Funksec Ransomware Teams Up with Another Ransomware Group to Double Down on Targets

FunkSec is a relatively new but highly active ransomware group that, as of this writing, has targeted several dozen victims across industries like government, banking, communications, and education. In a recent blog post, the group announced a partnership with another ransomware outfit, FSociety, aiming to carry out attacks more efficiently.
This week, SonicWall Capture Labs research team analyzed the group's malware, known as FunkLocker ransomware. Interestingly, rather than demanding massive payouts, FunkSec typically requests just 0.1 Bitcoin. This suggests they may be pursuing a "churn and burn" strategy — favoring a quick turnover approach to rapidly generate revenue.
Infection Cycle
Upon execution, it spawns legitimate Windows processes to do system reconnaissance.
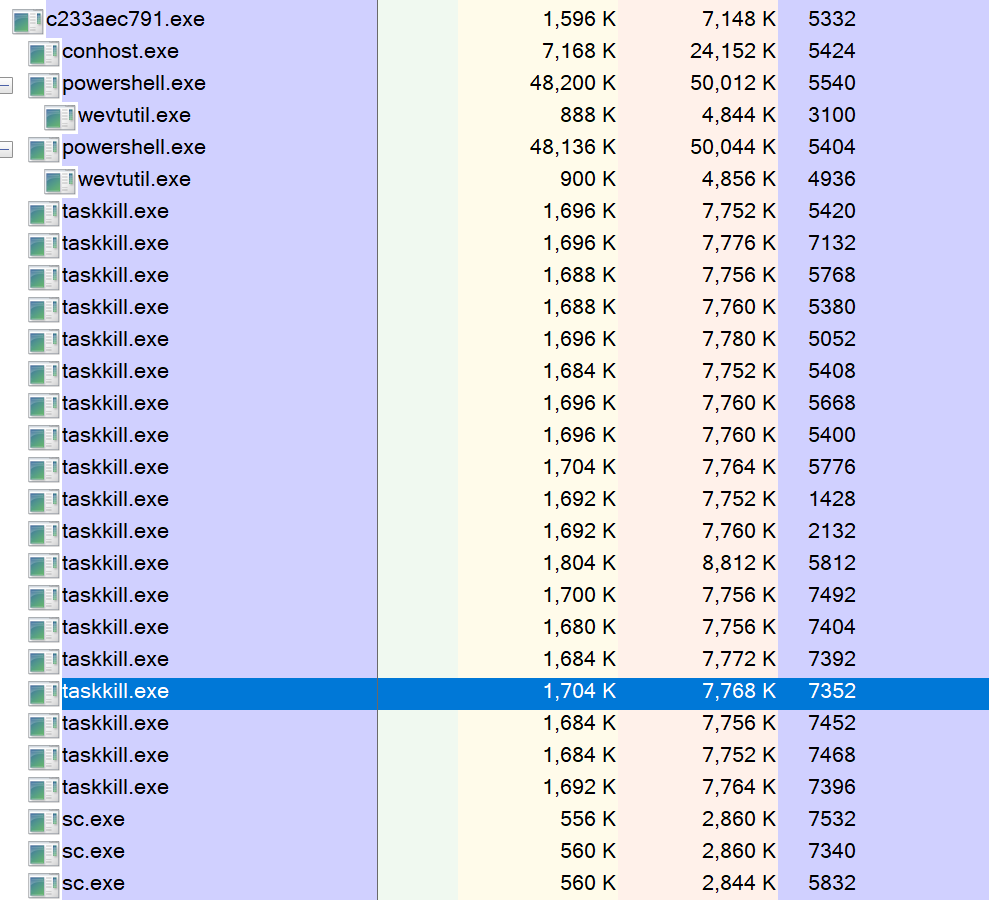
Figure 1: Legitimate Windows processes are spawned upon execution of malware
It uses PowerShell to check for certain system policies in the Windows registry such as internet settings, installed system certificates, current control set code integrity settings, etc.
