Zero Trust Network Access (ZTNA)
What is ZTNA (Zero-Trust Network Access)?
Zero-Trust Network Access (ZTNA) is a cybersecurity framework that enforces strict identity verification for every user and device attempting to access resources on a private network, regardless of whether the connection originates from inside or outside the network perimeter.
Unlike traditional VPNs or perimeter-based security models that implicitly trust users within the network, ZTNA operates on a “never trust, always verify” principle. ZTNA was born out of the need to address modern security challenges driven by remote work, cloud adoption, and increasingly sophisticated threats. It is particularly important today as organizations face growing risks from lateral movement attacks, insider threats, and the complexities of hybrid IT environments.
Key Features of ZTNA
Identity-Centric Access ControlEvery access request is authenticated based on the user’s identity, role, device posture, and location before access is granted.
Micro-SegmentationLimits access to only the specific resources a user needs, reducing the attack surface and containing potential breaches.
Application-Level AccessUnlike VPNs, ZTNA connects users to individual applications, not the entire network, minimizing exposure.
Continuous MonitoringZTNA solutions constantly evaluate user behavior, device health, and session risk for adaptive access control.
Cloud-Native ArchitectureMany ZTNA solutions are built to support multi-cloud and hybrid environments, enabling scalable and flexible deployments.
Benefits and Use Cases
ZTNA delivers significant security advantages by eliminating implicit trust within networks and providing granular, identity-based access to applications. One of the major benefits isreduced risk of lateral movement; users and devices can only access the resources they’re explicitly authorized to use, which helps prevent attackers from traversing the network if a breach occurs.
ZTNA is highly effective insupporting secure remote work, especially for organizations with distributed teams and contractors accessing corporate applications.
It's also ideal forenforcing compliance in regulated industrieslike finance, healthcare, and government by providing robust access logging and visibility. In addition, it enables organizations to transition smoothly to cloud-based infrastructures by securing application access across hybrid environments without relying on legacy VPNs.
ZTNA addresses challenges posed by bring-your-own-device (BYOD) policies and unmanaged devices by validating device posture before granting access. As such, ZTNA has become a critical component of modern cybersecurity strategies, protecting both on-premises and cloud resources from unauthorized access and potential data breaches.
Challenges and Considerations
Implementing ZTNA can present several challenges, particularly during the transition from legacy perimeter-based models. Organizations may face technical complexities when integrating ZTNA with existing infrastructure or identity providers. Ensuring consistent policy enforcement across diverse environments can also be difficult without the right tools.
Additionally, while ZTNA solutions typically improve security, there may be concerns about latency or access delays if not properly configured. Budget constraints and skill gaps may further hinder adoption for some organizations.
However, ZTNA plays a pivotal role in overcoming these hurdles. By enabling centralized policy management and leveraging modern authentication standards, ZTNA helps streamline secure access while reducing administrative overhead. Many vendors now offer cloud-based ZTNA solutions that lower deployment barriers and minimize operational costs.
Moreover, the visibility and control gained through ZTNA contribute to a stronger security posture over time. Despite the learning curve, the long-term value and risk reduction make ZTNA a worthwhile investment for organizations prioritizing secure digital transformation.
ZTNA Industry Trends
ZTNA adoption is accelerating as organizations shift toward hybrid work models and decentralized infrastructures. One key trend is the convergence of ZTNA withSecure Access Service Edge (SASE)frameworks, which integrate networking and security functions into a unified cloud-native service. This trend reflects the industry’s move toward simplifying security management while enhancing protection across cloud and edge environments.
Another emerging development is the integration of artificial intelligence and machine learning into ZTNA solutions, enabling real-time threat detection and dynamic access decisions. Vendors are also enhancing endpoint posture checks and behavioral analytics to further reduce risk. The rise of API-driven infrastructures and containerized workloads is driving demand for ZTNA solutions that can protect not just users, but also machine-to-machine communication.
Regulatory pressures and compliance requirements are also prompting enterprises to implement ZTNA to meet data protection standards like HIPAA, GDPR, and PCI DSS. Looking ahead, ZTNA is expected to become a foundational element of zero-trust architectures, working in tandem with identity governance, endpoint detection, and threat intelligence platforms to provide comprehensive and adaptive security.
