A Look At RondoDox ARM Malware

Overview
This week, the SonicWall Capture Labs Threat Research Team analyzed a sample of RondoDox, a Linux botnet infector. This malware is often paired with Mirai, and once installed on a victim system, it accepts C2 commands and can perform system reconnaissance while joining botnet DDoS activities. It has several methods of evading detection along with anti-debugging capabilities.
Technical Analysis
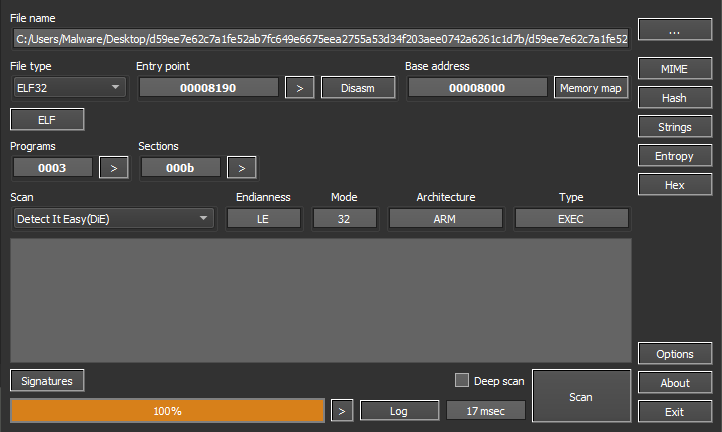
Initial detection of the sample shows a 32-bit ELF binary for ARM architecture. The symbol table has been stripped to make analysis more difficult.
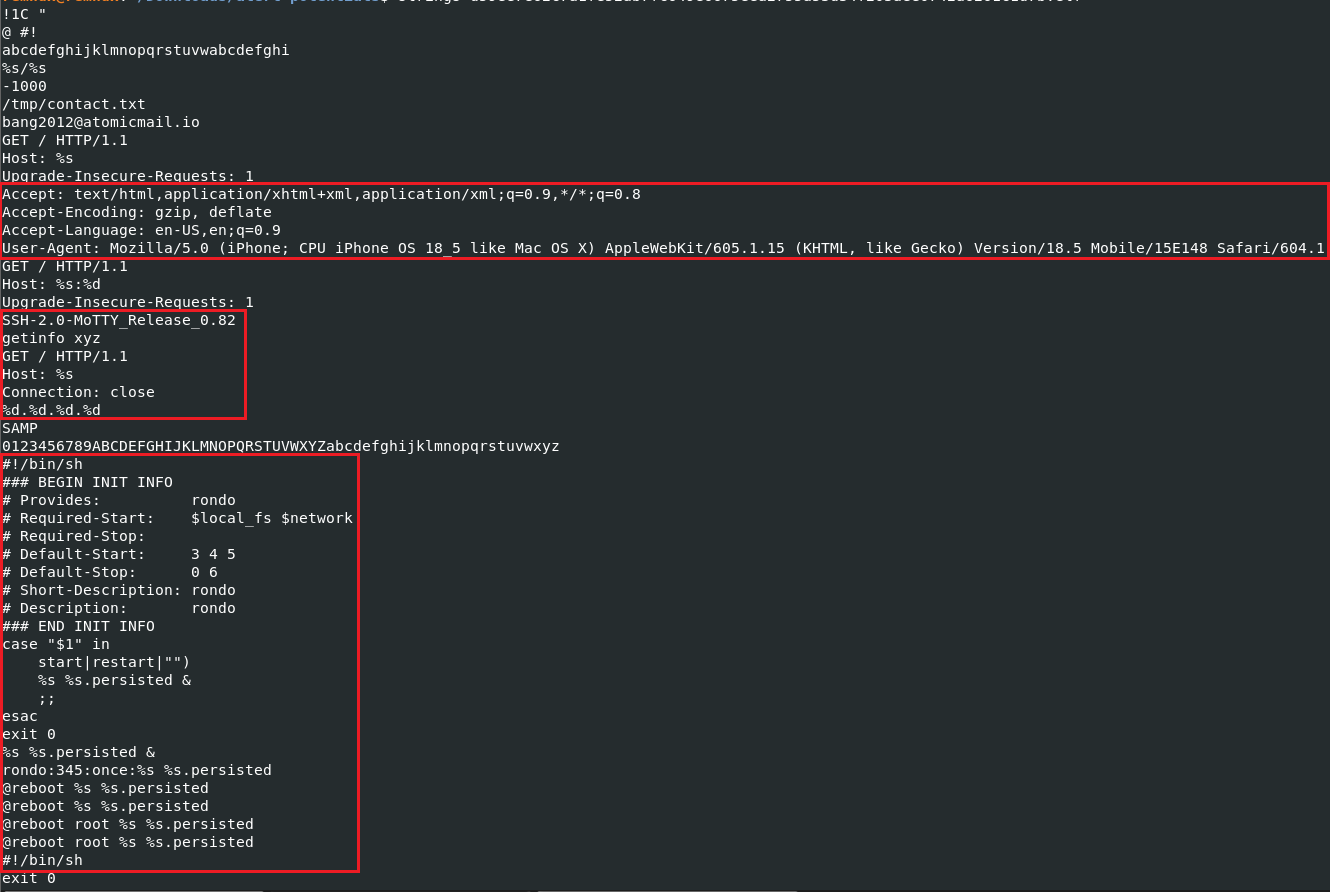
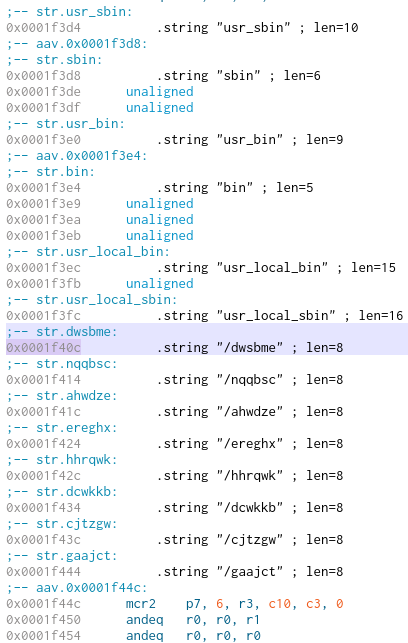
There are a variety of cleartext strings available from an initial search, including a user-agent associated with iPhone OS, the shell script configuration, and network items to enumerate for C2 communications. There is an output file of ‘/tmp/contact.txt’ if runtime is successful, but the file will unlink and delete itself if run without the proper environment.
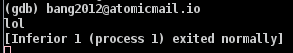
Running the binary will result in an email address printing in the terminal along with ‘lol’. The sample then deletes itself. Further analysis shows a function that checks for the original file name; if the file has been renamed, this is the result (Figure 4).