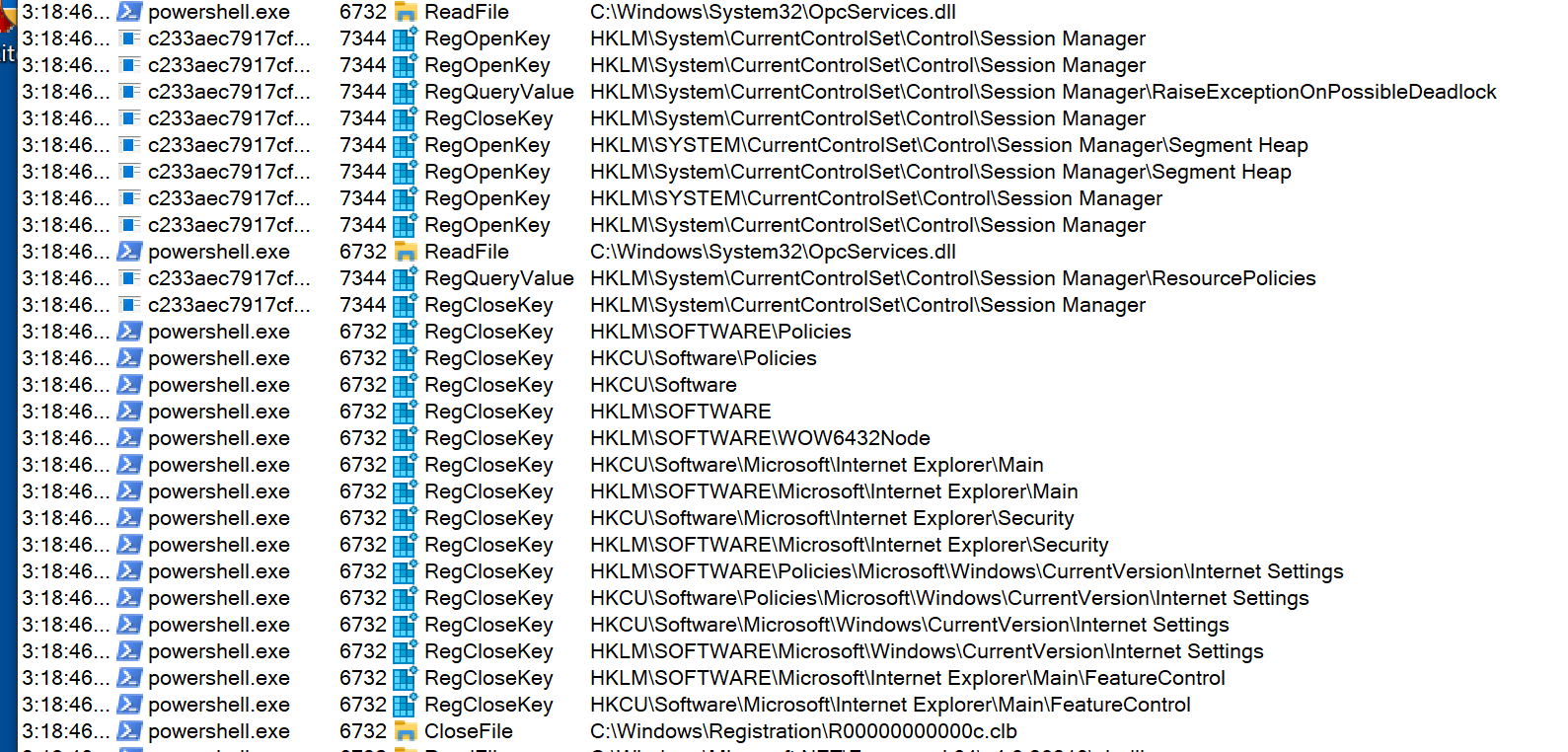
Figure 2: Powershell.exe is used to check various system registry settings
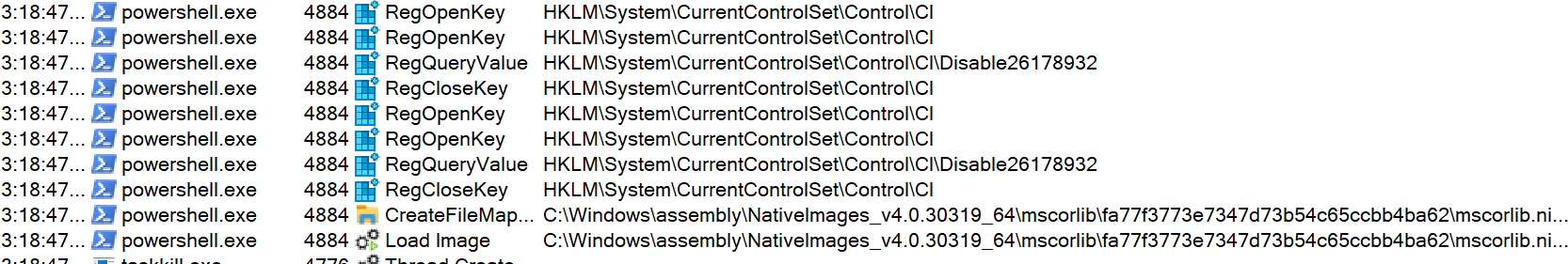
Figure 3: Disabling Current Control Set CI or Code integrity allows applications that might not meet security standards to run on the system.