ZTNA and SonicWall’s Cloud Secure Edge (CSE)
SonicWall offers comprehensive, secure access to on-prem, hybrid, and multi-cloud infrastructure and applications – from anywhere. The ZNTA discussed below is part of ourCloud Secure Edge (CSE)- Secure Private Access (SPA) license.
Why You Need SonicWall’s ZTNA
Traditional network-centric access solutions like VPNs present limitations and challenges for organizations of all sizes, including pressing security risks, high costs, complex management, and scalability issues. Organizations are increasingly taking advantage of Zero Trust Network Access (ZTNA) to enable employees and third parties to access on-premises, hybrid, and multi-cloud applications and infrastructure from anywhere.
SonicWall’s ZTNA offering, Cloud Secure Edge, works consistently, regardless of worker location, enabling least-privilege access to hosted applications and infrastructure based on real-time contextual factors including user and device trust scoring and resource sensitivity. Best of all, it is easily managed and provides a superior user experience.
How SonicWall’s CSE Works
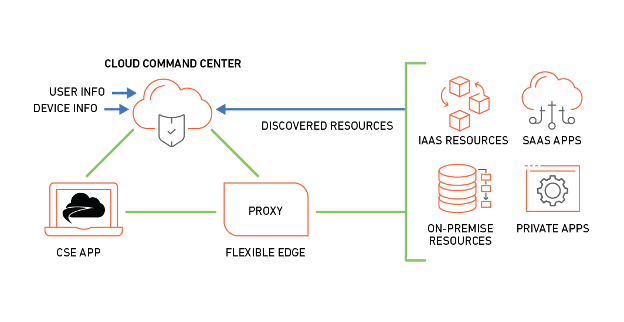
CSE’s ZTNA consists of three main components:
Cloud Command Center: A trust level is calculated based on the user ID, device ID, and device security posture then evaluated against policy, and if approved, short-lived certs are issued to permit access, which is now a direct path to the approved application or resource.
Flexible Edge: Access requests are received by the Flexible Edge, then fully vetted by the Cloud Command Center (which is tied into your IdP as well as your existing Endpoint Detection & Response (EDR) and Unified Endpoint Management (UEM), if desired).
CSE App: Since CSE employs continuous authorization, should the user’s trust score drop to an unacceptable level, existing access sessions are suspended. They can go to the CSE app, see what adversely affected their Trust Level and self-remediate.
How Cloud Secure Edge – Secure Private Access (CSE-SPA) Works
The CSE Advantage
Cloud Secure Edge is the best choice for cloud-forward organizations providing the modern workforce easy, secure access to on-premises, hybrid, and multi-cloud applications and infrastructure from anywhere. Our solution offers numerous advantages over legacy products, including:
Easy to deploy, manage, and use.
Cloud-managed centralized configuration platform (Cloud Command Center).
CSE’s Flexible Edge deployment model can be deployed in seconds locally next to the resource (we call this “Private Edge”), or with a lightweight Connector that interfaces with cloud-based PoPs (the “Global Edge”).
Runs alongside existing VPN if desired, allowing low-risk incremental deployment by application or user group, retaining safety net of existing legacy services.
CSE works seamlessly with IaaS and PaaS environments providing one-click access to corporate applications as well as resources like SSH/RDP servers, Kubernetes, and databases. Least privilege access allows differentiated access for employees and third parties alike that is a snap to deploy, administer, and audit.
Seamlessly integrates with existing Identity Provider (IdP), Endpoint Detection and Response (EDR), and Unified Endpoint Management (UEM) investments, not to mention automation integration with DevOps tooling (think “Zero Trust as code”).
Consistent, simple user experience that is always the same no matter where they happen to be.
Unmatched security.
Least-privilege access ensures workers only have access to the resources they need to do their jobs.
Fine-grained controls use CSE’s trust score-powered policy engine, enabling continuous authorization based on user and device trust, device security posture, and resource sensitivity. CSE aligns the risk of the request with the sensitivity of the resource, revoking access mid-session if warranted.
A single policy governs users, whether on-campus or remote, removing risk of coverage gaps.
Visibility driven controls.
Interactive dashboards show zero trust achievement.
Deep visibility into user, device, app, and service activity, permitting superior control and accountability.
Automatic Discover & Publish capabilities make it easy to know what’s available to be published.
Find out more about SonicWalls’s Cloud Secure Edge.