The Dangers of Zero-Days in Popular Products
Even if the recently disclosed vulnerabilities don’t directly affect your organization (that you know of …), they should stand as a warning to everyone.

In recent years, we have witnessed cybercriminals targeting technology vendors at an alarming rate. Their quest to find a way to breach one entity to access many others is the ultimate prize. Some threat actors are increasingly focusing on moving upstream into the global supply chains of software and hardware components, targeting the build process to increase the impact of an attack. These “supply-chain attacks,” such as the SolarWinds breach of 2020, can be devastating.
Similarly, some attackers are focusing on finding and exploiting weaknesses already present in widely used products and solutions. The latest of such attacks is currently tracking as CVE-2023-2868 with a CVSS severity score of 9.8/10. While not the result of a supply-chain attack itself, this highly critical vulnerability follows the hallmarks of previous well-recognized supply chain attacks, including 3CXDesktop App (2023), Kaseya VSA (2021), SolarWinds (2020), Asus Live Update Utility (2018), and NotPetya Ransomware (2017).
Much has been written in the past two weeks on this publicly known vulnerability. But this blog highlights the nature of the vulnerability, why it should matter to you even if the affected product is not in your network, and what you can do to minimize your exposure to similar attacks in the future.
To help you with that, we highlighted several critical strategies for consideration below, which included components of a Business Impact Plan (BIP), a vendor management program, and an incident response playbook.
What is CVE-2023-2868?
In the case of CVE-2023-2868, a threat actor exploited the target security vendor's SMTP daemon software components with a new weaponized vulnerability. This attacker successfully injected and executed a uniquely crafted payload containing backdoor functionalities and a reverse shell tool to gain remote access to the vendor's affected systems, which are deployed at an undisclosed number of client networks. As a result, persistence mechanisms were established on infected devices for eight months before discovery. These mechanisms include system manipulation with backdoor command and control (C2) operations, tunneling capabilities to obfuscate C2 communication channels and exfiltration of clients’ sensitive data from affected vendor systems without detection.
For our technical-minded readers, you’ll appreciate the nature of this exploit for its sophistication and impact on the various parts of the target vendor's software stack. To help us keep track of the effects, the vendor assigned codenames SALTWATER, SEASIDE, and SEASPY to inform you of identified indicators of compromise (IOC) as it continues its investigation and remediation. Moreover, to aid clients’ incident response teams in investigating their environments, a series of YARA rules and lists of observed endpoints and network IOC is publicly published.
Malicious payloads with advanced backdoor and reverse shell features — such as we’re seeing with UNC4841’s SALTWATER, SEASPY and SEASIDE attacks — are popular because they can bypass firewall filters, initiate persistent connections from inside the target network and obfuscate C2 traffic from intrusion scanners. These features make such exploits all the more dangerous.
Why should this matter to you?
What we can learn from the CVE-2023-2868 incident is that sometimes there’s no easy remediation. The vendor is unable to adequately remediate actions taken by the threat actors while the appliances are in the field, creating a vicious cycle that could impact your organization — even if you think you’re safe.
You may know for sure that the affected products aren’t present in your own environment. But do you know that they aren't present in the networks of your vendors? What about the organizations that hold your data in SaaS platforms: Is your data impacted there?
Combined with supply chain attacks, the ongoing exploitation of this vulnerability and ones like it demonstrates how interconnected — and fragile — all of our networks truly are. Even if you’re able to confirm this vulnerability can’t affect you in any way, it’s only a matter of time before another high-quality, zero-day vulnerability is discovered. Once it’s found and weaponized, there’s a thriving marketplace with brokers and buyers waiting to acquire it. Where a zero-day vulnerability with a fully verified proof-of-concept (POC) exploit ends up rests entirely at the creator’s discretion. The odds of it falling into the hands of threat actors looking for a big return are a near-certainty.
Taking this as fair warning should encourage us to establish processes to regularly assess and improve our security capabilities and vendor vetting practices.
What actions should you take to manage the risk and impact?
As threat actors continue to shift away from targeting specific organizations and toward targeting supply chains and popular products, we must evolve our security response capabilities to manage the risk and impact that could stem from our technology stack. Here are some key strategies that you can implement at your discretion and as your budget allows:
Develop a Business Continuity Plan (BCP) or Business Impact Plan (BIP) to comprehend the impact of a complete business disruption. Components of these plans can include:
- Mapping of all assets that product-based and supply-chain attacks can impact
- Conducting security pen testing to profile your technology risks
- Identifying the necessary resources, such as personnel and technology, needed for remediation, recovery and continuity of all business functions
- Determining the acceptable downtime or recovery time after the impact
- Describing the testing frequency and processes for updating and maintaining the plan to ensure its relevance over time
- Specifying record-keeping practices and reporting mechanisms to document the findings, actions and lessons learned from an incident
- Outlining the training programs and awareness campaigns to educate employees and stakeholders about the Business Impact Plan, their roles and the actions needed to respond to disruptions
Execute a vendor management program that encompasses:
- Adopting the National Institute of Standards and Technology (NIST) Risk Management Framework to help you assess, uncover and mitigate potential risks within your supply chain
- Executing a clear and comprehensive agreement outlining specific security requirements and expectations involving vulnerability assessments, security controls and incident response protocols
- Putting into motion a regular cadence for auditing and evaluating suppliers’ security development practices, Product Security Incident Response Team (PSIRT) procedures and supply-chain management processes
Establish an incident response playbook and run practice simulations to curtail the impact by:
- Following the NIST Response Framework as a procedural guide
- Assigning roles and responsibilities of the incident response team
- Defining the decision hierarchy and escalation process
- Setting clear communication protocols up and down the organization chain
- Sharing and receiving information regarding new vulnerabilities and remediation procedures to collectively strengthen supply-chain security
- Putting necessary tools in place to help hunt indicators of compromise (IOC) and identify and isolate affected systems
Alternatively, you can outsource the incident response tasks to a third-party threat management service provider to augment your in-house security team. Find a company with experience using the MITRE ATT&CK framework to increase the effectiveness of its threat-hunting activities.