It also tries to disable certain services using sc.exe.
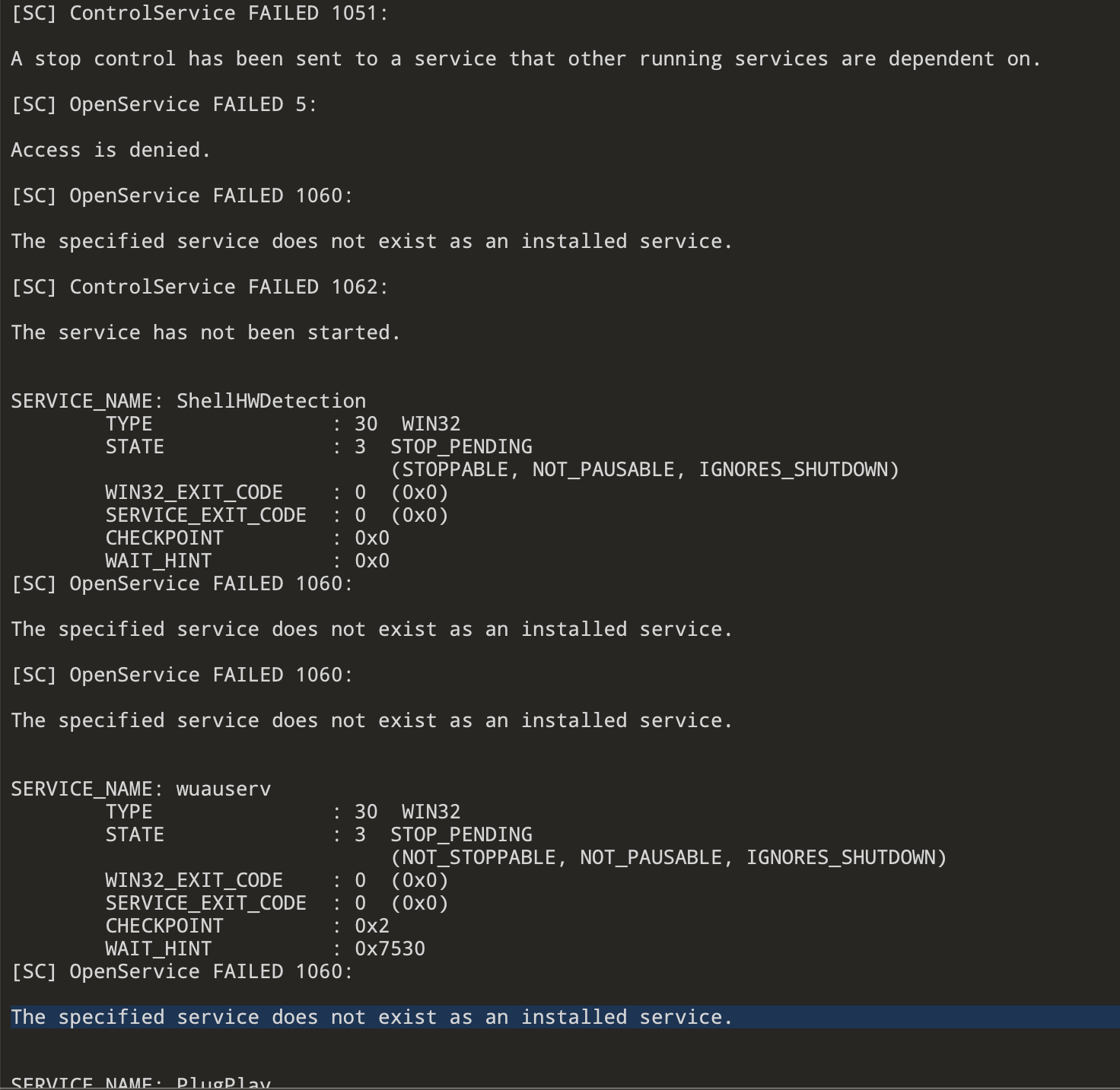
Figure 4: Command line window that shows certain services being disabled
It will then encrypt target files, add the “.funksec” file extension and then reboot the system.
