UC Browser: Web Browsing Incognito (Dell SonicWALL Application Control)

UC Browser on Android
UC Browser (UCWeb Inc.) is a mobile web browser with a large market share in China, and India. It has versions for most of the popular mobile devices. As of 2015, they claim to support over 3,000 models of cell phone devices. The browser tunnels your web traffic via the UCWeb servers located in China. They claim that their compression of web data improves download speeds and reduces data usage charges for customers. The Incognito mode allows user web surfing to evade firewall filtering. This article analyses UC Browser Incognito mode traffic to their UCloud from an Android smart phone, and the stand-alone PC version. The company is affiliated with TaoBao, and the parent company is Alibaba.
Install the App from the Google Play Store

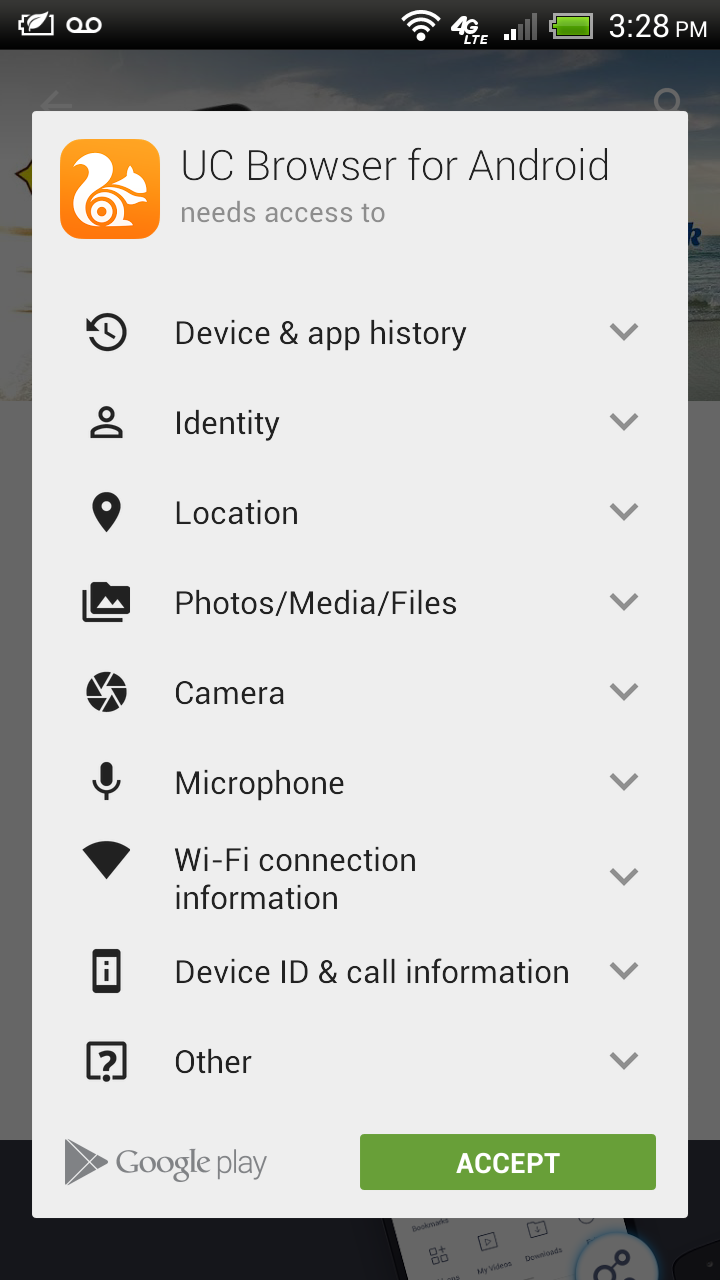
Beware of the Terms of Agreement
Many mobile apps include access to your pictures and other media on the phone, camera, and microphone, device ID and call information, identity, other.
