Emotet Malware spreading via IRS theme based spam email

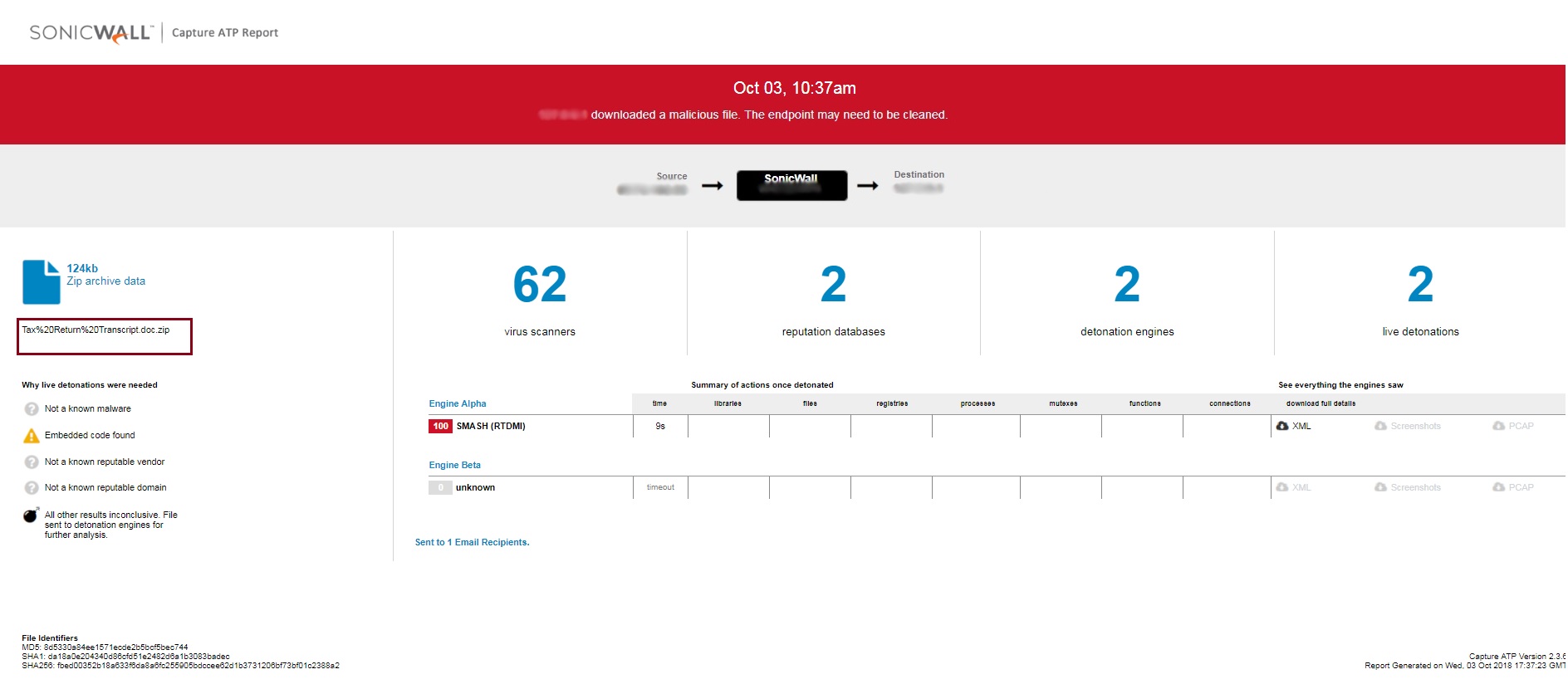
SonicWall RTDMI engine detected an archive attachment consisting of malicious word documents inside of spam email appearing to be from the IRS department. Similar spams were observed during the month of July this year as well. But at that time the spam email contains a malicious word document as an attachment whereas this time the attachment is an archive with malicious word document inside the archive. Information about these fresh attacks was not available in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs.

