NetSupport RAT Malware Spied in Ukraine

Overview
This week, the SonicWall Capture Labs threat research team analyzed a sample of NetSupport RAT malware. OSINT shows that this malware has been regularly seen in Ukraine and Poland as of mid- to late-2024. It is a complete Remote Access Tool capable of avoiding AV detection, detecting and breaking analysis tools, persistence, data exfiltration and privilege escalation.
Technical Analysis
The parent file is ‘setup.rar’. It has no defining characteristics beyond being a 2.12MB RAR file.
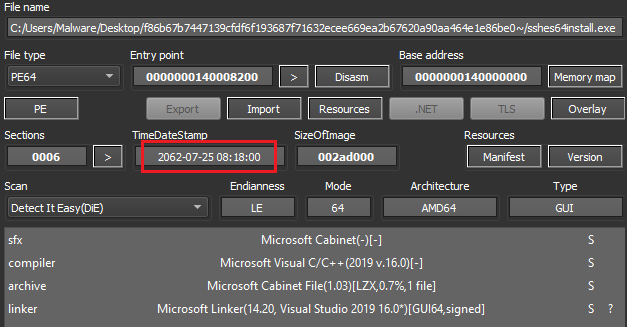
Unpacking this gives a file named ‘sshes64install.exe’, a self-extracting and installing CAB file. The immediate red flag is a timestamp of ‘2062-07-25’. Second, the file itself is 695MB in size.
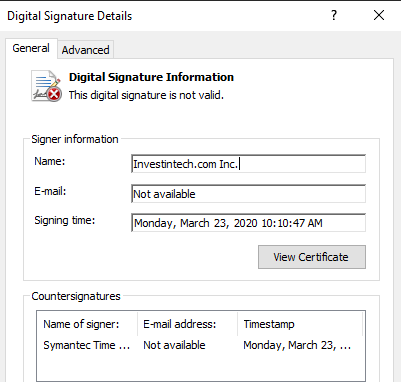
A signed certificate is attached to the file by ‘Investintech.com Inc.’, but it expired in 2021.
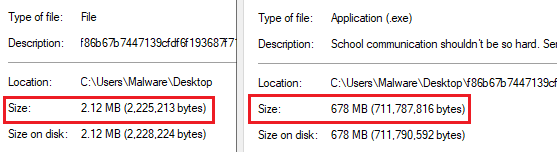
The inflation is artificial. Running the extracted file through a debloat tool shows that the size is due to a single repeating byte in the resources section. This is an anti-analysis/evasion technique, as many tools do not scan files this large.
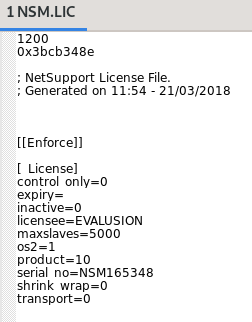
Carving out the contents of this CAB file shows a variety of DLL and configuration files, all of which are in plaintext and unencoded. Please note that the ‘msvcr100.dll’ is a valid DLL from Microsoft; it’s abused to allow for malicious operations.