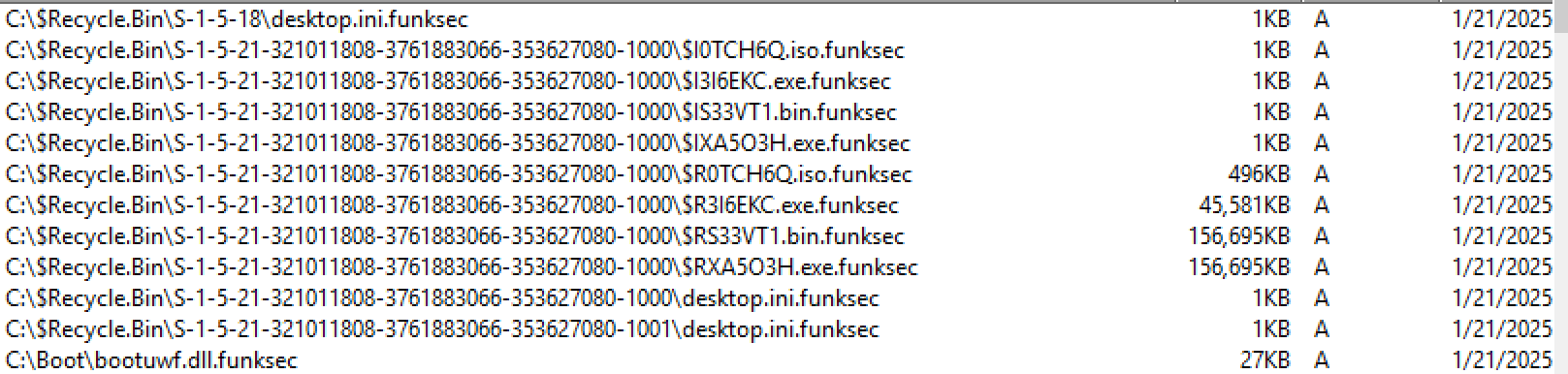
Figure 5: Encrypted files with .funksec file extension
Upon reboot, the victim can find a ransom note on the desktop that asks for roughly the equivalent of $10,000 in Bitcoin in exchange for decrypting the files.
