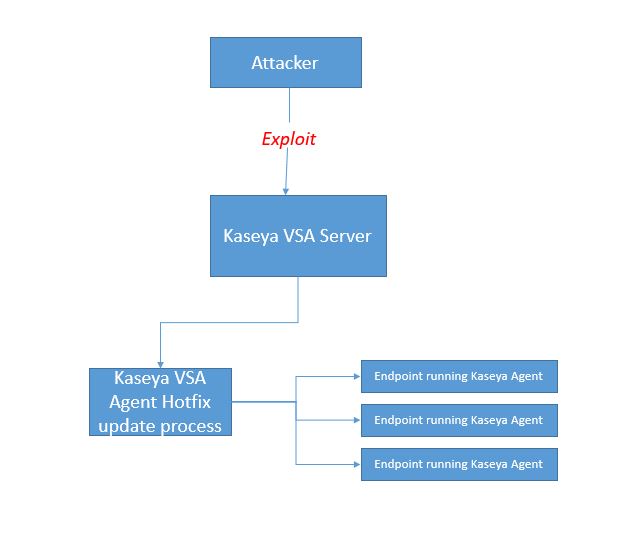
Kaseya VSA server exploitation and another supply chain ransomware attack

The SonicWall Capture Labs threat research team has analyzed the ransomware that is spreading using the exploitation of the Kaseya standalone on-premises VSA server and the subsequent supply-chain attacks.
The attack starts with exploitation of the Kaseya server. The ransomware dropper (agent.crt) encoded in base-64 format is uploaded to the Kaseya VSA server using the file upload functionality. In addition, the attacker uploads userFilterTableRpt.asp on the victim server which likely allows it to take advantage of additional vulnerabilities on the VSA server in order to issue the hotfix procedure. Once the server (standalone version) is exploited the attacker issues a hotfix update to the agent to transfer ransomware from the server to all the managed endpoint agents. This file is decoded/decrypted as agent.exe and executed. The sample is found to belong to the REvil/Sodinokibi ransomware family.
Infection Cycle:
The sample agent.exe is the ransomware dropper and its purpose is to drop the following files that are stored in its resource section and execute them. The location where the files are dropped in the system depends on the user's privilege access.
- mpsvc.dll (stored in the resource named 'MODLIS' )
- MsMpEng.exe (stored in the resource named 'SOFTIS' )
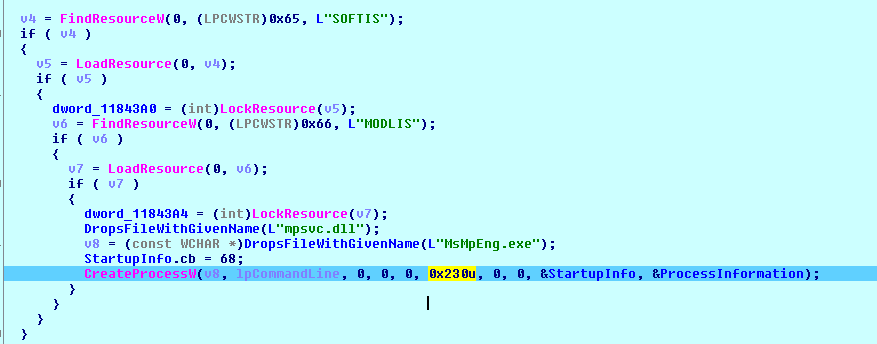
Fig-1: Dropper retreiving files from Resource
agent.exe executes 'MsMpEng.exe' using CreateProcess API as shown in the above image. MsMpEng.exe is a clean file related to Microsoft Security Essentials. It imports a custom dll named 'mpsvc.dll', which is the same name used by the threat actor for the other malicious DLL dropped by agent.exe. Due to the order of preference, while loading dll, malicious DLL present in the current folder is loaded into memory by MsMpEng.exe
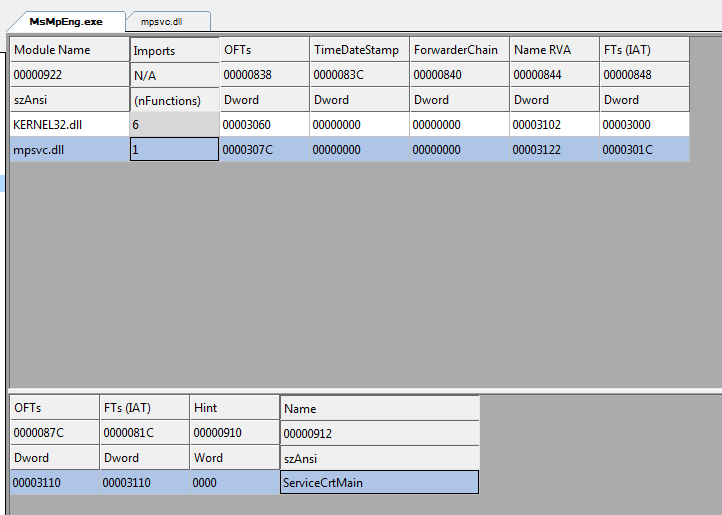
Fig-2:Import table of MsMpEng.exe
MsMpEng.exe loads the mpsvc.dll and executes the function 'ServiceCrtMain', which is exported by the dll, as shown below:
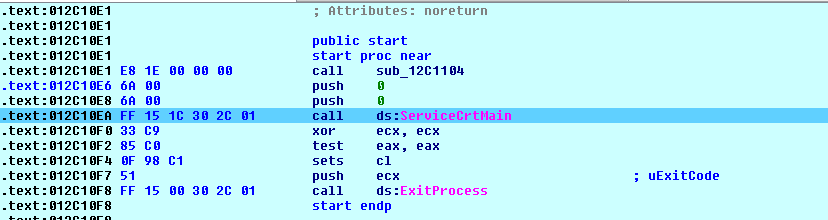
Fig-3:MsMpEng.exe calling ServiceCrtMain
Once the execution control is transferred to mpsvc.dll, it does the following:
- Creates a Mutex
- \BaseNamedObjects\422BE415-4098-BB75-3BD9-3E62EE8E8423
- Encrypts the files and changes the extension to a random name
- "filename.doc" is renamed to “filename.doc.6t0s1w”
- Adds a readme.txt ransom note in every folder, the name of readme text will be the same, as per appended extension, to every encrypted file
- “6t0s1w-readme.txt”
- There is a configuration file embedded in the DLL, which contains:
- Folders that are excluded during the ransomware encryption routine
- program files, appdata, mozilla, application data, google, windows.old, programdata, system volume information, program files (x86), boot, tor browser, windows, intel, perflogs, msocache
- Files that are excluded during the ransomware encryption process:
- ntldr, thumbs.db, bootsect.bak, autorun.inf, ntuser.dat.log, iconcache.db, bootfont.bin, ntuser.dat, ntuser.ini, desktop.ini
- File extensions that are excluded from the encryption process
- ps1, ldf, lock, theme, msi, sys, wpx, cpl, adv, msc, scr, bat, key, ico, dll, hta, deskthemepack, nomedia, msu, rtp, msp, idx, ani, 386, diagcfg, bin, mod, ics, com, hlp, spl, nls, cab, exe, diagpkg, icl, ocx, rom, prf, themepack, msstyles, lnk, icns, mpa, drv, cur, diagcab, cmd, shs
- Terminates the following process if running:
- encsvc, powerpnt, ocssd, steam, isqlplussvc, outlook, sql, ocomm, agntsvc, mspub, onenote, winword, thebat, excel, mydesktopqos, ocautoupds, thunderbird, synctime, infopath, mydesktopservice, firefox, oracle, sqbcoreservice, dbeng50, tbirdconfig, msaccess, visio, dbsnmp, wordpad, xfssvccon
- The following services are stopped if running:
- veeam, memtas, sql, backup, vss, sophos, svc$, mepocs
- Folders that are excluded during the ransomware encryption routine
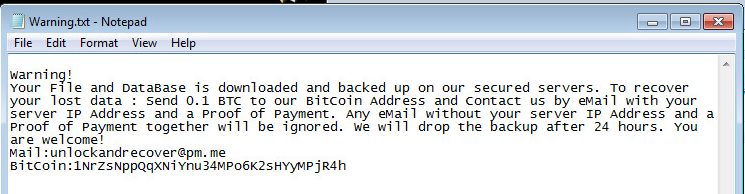
On completion of the encryption routine, the following ransom note is displayed to the victim.
