Malicious Cyber activity roundup: The Thanksgiving week 2018 edition

As retailers are gearing up with their Black Friday doorbuster deals, cybercriminals are also upping the ante to lure shoppers into clicking that malicious link or downloading that latest shopping app in exchange for deals and best prices on their most coveted items.
Here at the SonicWall Capture Labs, we have spent the last few weeks combing through file samples, websites and emails that have surfaced with all the sales, top deals and freebies. We rounded up some of the most common tricks cybercriminals use that consumers should watch out for.
Spam is still one of the top sources for shady deals that can lead victims to giving up their personal information. The spam emails we have seen have a common theme of trying to lure consumers to clicking malicious links embedded within the body of the email. Some of the common email subjects are:
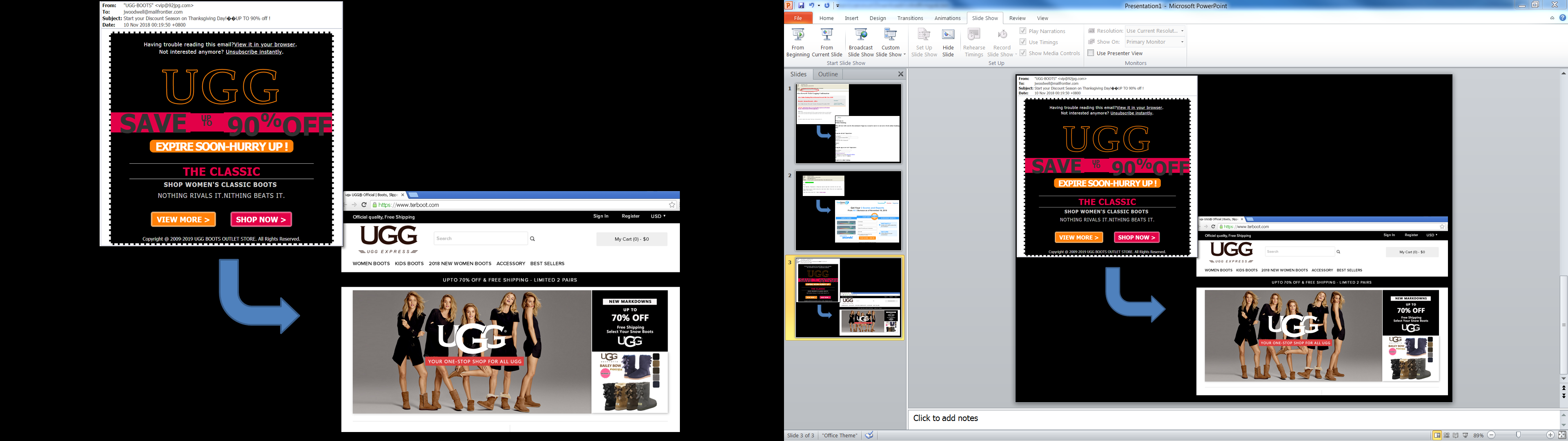
- Start your Discount Season on Thanksgiving Day! UP TO 90% off !
- Spray in your mouth and drop 25 lbs by Thanksgiving
- Thanksgiving Flash Sale
- Last day to order in time in BlackFriday (free shipping) win $63
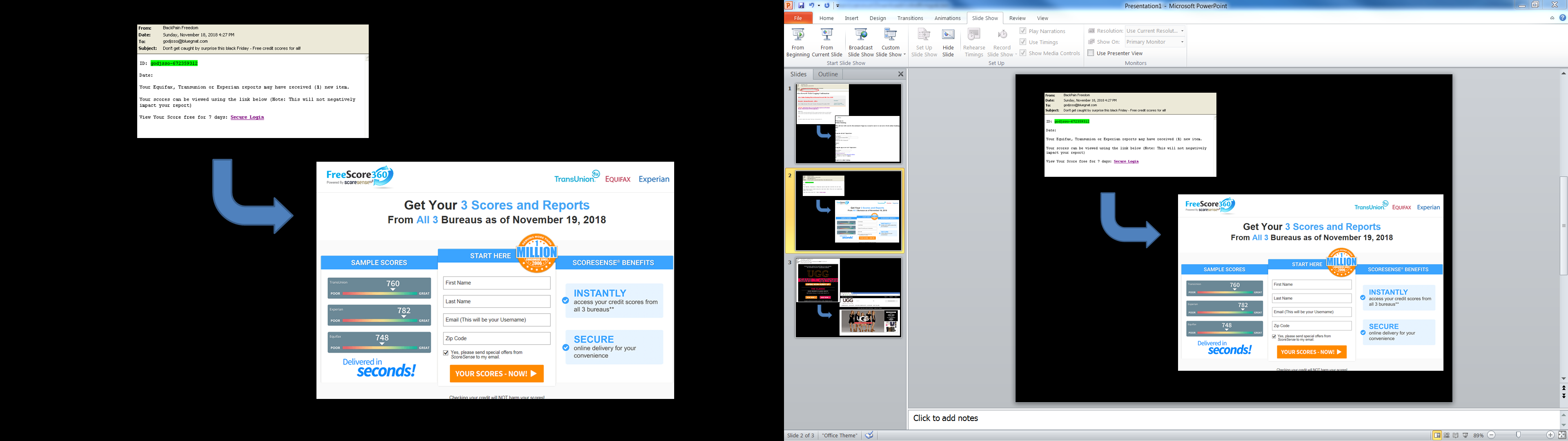
- Don't get caught by surprise this black Friday - Free credit scores for all!