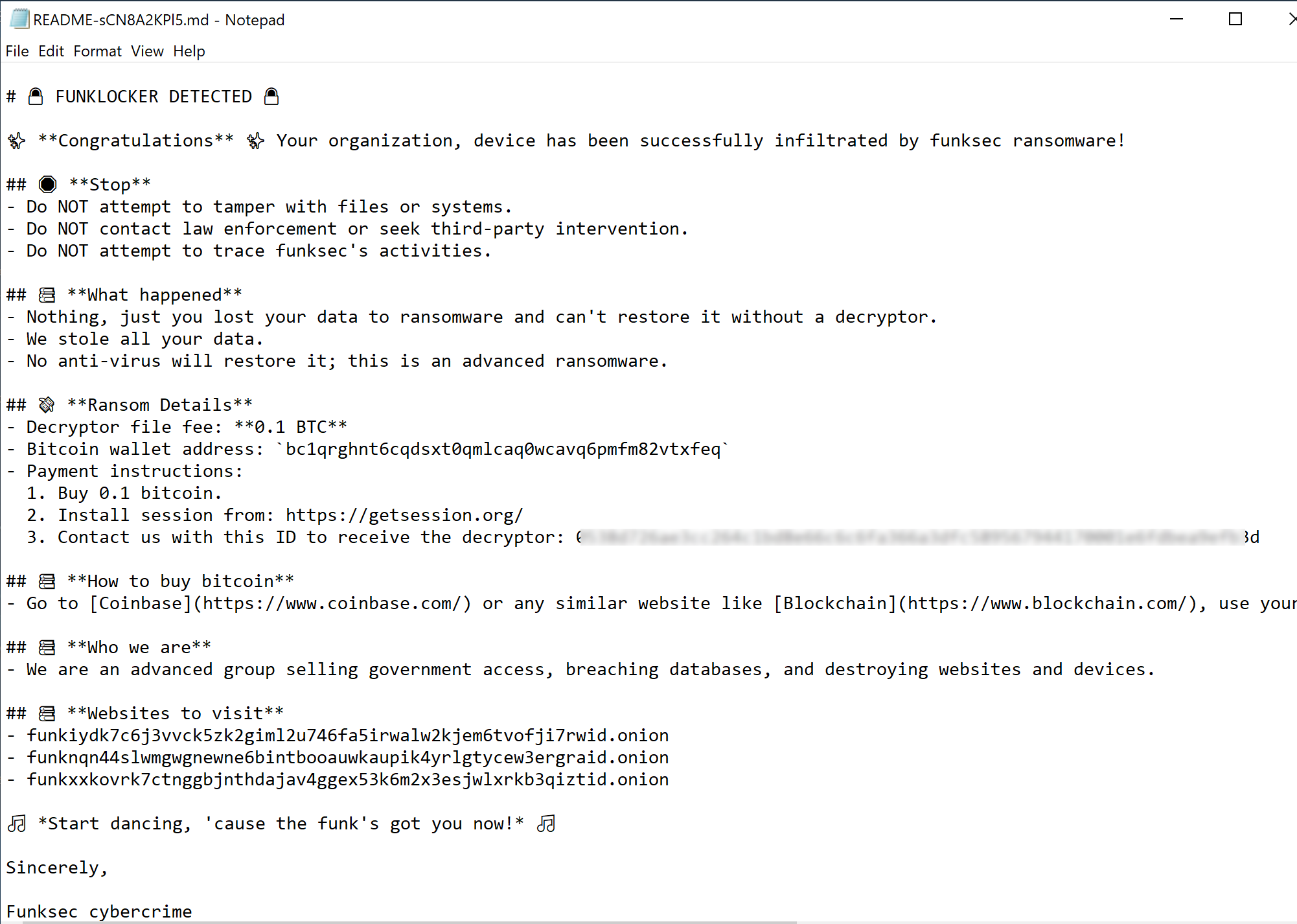
Figure 6: Ransom note on the victim’s machine
On the Funksec TOR website, it displays all of its alleged victims which span across different industries

Figure 7: Funksec TOR website displaying high-profile victims
Funksec's website also features a marketplace where other cybercriminal groups can sell data, which may not necessarily be data stolen by Funksec.
