What you should know about EternalBlue exploit and WannaCry Ransomware

Since last weekend, the outbreak of WannaCry ransomeware has became the headline of the security news. This worm attack has integrated one of the most effective way of spreading - a 0day exploit on default windows service; And one of the most destructive yet profitable kind of payload: ransomware. SonicWall Threat Research Team has already released several SonicAlerts analyzing the exploits and ransomware (Shadowbroker releases alleged NSA EquationGroup Exploit Code Dump and WannaCrypt.RSM (high risk alert)). In this article, we will continue share more stories, insights and lessons learnt from this security incident.
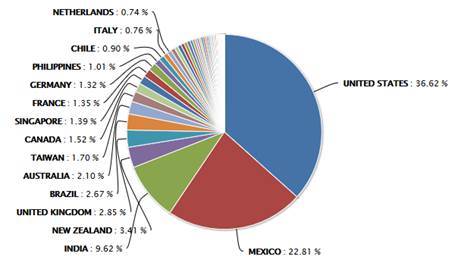
The Data from SonicWall:
Since the "ShadowBroker"'s initial NSA 0day leak, numerous exploits of MS17-010 have already in-the-wild. As of May 18 2017, SonicWall has tracked and intercepted over 800,000 attacks from 60 countries. The Top 3 are: US: 293306, Mexico: 3119, and Indian: 7035.

Details about the WannaCry ransomware:
The vulnerability used in "EternalBlue" (MS17-010) is triggered by a logical error on calculating the buffer boundary in the srv.sys. The attack surface is on Windows SMB service, via TCP port 445. Most of the ISPs has blocked this port from external access. However, it spreads fast in a local network filled with unpatched hosts.
Comparing to the 0-day exploit, the ransomware is rather immature. On the following aspects:
- The payment: Bitcoin is a major ransom payment channel nowadays, thanks to its anonymity, cross-border payment and wider buying channels. In the "WannaCry", the payment is implemented poorly: It hardcoded 3 Bitcoin wallet addresses in the code. As Bitcoin's transaction records are transparent, the ransomware author will expose the amount of money he has received. And it's also easier to track him when he is moving the money out of the wallets. Moreover, he hasn't design an automatic way to determine if someone has paid - victims can only contact the author to do so. This further increased his possibility to be unveiled. If the ransomware generates new Bitcoin wallets for each victim, both issues could be solved and the author will be a lot harder to trace.
- The file encryption: The WannaCry uses RSA + AES encryption, which is considered irreversible without a proper key. However, the encryption implementation is flawed, and the encrypted files are possible to be recovered. WannaCry uses the malware's common practice to encrypt the files on user's Desktop: overwrite the original file's disk space with the encrypted file. However, for the files under non-system partition, it simply moves them to the %TMP% folder, and only uses standard deleting. So the files have a high chance to be recovered.
- The kill switch: A strange domain name (www.ifferfsodp9ifjaposdfjhgosurijfaewrwergwea.com) has become the kill switch for WannaCry, the infection slows down after the domain name is registered. Link
This "kill switch" is likely to be part of its anti-sandbox approach. To avoid being discovered by dynamic analysis, some malwares will first identify whether the running environment is in a sandbox (if so, it won't commit malicious behaviors). To better analyze malwares with a dead C&C server, sandboxes sometimes fake responses from server side to let the sample expose more behaviors. WannaCry exploits this feature to identify the sandbox environment - if it received a response from a domain name that shouldn't exist, then stop working. And ironically, this made itself a kill switch.
Development of the story:
Windows XP Users might be able to recover the encrypted files due to another vulnerability on the Windows XP crypto library : The CryptDestroyKey and CryptReleaseContext functions does not erase the prime numbers from memory before freeing the associated memory. Which allows recovering the RSA key pair and then the encrypted files. The tool "WannaKey" is available on GitHub: Link
Microsoft blame on NSA for leaking their 0-days: Link
North Korea hackers might have involved in the incident: Link
Lessons from this incident:
Although the worm exploits a new vulnerability, its spreading mechanism has many similarities to the old "Blaster" (MS04-011) and "Confiker" (MS08-067). And the worm still caused heavy damage on today's Internet, infected companies, institutions and government agencies.
Here are some possible factors for making you a "WannaCry" victim, which may exist on some people for a decade:
- Your organization does not install a firewall with proper rules/file filters. You don't have a updated anti-virus software with active protection.
- You don't keep Windows updated.
- You don't backup important files.
- You use Windows XP.
(Although Microsoft has issued emergency patch for the discontinued Windows XP, it was too late for most Windows XP victims)
SonicWall have created the a series of signatures to protect our customers from the the leaked NSA exploits:
- 12700 Windows SMB Remote Code Execution (MS17-010)
- 12792 Windows SMB Remote Code Execution (MS17-010)
- 12794 Windows SMB Invalid Trans Session Setup Request
- 12795 EternalBlue MS17-010 Echo Response
- 12796 Suspicious CIFS Traffic 13
- 12801 Windows SMB Remote Code Execution (MS17-010)
- 12800 Windows SMB Remote Code Execution (MS17-010)
- 9732 WannaCrypt.RSM.ar7
- 9734 WannaCrypt.RSM.ar6
- 9735 WannaCrypt.RSM.ar5
- 9736 WannaCrypt.RSM.ar4
- 9739 WannaCrypt.RSM.ar3
- 9741 WannaCrypt.RSM.ar2
- 9742 WannaCrypt.RSM.ar1
- 9744 WannaCrypt.RSM.7z3
- 9745 WannaCrypt.RSM.7z2
- 9747 WannaCrypt.RSM.7z1
- 12293 HydraCrypt.C
- 16519 WannaCrypt.RSM
- 18723 WannaCrypt.RSM_2
- 18771 WannaCrypt.RSM_3
- 18789 WannaCrypt.RSM_4
- 19199 WannaCrypt.RSM_8
- 19881 HydraCrypt.C_2
- 36011 WannaCrypt.RSM_4
- 36115 WannaCrypt.RSM_5
- 36136 WannaCrypt.RSM_6
- 36145 WannaCrypt.RSM_7
Share This Article

An Article By
An Article By
Security News
Security News