Although the code shows that XOR 0x21 is the operation and key to decrypt many items, emulation and debugging through Ghidra and Cutter run into issues with software interrupts and bad code blocks that act as anti-analysis methods.
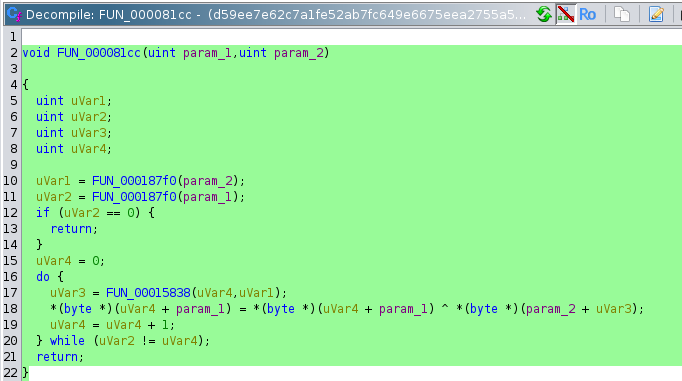
Of the commands that are able to be decrypted, here are the most prominent and what they relate to:
- KGDBOC: GDB over console, a way to debug using a single serial port
- BUSYBOX: A combination of multiple *nix commands in a single executable file
- TOYBOX: Alternative to BusyBox that provides similar functionality
- TCPLEGIT, UDPRAW, HANDSHAKE, SPOOF: Methods of DDOS attacks the malware can perform via C2 commands
- NETSTAT, IPTABLES: Enumeration of network information
- PGREP, FETCH: Methods of enumerating files and system information
[1] Botnet commands via https://cybersecuritynews.com/langflow-rce-vulnerability-exploited/
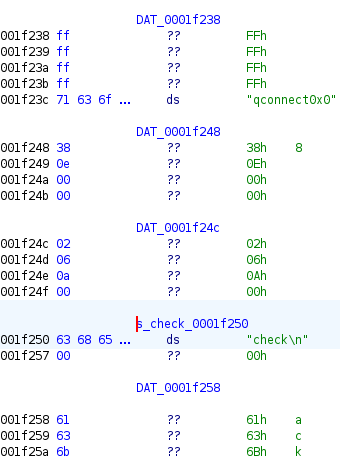
Rondo has the capability of sending the traffic as HTTP, TCP, and UDP, as well as masking itself as other programs; DayZ and was referenced in the code. There are also encoded strings in Han, Thai, Chinese, and Cyrillic, showing the potential for targets in these regions.
SonicWall Protections
To ensure SonicWall customers are protected against this threat, the following signature has been released:
RondoDox.ARM
IOCs
d59ee7e62c7a1fe52ab7fc649e6675eea2755a53d34f203aee0742a6261c1d7b
Share This Article

An Article By
An Article By
Security News
Security News