If the sample has administrator privilege, then it encrypts the MasterBootRecord (MBR).
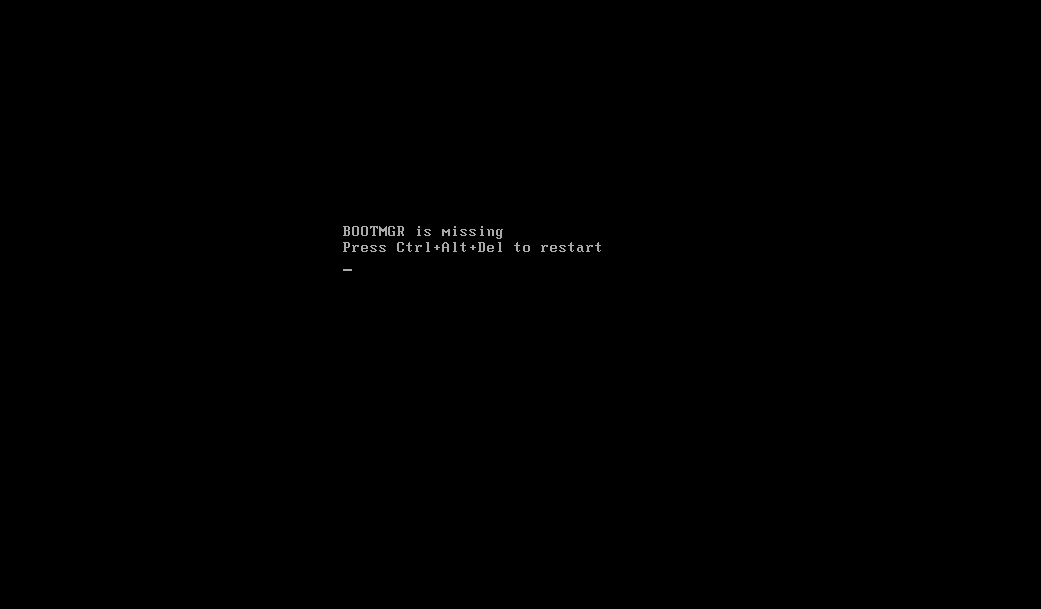
Fig-5: System with infected MBR
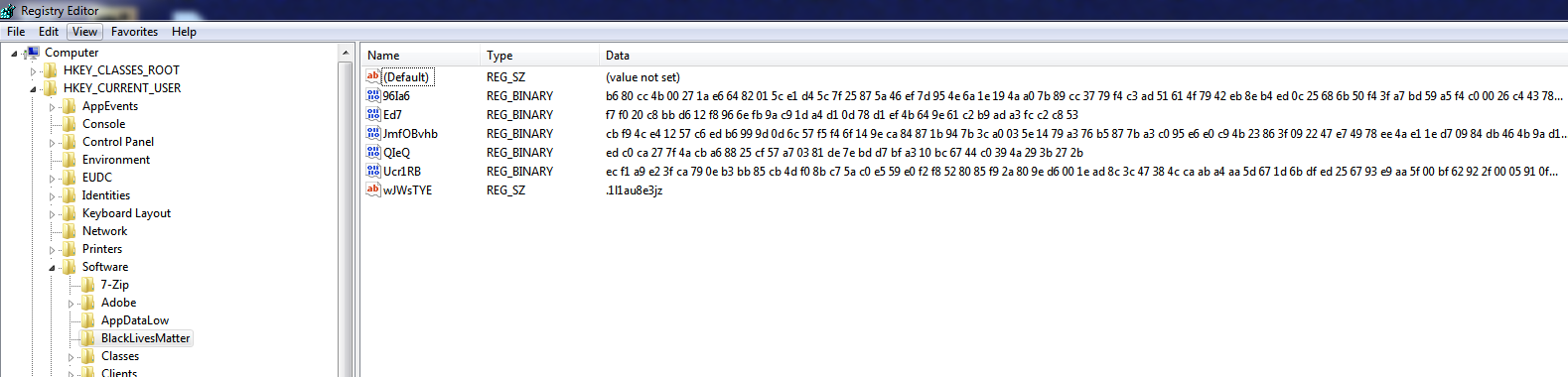
The ransomware will store all generated public / private keys and random file extension ( appended to encrypted files ) during its operation under “SOFTWARE\BlackLivesMatter” reg key. This crucial information can be used later by malware .
Fig-6: Registry Key Created - Software/BlackLivesMatter
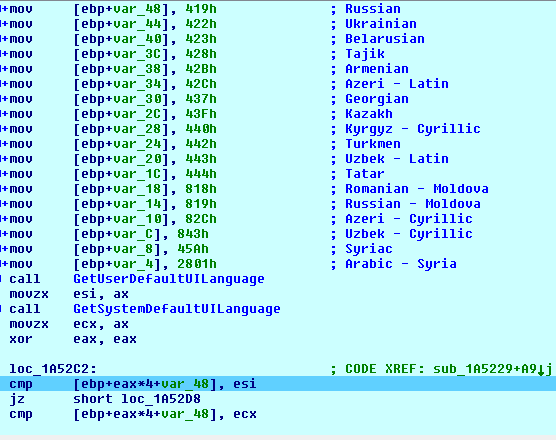
The malware checks the default set language of the user and system using GetUserDefaultUILanguage and GetSystemDefaultUILanguage.
If it matches the listed language then it stops further execution.
Fig-7: Language check
It creates mutex to execute only one instance using createMutexW API.
If we execute more than one instance of malware then it will show error as "ERR0R D0UBLE RUN!"
