NightSpire Ransomware Encrypts Cloud-Stored OneDrive Files

This week, the SonicWall Capture Labs threat research team analyzed a ransomware variant known as NightSpire. While its behavior is typical of most ransomware—encrypting user files and providing recovery instructions via a text file—what makes NightSpire especially concerning is its rapid growth. First surfacing in March of this year, the malware now claims to have infected more than 45 organizations globally.
Infection Cycle
The malware arrives as a portable executable written in Go.
Once executed, it immediately opens a console window using conhost.exe and begins listing all system directories and files as it searches for content to encrypt.
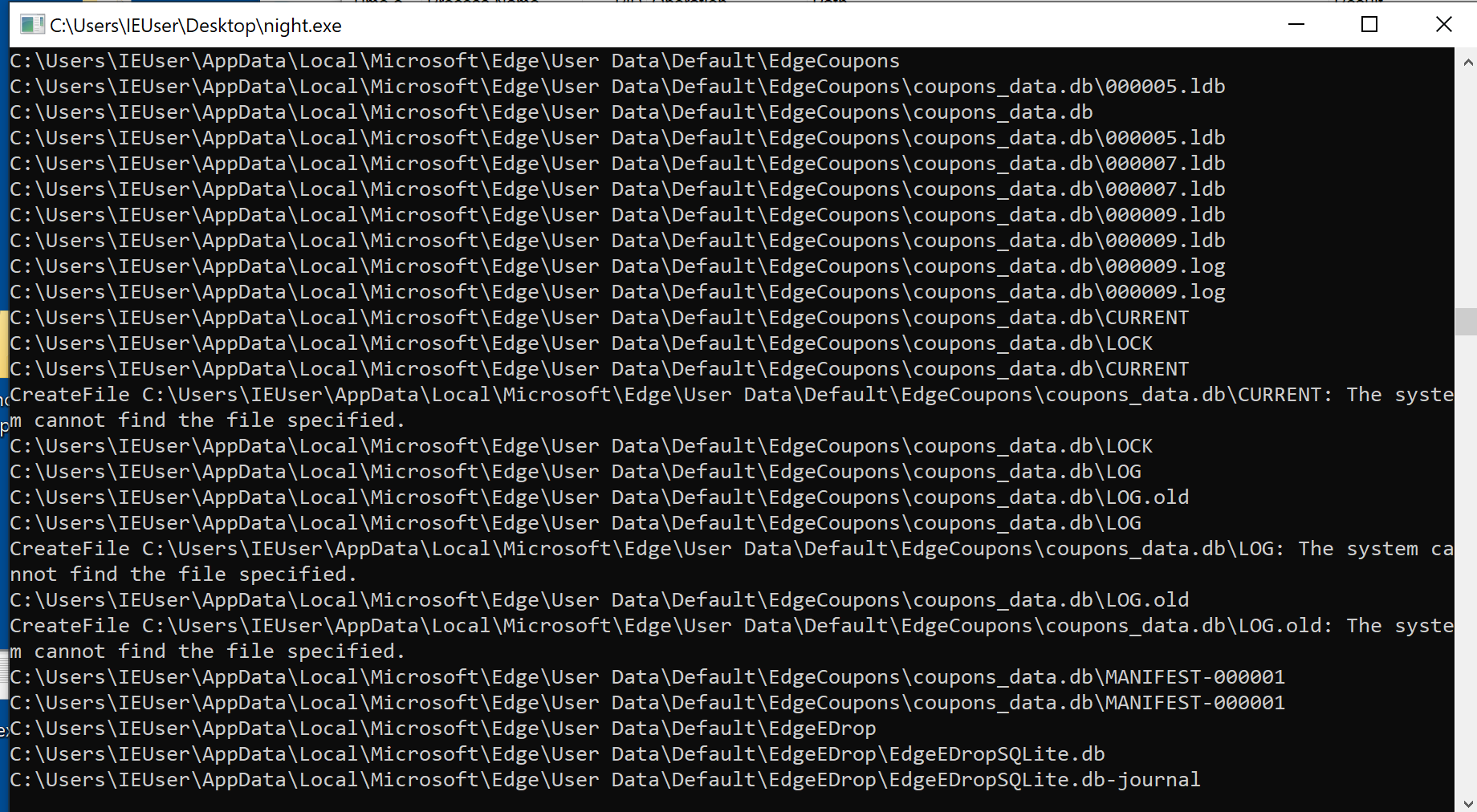
Encrypted files are appended with the .nspire file extension.
