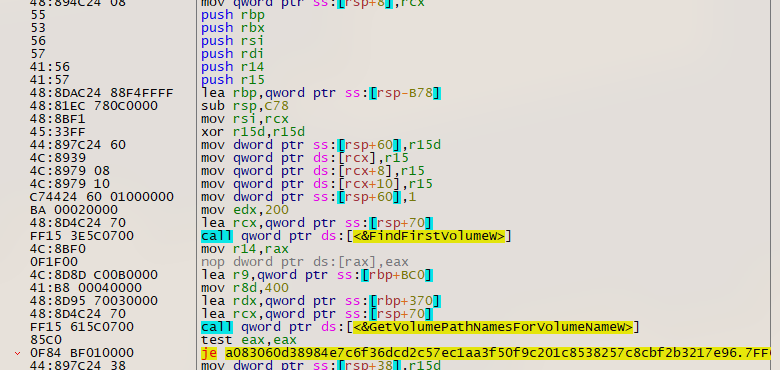

Encrypted files are given a ".basta" file extension.
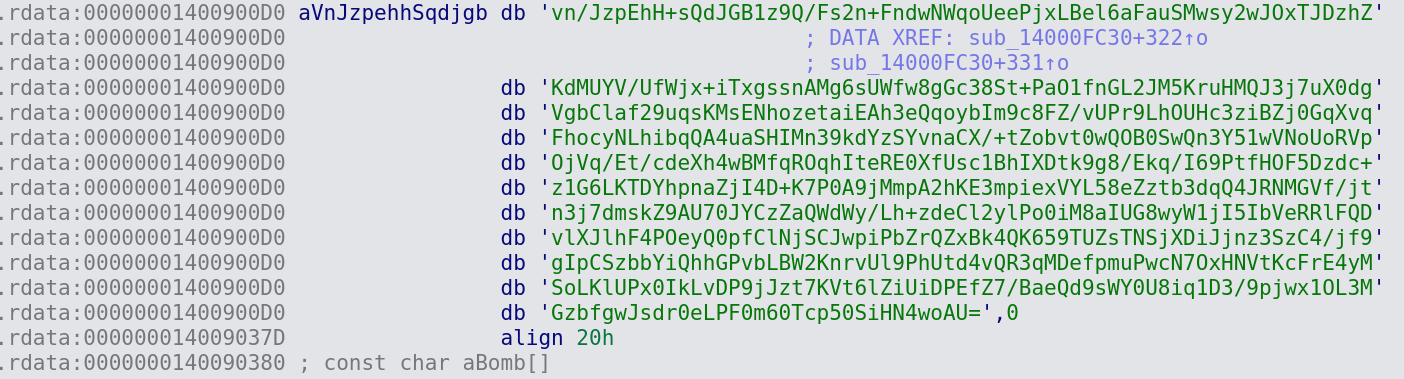
The malware uses RSA encryption. The key is hardcoded and can be seen in the decompiled binary:
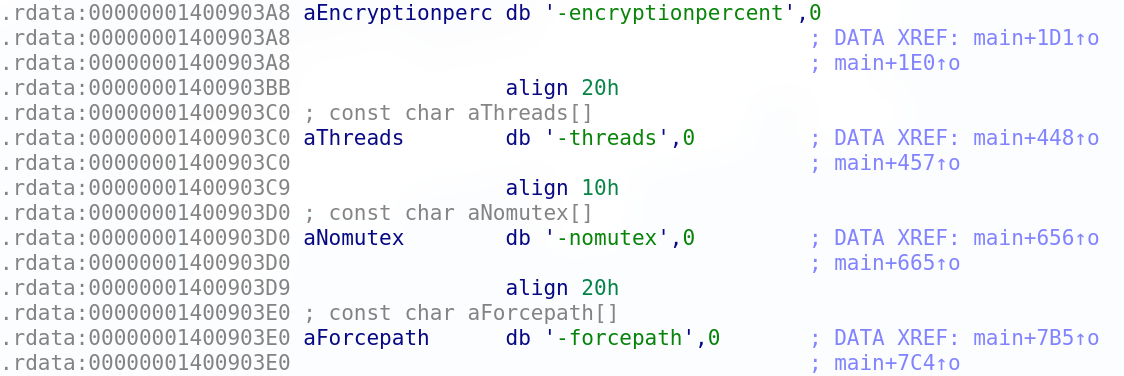