Up your threat detection capabilities by:
- Deploying an intrusion detection/prevention system (IDP/IPS) to hunt for indicators of compromise (IoCs) such as unexpected data transfers, unauthorized access attempts, or unusual system behavior.
- Implement continuous monitoring and log analysis to identify any suspicious activities or unauthorized access attempts.
At no cost, get threat feeds and free tools from the Cybersecurity and Infrastructure Security Agency (CISA)
- Sign up for alerts to be notified whenever a new vulnerability has been added
- Apply the workflow below to help you determine if the new vulnerability directly impacts your organization
- Determine whether there are weaknesses in your defense against that vulnerability
- Utilize SonicWall Capture Client’s ability to scan hosts for vulnerabilities. Alternately, you can leverage this free security scanning tool to uncover software bugs and configuration problems that you need to address
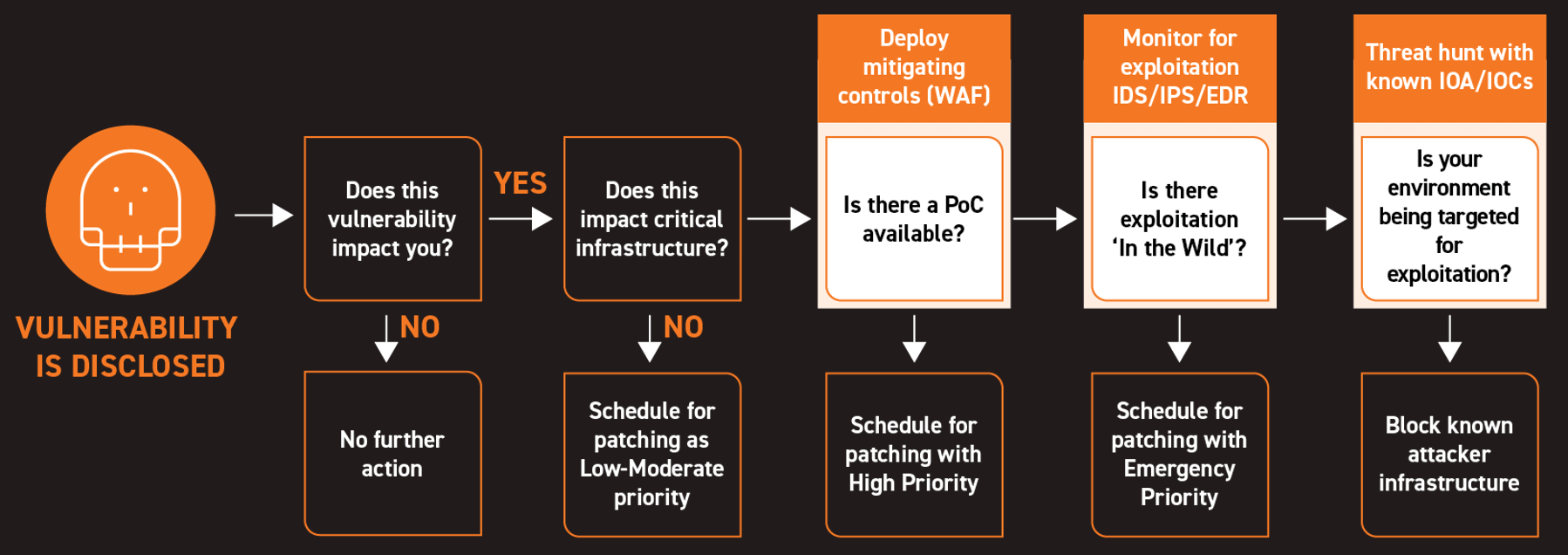
This shouldn’t be taken as an all-inclusive list: Given the complexity of both today’s threat landscape and many of the networks at risk from it, there will almost certainly be things left to do in order to secure your specific environment. But taking the steps outlined above will put you in a vastly better position to prevent and combat attacks such as the ones exploiting CVE-2023-2868.
SonicWall, like other cybersecurity vendors, is working to ensure greater security on our end, as well. We are acutely aware that, even with over 30 years of maturity and experience in the security industry, we’re not immune to attacks targeting popular products. That’s why we’re committed to incorporating every possible security best practice, including PSIRT and Shift-Left secure software development processes, into each stage of our development and design cycles to earn and maintain our customer’s confidence and trust when using our technologies.
Contact us to explore how we can strengthen your defense against supply-chain and product-based threats.
Share This Article

An Article By
An Article By
SonicWall Staff
SonicWall Staff