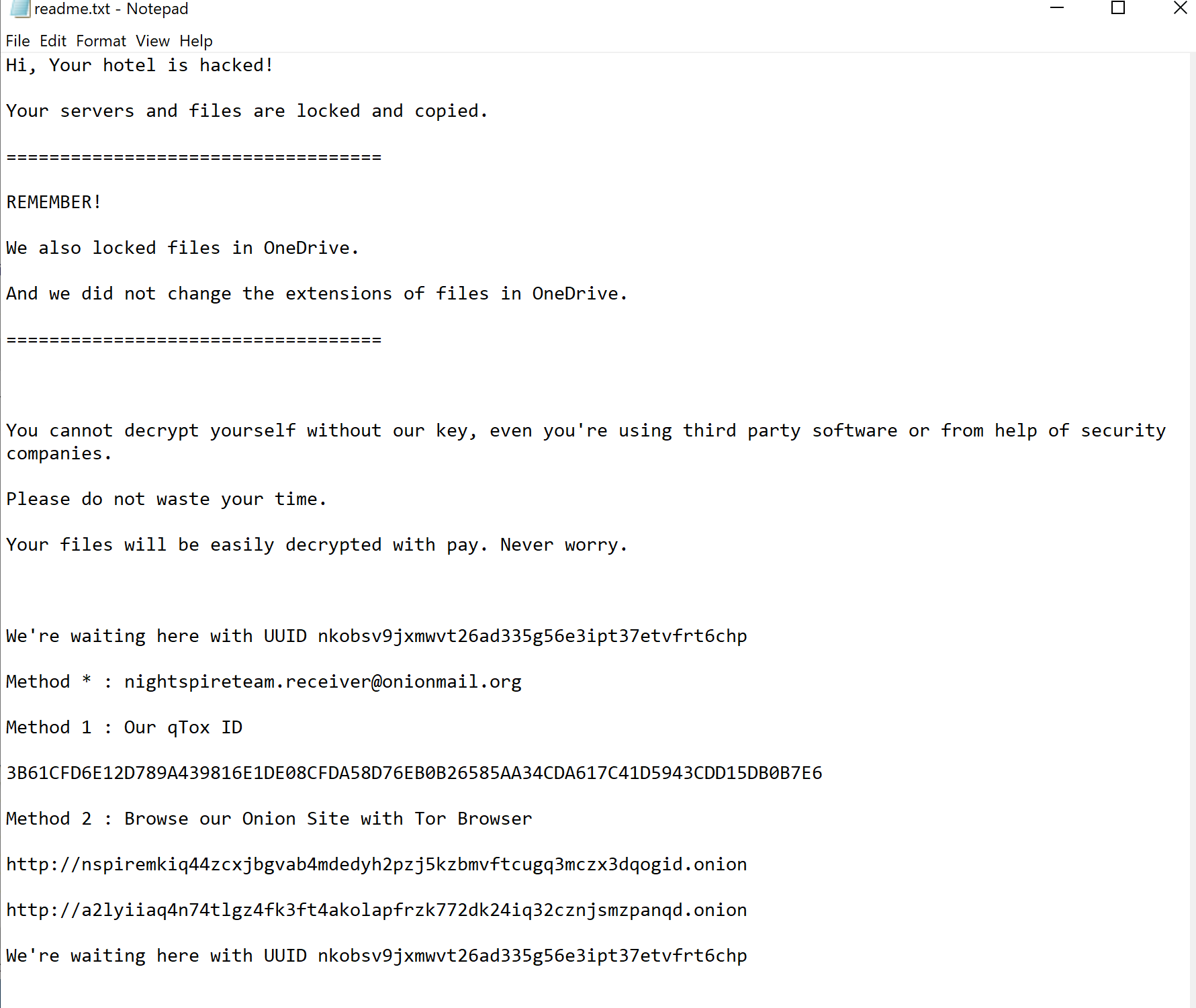
A file named readme.txt is created in every directory containing encrypted files. This ransom note includes instructions on how to contact the cybercriminals and emphasizes that even files stored on OneDrive have been compromised.