We have also noticed an increase in the amount of phishing emails promising rewards and free money pretending to be from popular retailers such as Amazon, Walgreens, CVS or even banks.
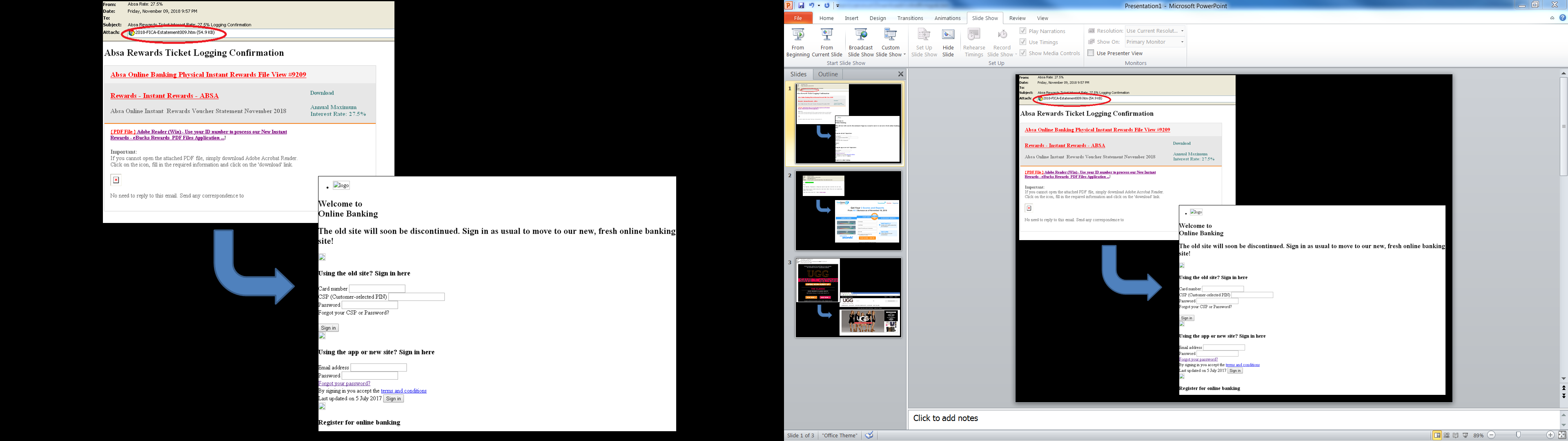
- Absa Rewards Ticket Interest Rate: 27.5% Logging Confirmation
- CVS e-rewards , #9483255
- you have amazon rewards ending tonight (vouch 9049229)
- Your amazon.com: prime-rewards 101490715 expiring: scott2013 thanks
- scott2013 here are your new walgreens-rewards ending tonight (wal-7761433937)
Looking further at the phishing email from Absa bank, for instance, the message promises an outrageous interest rate of 27.5%. Once you follow the link to claim the “reward”, the victim will be taken to a fake banking website different from the actual bank’s website asking for his online banking login information.
The “free” credit score spam email is similar. Once the victim clicks on the link, he will then be taken to a website asking for his personal information to get “instant access” to his credit scores.
Another example is from a retailer promising a discount of up to 90%! The victim will then be taken to a fake website. There is never a guarantee of ever receiving the products when you shop on such sketchy websites.
