Trojanized Android Ahmyth RAT spreads via legitimate apps

SonicWall Capture Labs Threats Research team observed an Android Remote Administration Tool (RAT) named Ahmyth which is being trojanized into other Android apps and is getting distributed in the wild. Upon infecting an Android device this RAT can send sensitive information present on the device like SMS and call logs as well as perform functions like taking a picture, sending a text message or record audio via the microphone.
After obtaining a couple of malicious RAT samples we investigated further revealing the origins of this RAT. We found a Github repository that hosts the code for this RAT - https://github.com/AhMyth.
This RAT was released in 2017 and supports multiple Operating Systems:
The author claims that this was developed for educational purposes (as highlighted on Github) but clearly someone is spreading this RAT for their own malicious motives, more on that later.
Inside Ahmyth
This RAT contains two components:
- Client side component - which runs on the victim's Android device
- Server side component - this runs on the computer which is used to monitor the victim and send commands to the infected device
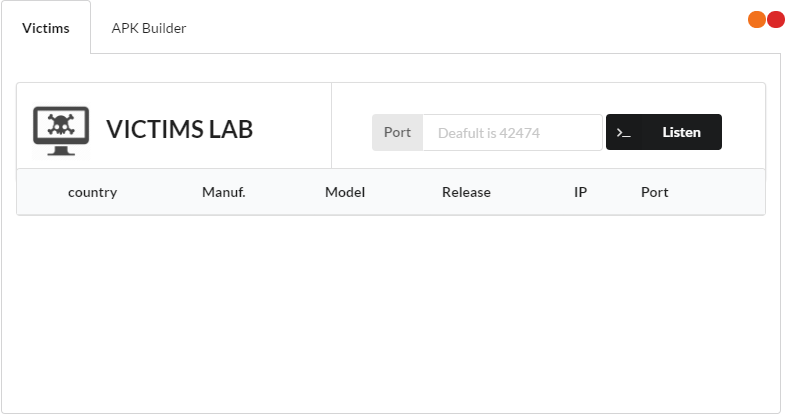
Upon installing and running the server component we see the opening screen which shows a list of victims, currently in the image below there are none since we haven't infected any victims yet.
In-order to report back to the server we add the server's IP address in the source, once done we can build an apk which will report back to our machine:
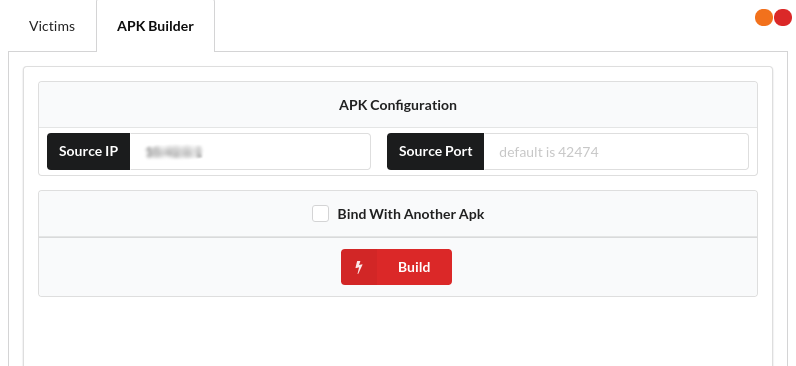
Now the apk is ready to infect a device and report back to the server. Upon installing on a device the apk reports back to the server and we can see the victim's entry on the dashboard:
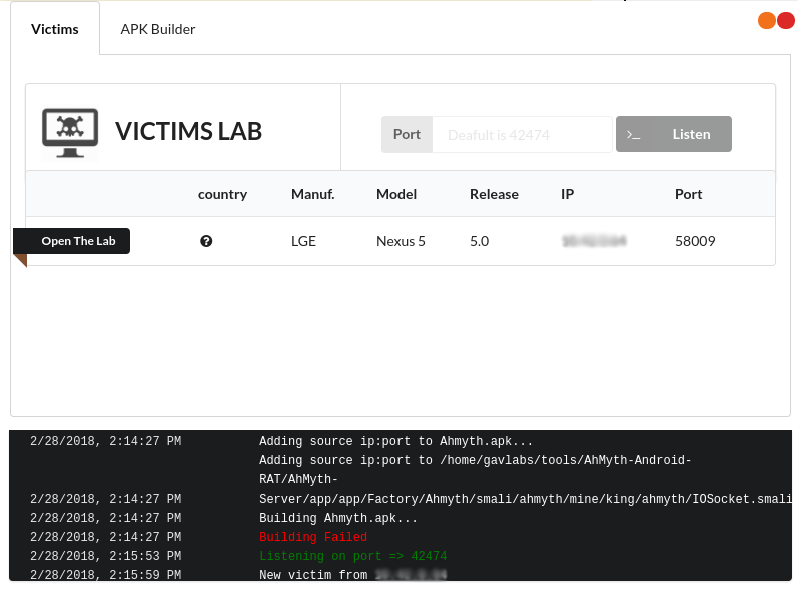
The attacker can now command the RAT to perform a number of functions, few of them are highlighted below:
- View Call logs
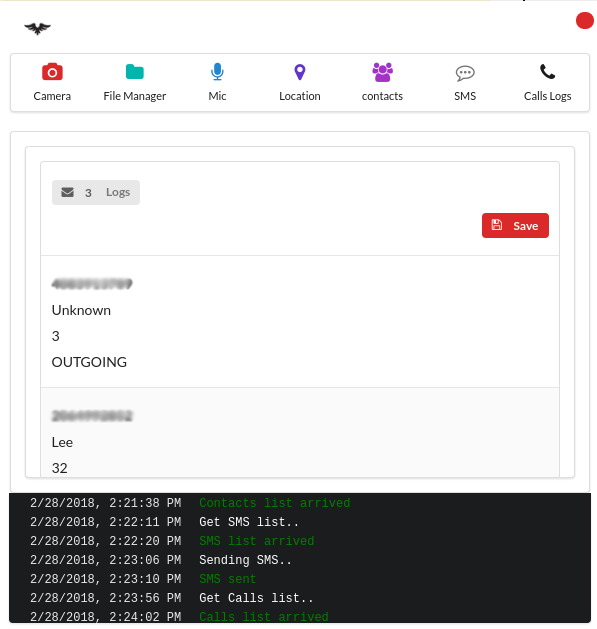
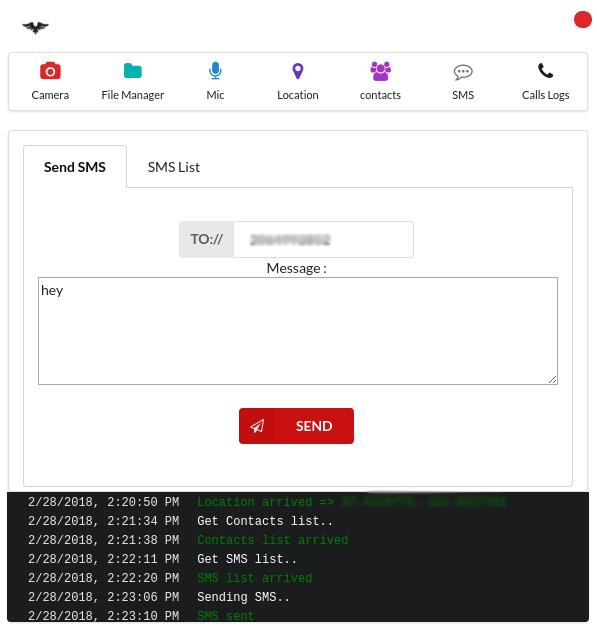
- View and send SMS
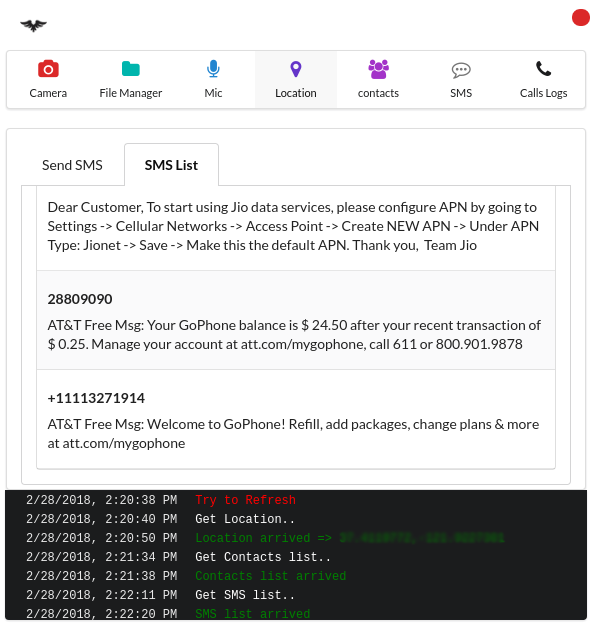
- View contacts
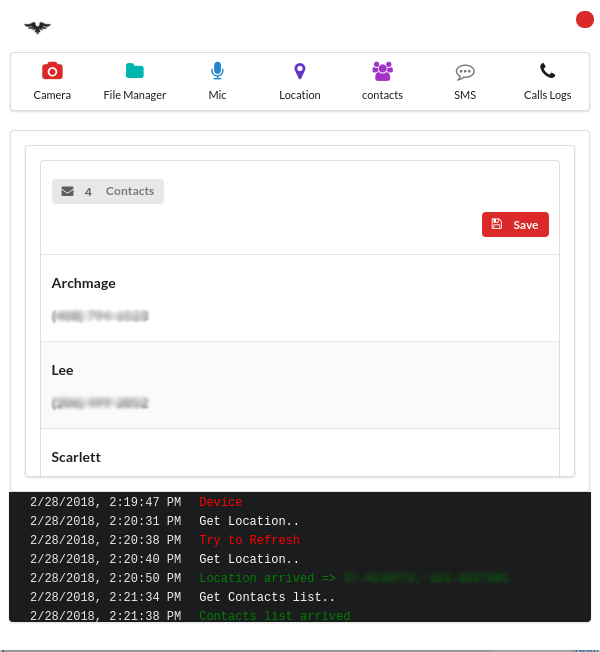
