Docassemble Path-Traversal + SSTI Enables RCE (CVE-2024-27292)

Overview
SonicWall Capture Labs threat research team became aware of the threat CVE-2024-27292, assessed its impact, and developed mitigation measures for this vulnerability.
CVE-2024-27292 is a high-impact path traversal vulnerability in Docassemble, the Python-based expert system for guided interviews, introduced in v1.4.53 and persisting through v1.4.96. The flaw, triggered by a crafted multipart/form-data upload manipulating filename and content-type parameters, causes the application’s file-storage logic to resolve paths outside the intended namespace, allowing authenticated attackers to plant Jinja templates in unauthorized locations. The CVE as reported is limited to this path traversal issue (CWE-22) and carries a CVSS 3.1 base score of 7.5 (High). However, it does not include the subsequent server-side template injection (SSTI) vulnerability (CWE-94) that enables rendering of those templates and leads to full remote code execution. While this SSTI remains unassigned due to a disagreement with the developer, our research team has confirmed the full exploit chain, which results in a working reverse shell payload. When combined, we believe these issues justify a composite severity of 9.8 (Critical).
Disclosed on 29 February 2024 and updated on 21 March 2024, the issue has a 93.85% EPSS likelihood and ranks in the 100th percentile for exploitation risk. The path traversal is documented in the NVD entry, GitHub advisory, and commit 97f77dc, which introduces canonical-path validation. Although not yet listed in CISA’s KEV catalog, the viability of RCE suggests imminent automated exploitation. Users should upgrade immediately to v1.4.97, which remediates the path traversal and disables untrusted template rendering (GitHub advisory, release notes). No reliable workarounds exist.
Technical Overview
Docassemble (v1.4.53–v1.4.96) is exposed to a dual exploitation vector: path traversal and SSTI due to CVE-2024-27292. By smuggling a malicious filename and content-type field inside a multipart/form-data upload, an authenticated user can first break out of the intended storage directory, write an arbitrary Jinja template, and then coerce the application into rendering that template with attacker-supplied data. The end result is reliable remote-code execution under the Docassemble service account, placing confidential interview answers, system credentials, and adjacent services at risk.
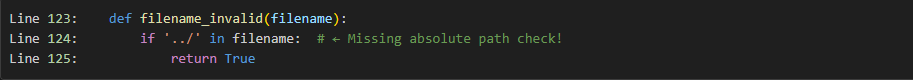
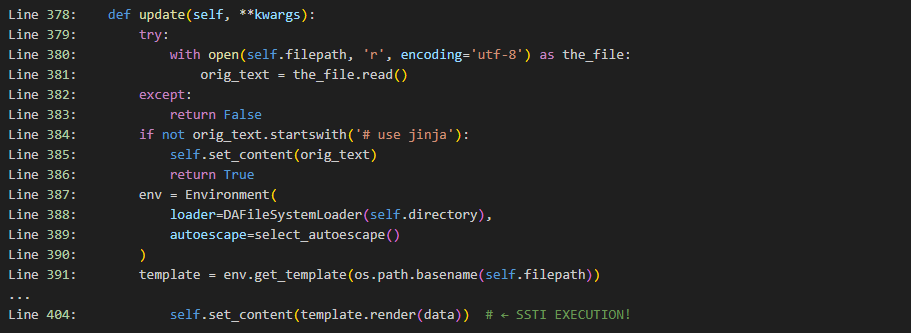
The root cause lies in docassemble_base/docassemble/base/functions.py, where the helper filename_invalid() originally checked only for the string ../. Absolute paths beginning with / or Windows drive letters passed the filter, enabling directory traversal. Once a malicious file reached the server, Docassemble’s update() method (Figure 2) loaded the file with Environment(loader=DAFileSystemLoader(self.directory)) and rendered it via template.render(data), executing any embedded Jinja expressions. Because uploads can be forced to start with # use jinja, the normal “treat as plain text” short-circuit at line 384 is bypassed. This two-stage abuse chain—write anywhere, then execute—yields full RCE.
