Critical RCE Vulnerabilities in Commvault: CVE-2025-57791 & CVE-2025-57790

Overview
The SonicWall Capture Labs threat research team became aware of a critical chain of remote code execution (RCE) vulnerabilities in Commvault CommServe. Two chains of vulnerabilities, including four separate CVEs with different severity levels, when combined, form grounds for exploitability in Commvault Cloud. CVE-2025-57791 and CVE-2025-57790, being argument injection and path traversal vulnerabilities in CommServe,is respectively, allow remote attackers to inject or manipulate command-line arguments passed to internal components, potentially compromising the entire network access control infrastructure. Though each has a low severity score, when chained together, both CVEs create a significant threat to businesses. Commvault’s enterprise backup solutions are deployed across major corporations, MSPs, and critical infrastructure, making these vulnerabilities particularly dangerous for large-scale attacks.
Commvault includes its own command interface, QCommands, which is a special set of CLIs that can perform almost any administrative task available in the CommCell Console, from listing jobs to running backups and restores. Versions before 11.36.60 are affected by this flaw. The vulnerability resides in the qlogin method, where insufficient input validation leads to an initial authentication bypass. Any process that can influence arguments or parameters passed to qlogin, whether via CLI or an API call that wraps it, can potentially control authentication flow. Exploitation requires no authentication, making immediate patching critical. The patches cover versions 11.32.0 to 11.32.101 and versions 11.36.0 to 11.36.59 of Commvault for Linux and Windows environments and take them to versions 11.32.102 and 11.36.60, respectively. A valid proof-of-concept exploit has appeared in publicly accessible articles.
Technical Overview
The vulnerability stems from how Commvault handles its special set of QCommands for authentication and other purposes. One such command, qlogin, handles authentication. It accepts a username and password, and if the credentials are valid, it generates an API token. This function is insecure due to insufficient input validation, leading to successful exploitation, creating a valid application programming interface (API) token for a user session for a low-privileged account. These commands can be invoked by local CLI, internal QAPI, or authenticated REST API.
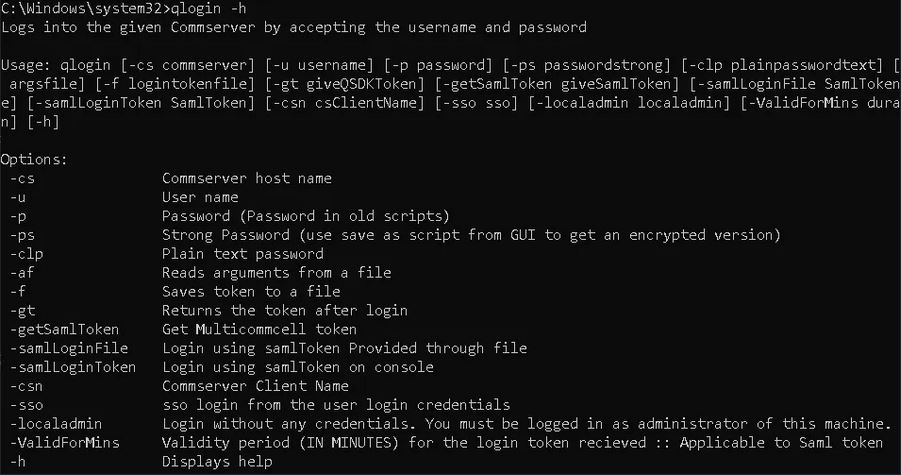
An attacker can embed high-value QCommands within specially crafted API requests. CVE-2025-57791 enables unauthenticated remote code execution by injecting arguments into the qlogin command, bypassing authentication mechanisms. The main authentication endpoint mapped to /commandcenter/api/Login is implemented with a Java-based frontend and a .NET API backend. Typically, a login request requires basic credentials such as username and password to prove authentication, but in Commvault, due to a function named CheckCredentialReq, an attacker can manipulate the Commvault authentication process since this function defines support for 40 properties apart from username and password.
Triggering the Vulnerability
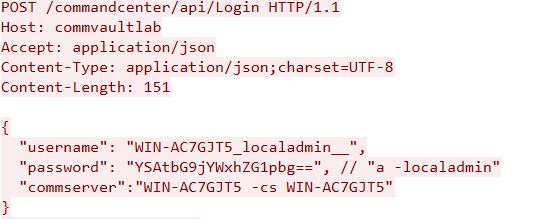
To trigger this vulnerability, an attacker needs to:
- Have network access to the Commvault CommServe platforms.
- Retrieve a valid hostname of the target instance via /commandcenter/publicLink.do.

- Pass the correct username in the login request so GetQSDKUserInfo succeeds with the localadmin token.
- Include the localadmin QCommand option in the request, which issues a valid authentication token without requiring any credentials when run as SYSTEM.