- View GPS location of the device
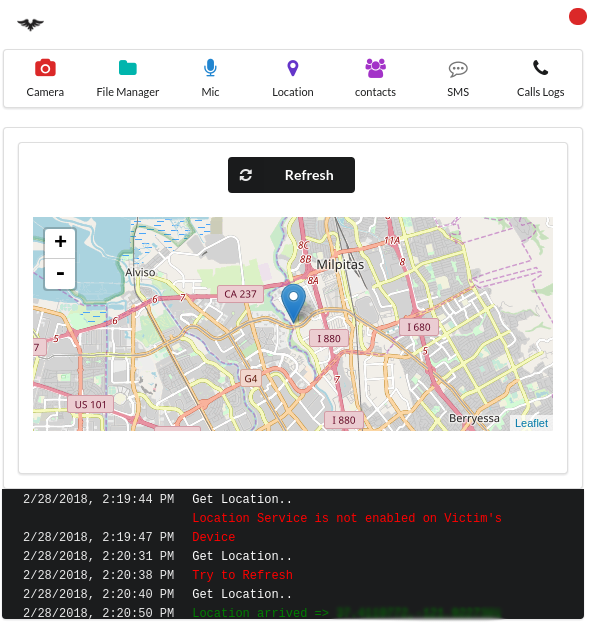
- View files on the device
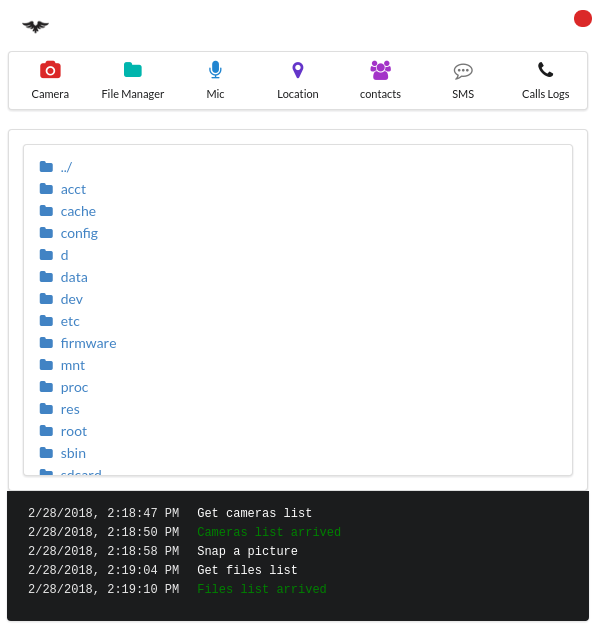
We obtained samples with different source location, this is the address where the apk will report back to:
- oleg12221443242.zapto.org:2222
- vivanesko2002.ddns.net:22708
- tafelrubber.us.to:6220
Spreading Ahmyth further
Malicious apk's spread mainly via the following two routes:
- As text message with a link to install the malicious apk
- Email message containing a link to install the app
Additionally an attacker can spread this RAT via the Ahmyth control server by:
- Sending a text message from the infected device to one of the victims contacts. For the new target it would appear as a text message from someone he knows, thereby there is a higher chance that he will trust this message
Another way to spread is this RAT is to trojanize it into something benign. Malware writers have already started combining Ahmyth with other clean Android apk's, we identified a few of them:
- Minecraft -com.mojang.minecraftpe