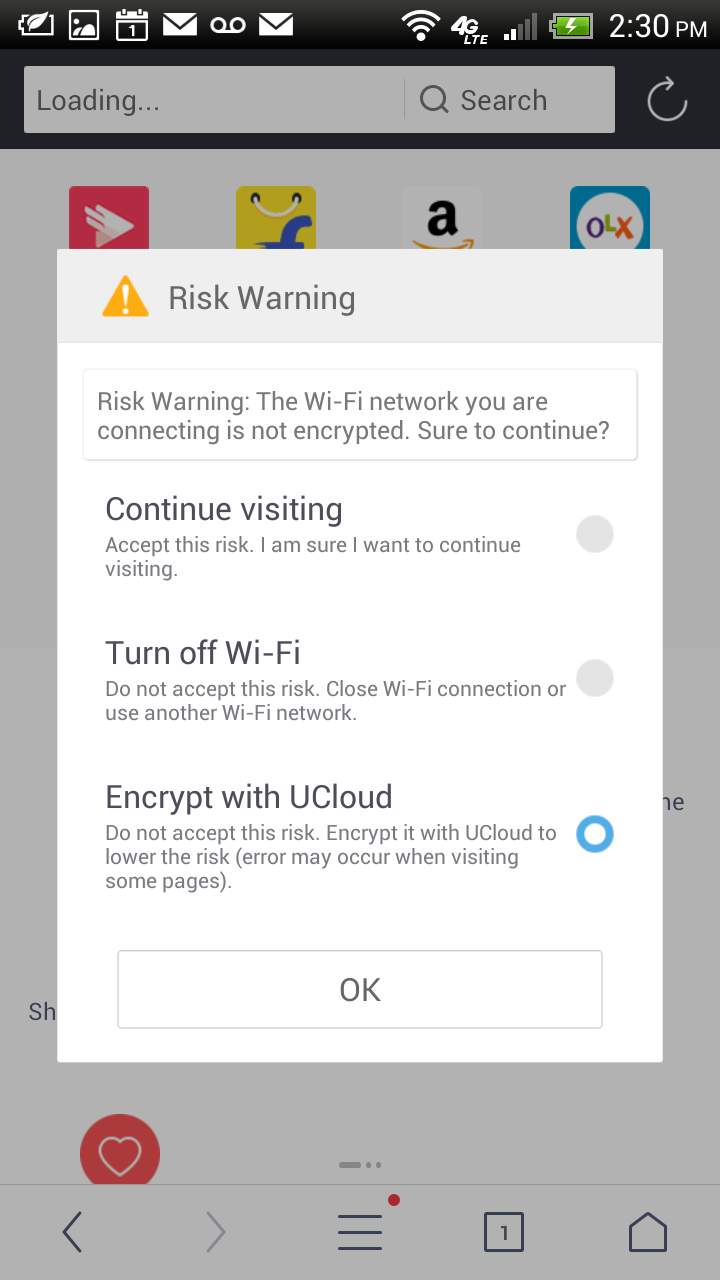
Enable Encrypt with UCloud
Go to the options menu, and choose "Encrypt with UCloud".

Enter a URL
Here I am browsing to www.craigslist.com.

Network Packet Traces
Here you can see a few representative samples of traffic collected from the application.
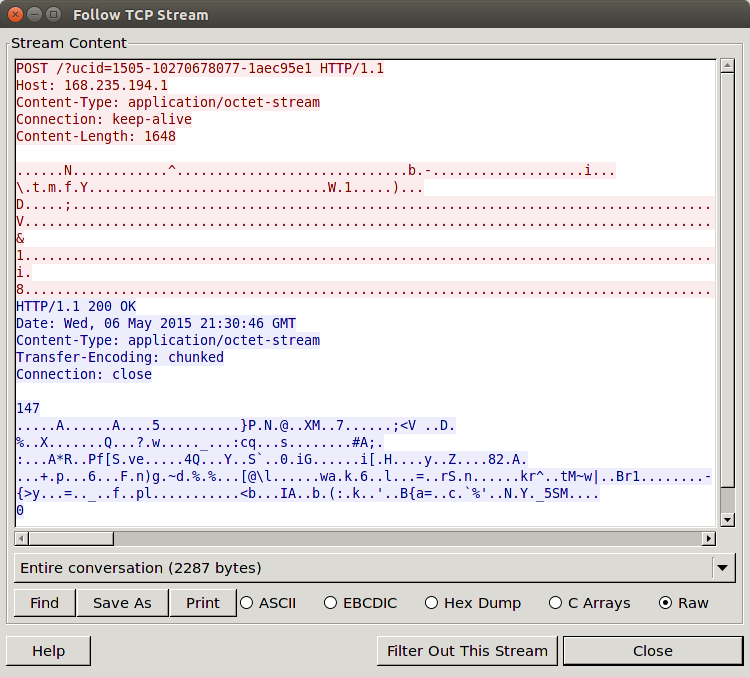
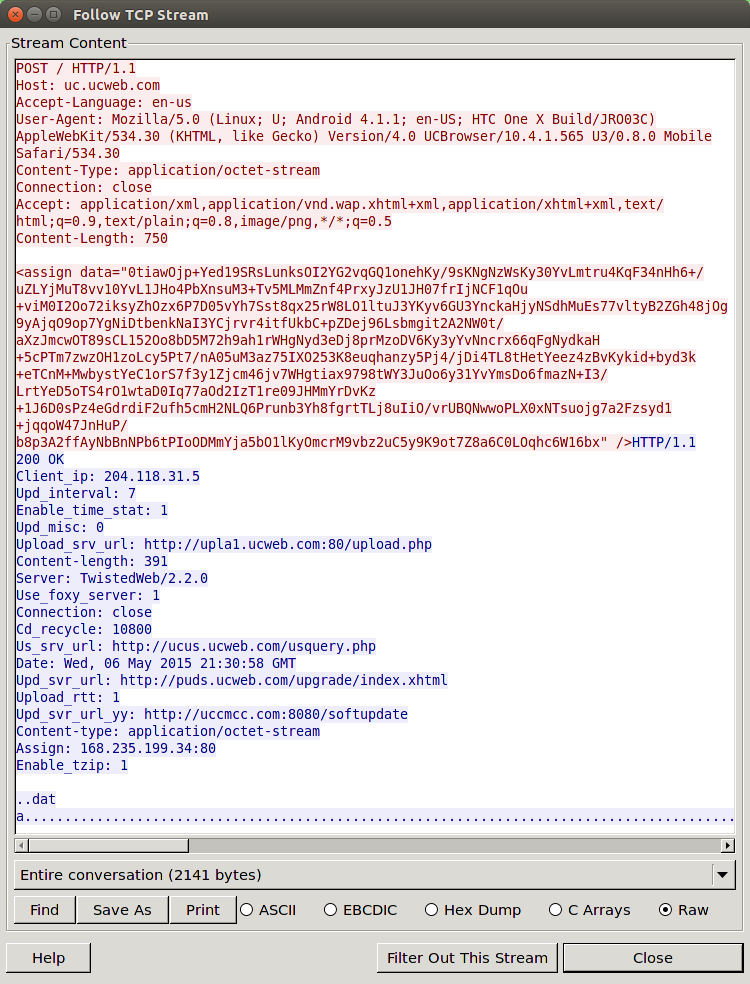
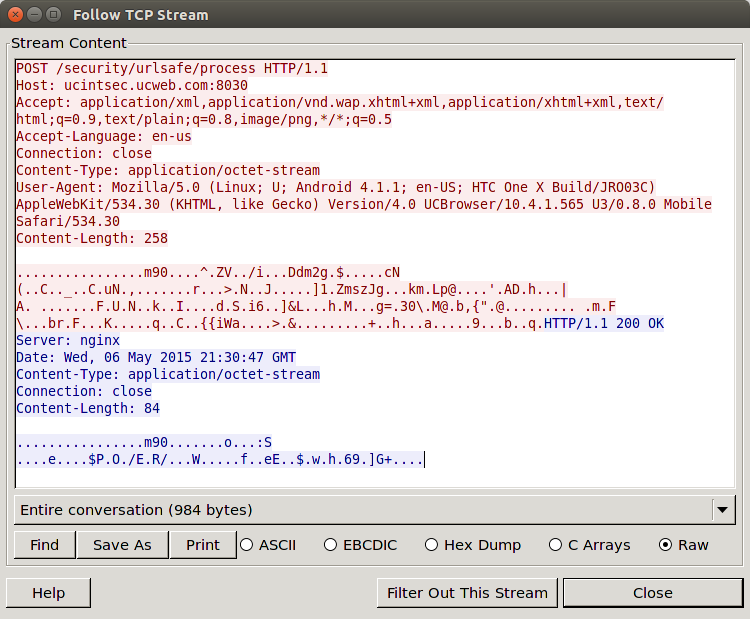
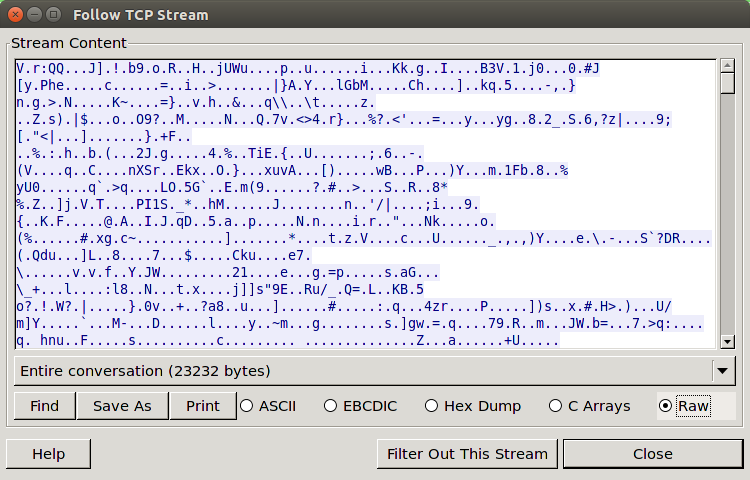
This application is collecting data from the application and sending it back to a UCWeb domain.
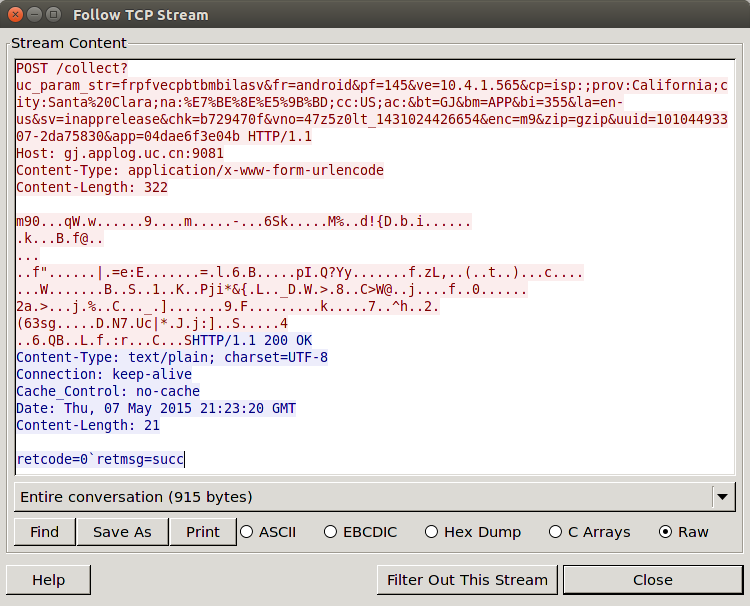

Proxy Servers hosted by MileWeb
Most of the application traffic passes through proxy servers hosted by a company called MileWeb (www.mileweb.com). The traffic to the server seems to be encrypted. The traffic coming from the server HTTP Chunk (Transfer) Encoded. I was not able to decode the encrypted traffic in either direction. After de-chunking the servers traffic, it appears to be using compression format called TTComp archive data. However it did not decode as such, so may be a proprietary compression format.
Blocking this traffic with Dell SonicWALL Application Control
To block this traffic, enable the following Dell SonicWALL Application signatures:
- 10913 UC Browser -- HTTP Activity 1
- 10914 UC Browser -- HTTP Activity 2
- 10915 UC Browser -- HTTP Activity 3
- 10921 UC Browser -- HTTP Activity 4
- 10922 UC Browser -- HTTP Activity 5
To block unknown encrypted traffic communications from your network, enable the following:
- 5 Encrypted Key Exchange -- Random Encryption (Skype,UltraSurf,Emule)
- 7 Encrypted Key Exchange -- UDP Random Encryption(UltraSurf)
Share This Article

An Article By
An Article By
Security News
Security News