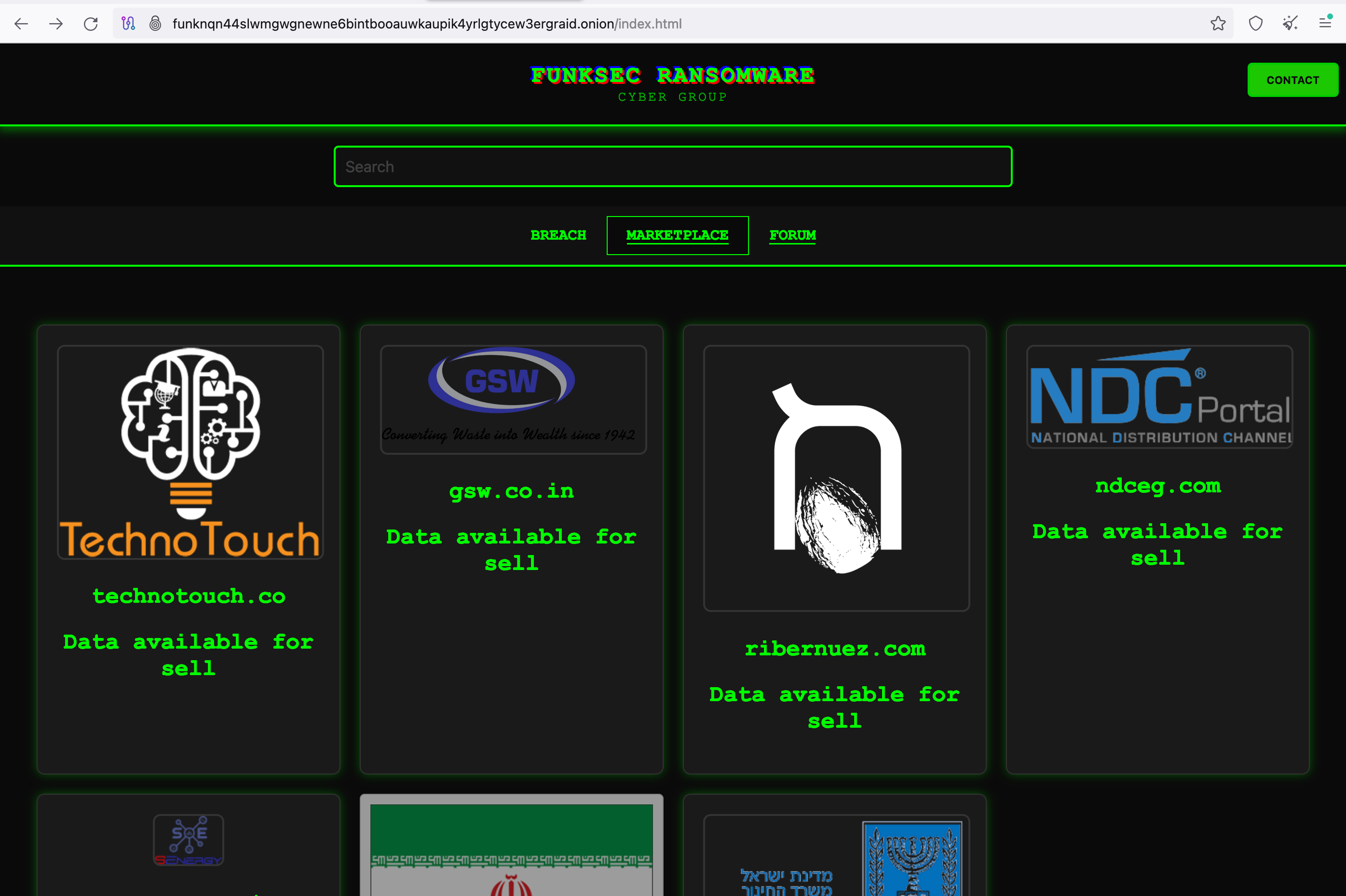
Figure 8: Funksec hosted marketplace for cybercriminals
Its forum site is very active and has recently announced its partnership with another ransomware group.