The threat actors host a blog on the Tor network that functions as an announcement page, featuring updates from the ransomware group.
A section of the blog lists all known victims, with the most recent being a facility services organization in Spain.
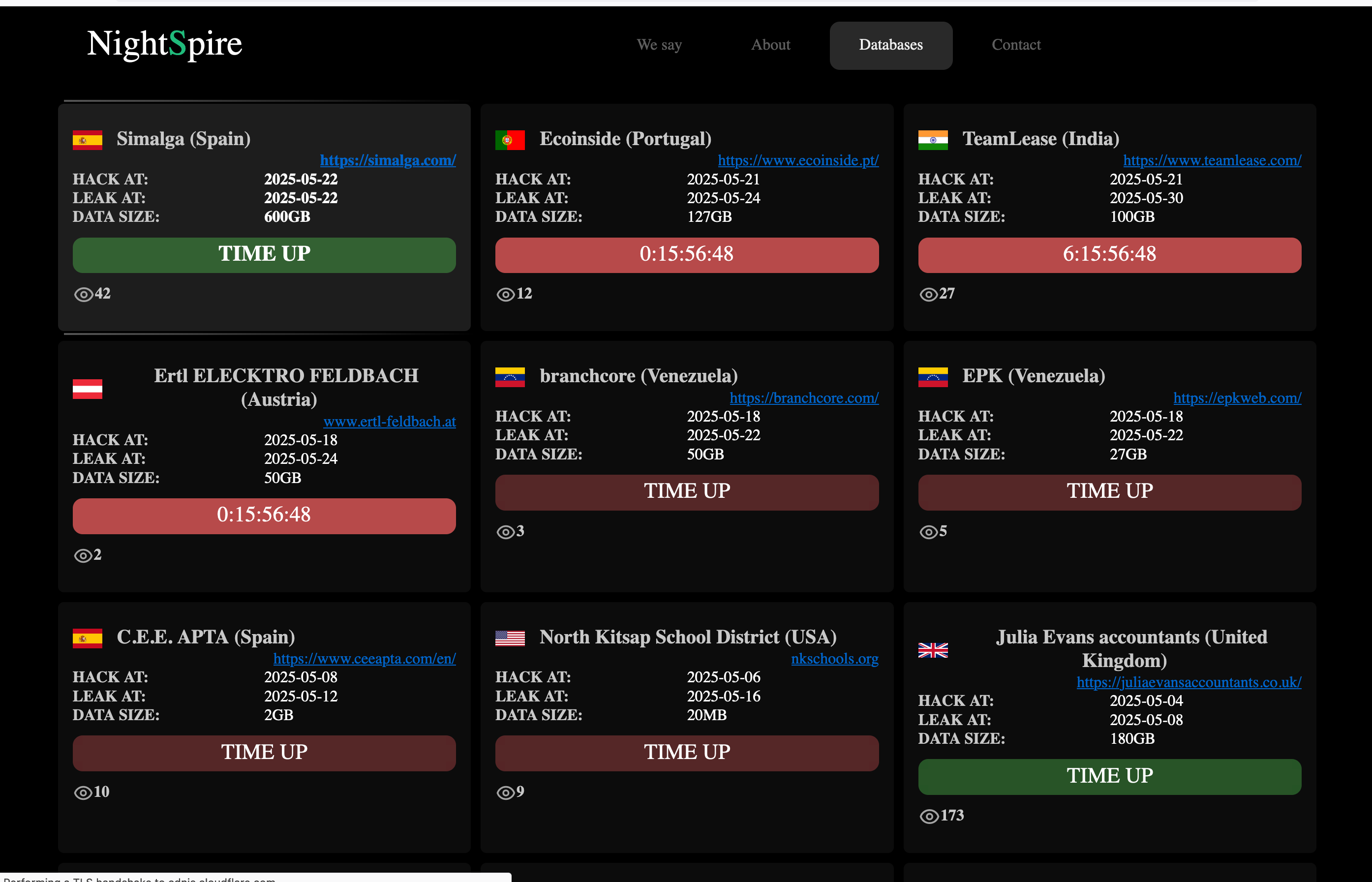
Companies that refuse to negotiate or pay the ransom find their stolen data published in this section of the portal. The site includes view tracking and a preview of the leaked data, along with instructions for purchasing it.
