WordPress Unauthenticated Arbitrary SQL Execution Vulnerability

Overview
The SonicWall Capture Labs threat research team became aware of a noteworthy vulnerability –an SQL injection in the WordPress plugin Automatic by ValvePress – assessed its impact and developed mitigation measures for it. Around ~38k active users have installed this premium plugin. The issue allows trivial SQL injection attacks against the plugin user’s authentication process, which could allow WordPress website takeovers. The SQL vulnerability is identified as CVE-2024-27956 and was assigned a critical CVSSv3 score of 9.9. Considering the sizeable user base, low attack complexity, and publicly available exploit code, including a simple SQL query, WordPress users are strongly encouraged to upgrade their instances to the latest or automatic plugin version above 3.92.1 with utmost priority.
Technical Overview
This vulnerability allows threat actors to circumvent the authentication mechanism by sending a crafted SQL query to the web server.
The WordPress Automatic plugin, developed by Valvepress, is popularly known for automatically posting content from any website. It can import content from popular sites like YouTube, Flickr, Vimeo, Twitter and other social media platforms utilizing the APIs from almost any website. It can also generate content using OpenAI’s ChatGPT.
CVE-2024-27956 arose due to improper neutralization of special elements used in an SQL Command. This allows unauthenticated actors to bypass the normal authentication process and inject SQL code that grants them elevated system privileges. This further allows nefarious activists to create admin‑level user accounts, upload malicious files and take full control of affected sites. Out of the 5.5 million attacks observed, as reported by HackerNews in the last week of March 2024, it was observed that attackers changed the name of the vulnerable file “inc/csv.php” and renamed sensitive files to prevent the site owner or fellow hackers from controlling the hijacked site. Once a WordPress site is under their control, attackers ensure the longevity of their access by creating backdoors and modifying the code.
Triggering the Vulnerability
The flaw exists in “inc/csv.php”, which generally resides under the plugin installation directory. A typical path to the vulnerable file is “/wp‑content/plugins/wp‑automatic/inc/csv.php”. It is also shown in our PoC demonstration in Figure 2.
WP users can supply any random SQL query to the $q variable, as shown in Figure 1. This variable will be further executed on line 32 of Figure 1, with $wpdb->get_results( $q).
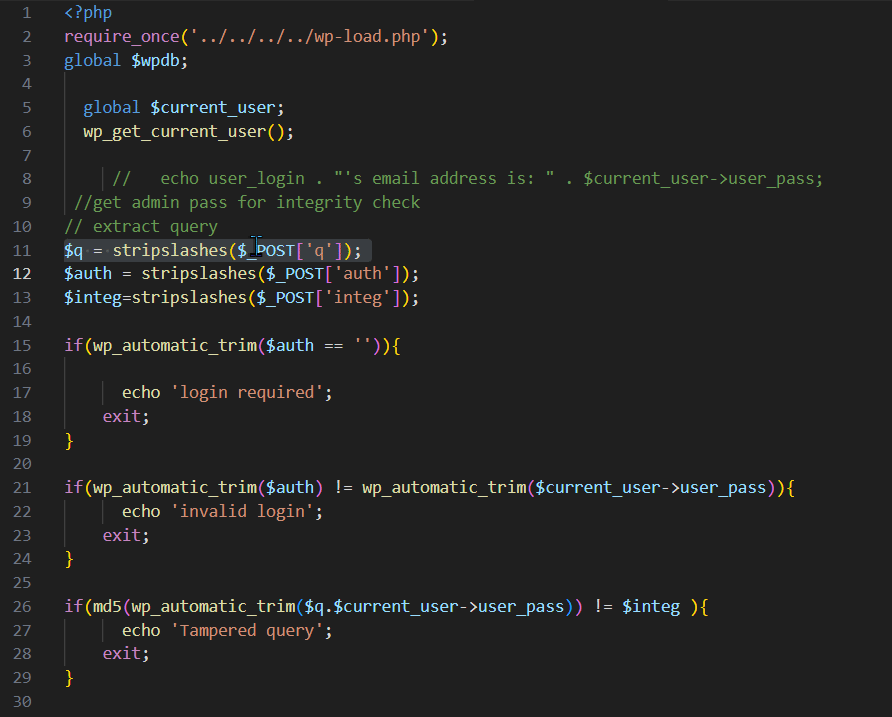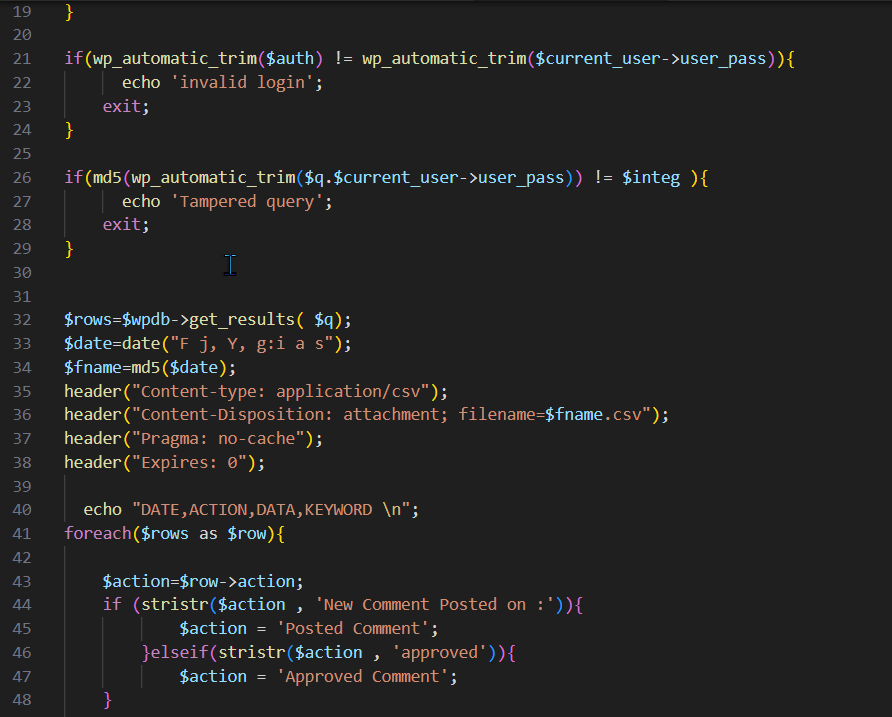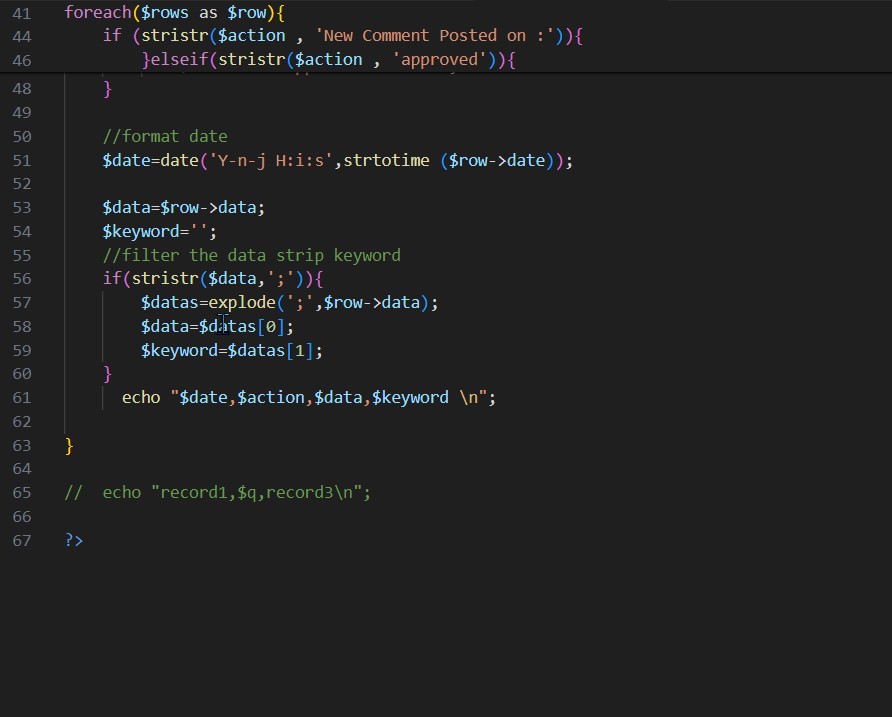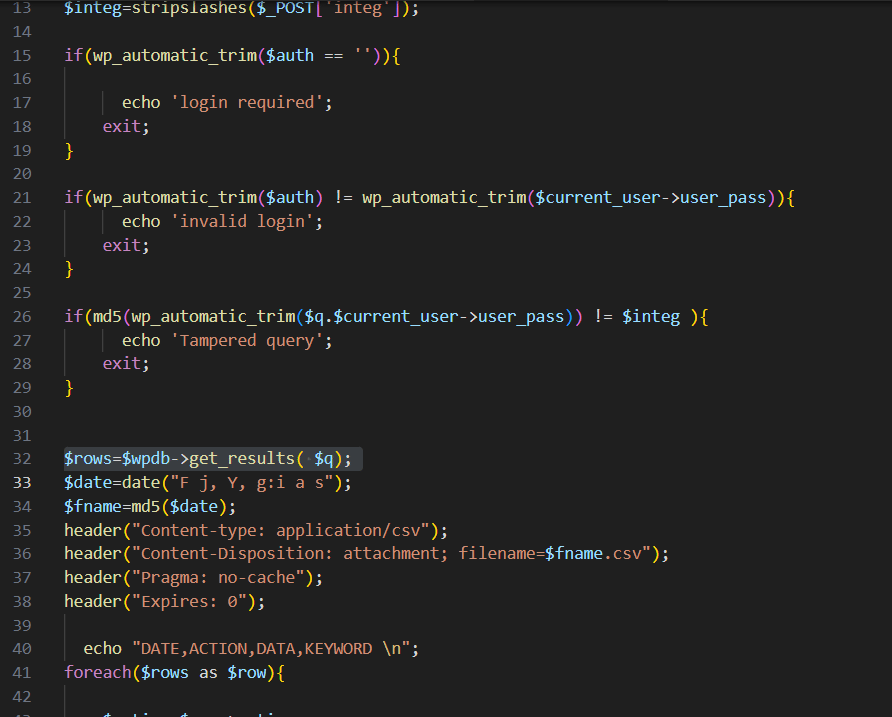
Figure 1: inc/csv.php
Prior to execution, there are basic authentication and integrity checks.
- The first check involves the $current_user->user_pass This value would be an empty string if an unauthenticated user accessed the file.
- The second check needs only the MD5 value of the supplied SQL query to the $integ since $current_user->user_pass is an empty string.
- Additionally, before the two checks, there is a check of if(wp_automatic_trim($auth == '')), which means one can't just input an empty string to the $auth.
- To bypass this, an attacker can supply a single whitespace (" ") to the $auth as &auth=%00 and achieve an arbitrary SQL query execution.
An example POST request to trigger the vulnerability would look like:
http[:]//target-ip:port/wp-content/plugins/wp-automatic/inc/csv.php
q={{query}}&auth=%00&integ={{md5query}}
With the authentication parameter containing whitespace, as shown in Figure 2.
Exploiting the Vulnerability
To exploit the issue, a WordPress setup with ValvePress’ vulnerable WordPress automatic plugin (< 3.92.1 version) is needed. An attacker only needs to be able to access the instance remotely which could be over the internet or a local network. A working PoC with a crafted SQL query aids in exploiting this vulnerability.
A demonstration of exploitation based on the publicly available PoC can be seen in Figure 2 (below).