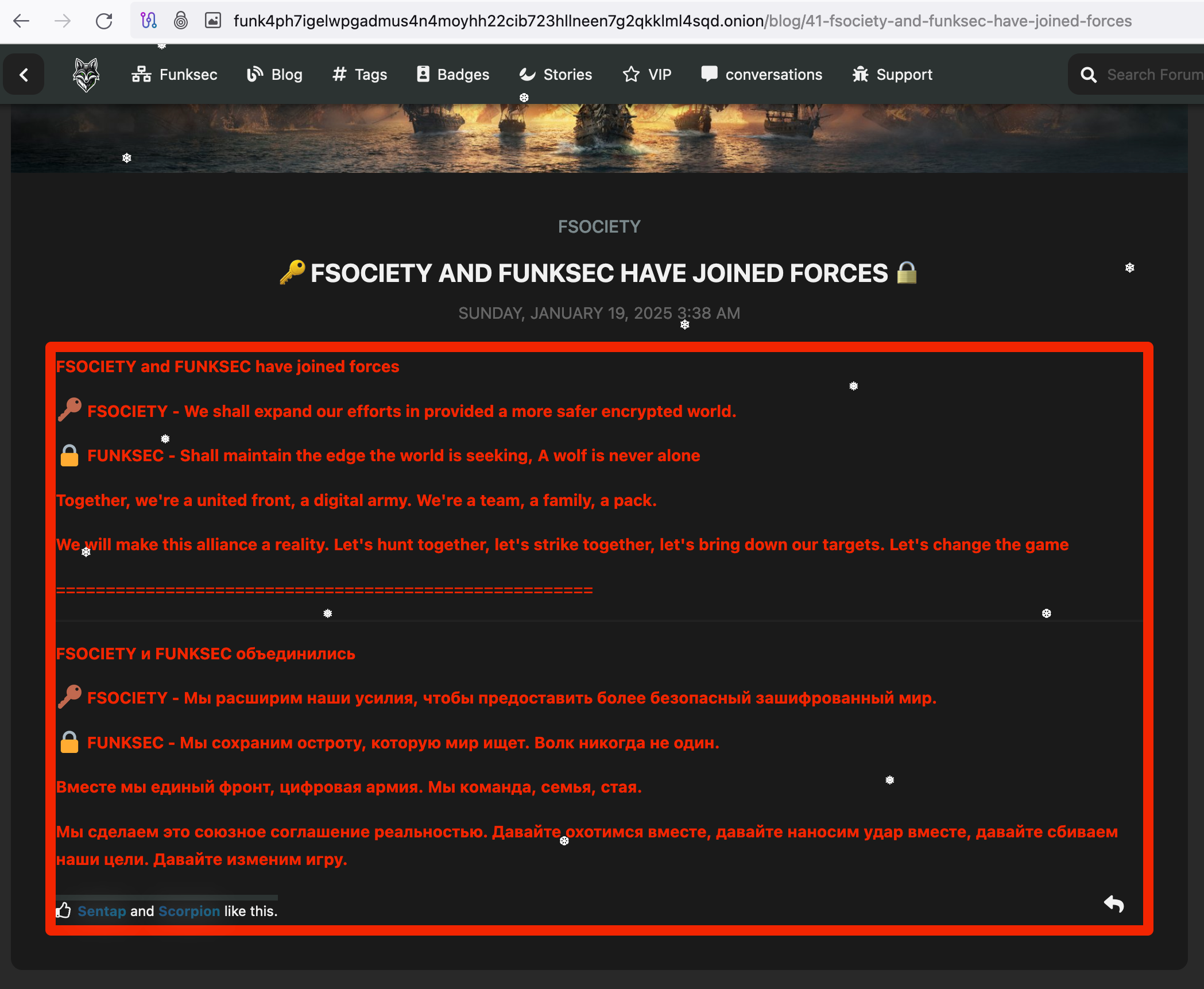
Figure 9: Funksec announces partnership with FSociety
One of the latest threads created shows an example of how this cybercriminal group has been in correspondence with another alleged victim. The operators emphasize the low ransom payment and that they are not interested in negotiation.