Various configuration options can also be seen in the decompiled code:
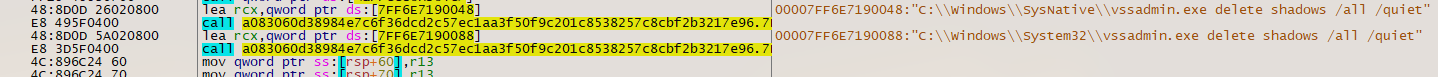
In order to prevent system recovery, the malware disables volume shadow copies using the vssadmin.exe program:
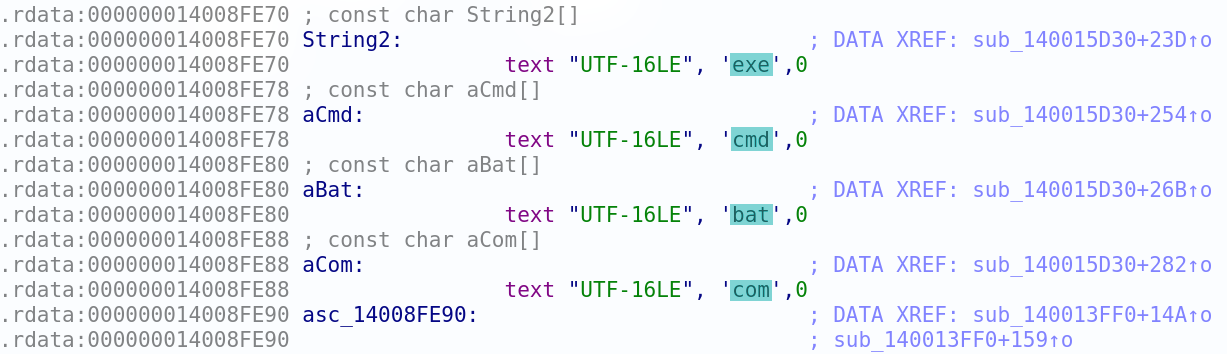
The malware drops dlaksjdoiq.jpg

