This long spreading Android locker has been spotted using Coronavirus theme

SonicWall Capture Labs threat research team observed a number of Android locker samples that cover the homescreen with a ransom message. We observed a number of malicious apps belonging to this locker campaign that are re-packaged to appear as popular apps such as Whatsapp, Netflix and a recent Coronavirus app named in Uzbek - Koronavirus haqida - which translates to "About Coronavirus"
We observed samples as latest as 2020-06-15 on the popular malware portal VirusTotal belonging to this campaign.
Infection Cycle
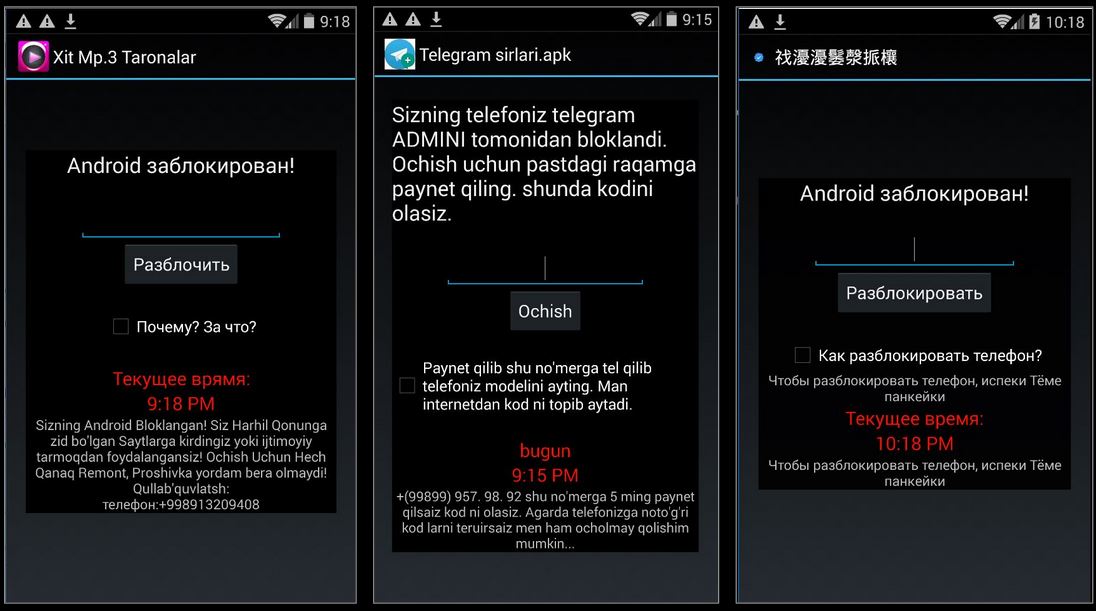
Upon execution the screen is covered by a warning message, the message varies from app to app. Only some apps from this campaign demand a ransom in exchange of the unlock keys. However the template used by these ransom messages is somewhat similar:
Translation of some of the messages shown on the screen by few malicious lockers belonging to this campaign are as below:
- "Your Android is Blocked! You have visited or used sites in violation of law"
- "Android is locked !"
- "Your phone is coded!"
However there are few apps from this campaign that make an effort to stand out:
Startup trigger
Even though the locker does not encrypt files such as a regular ransomware, the phone becomes unusable as buttons do not respond and the phone screen is covered by the ransom message. At this point a victim may not have many options other than to try and reboot the device.
However that does not work because of the permission requested by the malicious locker - RECEIVE_BOOT_COMPLETED. As soon as the device boots, the background service in the malicious locker LockService gets triggered which starts the locker and displays the ransom message over the screen.
Hardcoded unlock key
This locker campaign locks the screen with a ransom message and demands ransom for an unlock code. However the unlock code is hardcoded and can be found within the same class file in the samples belonging to this campaign - com.lololo/LockService;->onClick()
The image below shows hardcoded unlock codes for few samples:
Easy removal
The apps from this campaign do not request dangerous permissions such as BIND_DEVICE_ADMIN and BIND_ACCESSIBILITY_SERVICE, there are no safeguards against their uninstallation from the device. If Developer Tools are enabled on the device a victim can easily remove this locker by issuing the command below over adb:
- adb shell pm uninstall com.lololo
Popular Targets
The apps from this campaign are re-packaged with different app names and icons that match popular apps. Some of the apps we observed during our analysis include:
- Netflix
- Telegram
- Grand Theft Auto 5 hacks
- Minecraft hack
- King root
With the recent Coronavirus pandemic and malware writers capitalizing the 'Coronavirus' theme to propagate their malware, apps belonging to this campaign might soon carry this theme. We already identified one sample by the name - Koronavirus haqida - we can expect more apps from this campaign to carry this theme.
SonicWall Capture Labs provides protection against this threat with the following signature:
- AndroidOS.LockScreen.HM
Indicators Of Compromise (IOC):
- 476b68a650223780ec73f804e639b7ce
- f5cbc2e11e236e5d22d5a3d9af94fdef
- 80738faefeee89e9356645b31e1854e5
- 9e300ed7388a597cdc528b4720859526
- 3178ad2f9d84ba06e14184dd4426c39b
- 19be9e9f7d26cb47054354eefe4bc86c
- 3372427fcd1c02bfc2ab2d65cc3b6311
- 5ece87cded91da6e2a1e7c6a4b8afe0d
Share This Article

An Article By
An Article By
Security News
Security News