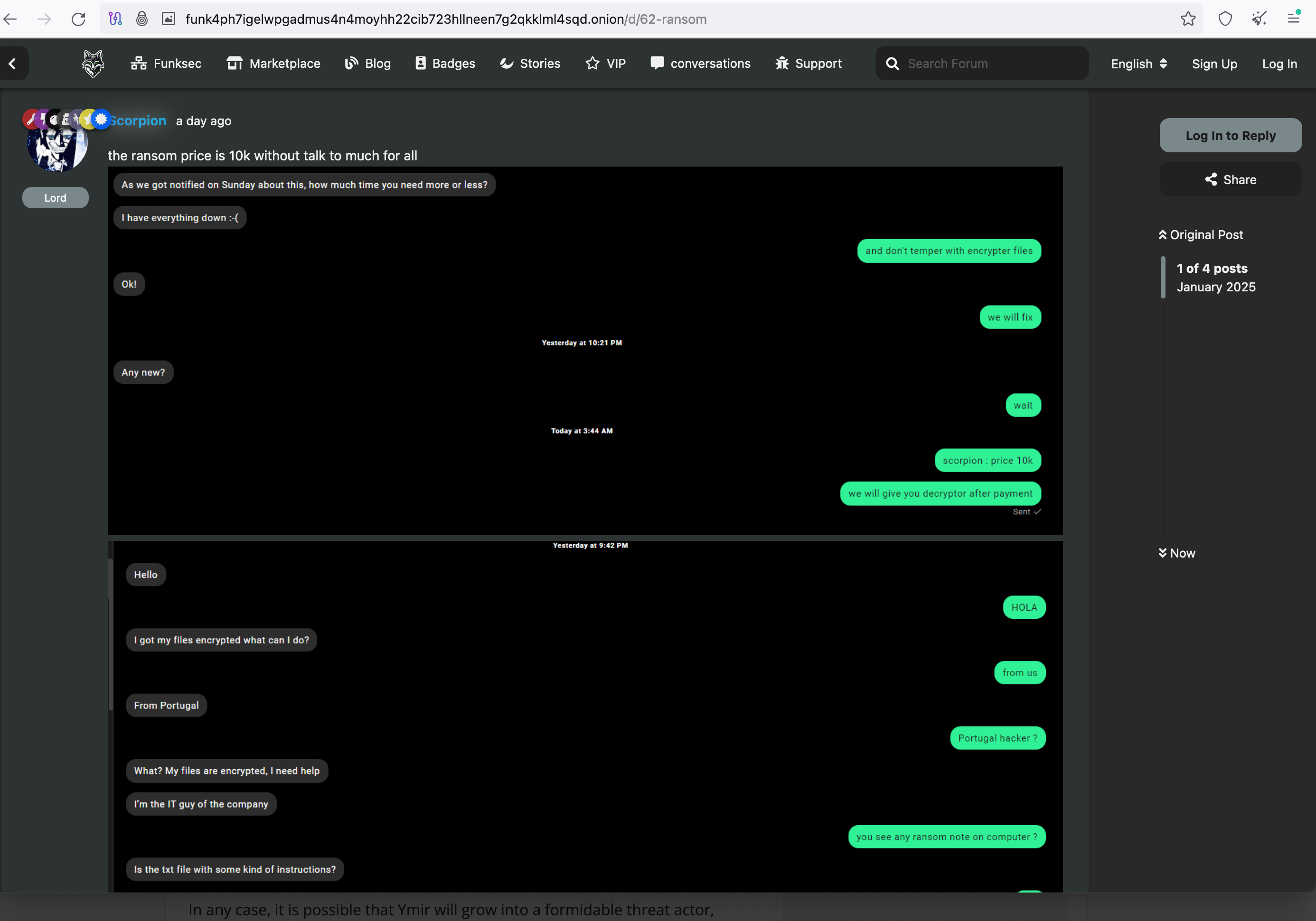
Figure 10: Correspondence with an alleged victim
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV:Funklocker.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