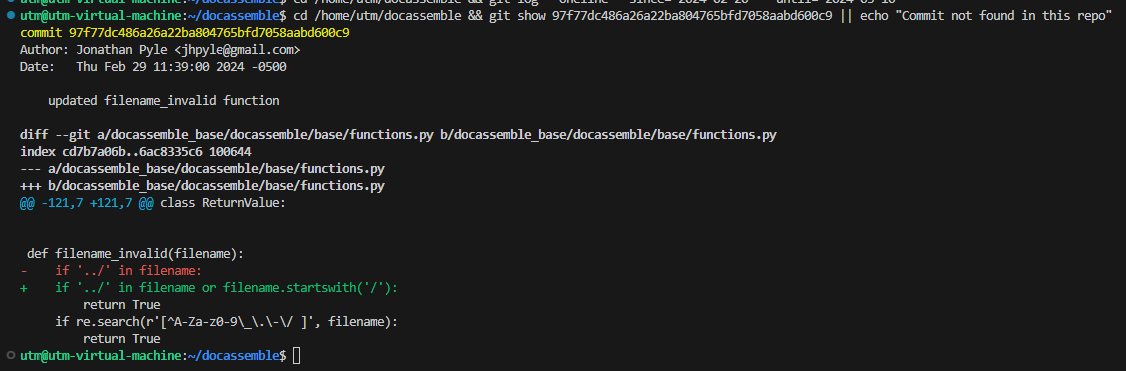
Commit 97f77dc (29 Feb 2024) closes the gap by extending filename_invalid() to reject absolute paths and by hardening canonical-path checks throughout the upload pipeline. Version 1.4.97 incorporates the patch and additionally disables untrusted template rendering for files outside approved directories, neutralizing both traversal and SSTI vectors. Administrators should upgrade immediately; no reasonable mitigations exist short of disabling file uploads outright.
Triggering the Vulnerability
Running Docassemble v1.4.96, an attacker can exploit the platform’s interview file-upload (.yml) feature by chaining an unauthenticated path traversal vulnerability (CVE-2024-27292) with an authenticated server-side template injection (SSTI) issue to achieve remote code execution. By issuing an identical multipart/form-data request matching all headers and parameters, the attacker stores a malicious Jinja template in a location that the interview engine later renders, resulting in arbitrary code execution as the www-data service account.
- Leverage the path traversal flaw to gain access to the Docassemble server
- Authenticate with any valid Docassemble account
- Send a crafted multipart/form-data POST request that uploads the Jinja payload and includes the required filename and Content-Type fields
- Allow the interview engine to process the upload and save the file in the session directory
- Issue a GET request to the resulting file URL, causing Docassemble to render the template and execute the code
- Embed a reverse-shell command in the template to obtain a remote shell running as www-data
Exploitation
As demonstrated in the SSTI exploit script, once the attacker submits a crafted Jinja payload file via the multipart upload endpoint, Docassemble persists it in the session directory and a simple GET to the file URL invokes the template engine. If only proof of concept is needed, embedding a payload that returns a unique marker (for example, {{7*7}}) and observing the HTTP 501 response confirms SSTI execution. For full remote code execution, the adversary injects a reverse-shell command directly in the template (e.g., {{__import__('subprocess').Popen([remote_callback])}}) and repeats the GET request, spawning a shell as www-data. Because session files remain on disk and are processed by interview flows or scheduled jobs, the malicious template can be retriggered without reuploading, yielding persistent RCE with minimal privileges required.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:21317 Docassemble interview SSTI (CVE-2024-27292)
Remediation Recommendations
The risks posed by CVE-2024-27292 can be mitigated or eliminated by:
- Upgrade Docassemble: promptly move to version 1.4.97 or later, as outlined in the official security advisory.
- Enforce file upload restrictions: implement strict server-side validation for filenames, file types, and maximum sizes to prevent path traversal.
- Harden template rendering: disable raw Jinja execution or implement a secure sandbox to block unauthorized code injection.
- Utilize up-to-date IPS signatures to detect and block malicious payloads targeting this vulnerability.
- Continuous monitoring: log and alert on HTTP 501 SSTI errors, and review file access patterns to detect abnormal activity.
Relevant Links
CVE-2024-27292: docAssembling exploits for RCE
GitHub Security Advisory
github commit
docassemble github
docassemble website
National Vulnerability Database (NVD) Entry
CWE-706: Use of Incorrectly-Resolved Name or Reference
Share This Article

An Article By
An Article By
Security News
Security News