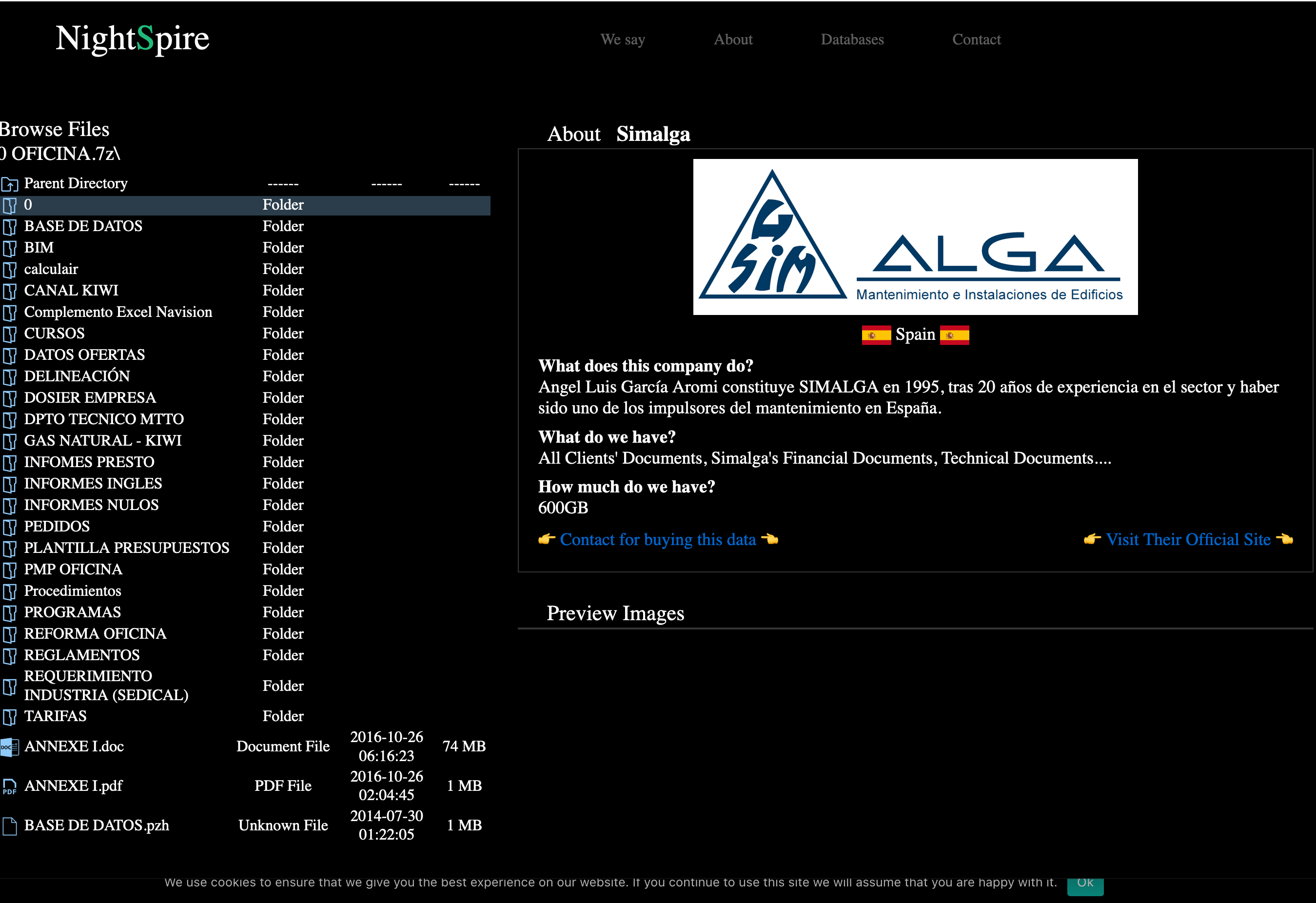
As of now, the group appears to operate privately, according to their “About” page. However, given the pace of their growth, it would not be surprising to later discover the existence of affiliates operating internationally.

SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: NightSpire.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI, as well as the Capture Client endpoint protection solutions.
Share This Article

An Article By
An Article By
Security News
Security News