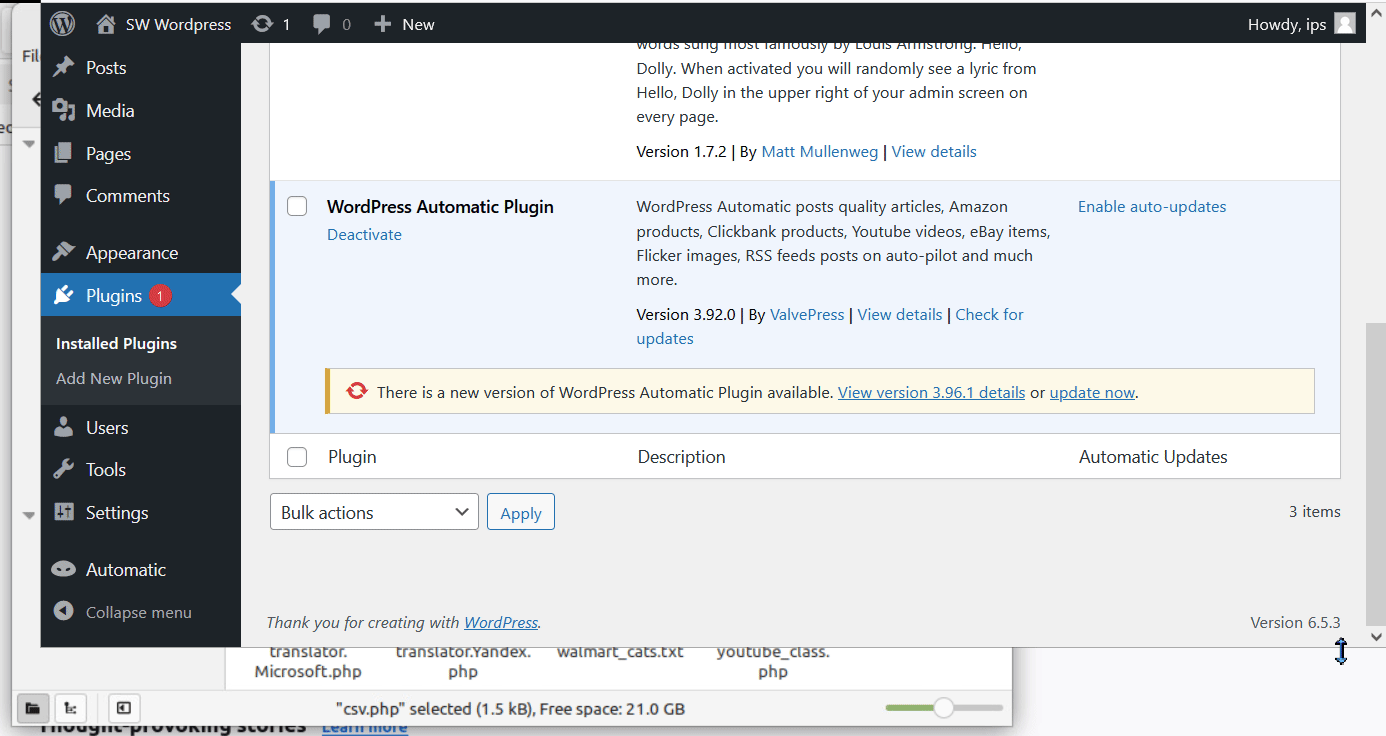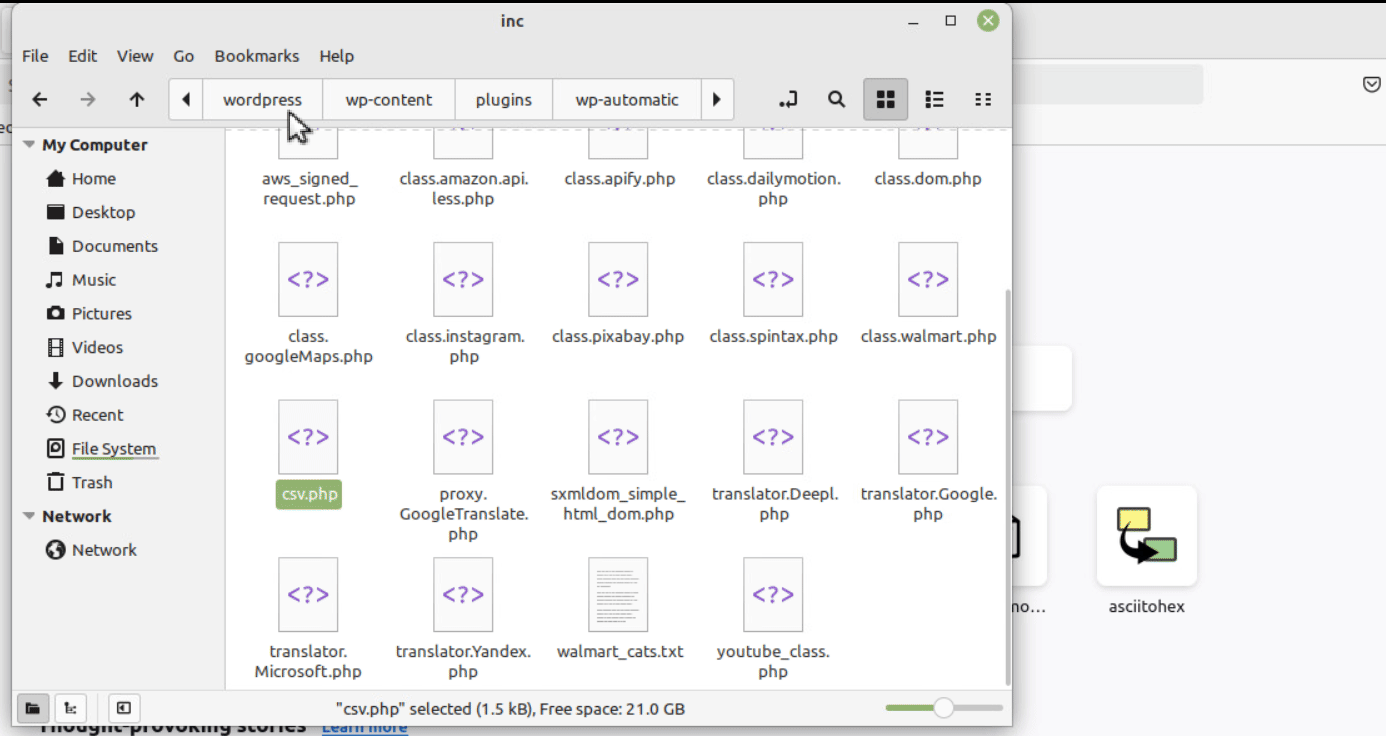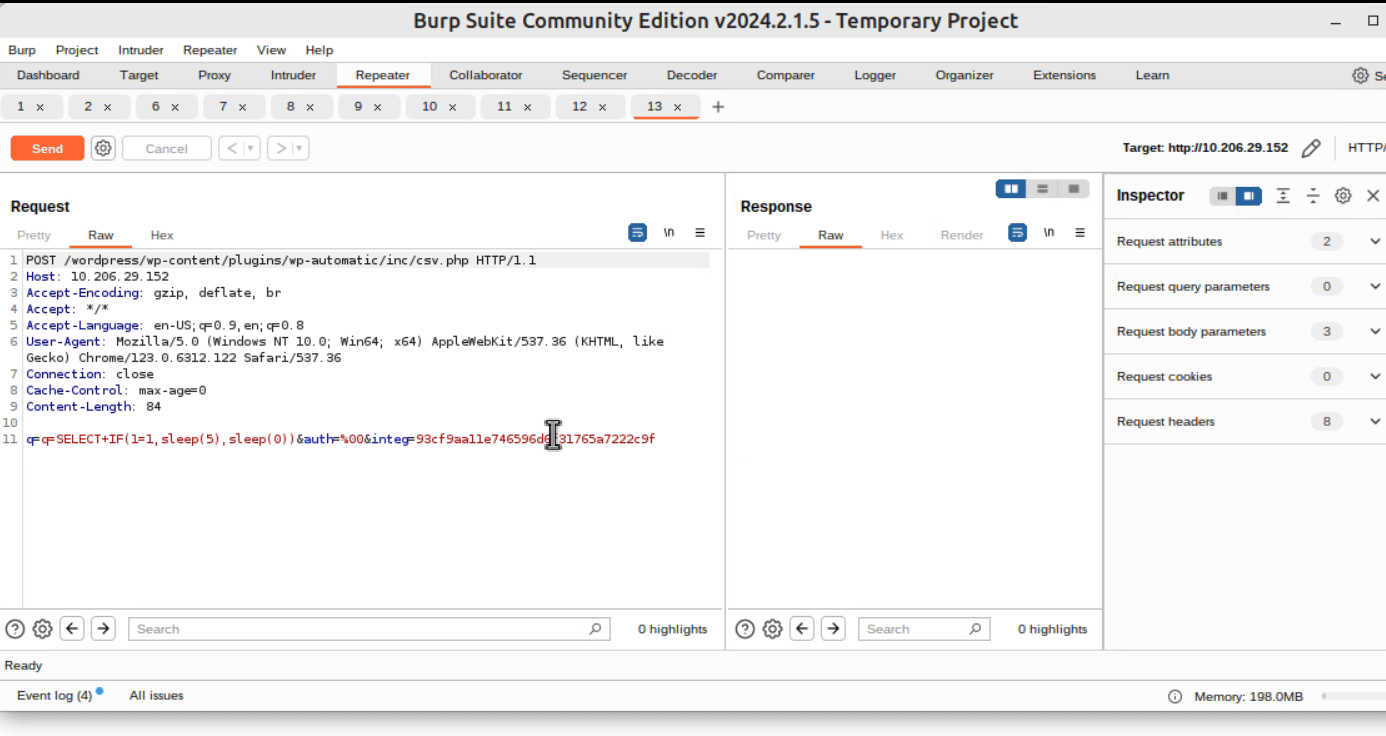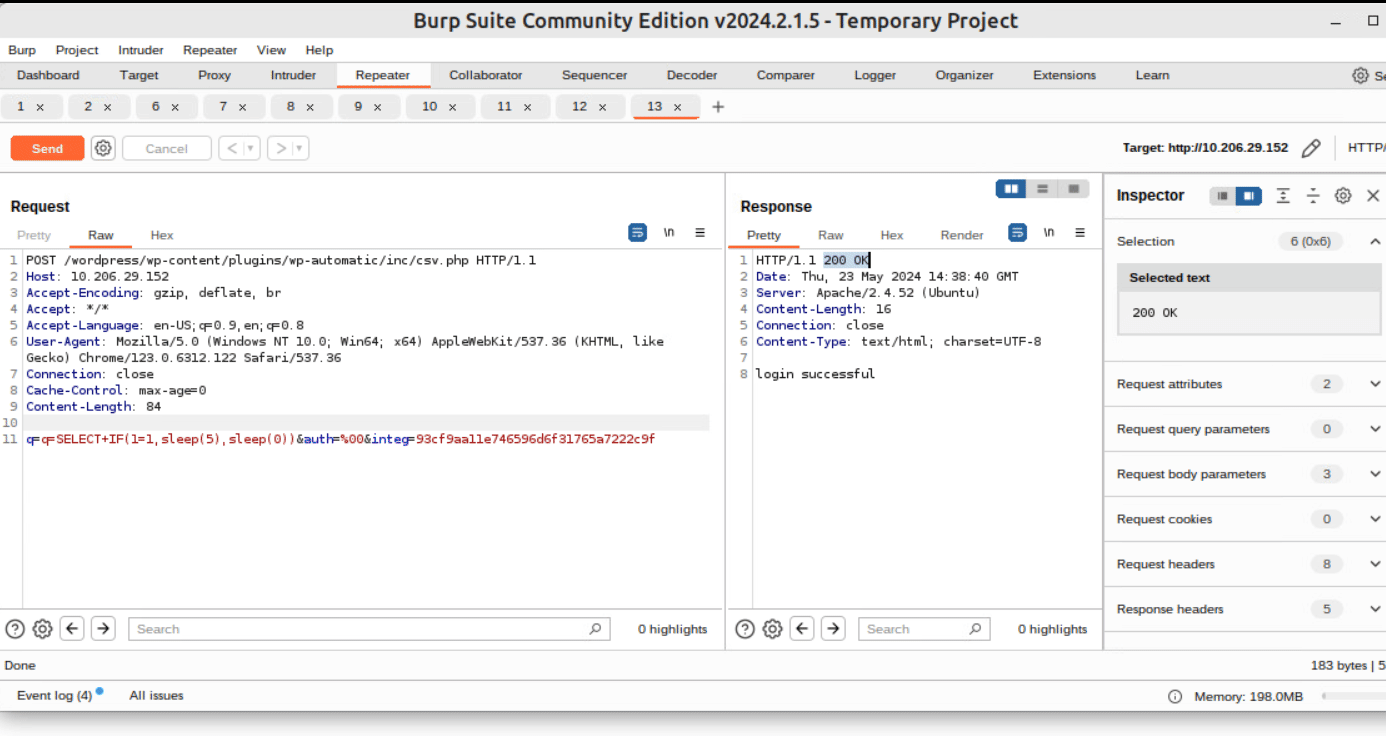
Figure 2: CVE-2024-27956 Exploitation
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
IPS: 19918 - WordPress Automatic Plugin SQL Injection
Remediation Recommendations
Considering the severe consequences of this vulnerability and the trending of nefarious activists trying to leverage the exploit in the wild, users are strongly encouraged to update their instances to WP automatic plugin version 3.92.1 or later to remove the vulnerability.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News