dlaksjdoiq.jpg contains the following image:

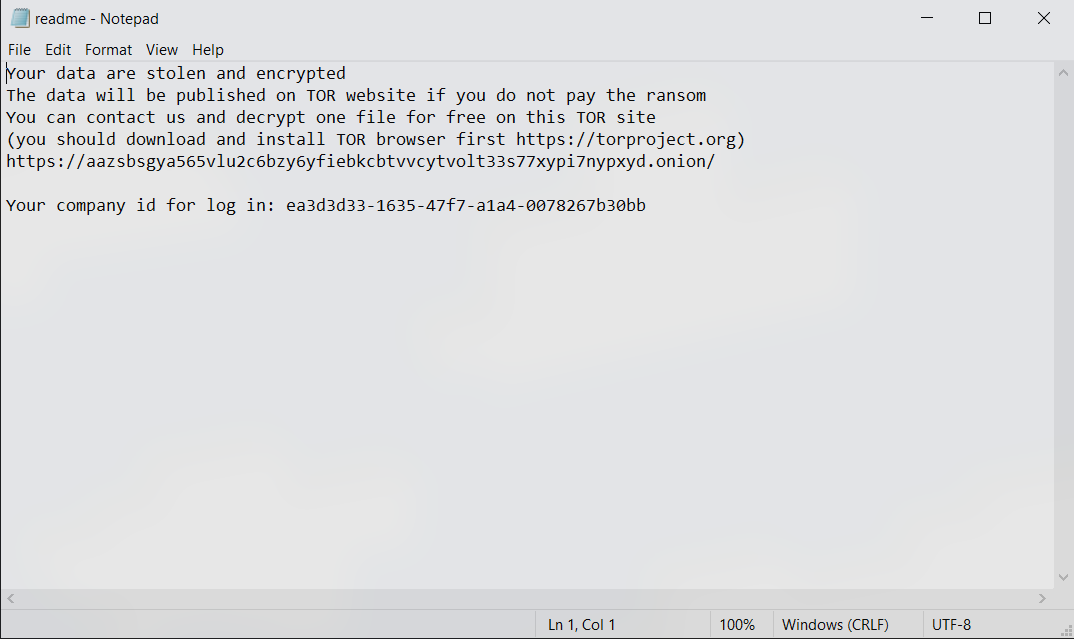
A ransom message is written to readme.txt. This file is copied into all directories containing encrypted files:
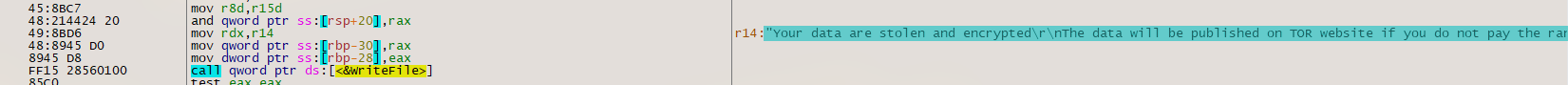
readme.txt contains the following ransom message:
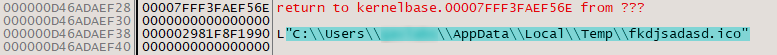
fkdjsadasd.ico is dropped onto the system:
It contains the following icon:

The tOr link leads to the following page:
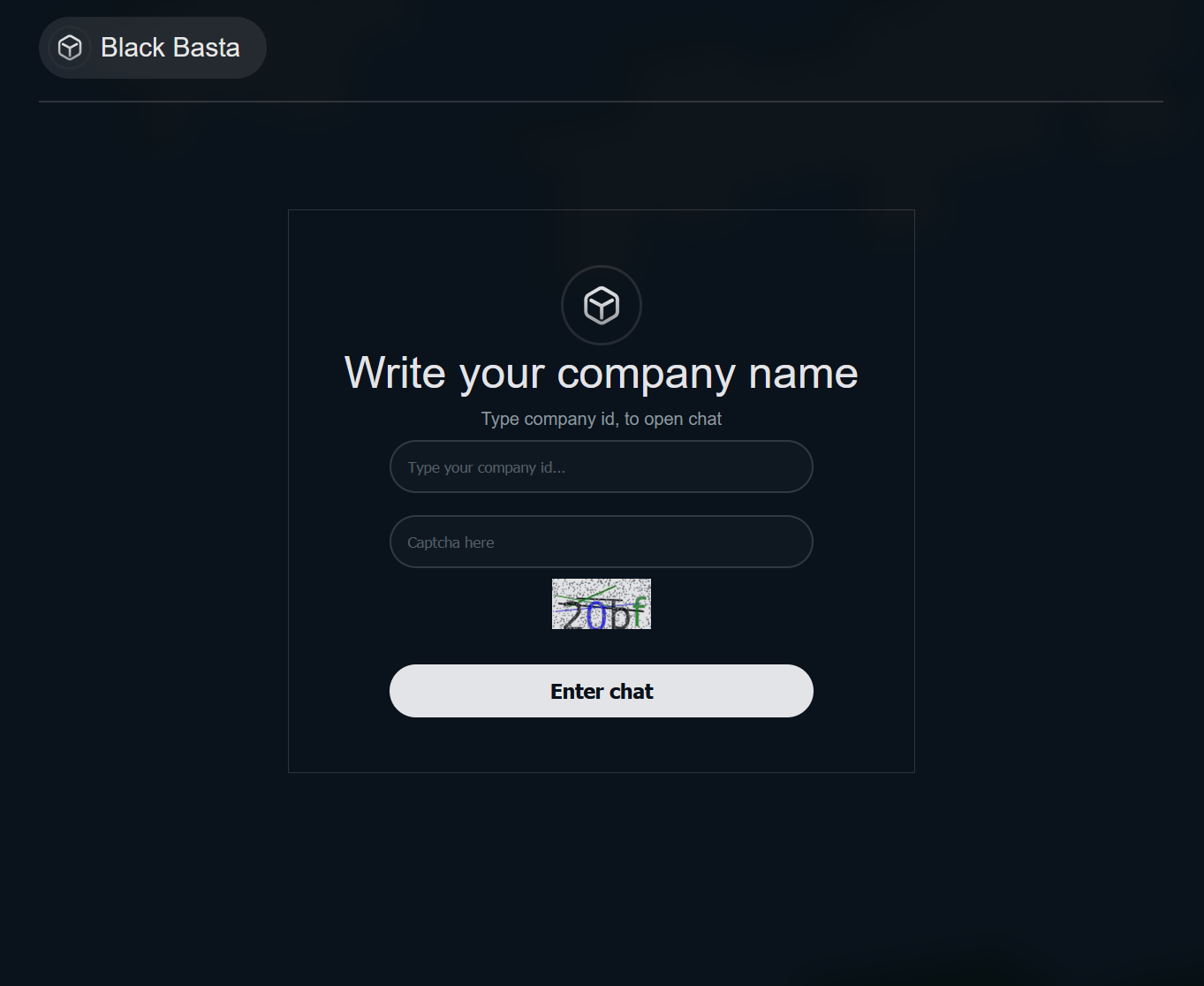
After logging in using the requested information, a chat interface is presented:
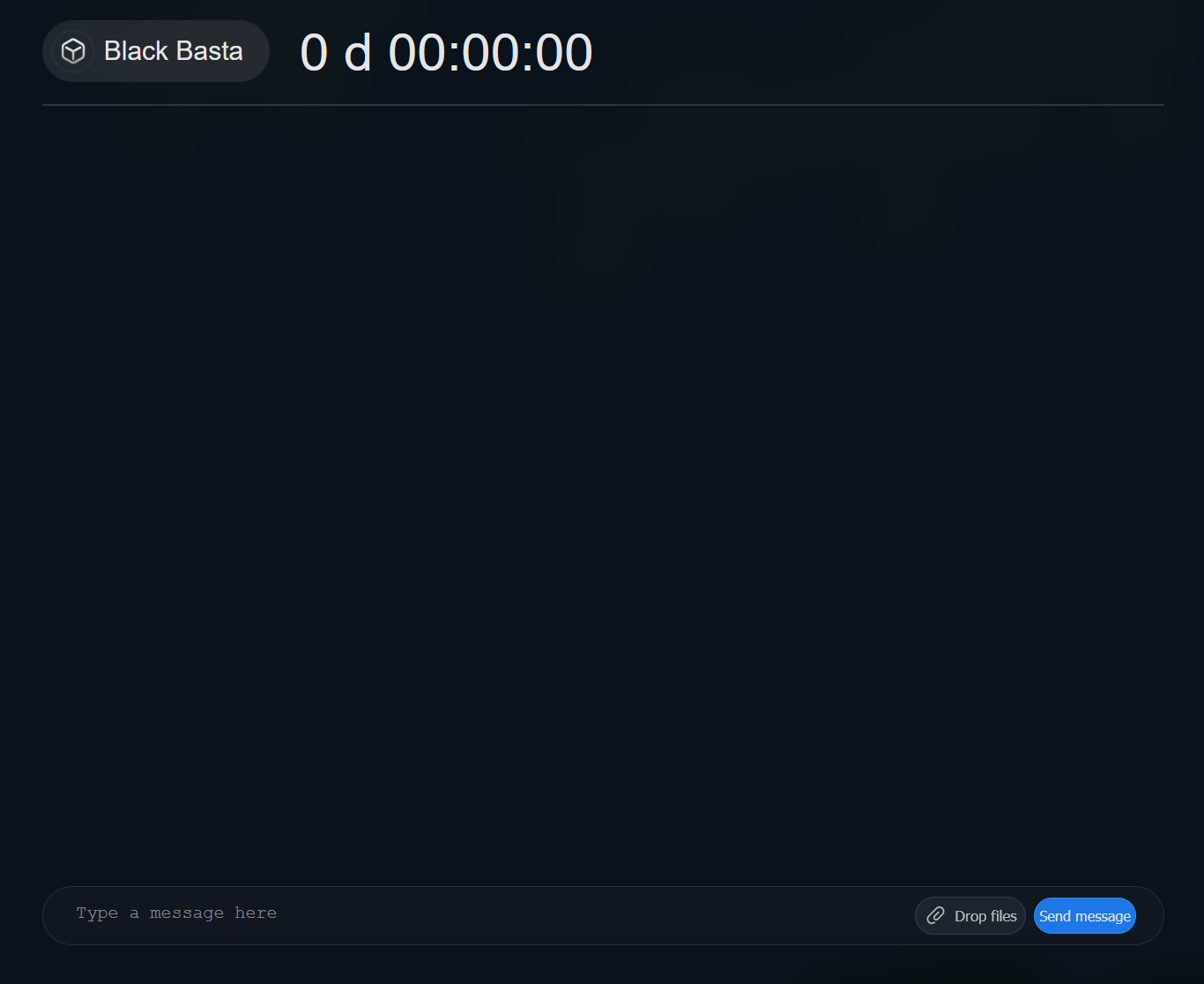