Client32.exe is the main executable that uses the provided libraries during runtime, each with a suite of capabilities. PCICL32 has the most functionality, performing the following:
Anti-Debug:
- PEB NtGlobalFlag check
- IconResource check
- GetTickCount
- Prints debug messages
Anti-VM:
- Checks for mouse movement via GetMousePos
- Checks for keystrokes via GetKeyState, GetAsyncKeyState, and polling
- Uses GetForegroundWindow, GetActiveWindow, GetProcessHeap
Enumeration:
- Drives
- Network connections
- User accounts
- Files/Folders
- Registry
- Clipboard
- Running processes
- Running services
- Open windows
Collection:
- Screenshots
- Audio
- WMIC for system information
- SELECT * FROM Win32_ComputerSystem
- SELECT * FROM Win32_SystemEnclosure
Network:
- Opens sockets with Winsock and afd.sys driver
- Controls the firewall with INetFwMgr
Control:
- Processes
- Services
- System Power
- Hardware (keyboard, mouse)
- File/Directory (RWX)
- Privilege escalation via tokens and/or afd.sys exploitation
There is also a snippet of the SFX script shown during extraction:
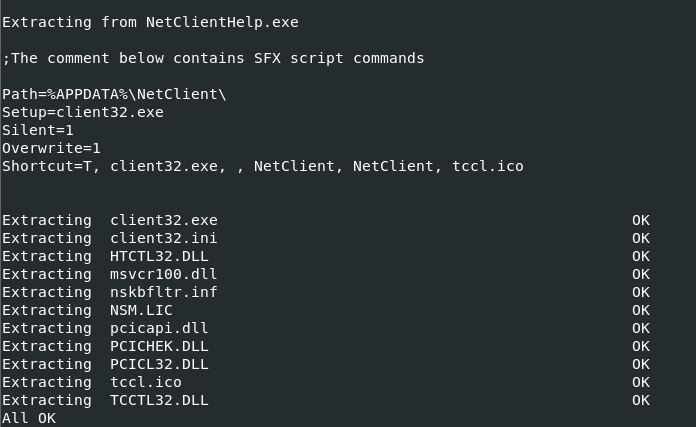
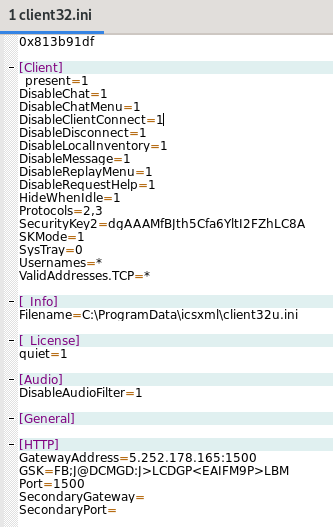
During runtime, ‘client32.exe’ opens local ports 5405, 49556, 49691, 49694-49697, then sends data to ‘5.252.178.165:1500’ and ‘172.67.68.212’, as well as getting the victim’s geolocation via ‘http://geo.netsupportsoftware.com/location/loca.asp’. The ports are opened using what appears to be a ‘use-after-free’ exploit with afd.sys, as the program uses multiple anonymous named pipes. This also allows privilege escalation.
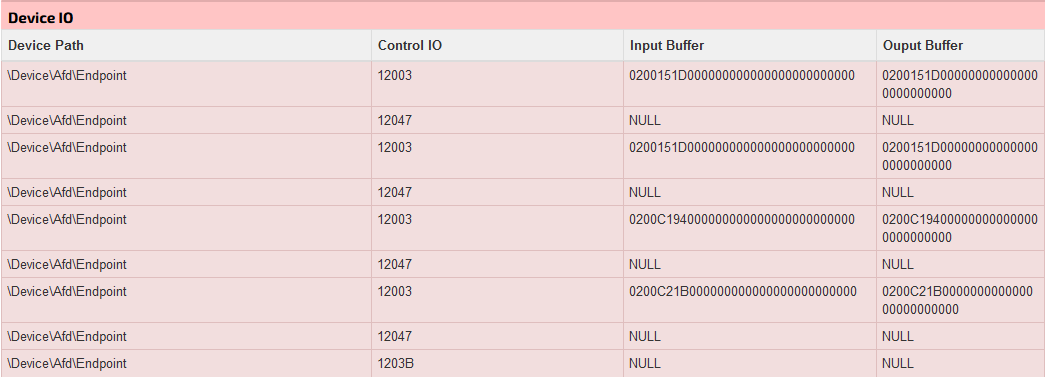
No traffic was observed during runtime from an attacker's IP. Along with this, firewall settings are changed using INetFwPolicy, INetFwRule, and INetFwMgr to allow for further access.
Persistence is set in the registry at ‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce’, as well as dropped files being moved into the ‘~\Startup’ directory. If detected, the malware has the ability to self-delete using a COMSPEC environment variable.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, this is covered by the following rule:
- MalAgent.NetSupport
IOCs
- f86b67b7447139cfdf6f193687f71632ecee669ea2b67620a90aa464e1e86be0 / setup.rar
[ [1] https://cybersecuritynews.com/windows-driver-use-after-free-vulnerability] - a24e61edf5a2116d3d5fc88caa2262a65b1ab53bf8f87c3a0872f03af64ab21e / sshes64install.exe
- 313117e723dda6ea3911faacd23f4405003fb651c73de8deff10b9eb5b4a058a / PCICHEK.dll
- 63aa18c32af7144156e7ee2d5ba0fa4f5872a7deb56894f6f96505cbc9afe6f8 / pcicl32.dll
- 9074fd40ea6a0caa892e6361a6a4e834c2e51e6e98d1ffcda7a9a537594a6917 / pcicapi.dll
- edfe2b923bfb5d1088de1611401f5c35ece91581e71503a5631647ac51f7d796 / HTCTL32.DLL
- 6795d760ce7a955df6c2f5a062e296128efdb8c908908eda4d666926980447ea / TCCTL32.DLL
- 8793353461826fbd48f25ea8b835be204b758ce7510db2af631b28850355bd18 / mscvr100.dll
Share This Article

An Article By
An Article By
Security News
Security News