Since savvy shoppers have increasingly been downloading and using apps that are related to shopping when looking for deals this season, malware writers are spreading their malicious creations and target unsuspecting shoppers on mobile platforms.
We observed a few malicious Android samples with interesting app names that fall into line with the current shopping season:
- Amazon Shopping
- Aliexpress Shopping App
- eBay
- Jumia Online Shopping
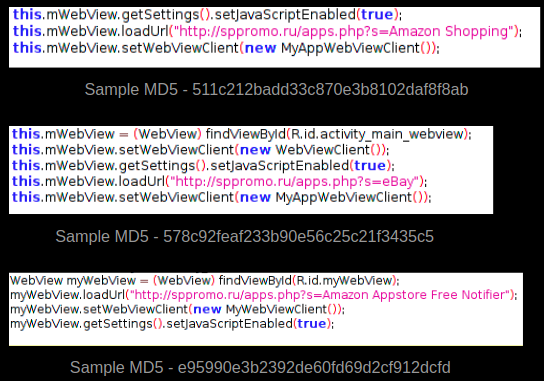
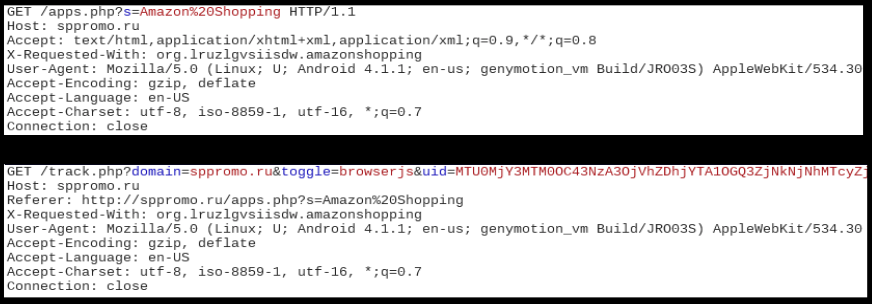
When executed, these apps show similar behaviors - they communicate with malicious domains based on hardcoded links within the code:
As clearly visible, for each of these links the value of parameter "s"changes.
We saw the following GET requests to the host:
At the time of writing this blog the domain appears to have been taken down and therefore we did not see any further communication between the app and this domain.
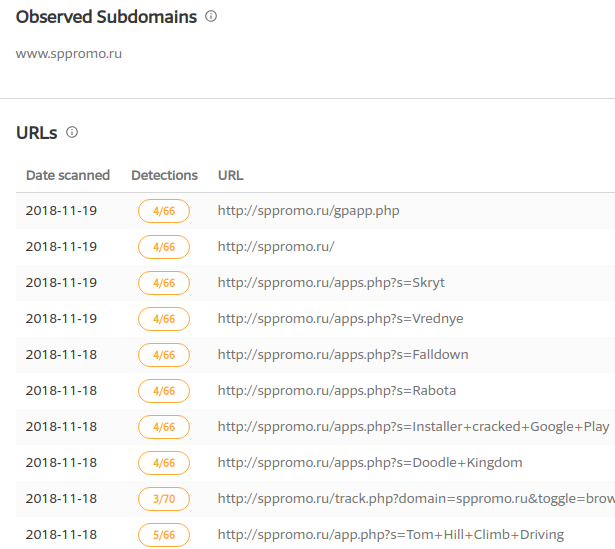
Further investigation about the domain - sppromo.ru - gave us more insight about the widespread nature of this threat:
- This campaign contains a number of different infected apps based on VirusTotal results for this domain. As shown below multiple links are present under this domain with different values for the variable s signifying multiple app names:
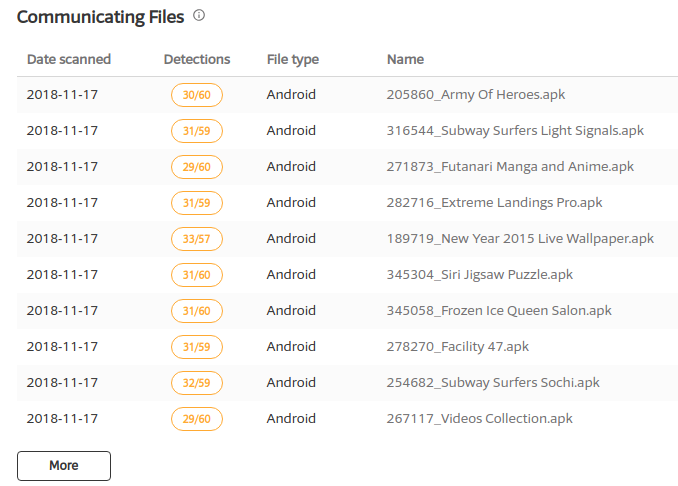