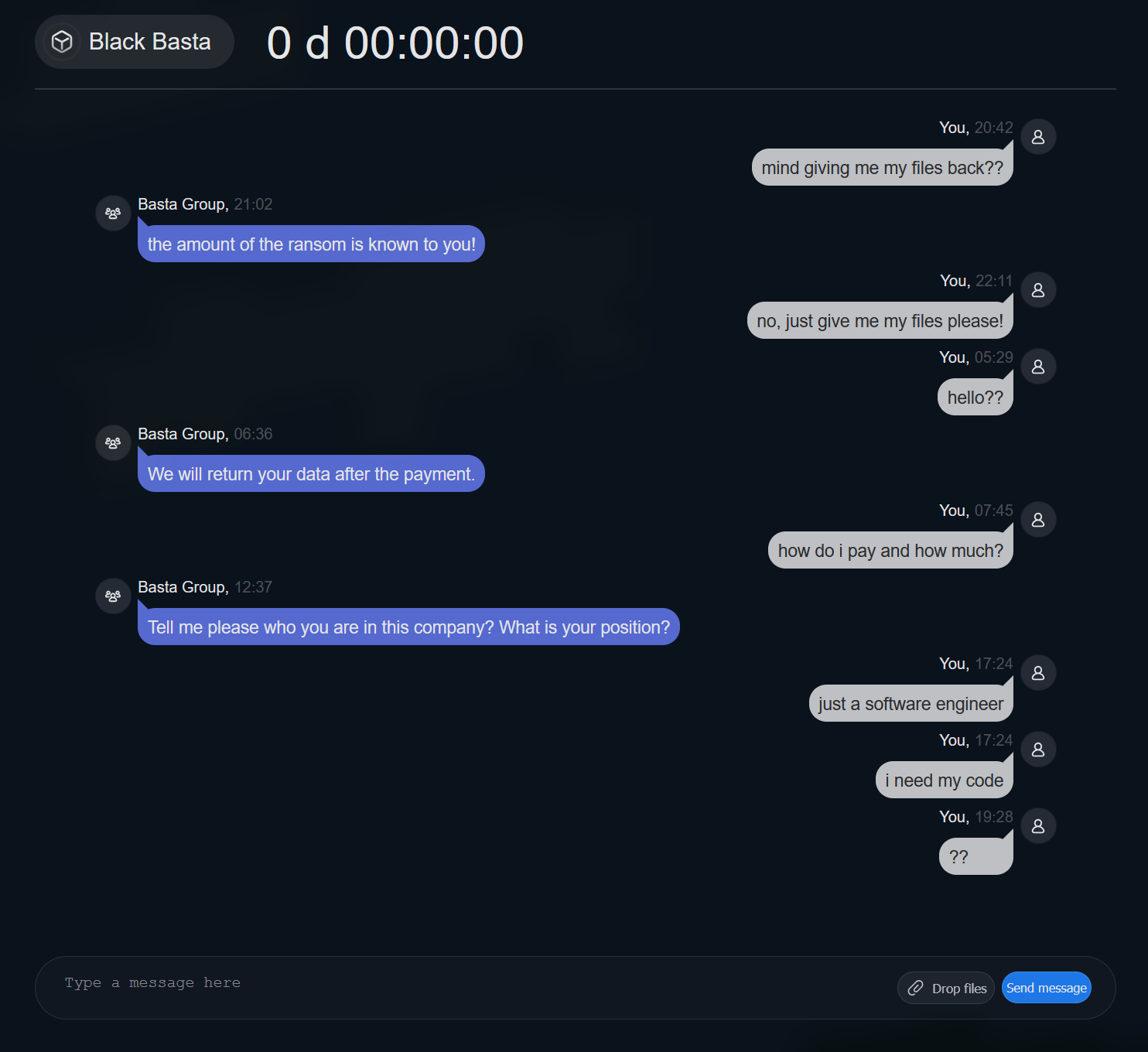
We had the following conversation with the attacker but were unable to obtain information about file retrieval costs:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: BlackBasta.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News