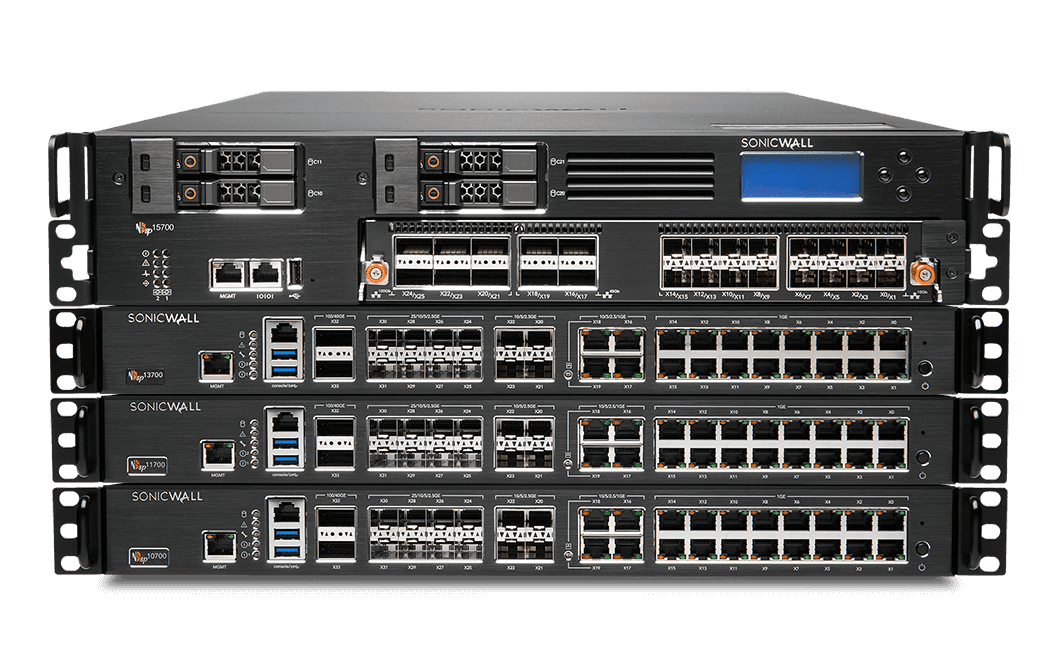
NSsp Series Next-
generation
Firewall (NGFW)
Use Cases
Schools are growing increasingly dependent on cloud-based apps while the number of mobile devices explode. Meanwhile compliance and security requirements are more stringent than ever. SonicWall is helping schools close their security and compliance gaps and enable the new digitally driven approach to education. From the central office to individual schools and campuses, find out how SonicWall firewalls help deliver advanced protection and functions like content filtering and powering PoE devices, all within increasingly tight budgets.
Schools are growing increasingly dependent on cloud-based apps while the number of mobile devices explode. Meanwhile compliance and security requirements are more stringent than ever. SonicWall is helping schools close their security and compliance gaps and enable the new digitally driven approach to education. From the central office to individual schools and campuses, find out how SonicWall firewalls help deliver advanced protection and functions like content filtering and powering PoE devices, all within increasingly tight budgets.
State and local governments are increasingly under attack by increasingly sophisticated threat actors while also required to meet stringent compliance requirements. With highly distributed organizations, maintaining centralized management and effective threat protection is a sizable challenge. Find out how a SonicWall solution, from government data centers and clouds to branch offices, block threats, ensure compliance and allow you to focus on your constituents and your mission.
State and local governments are increasingly under attack by increasingly sophisticated threat actors while also required to meet stringent compliance requirements. With highly distributed organizations, maintaining centralized management and effective threat protection is a sizable challenge. Find out how a SonicWall solution, from government data centers and clouds to branch offices, block threats, ensure compliance and allow you to focus on your constituents and your mission.
Gen 7 Firewalls: Our Platform-Ready NGFW