Fig-1: Virustotal results of the malicious file
The email attachment is named as one of the following:
- Tax Return Transcript.doc.zip
- Wage and Income Transcript.doc.zip
- Verification of Non-filing Letter.doc.zip
Upon extracting the archive, one can observe two Microsoft Word documents which are same but with different names. One file name will be in IRS__.doc format and another file will have the name of the archive as shown in the below image.
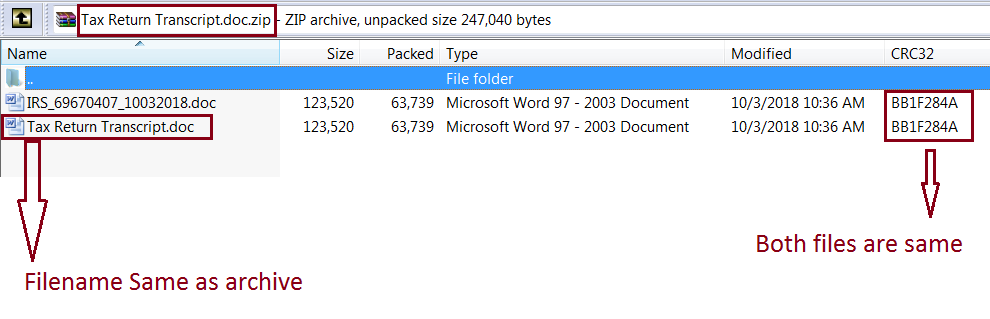
Fig-2: Archive contents
On opening the document, it will ask the user to Enable Editing and Enable content, in order to execute the macro code which downloads the payload by launching PowerShell command.
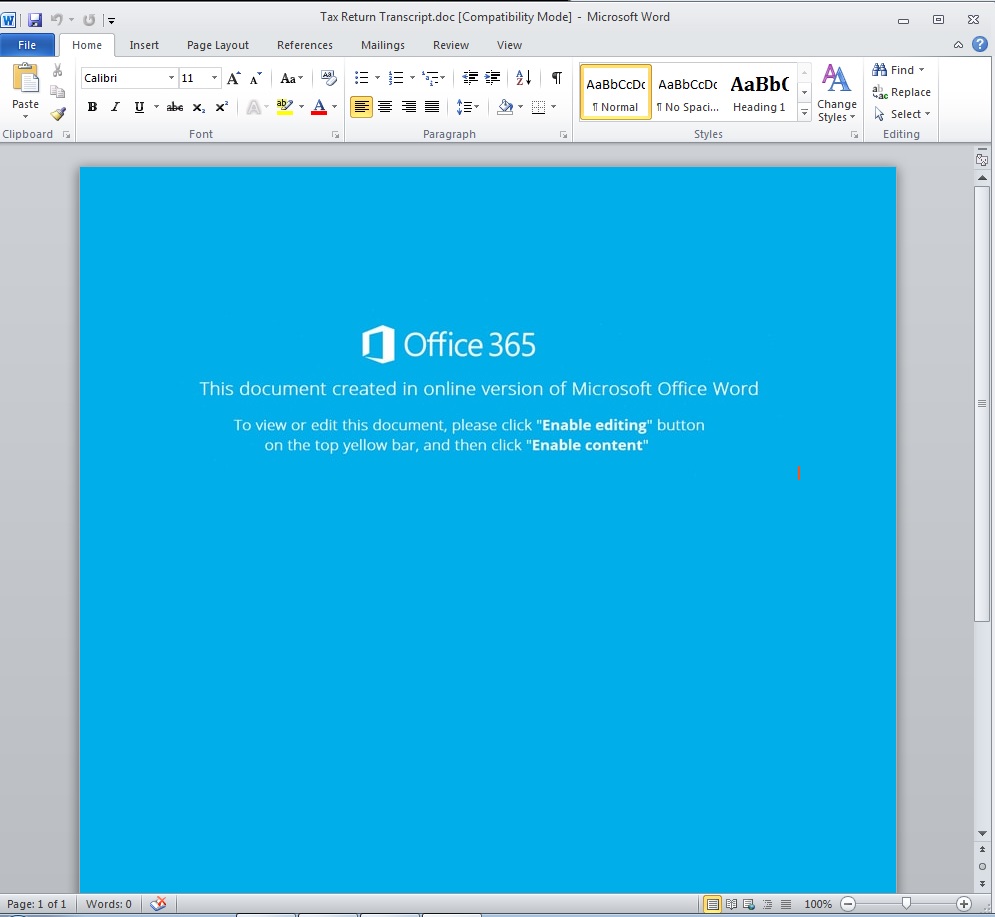
Fig-3: Word document
The payload belonging to Emotet family is being delivered at the time of analysis.
Indicators of Compromise (IOC):
- fbed00352b18a633f6da8a6fc255905bdccee62d1b3731206bf73bf01c2388a2 : Archive
- 149da2a8074796bc5f3c9dcfe139082df1b60d5ac5e18095a10d5b5359664157 : Word document
- hxxp://albuthi.com/RUBhR7
- hxxp://abbasiwelfaretrust.org/1yTfF
- hxxp://aadityainc.com/jadEM
- hxxp://www.firststpauls.org/rU4L9
- hxxp://www.galaxyla.com/pXXRHEQK
- 23974dc955970ae56fd21b938ed1937fe52790313eee12ed8d30203e8d9efb58 : Emotet Malware
Hashes of similar malicious attachments:
- 2b572ea00fced178b6c8c516e4569725cb4eea95f6d1128f22266d1552e66440
- 76b252a5a5416aedcbacd81f2b4a93ba7be4d2ce1c2f3cdfeb556cd37dd47823
- 8bb0262c39e986298e5be134e3b0ebf1b4044b21002f844bb05b7dbe4d93b8f7
- f6dab997b23045242e2f28fbc076efbd48ed2c778b13a7d7cf3c9a15f2b4721b
Capture ATP report for this file:
Share This Article

An Article By
An Article By
Security News
Security News