- YouTube Downloader -dentex.youtube.downloader
Below is a comparison of the code structure found in the original Ahmyth client apk and a few trojanized samples in the wild:
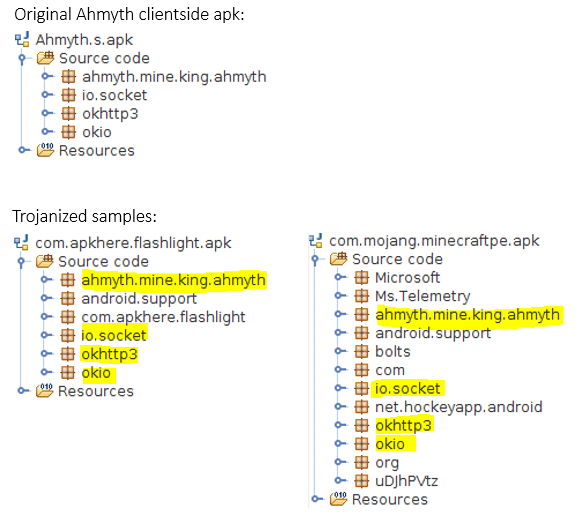
Overall this looks like another case where a publicly available tool has been used for personal reasons with a malicious intent. We can expect more trojanized Android samples with a hidden Ahmyth RAT in the near future.
Sonicwall Capture Labs provides protection against this threat with the following signatures:
- GAV: AndroidOS.AhRat.INFSTLR (Trojan)
- GAV: AndroidOS.AhRat.INFSTLR_2 (Trojan)
- GAV: AndroidOS.AhRat.INFSTLR_3 (Trojan)
Basic details about the samples analyzed:
-
- Package name: ahmyth.mine.king.ahmyth
- MD5: 8a630c3f3d441f012778efac3d154b90
-
- Package name: com.mojang.minecraftpe
- MD5: c552f2565df8b793fa68870309489b72
-
- Package name: dentex.youtube.downloader
- MD5: c1f5e9e560388d5aeedc71628967e119
- Package name: com.apkhere.flashlight
- MD5: 2b648af46eb081d896768a9b3413e3b4
Share This Article

An Article By
An Article By
Security News
Security News