- Multiple malicious apk files can be seen associated with this domain:
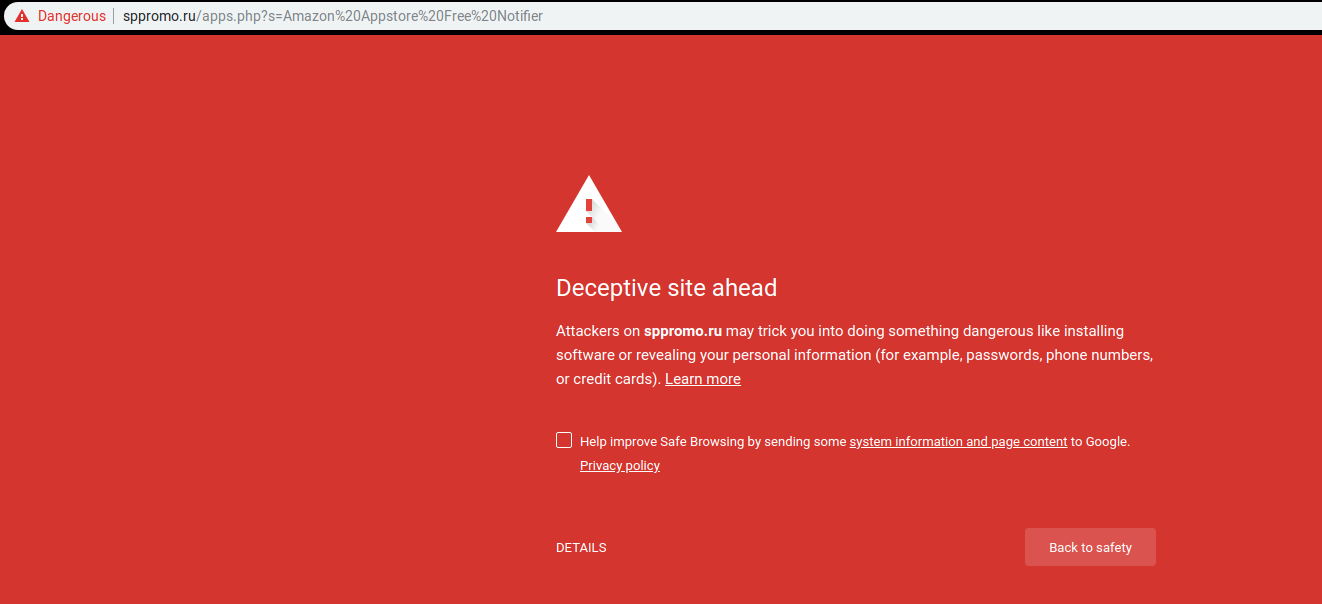
- The Google Chrome browser even identifies this website as "deceptive" and gives a warning when this link is visited:
We analyzed a number of samples belonging to this threat, interestingly the earliest sample appears to be from mid-November 2018 indicating that this is a fairly new threat campaign. The timing of this campaign with Black Friday may be a coincidence, regardless it is possible that the attackers created more apk's with shopping related names to increase their chances of infecting more unsuspecting users since they already have some apps with such names as mentioned earlier.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: AndroidOS.SPP.DWNL (Trojan)
Here are some hashes of a few additional samples from this campaign:
-
- Amazon
- e95990e3b2392de60fd69d2cf912dcfd - Amazon Appstore Free Notifier
- 085c5e419f0d86222ea08b95df765f92 - Amazon
- 511c212badd33c870e3b8102daf8f8ab - Amazon Shopping
- Amazon
-
- Shopping
- 73e79c49410a31a3bc4c58d91ae8ca00 - Jumia Online Shopping
- 4a62fb20248a6c5ea6930fb384895ad9 - Aliexpress Shopping App
- f44cc20ce344fbd0880f98b816b4c1db - Aliexpress Shopping App
- Shopping
-
- eBay
- 8157c2c5ceb3f045781c4d09982329df - eBay
- 578c92feaf233b90e56c25c21f3435c5 - eBay
- eBay
Share This Article

An Article By
An Article By
Security News
Security News