In a typical attack scenario, the adversary sends a specially crafted POST request to the vulnerable API route on CommServe. The target endpoint is /commandcenter/api/Login. The attacker’s request includes a malicious payload containing embedded system commands designed to inject arguments or execute scripts.
Exploitation
Following successful exploitation, attackers typically gain shell access or execute arbitrary commands on the vulnerable Commvault Cloud platforms when chained with CVE-2025-57790. The watchTowr Labs researchers’ exploit demonstrates a multi-step attack chain:
- Authentication bypass to generate a valid API token for the localadmin user.
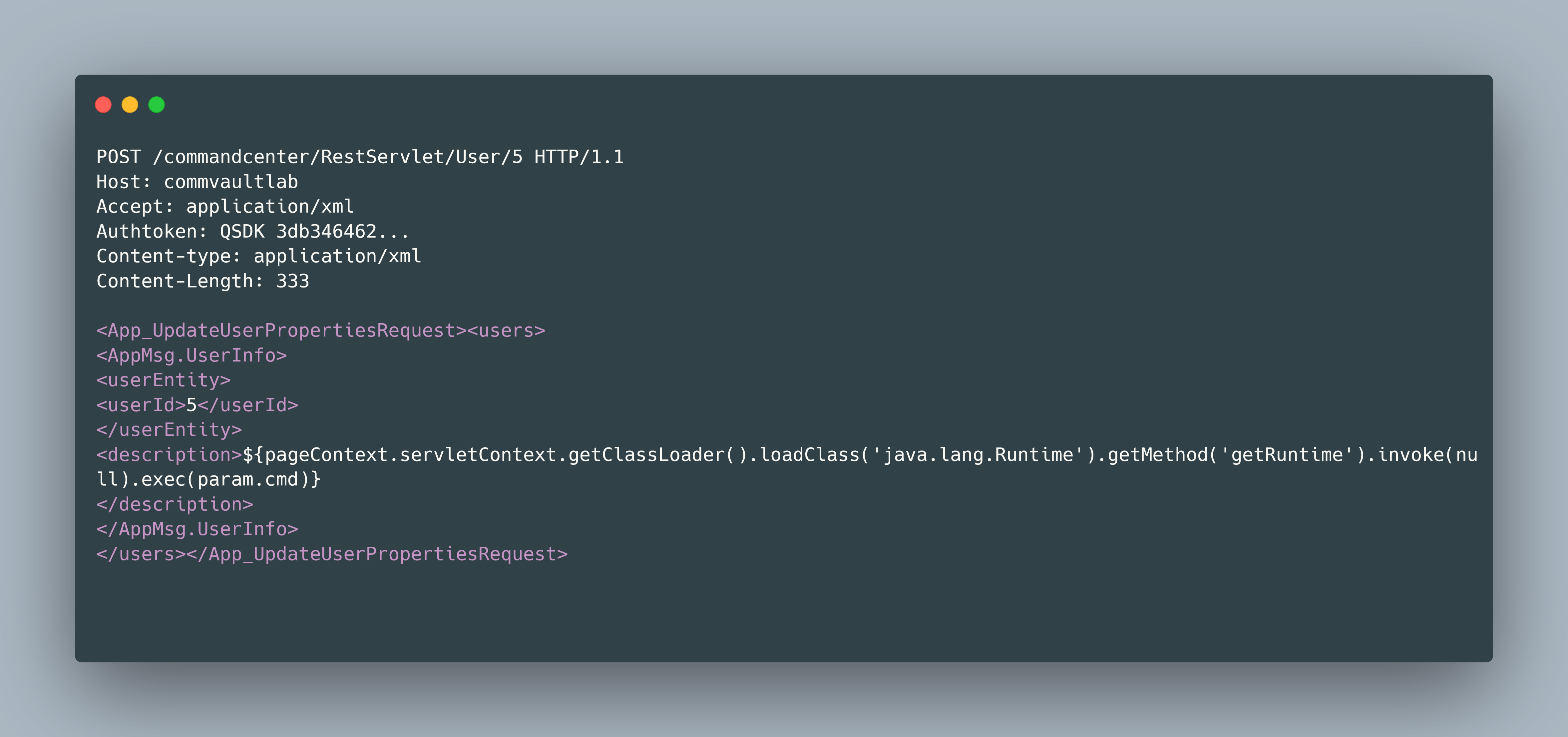
- Absolute path traversal in QCommand handling, allowing a JSP web shell to be written directly into the webroot for remote code execution.
- A malicious request to achieve RCE is shown in Figure 4.
SonicWall Protections
To ensure SonicWall customers are prepared for exploitation attempts related to this vulnerability, the following signatures have been released:
- IPS: 21399 Commvault QCommand Arbitrary File Write
- IPS: 21400 Commvault QCommand Path Traversal
Remediation Recommendations
Users of Commvault Cloud instances are strongly advised to upgrade to the latest patched version as outlined in the official vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.