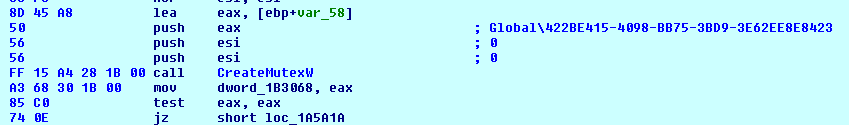
Fig-8: Mutex Created
The files are encrypted using the Salsa20 algorithm.
Fig-9: Salsa20 algorithm
This threat can be detected via the following methods:
- GAV: MalAgent.VSA (Trojan)
- GAV: Filecoder.N (Trojan)
- IPS: Kaseya VSA Server userFilterTableRpt Request
This threat can also be detected by SonicWall Capture ATP with Real-Time Deep Memory Inspection (RTDMI) and the Capture Client endpoint solutions.
SonicWall Capture Labs continues to monitor this threat and will provide further information as it becomes available.
Indicators Of Compromise (IOC):
Files:
- 561cffbaba71a6e8cc1cdceda990ead4 (agent.exe)
- a47cf00aedf769d60d58bfe00c0b5421 (mpsvc.dll)
- 95f0a946cd6881dd5953e6db4dfb0cb9 (agent.crt)
Registry:
- HKLM\BlackLivesMatter\
References:
Share This Article

An Article By
An Article By
Security News
Security News